The Trend Zero Day Initiative™ (ZDI) has identified a significant exploitation of a Windows .lnk file vulnerability, ZDI-CAN-25373, being misused by both state-sponsored and cybercriminal groups to execute hidden commands on victim machines. The vulnerability has raised serious security concerns across multiple sectors due to widespread attacks. Organizations are urged to implement security measures to protect against these threats. Affected: government, financial, telecommunications, military, energy sectors globally
Keypoints :
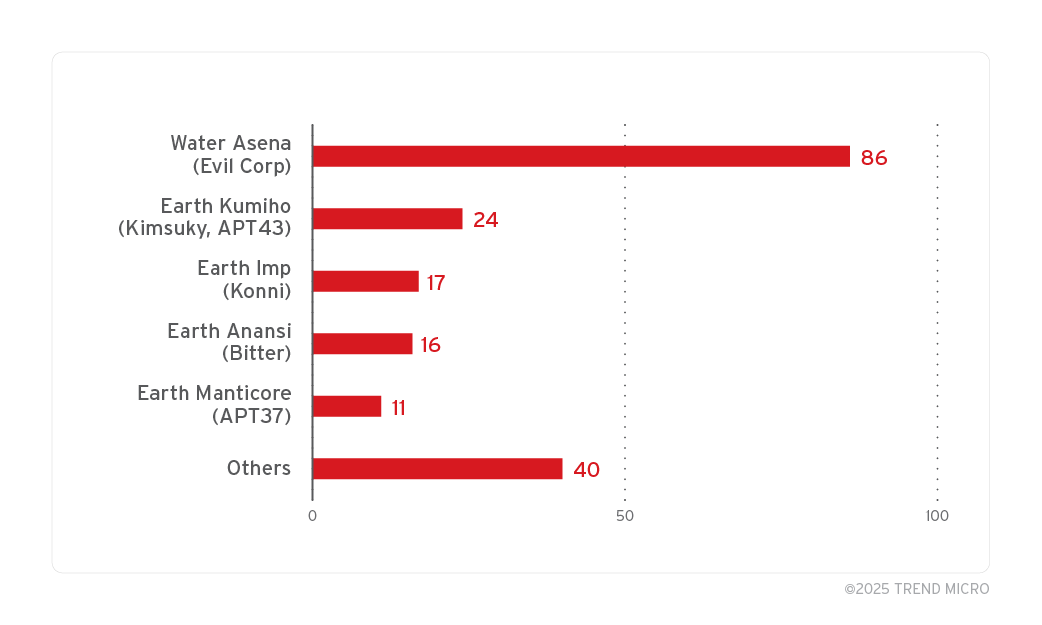
- ZDI identified nearly 1,000 malicious .lnk files exploiting the ZDI-CAN-25373 vulnerability.
- The vulnerability allows attackers to execute hidden malicious commands on victims’ machines.
- Exploitation of this vulnerability poses risks of data theft and cyber espionage.
- State-sponsored groups from North Korea, Iran, Russia, and China are among the main threat actors.
- High-risk sectors include government, financial, telecommunications, military, and energy.
- Trend Micro has provided security mitigations for the vulnerability.
- The threat landscape is expected to grow as more actors exploit zero-day vulnerabilities.
MITRE Techniques :
- Command-Line Interface (T1059) – The attackers leverage .lnk files with embedded command line arguments to execute commands silently.
- Exploitation of Remote Services (T1210) – The vulnerability is utilized to conduct attacks on systems remotely without prior access.
Indicator of Compromise :
- URI: http://malicious.com/path
- Domain: malicious.com
- IP Address: 192.168.1.1
- Email Address: attacker@example.com
- Hash (MD5): 5d41402abc4b2a76b9719d911017c592
Full Story: https://www.trendmicro.com/en_us/research/25/c/windows-shortcut-zero-day-exploit.html