Summary: Security researcher Ynwarcs has released an analysis and proof-of-concept exploit for the critical zero-click CVE-2024-38063 vulnerability in Windows TCP/IP, which allows remote code execution on systems with IPv6 enabled. This vulnerability poses a significant risk as it can be exploited without user interaction, affecting millions of devices globally.
Threat Actor: Unknown | unknown
Victim: Windows Users | Windows Users
Key Point :
- CVE-2024-38063 is a zero-click vulnerability that allows remote code execution through specially crafted IPv6 packets.
- The flaw originates from an Integer Underflow issue in the Windows TCP/IP stack, which can lead to a buffer overflow.
- Ynwarcs has provided a proof-of-concept exploit that currently causes a denial of service, highlighting the potential for further exploitation.
- Microsoft has released security updates to address this vulnerability, urging users to apply them immediately.
- Security teams should monitor network traffic for unusual IPv6 packet activity to detect potential exploitation attempts.
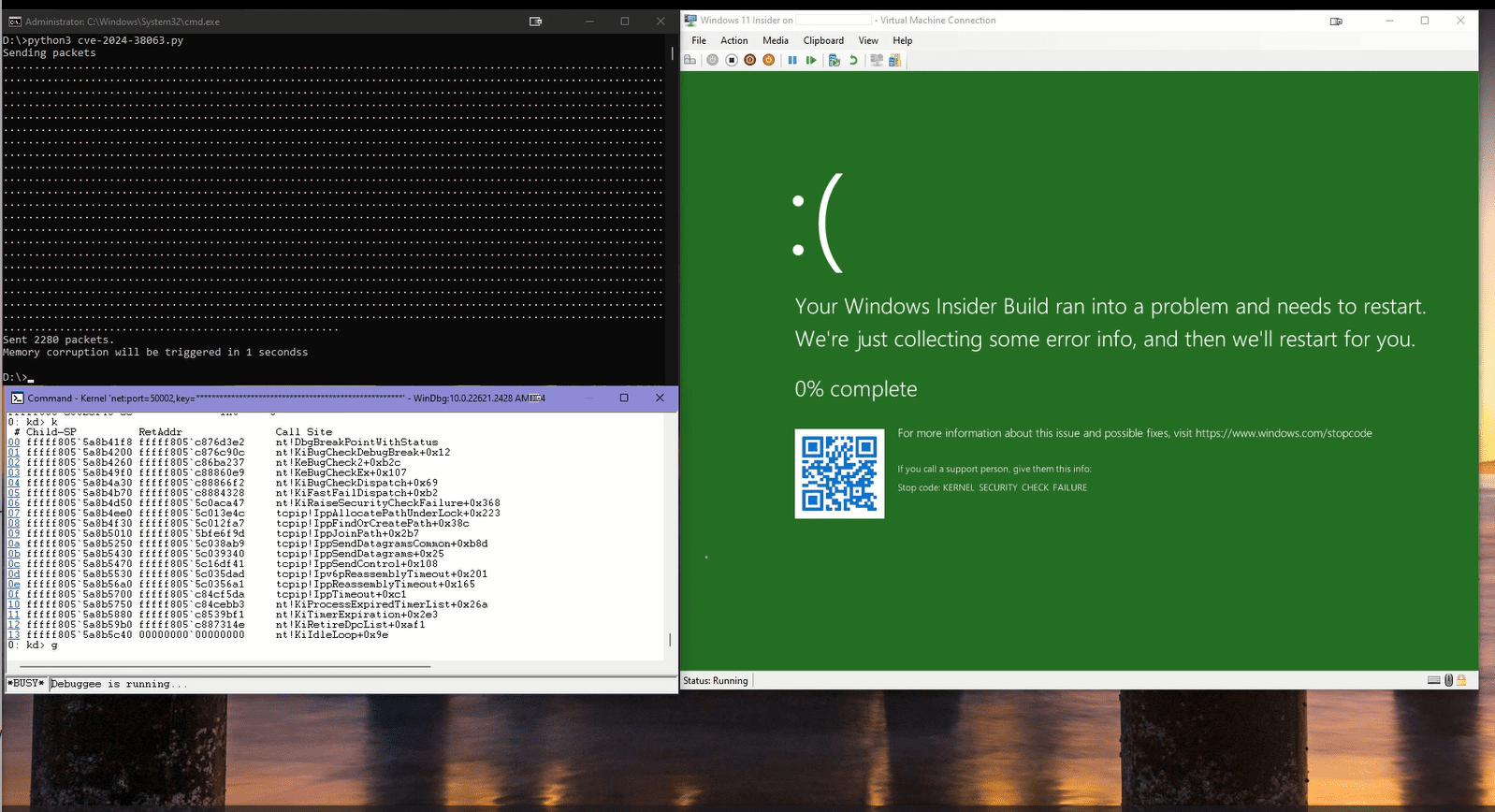
In a significant development for cybersecurity professionals, security researcher Ynwarcs has published an in-depth analysis and proof-of-concept (PoC) exploit code for a critical zero-click CVE-2024-38063 vulnerability in Windows TCP/IP. This remote code execution (RCE) flaw affects all Windows systems with IPv6 enabled, making it a potential threat to millions of devices worldwide.
CVE-2024-38063, originally discovered by XiaoWei of Kunlun Lab, stems from an Integer Underflow weakness within the TCP/IP stack of Windows. This vulnerability can be exploited by attackers to trigger a buffer overflow, allowing them to execute arbitrary code on vulnerable Windows 10, Windows 11, and Windows Server systems. What makes this vulnerability particularly dangerous is that it requires no user interaction—attackers can remotely exploit it by simply sending a series of specially crafted IPv6 packets.
As explained by Ynwarcs in his detailed technical analysis, the vulnerability lies in the way Windows processes coalesced IP packets. When multiple IPv6 packets are batched together, the system processes their extension headers first before moving on to the packet data. However, a parsing error in the “destination options” extension header can lead to a chain reaction of errors, ultimately causing a buffer overflow.
Ynwarcs describes how the flaw can be abused through a sequence of carefully orchestrated steps, involving the manipulation of packet offsets and header fields to cause unexpected behavior during packet reassembly. The key to exploiting CVE-2024-38063 lies in triggering a timeout in the IPv6 packet reassembly process, leading to an integer overflow and subsequent heap-based buffer overflow.
While Ynwarcs has released PoC exploit code for the CVE-2024-38063 vulnerability, they note that the current version triggers a denial of service (DoS) rather than full remote code execution. Despite this, the existence of the PoC serves as a stark reminder of the potential for further exploitation, particularly as attackers refine their techniques.
The PoC exploit involves sending malformed IPv6 packets with a “destination options” extension header designed to trigger errors in packet parsing. By carefully crafting these packets and manipulating fields such as the hop limit and flow label, the PoC attempts to exploit the vulnerability by causing multiple corruptions in the system’s memory.
Despite the alarming potential of CVE-2024-38063, achieving full remote code execution with this vulnerability is no easy task. As noted by the well-known security researcher farmpoet, who commented on the PoC, the constraints surrounding this vulnerability make RCE highly challenging. However, the door remains open for future developments, with Farmpoet adding, “I’m open to being proven wrong.”
The PoC code has been made available on GitHub, allowing security researchers and developers to study the vulnerability in detail. However, the availability of such code also raises the stakes for system administrators and organizations worldwide, who must act quickly to patch affected systems before attackers can leverage this vulnerability in the wild.
Given the seriousness of CVE-2024-38063, Microsoft has urged users to apply the latest security updates as soon as possible. The vulnerability was addressed in the company’s August Patch Tuesday release, which includes updates that fix the underlying Integer Underflow issue in the TCP/IP stack.
For organizations and individuals running Windows systems with IPv6 enabled, the immediate application of these patches is crucial to prevent potential exploitation. Additionally, security teams are advised to monitor network traffic for any signs of unusual IPv6 packet activity, which could indicate attempts to exploit this vulnerability.
Related Posts:
Views: 0

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português