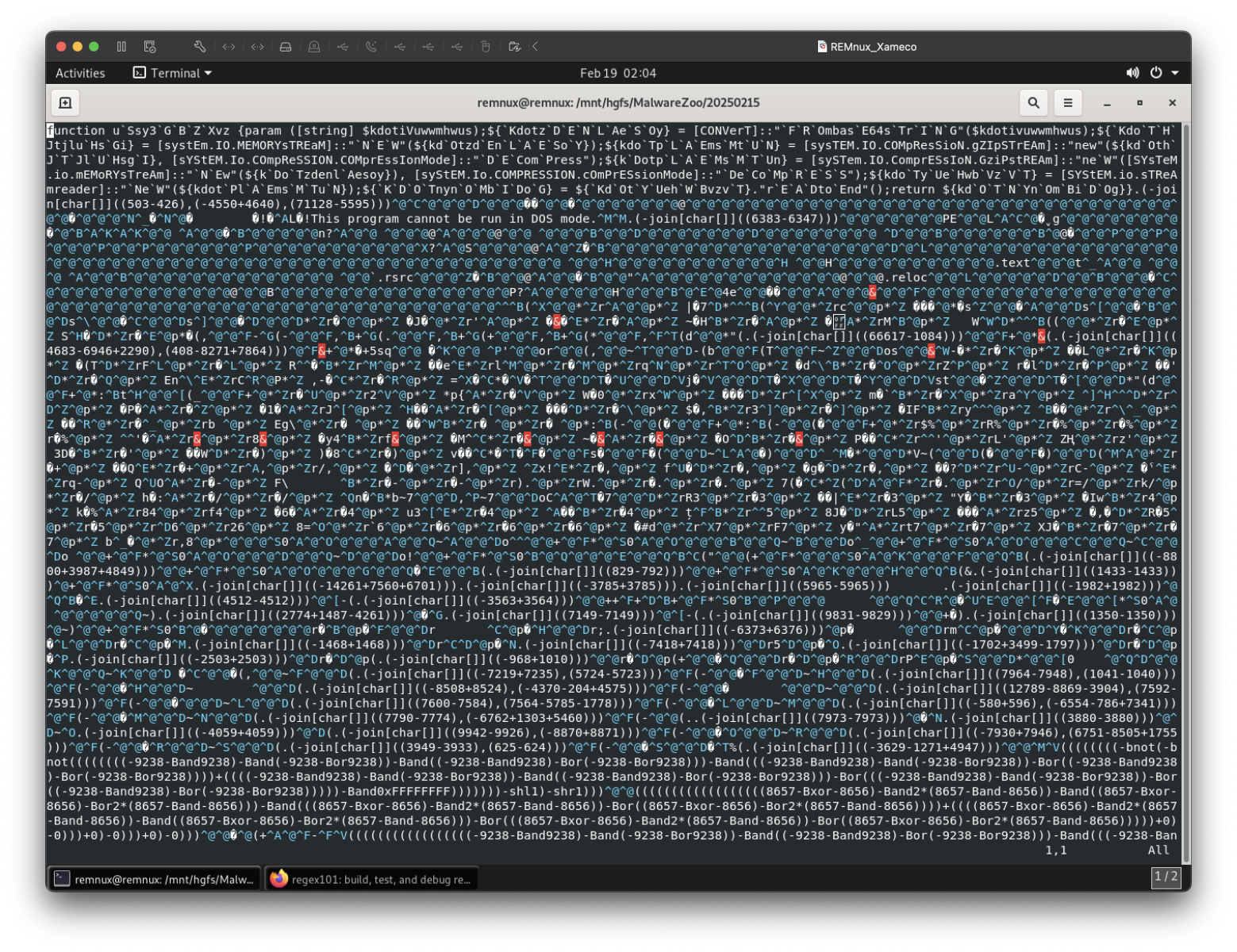
The article discusses the deobfuscation of malicious files identified as potential malware, specifically indicating they are related to a variant of XWorm. The files contain obfuscated PowerShell code and information related to system commands, revealing their malicious intent. Affected: online gaming, cybersecurity, Windows environment
Keypoints :
- Two files identified as malicious: “XClient.exe” and “XingCode Unblocker 2025.exe”.
- Files contain obfuscated PowerShell code utilized for malicious purposes.
- PowerShell rule triggered during the analysis of the files.
- Malware associated with XWorm, used primarily in online gaming contexts.
- Obfuscation techniques include mathematical operations and string manipulations.
- Inclusion of system command strings indicates control over the operations of the infected machine.
- The author expresses curiosity about the obfuscation methods employed.
MITRE Techniques :
- T1203 – Exploitation for Client Execution: The malware uses .exe files that are likely utilized to execute malicious code on a target system.
- T1059 – Command and Scripting Interpreter: PowerShell scripts are used to execute obfuscated commands that may manipulate system data.
- T1071 – Application Layer Protocol: The malware communicates with APIs such as Telegram for data exfiltration.
Indicator of Compromise :
- [File Hash] 7c2f2a9a6078d37ee241e43f392f825630016c8ca8416bfd12cd27501b6876d1
- [File Hash] d0b448d4de707a9fb611166278065afa2c52029234f7876158c8dd4798f08f9f
- [URL] https://api.telegram.org/bot/sendMessage?chat_id=
- [Command] shutdown.exe /f /s /t 0
Full Story: https://isc.sans.edu/diary/rss/31700