The article discusses the discovery of multiple cyberattack campaigns targeting job applicants at Food Corporations of India, using a variant of ransomware named Xelera. The attack begins with a malicious document aimed at enticing applicants, which ultimately installs a PyInstaller executable that also utilizes Discord for command and control. The ransomware performs various malicious tasks, including data exfiltration and credential theft. Affected: Job seekers, Food Corporation of India, computer systems
Keypoints :
- Seqrite Labs APT-Team identified campaigns with malicious job descriptions targeting job applicants at Food Corporations of India (FCI).
- The ransomware variant involved is known as Xelera, written in Python and deployed via a PyInstaller executable.
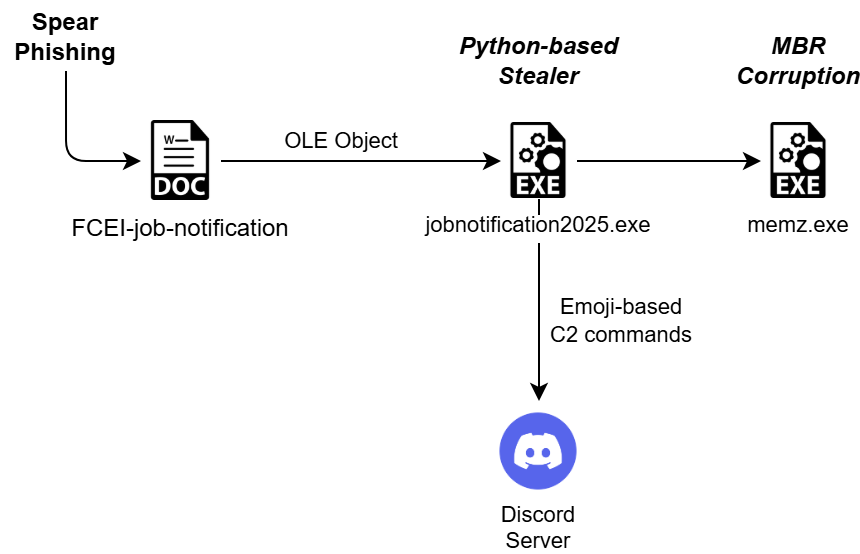
- The initial infection is spread through spear-phishing emails containing malicious documents.
- The attack involves a multi-stage infection chain: initial document, PyInstaller executable, and Python scripts.
- The Discord bot enables advanced features for controlling infected machines, such as stealing browser credentials and executing harmful commands.
- Xelera ransomware executes several destructive functions including data deletion and MBR corruption.
- The campaign has resulted in a significant number of transactions using the specified cryptocurrency wallet linked to the ransomware.
- Various indicators of compromise (IOCs) including file hashes, URLs, and email addresses are provided for threat detection.
MITRE Techniques :
- T1566.001 – Phishing: Spear phishing Attachment – The attack begins with a malicious document attachment sent to targeted job seekers.
- T1204.002 – User Execution: Malicious File – The execution of the malware occurs when the user opens the malicious document.
- T1059.006 – Python – The malware utilizes Python scripting for its operations.
- T1547.001 – Registry Run Keys / Startup Folder – The malware attempts to establish persistence by using registry run keys.
- T1562.001 – Impair Defenses: Disable or Modify Tools – The malware contains functionality to evade security tools.
- T1555.003 – Credentials from Web Browser – The ransomware is designed to extract sensitive information from web browsers.
- T1033 – System Owner/User Discovery – The malware may gather information about system users.
- T1217 – Browser Information Discovery – The malware retrieves browsing data.
- T1010 – Application Window Discovery – The ransomware can identify open applications on the victim’s computer.
- T1083 – File and Directory Discovery – The malware can scan for files and directories in the system.
- T1016 – System Network Configuration Discovery – The malware detects network configuration on the infected machine.
- T1560.002 – Archive via Library – Data collection processes occur to gather and archive sensitive information.
- T1056.001 – Keylogging – The malware is capable of capturing keystrokes from the infected system.
- T1113 – Screen Capture – The Discord bot can take screenshots of the victim’s screen.
- T1102.002 – Bidirectional Communication – The malware utilizes Discord for command and control operations.
- T1531 – Account Access Removal – The ransomware may disable user accounts.
- T1486 – Data Encrypted for Impact – The main impact involves data encryption by the ransomware.
- T1657 – Financial Theft – Ransom payments are requested via a cryptocurrency wallet.
- T1491.001 – Internal Defacement – The malware causes damage to the victim’s system interface and functionality.
- T1561.001 – System Shutdown / Reboot – Ransomware includes functionalities to shut down or restart the system.
Indicator of Compromise :
- [Filename] FCEI-job-notification.doc
- [SHA-256] ff06ce3fd6fe994aeaa0edc5162989d08f34440e9cacbc9e49e5db8ef98a74e3
- [Filename] mainscript.exe (jobnotification2025.exe)
- [SHA-256] 519401c998fe5d6eb143415f7c17ad5f8e5ef5ebae57ac91e9fa89a0bfcf0c7f
- [URL] hxxps[:]//github[.]com/Sam-cpu999/stuff/raw/main/MEMZ[.]exe
Full Story: https://www.seqrite.com/blog/xelera-ransomware-fake-fci-job-offers/
Views: 19