Introduction
Zloader (aka Terdot, DELoader, or Silent Night), is a modular trojan born from the leaked Zeus source code. It surfaced publicly in 2016 during a targeted campaign against German banks1, but its malicious activity traces back to at least August 2015. Zloader’s first run persisted until the beginning of 2018 when its activities abruptly ceased. Its resurgence at the end of 2019, marketed in underground forums as “Silent Night”, came with substantial alterations. The evolution of Zloader progressed steadily, leading to the development of version 2.0.0.0 around September 2021. Similar to Qakbot, the threat actors using Zloader also pivoted from conducting banking fraud to ransomware. In April 2022, security researchers executed a takedown operation2 to dismantle the botnet leading to an extended period of inactivity.
After an almost two-year hiatus, Zloader reemerged with a new iteration that appears to have started development in September 2023. These new changes include new obfuscation techniques, an updated domain generation algorithm (DGA), RSA encryption for network communications, and the loader now has native support for 64-bit versions of Windows. Initially, this new version was labeled with the old version number 2.0.0.0. However, over the past several months, they released version 2.1.6.0 and 2.1.7.0. In this blog, we will explore these new updates to Zloader.
Key Takeaways
- Zloader dates back to 2015 and has been advertised in underground cybercriminal forums under the name “Silent Night” since the end of 2019.
- Zloader has returned after an almost two-year hiatus after being taken down in April 2022 by security researchers.
- The new version of Zloader made significant changes to the loader module, which added RSA encryption, updated the domain generation algorithm, and is now compiled for 64-bit Windows operating systems for the first time.
- Zloader continues to use junk code for obfuscation, as well as API import hashing and string encryption in an attempt to hinder malware analysis.
Technical Analysis
In the following sections, we dive into the technical details surrounding Zloader’s new updates to their anti-analysis techniques, embedded configuration, DGA, and network encryption.
Anti-analysis techniques
Zloader uses a combination of API import hashing, junk code, a filename check, and string obfuscation. The following sections analyze each technique.
Imports and API resolution
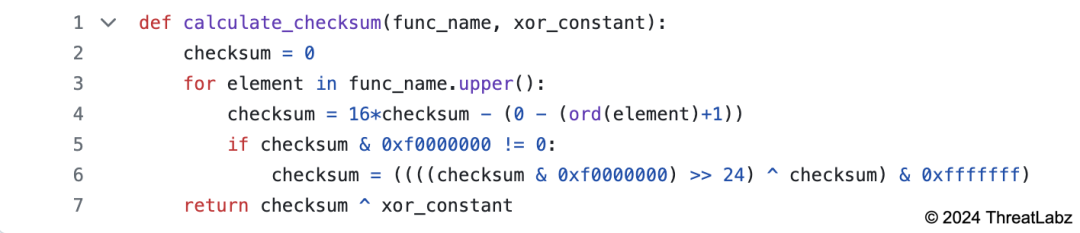
The newest Zloader samples only import a few functions from the kernel32 library. The remaining imports are resolved at runtime using checksums to obfuscate the functions that are used. This technique, already present in older versions, changes its implementation, adding an XOR constant which changes between samples. Python code that replicates the API hashing algorithm is shown below.
Code sample available on GitHub.
Junk code
Similar to previous versions, Zloader uses custom obfuscation. The new version of Zloader adds junk code that consists of various arithmetic operations, as shown in Figure 1 below.
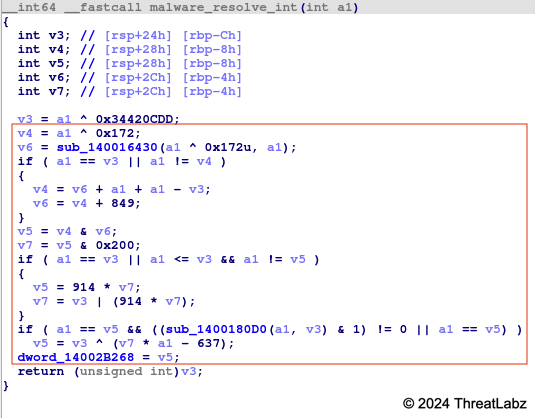
Figure 1. Example Zloader 2.1 junk code
In Figure 1, the instructions inside the red box are the junk code.
Anti-sandbox
Each Zloader sample expects to be executed with a specific filename. If the filename does not match what the sample expects, it will not execute further. This could evade malware sandboxes that rename sample files. Figure 2 shows an example of a Zloader sample that expects its filename to be CodeForge.exe.
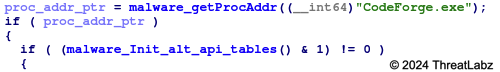
Figure 2. Example of Zloader’s anti-analysis filename check
ThreatLabz has observed Zloader use the following filenames:
- CodeForge.exe
- CyberMesh.exe
- EpsilonApp.exe
- FusionBeacon.exe
- FusionEcho.exe
- IonBeacon.dll
- IonPulse.exe
- KineticaSurge.dll
- QuantumDraw.exe
- SpectraKinetic.exe
- UltraApp.exe
String obfuscation
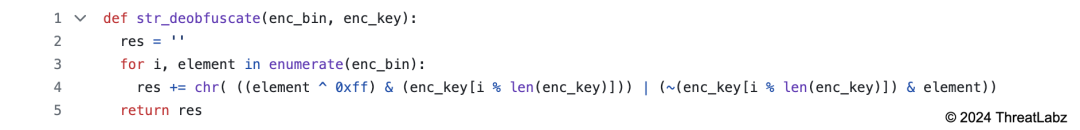
Similar to prior versions, Zloader implements a string obfuscation algorithm for some of the malware’s important strings such as registry paths, DLL names, and the DGA’s top-level domain (TLD) using XOR with a hardcoded key. Python code that replicates the string obfuscation algorithm is shown below:
Code sample available on GitHub.
The encryption key differs between samples and is also hardcoded in the .rdata section as shown in Figure 3 below.
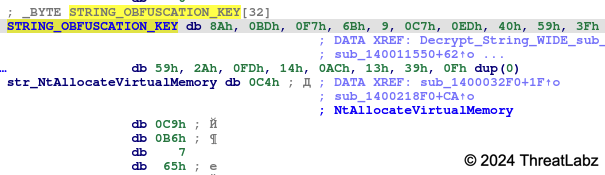
Figure 3. Example string obfuscation key used by Zloader
A list of Zloader’s obfuscated strings is shown in the Appendix.
Static configuration encryption and structure
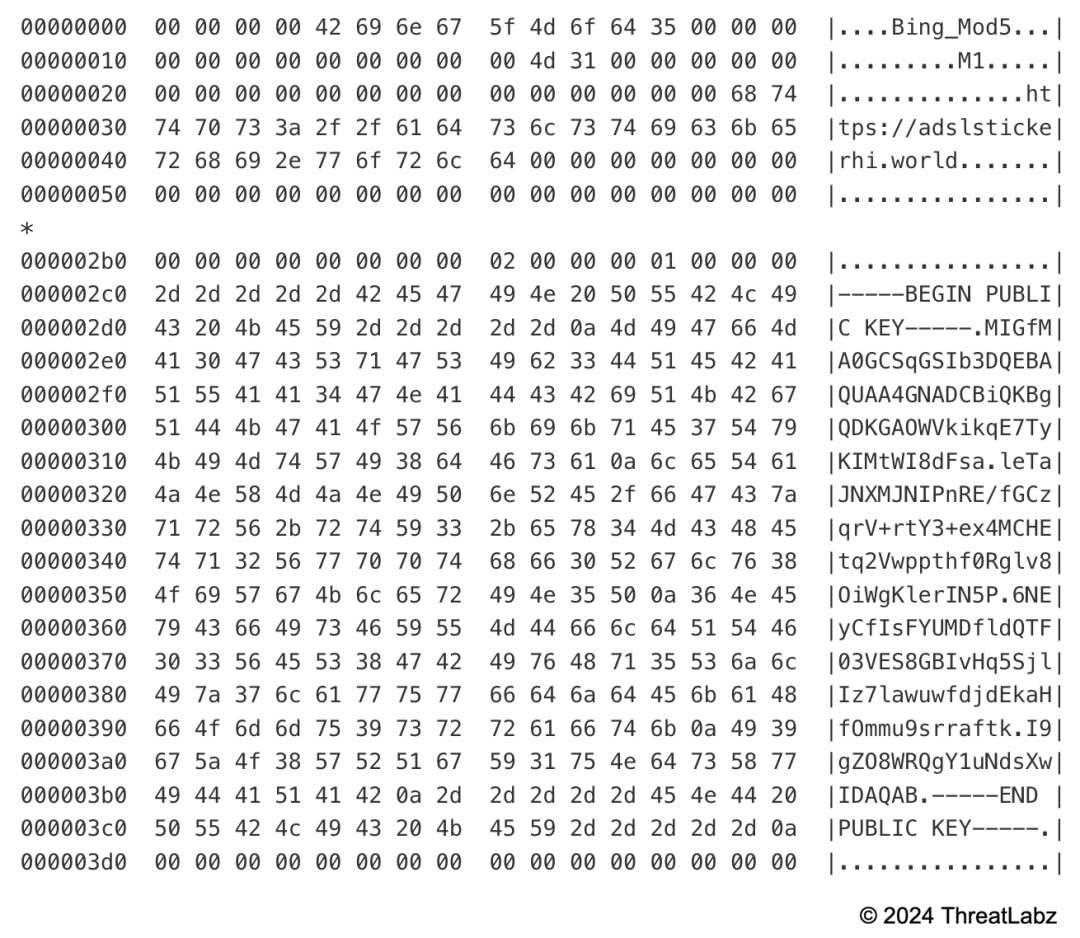
The Zloader static configuration is still encrypted using RC4 with a hardcoded alphanumeric key, but the structure is slightly different. The botnet ID, campaign name, and command-and-control servers (C2s) are set at fixed offsets, in addition to an RSA public key that replaces the old RC4 key that was used for network encryption. ThreatLabz has observed 15 unique new Zloader samples and all of them have the same RSA public key, likely indicating there is currently only a single threat actor using the malware.
An example Zloader static configuration is shown below.
Domain generation algorithm
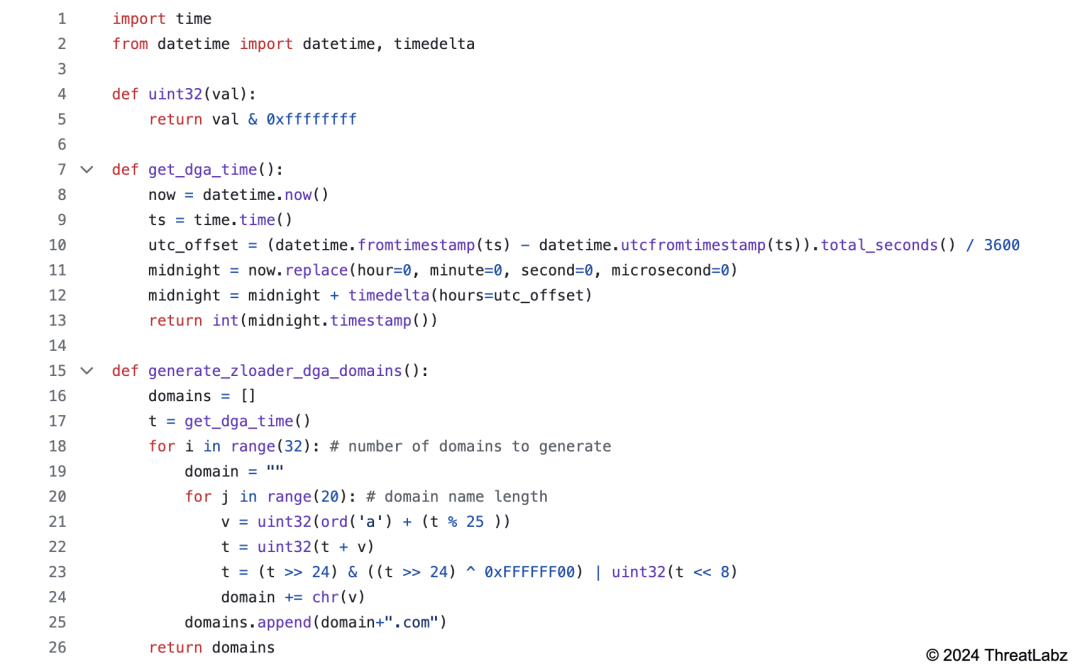
When the primary C2 server is not available, Zloader reverts to a DGA. The DGA algorithm has changed in the latest version and no longer contains a different seed per botnet. Python code that replicates Zloader’s new DGA algorithm is shown below.
Code sample available on GitHub.
The code generates 32 domains per day by using the local system time at midnight (converted to UTC) as a seed. Each of the DGA domains have a length of 20 characters followed by the “.com” TLD.
Network communications
Zloader continues to use HTTP POST requests to communicate with its C2 server. However, the network encryption is now using 1,024-bit RSA with RC4 and the Zeus “visual encryption” algorithms. Zloader uses the custom Zeus BinStorage format where the first 128 bytes are the RSA encrypted RC4 key (32 random bytes) and, the remaining bytes are encrypted with the RC4 key and visual encryption as shown in Figure 4:
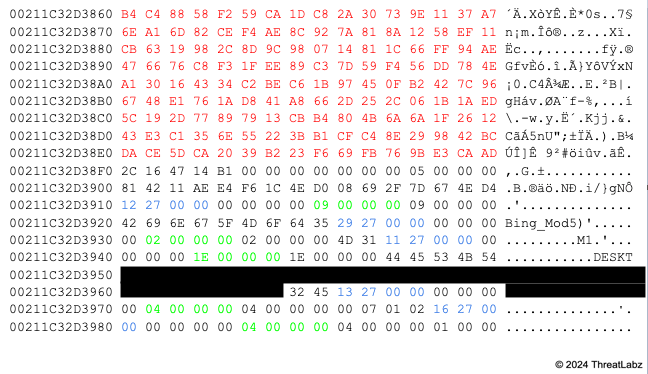
Figure 4. Zloader BinStorage object for a hello message (prior to encryption)
The Zeus BinStorage structure uses an ID integer value to represent the information stored, followed by the length and data. The BinStorage ID values in this example are shown in Table 1.
| Value (Decimal) | Value (Hexadecimal) | Description |
|---|---|---|
| 10002 | 0x2712 | Botnet ID |
| 10025 | 0x2729 | Campaign ID |
| 10001 | 0x2711 | Bot ID |
| 10003 | 0x2713 | Malware version |
| 10006 | 0x2716 | Unknown flag (set to 0x1) |
Table 1. Zloader BinStorage hello message fields
ThreatLabz has observed samples containing the following botnet IDs:
- Bing_Mod2
- Bing_Mod3
- Bing_Mod4
- Bing_Mod5
All of the campaign IDs have been set to the value M1.
Conclusion
Zloader was a significant threat for many years and its comeback will likely result in new ransomware attacks. The operational takedown temporarily stopped the activity, but not the threat group behind it. Returning after almost two years, Zloader has brought notable improvements to the loader module such as RSA encryption, an updated DGA, and enhanced obfuscation techniques, with more junk code, API import hashing, and string encryption to thwart malware analysis.
Zscaler ThreatLabz continues to track this threat and add detections to protect our customers.
Zscaler Coverage
In addition to sandbox detections, Zscaler’s multilayered cloud security platform detects indicators related to Zloader at various levels with the following threat names:
- Win64.Downloader.Zloader
Indicators Of Compromise (IOCs)
| SHA256 | Description |
|---|---|
| 038487af6226adef21a29f3d31baf3c809140fcb408191da8bc457b6721e3a55 | Zloader sample |
| 16af920dd49010cf297b03a732749bb99cc34996f090cb1e4f16285f5b69ee7d | Zloader sample |
| 25c8f98b79cf0bfc00221a33d714fac51490d840d13ab9ba4f6751a58d55c78d | Zloader sample |
| 2cdb78330f90b9fb20b8fb1ef9179e2d9edfbbd144d522f541083b08f84cc456 | Zloader sample |
| 83deff18d50843ee70ca9bfa8d473521fd6af885a6c925b56f63391aad3ee0f3 | Zloader sample |
| 98dccaaa3d1efd240d201446373c6de09c06781c5c71d0f01f86b7192ec42eb2 | Zloader sample |
| adbd0c7096a7373be82dd03df1aae61cb39e0a155c00bbb9c67abc01d48718aa | Zloader sample |
| b206695fb128857012fe280555a32bd389502a1b47c8974f4b405ab19921ac93 | Zloader sample |
| b47e4b62b956730815518c691fcd16c48d352fca14c711a8403308de9b7c1378 | Zloader sample |
| d92286543a9e04b70525b72885e2983381c6f3c68c5fc64ec1e9695567fb090d | Zloader sample |
| eb4b412b4fc58ce2f134cac7ec30bd5694a3093939d129935fe5c65f27ce9499 | Zloader sample |
| f03b9dce7b701d874ba95293c9274782fceb85d55b276fd28a67b9e419114fdb | Zloader sample |
| f6d8306522f26544cd8f73c649e03cce0268466be27fe6cc45c67cc1a4bdc1b8 | Zloader sample |
| fa4b2019d7bf5560b88ae9ab3b3deb96162037c2ed8b9e17ea008b0c97611616 | Zloader sample |
| fbd60fffb5d161e051daa3e7d65c0ad5f589687e92e43329c5c4c950f58fbb75 | Zloader sample |
| URL | Description |
|---|---|
| https://adslstickerhi[.]world | Zloader C2 |
| https://adslstickerni[.]world | Zloader C2 |
| https://dem.businessdeep[.]com | Zloader C2 |
Appendix
Tools
The code snippets in this blog have also been uploaded to our GitHub tools repository here.
Decoded strings
user32.dll | nbsp; | %s |
reg add HKCUSOFTWAREMicrosoftWindowsCurrentVersionRun /f /t REG_SZ /v %s /d “%s” | wininet.dll | td |
tr | br | SoftwareMicrosoft |
h3 | Local | hr |
POST | gdiplus.dll | NtWriteVirtualMemory |
https:// | * | ?? |
ntdll.dll | ws2_32.dll | _alldiv |
NtProtectVirtualMemory | NtGetContextThread | shell32.dll |
%s %s | psapi.dll | crypt32.dll |
S-1-15 | ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/ | _aulldiv |
“%s” | samlib.dll | S:(ML;CIOI;NRNWNX;;;LW) |
NtCreateThreadEx | regsvr32.exe /s “%s” | NtResumeThread |
bcrypt.dll | netapi32.dll | RtlGetVersion |
strtoul | winsta.dll | wldap32.dll |
NtReadVirtualMemory | Basic | 0:0 |
version.dll | h2 | InstallDate |
h5 | NtAllocateVirtualMemory | .com |
cabinet.dll | S:(ML;;NRNWNX;;;LW) | li |
kernel32.dll | %stmp_%08x | h6 |
aeiouy | div | rpcrt4.dll |
{%08X-%04X-%04X-%08X%08X} | iphlpapi.dll | mpr.dll |
C:WindowsSystem32ntdll.dll | Connection: close | gdi32.dll |
C:WindowsSystem32msiexec.exe | Global | |
wtsapi32.dll | NtCreateUserProcess | shlwapi.dll |
RtlUserThreadStart | %s | NtOpenProcess |
HTTP/1.1 | ncrypt.dll | INVALID_BOT_ID |
_aullrem | SoftwareMicrosoftWindowsCurrentVersionRun | dnsapi.dll |
ole32.dll | .dll | C:WindowsSysWOW64msiexec.exe |
bcdfghklmnpqrstvwxz | ftllib.dll | User metrics |
ThreadStart | MSIMG32.dll | * |
JKLMNOPQRSTUVW$$$$$$XYZ[]^_`abcdefghijklmnopq | h1 | NtSetContextThread |
*/* | GET | userenv.dll |
urlmon.dll | SoftwareMicrosoftWindows NTCurrentVersion | _ThreadStart@4 |
dxgi.dll | NtOpenSection | script |
/post.php | advapi32.dll | h4 |
secur32.dll | imagehlp.dll | |
%s_%s_%X | winscard.dll |
References
1 The Curious Case of an Unknown Trojan Targeting German-Speaking Users
2 Dismantling ZLoader: How malicious ads led to disabled security tools and ransomware | Microsoft Security Blog
Source: https://www.zscaler.com/blogs/security-research/zloader-no-longer-silent-night
Views: 0