Zhong Stealer is a new malware identified in a phishing campaign targeting the fintech and cryptocurrency sectors. Attackers used chat support platforms to distribute this malware, which modifies system settings for persistence and exfiltrates sensitive data to a command-and-control server in Hong Kong. Affected: Cryptocurrency sector, Fintech sector, Customer support services
Keypoints :
- Newly discovered malware named Zhong Stealer targets fintech and cryptocurrency sectors.
- Phishing campaign involved attackers posing as customers in chat support platforms.
- Zhong Stealer employs multiple tactics for execution and data exfiltration.
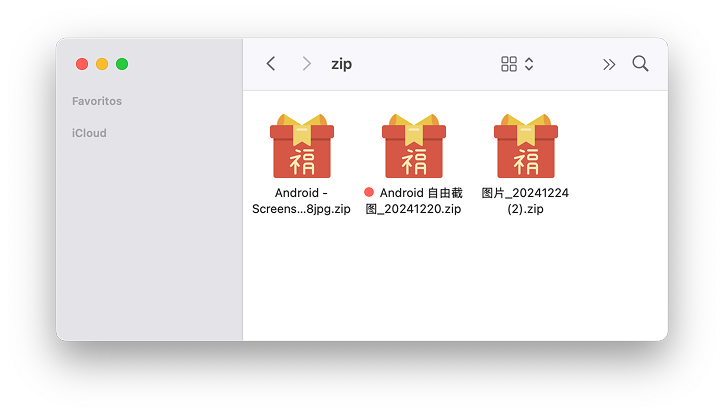
- It uses ZIP files containing malicious executable files named in Simplified and Traditional Chinese.
- The malware modifies registry keys and uses scheduled tasks to maintain persistence.
- Data is exfiltrated to a C2 server in Hong Kong via non-standard ports.
MITRE Techniques :
- T1562 – Disabling Event Logging: Prevents detection by interrupting logging features.
- T1547 – Gaining Persistence via Registry Keys: Modifies registry for startup execution of the malware.
- T1552 – Harvesting Credentials: Extracts sensitive data such as passwords and tokens from browsers.
- T1053 – Scheduling Tasks: To ensure the malware runs periodically even after reboots.
- T1571 – Communicating via Non-Standard Ports: Utilizes uncommon ports like 1131 for data transmission to evade detection.
Indicator of Compromise :
- [FileHash-MD5] 778b6521dd2b07d7db0eaeaab9a2f86b
- [FileHash-SHA1] ce120e922ed4156dbd07de8335c5a632974ec527
- [FileHash-SHA256] 02244934046333f45bc22abe6185e6ddda033342836062afb681a583aa7d827f
- [URL] hxxps://kkuu.oss-cn-hongkong.aliyuncs[.]com/ss/TASLogin.log
- [IP Address] 156.245.23.188
Full Story: https://any.run/cybersecurity-blog/cybersecurity-blog/zhong-stealer-malware-analysis/