During the past few weeks, we’ve observed a number of malicious Google search ads targeting IT staff. These malvertising campaigns are nothing new, in fact they have been documented numerous times before. However, by tracking them closely, we were able to see subtle changes and interesting connections.
In this blog post, we highlight how shared infrastructure is being used to distribute two payloads, namely MadMxShell backdoor and WorkersDevBackdoor. In addition to having an advert that overlaps for both backdoors, our most interesting finding was that the command and control server for MadMxShell can be directly tied to the WorkersDevBackdoor delivery infrastructure.
Both malware payloads have the capability to collect and steal sensitive data, as well as provide a direct entry path for initial access brokers involved in ransomware deployment.
Two backdoors
The two malware payloads we are talking about in this blog post need a little bit of an introduction.
MadMxShell was named by Zscaler in a blog post released in April 2024, and has the following characteristics:
- Distributed via malicious ads for IP scanners
- Uses DLL hijacking
- DNS for communication with its C2 server via OneDrive.exe
WorkersDevBackdoor has a longer and more complicated history. The most recent publication (and its name) come from eSentire although it was previously described by mithrandir as a new dropper for the StealC stealer. It has a very unique way of packaging its payload in a password protected archive. In theory, that payload could really be anything, but it has been tied to ThunderShell RAT and Parcel RAT.
- Distributed via malicious ads for IP scanners
- NSIS installer with encrypted 7z archive containing payload
- Payload is hosted on Dropbox
Google ads for “IP scanners”
In recent malvertising incidents we have tracked, the majority of ads we observed were related to IP scanners, and redirect to infrastructure that we associate with a campaign we call goodgoog1e. The goodgoog1e name comes from an email address used by the threat actor that ties all these domains together, something we will explore further in our investigation.
The image below shows ads from searches for Angry IP, Advanced IP Scanner or network scanning tools in general. We broke down the ads by their final payload: two backdoors known as MadMxShell and WorkersDevBackdoor.
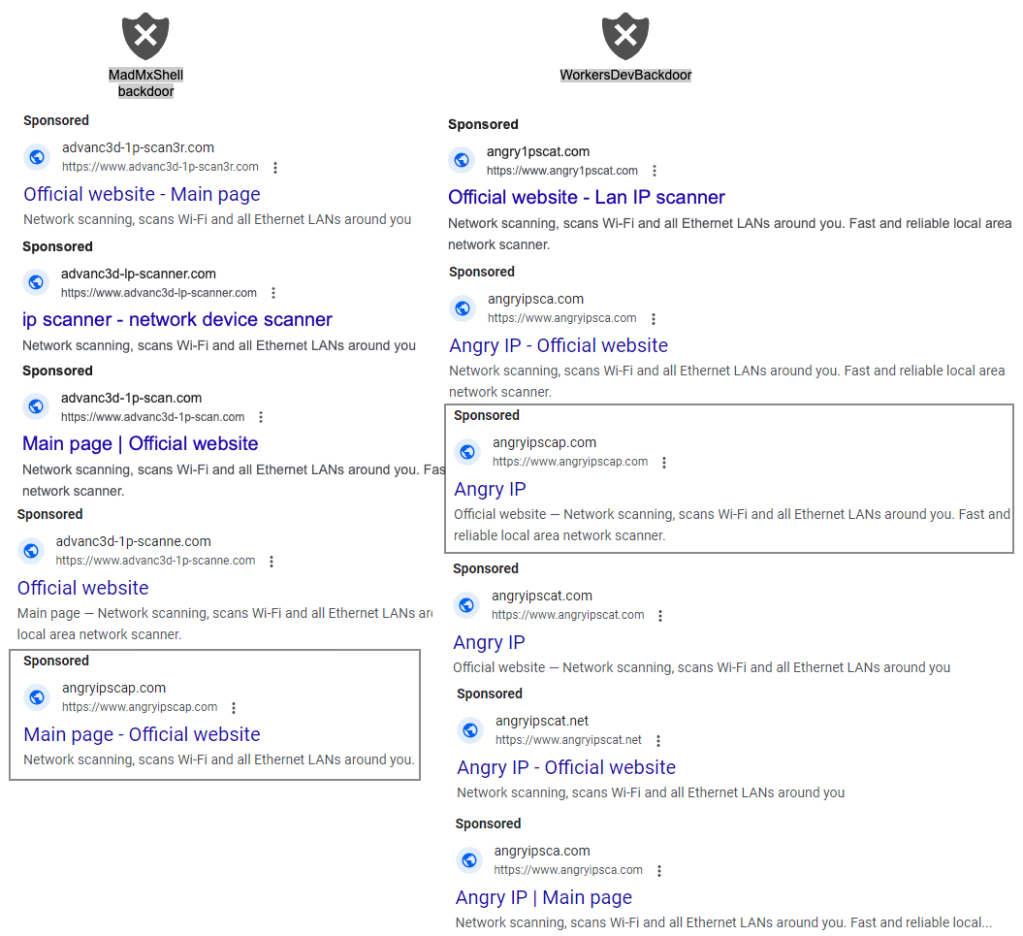
Distribution chains
Based on data collected by tracking those malicious ads, we drew a diagram showing the different incidents we observed. While they all start from the same entity (goodgoog1e) they are actually from different advertiser accounts listed below:
- Patrick Speleers
- Alex Robinson
- Drew Shader
- Bradley Nussbaum
- Nesim Bildirici
- Scott Willey
- 14621862906761838593
- 03177867021232635905
- 07839400636255830017
While all these identities are fraudulent, some are not identifiers yet, but only first and last name, presumably because the ad account is very new. Interestingly, we saw that one particular ad (from advertiser ID 03177867021232635905) was used to drop both payloads via the domain angryipo[.]org.
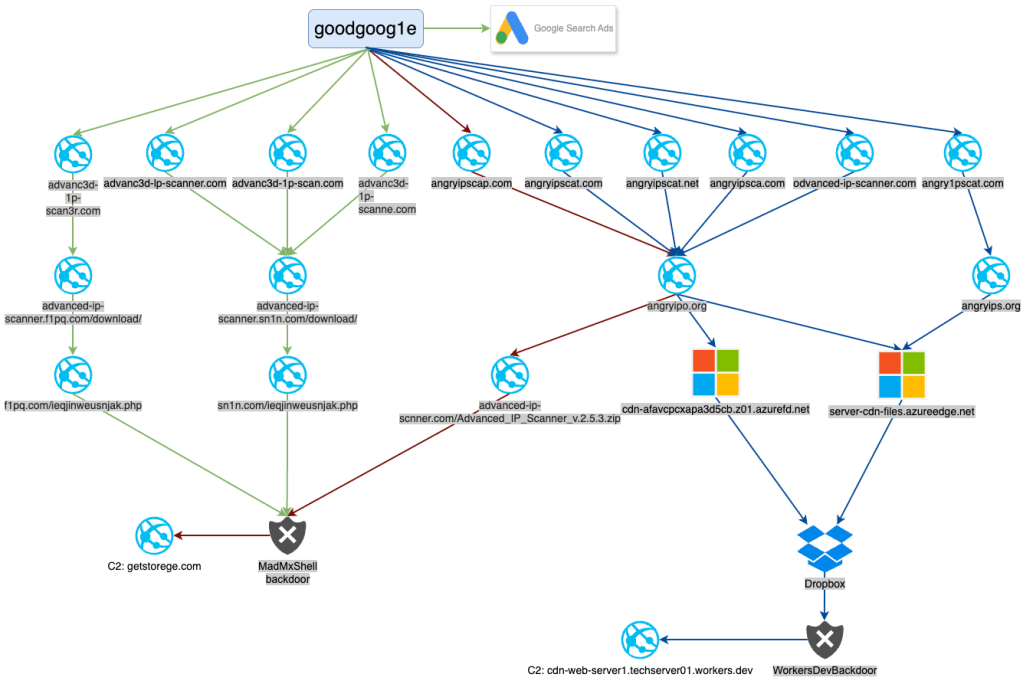
Network traffic
Looking at network traffic for their usual distribution path, both malware payloads have very different delivery techniques which we highlight below:
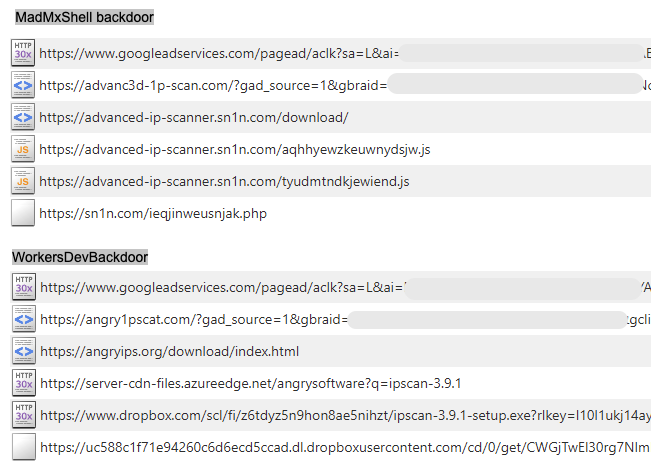
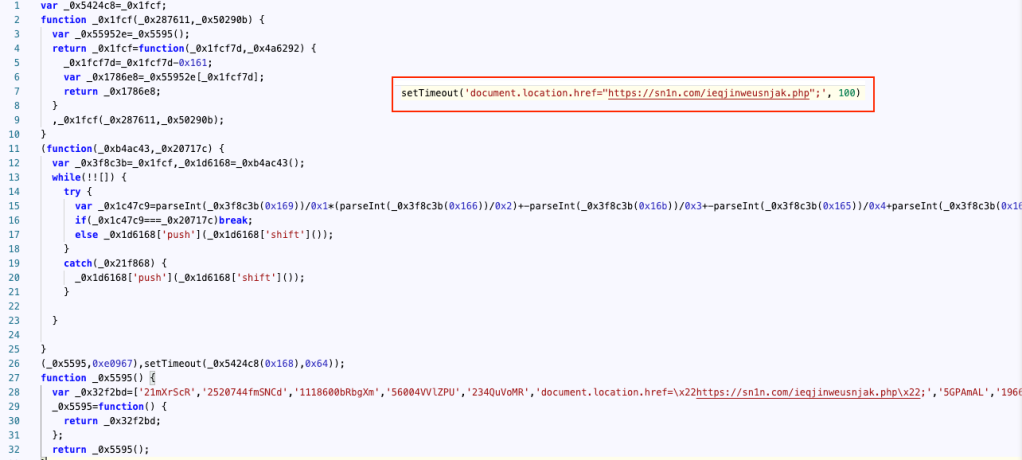
MadMxShell uses several obfuscated scripts to eventually lead to the payload; with a complicated script that produces a one-liner that triggers an automatic download:
WorkersDevBackdoor is hosted via Dropbox with rotating URLs (as they get reported). It’s interesting to note they are using azureedge[.]net (Microsoft content delivery) to get the Dropbox URL dynamically:
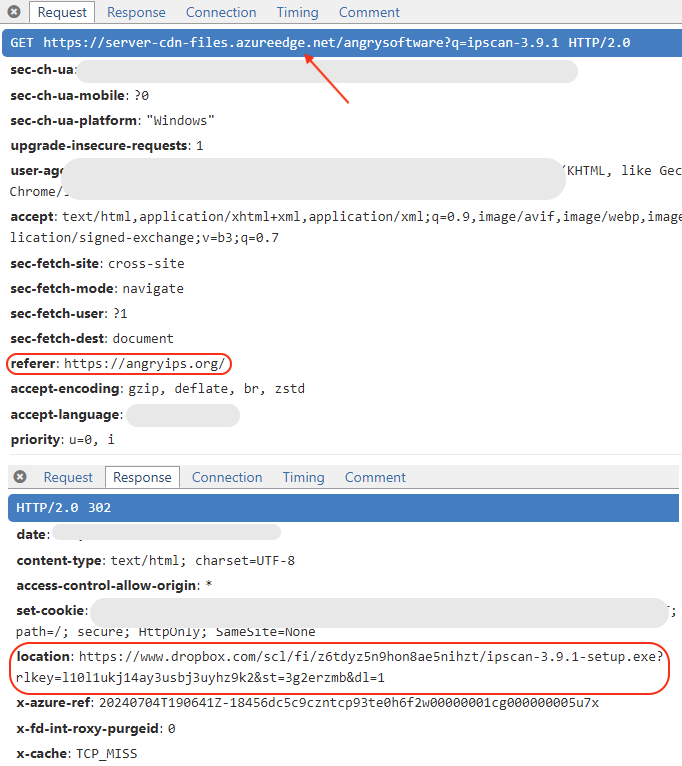
The C2 connection
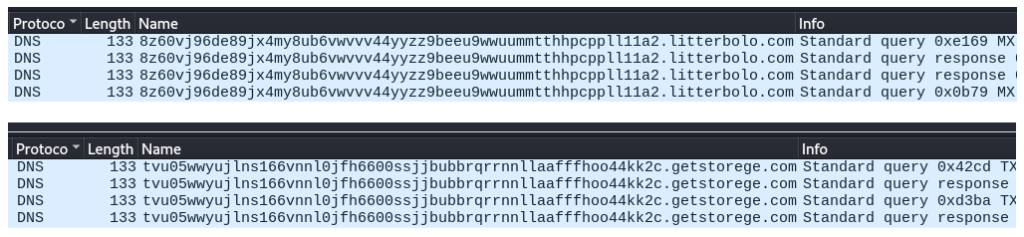
In their blog post, Zscaler identified litterbolo[.]com as the C2 server for MadMxShell. In the most recent campaign, the C2 switched to getstorege[.]com. Both follow the same 58-character length subdomain format:
The domain name getstorege[.]com was registered by goodgoo1ge@protonmail[.]com, the same email address used for infrastructure delivering both MadMxShell and WorkersDevBackdoor.
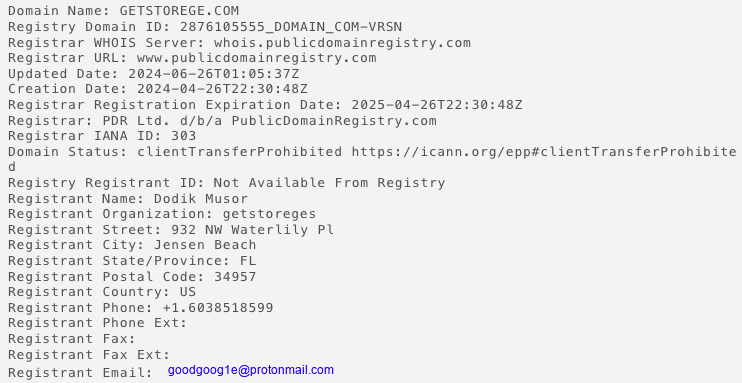
(On a side note, the email address wh8842480@gmail[.]com used to register the former C2 domain (litterbolo[.]com) was similarly reused for the malware distribution domains. However, no connection was made at the time about malware overlap.)
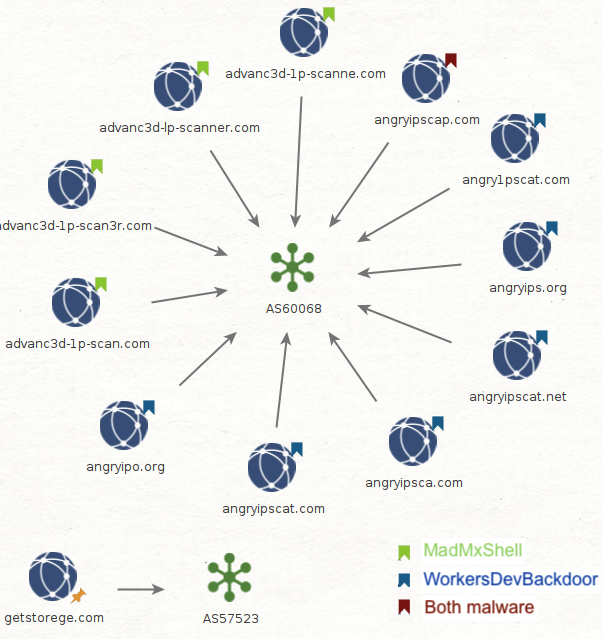
The graph below shows how the same email address connects domains associated with MadMxShell, including its C2, and domains tied with the distribution of WorkersDevBackdoor. It is interesting to see that the malware C2 shares the same registrant as the infrastructure used to deliver it. There could be a more direct involvement from the threat actor that setups the Google ads, ad domains and landing pages and the actual malware (MadMxShell).
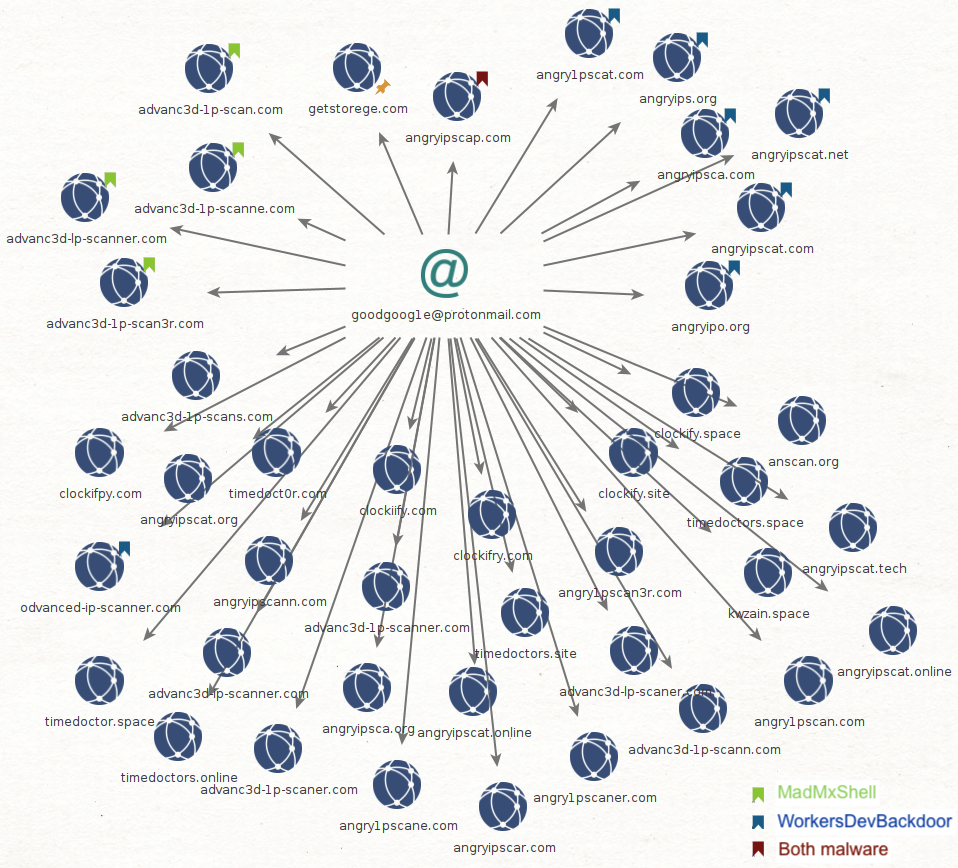
Obviously, seeing domains tied to the distribution of WorkersDevBackdoor by that same email address is also quite revealing. In the next section, we will show that this was not the only link, and that there is also infrastructure sharing.
Infrastructure overlap
The domains used to distribute both malware payloads were hosted on a server belonging to AS60068.(AKA CDN77 _). The C2 domain getstorege[.]com is on the notorious AS57523 (CHANGWAY-AS, HK). We’ve also noticed overlap with IP addresses shared in both malware distribution campaigns.
Target in sight: IT staff
One of the WorkersDevBackdoor samples we collected was different from the others as it contained a PowerShell script called soft_detect.ps1. The script loops through a list of keywords (.rdp, teamviewer, anydesk, vnc, logmein, putty) and checks for a path on the victim’s Desktop that would match any of these words. The output from this command determines whether the installation of the backdoor completes or exits quietly.
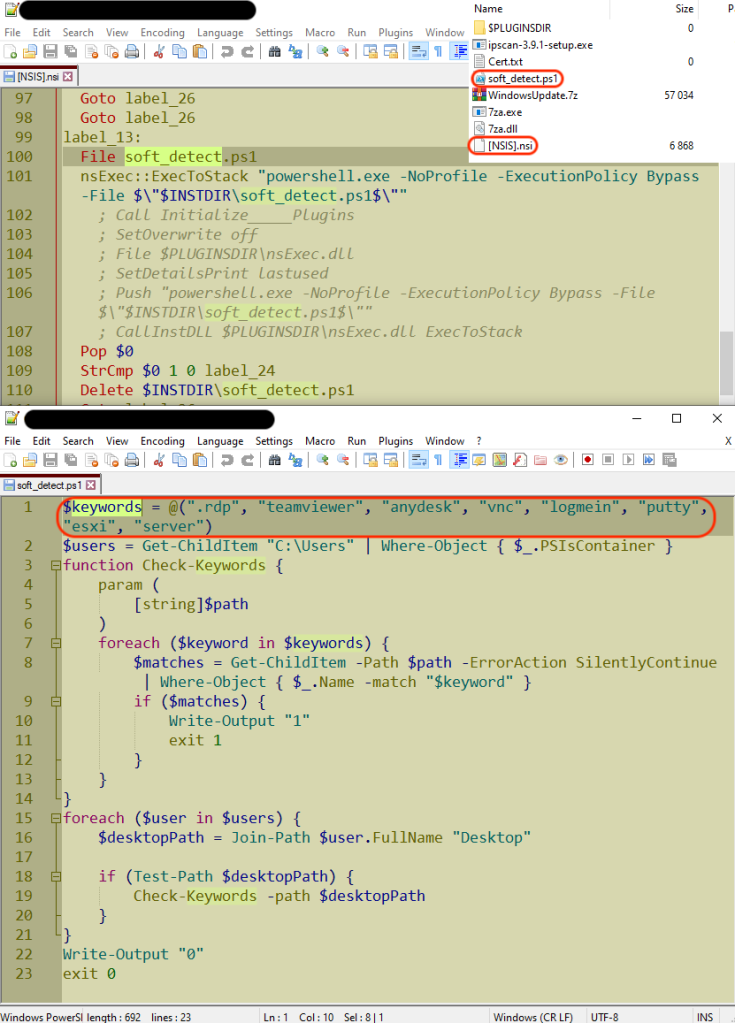
PowerShell scripts like this one or others that check if a computer is joined to a domain, allow attackers to avoid unnecessary log alerts generated by malware running in sandboxes or virtual machines. This is a good reminder that a file scanned statically or even ran in a sandbox could come out as legitimate simply because conditions were not met for its proper execution.
Conclusion
Often times, malvertising campaigns we track look quite similar on the surface, but we can’t always say whether they are run by the same threat actors. One of the most important questions in our investigations is about what malware payload is being distributed and usually what command and control server(s) it is connected to. After all, there would not be much point in using malicious ads if it weren’t for wanting to drop malware (or phish for credentials).
Before malware is dropped, there are a number of techniques, tactics and procedures (TTPs) that can often be unique and correspond to a particular threat actor. The same can be said for indicators of compromise (IOCs), with a caveat that malicious infrastructure can be used and reused by different threat groups.
In this blog post, we made observations related to the distribution of two distinct malware families, namely WorkersDevBackdoor and MadMxShell. We hope that our research builds on the existing body of knowledge we also gained from others in identifying relationships within the malware distribution landscape, and specifically via malvertising.
Protection
Malicious ads that are found are usually reported within minutes via a tracking spreadsheet. We protect our customers by blocking infrastructure we find during our investigations, whether it is already involved in active malware distribution or is likely to be.
ThreatDown customers have web protection that already blocks the malicious domains used in this campaign. They can also be more aggressive by disabling online ads if they want to, thanks to our DNS Filtering option. Malware detection comes from our anti-malware engines enhanced by our EDR technology and MDR service.
Indicators of Compromise
Malicious domains
advanc3d-1p-scan[.]com
advanc3d-1p-scans[.]com
advanc3d-1p-scann[.]com
advanc3d-1p-scanne[.]com
angry1pscan3r[.]com
angry1pscaner[.]com
angry1pscane[.]com
angry1pscat[.]com
angry1pscan[.]com
advanc3d-lp-scaner[.]com
advanc3d-lp-scanner[.]com
advanc3d-1p-scan3r[.]com
advanc3d-1p-scaner[.]com
advanc3d-ip-scanner[.]com
advanc3d-1p-scanner[.]com
angryipscat[.]tech
angryipscat[.]online
angryipscat[.]org
angryipscat[.]com
angryipscat[.]net
angryipscar[.]com
angryipsca[.]org
angryipscap[.]com
angryipscann[.]com
angryipsca[.]com
timedoct0r[.]com
clockifpy[.]com
clockiify[.]com
clockifry[.]com
anscan[.]org
clockify[.]space
clockify[.]site
angryips[.]org
angryipo[.]org
getstorege[.]com
odvanced-ip-scanner[.]com
timedoctor[.]space
timedoctors[.]site
kwzain[.]space
timedoctors[.]space
timedoctors[.]online
MadMxShell
2481ac76f08d691166a425a01cdf1ec8ab5e2fbdf451c1bfc3edcba3e4c482e5 (ZIP) 93962847285d6f81273132e72d66b03a2e6e1a0ff46893e58ad3747762548922 (DLL) 70bc544b5467da13db64b55c0102d821e66454985fea7e77674af53e2364c8ae (ZIP) 4a36a35aac6e37959e2337bb74ab9830c5f6c6965da6bb5112d4195350e8baf9 (DLL) 40acc736c093ddce187552a653c2fd10ff5df0b45b93ad257901e7593bcee215 (ZIP) 24bff1753a60215bab00386ea11e774f0a04e2e45e70dabb122b5a697b67d174 (DLL)
WorkersDevBackdoor
55d1a76e4ed7d6ed0018c8129d631a637b591e18e52128dbe891a4382564793b
a8b0e013bd0d350035f12fd6703f7760a87cb218803e68c0eb482753961f2a41
2264d2a23f365af0830b577360a724798a6132b1a2f4cd08a7ccfaa311ee920a
Dropbox URLs
dropbox[.]com/scl/fi/z6tdyz5n9hon8ae5nihzt/ipscan-3[.]9[.]1-setup[.]exe
dropbox[.]com/scl/fi/q1xoadn14acxg4wqf5k7s/ipscan-3[.]9[.]1-setup[.]exe
dropbox[.]com/scl/fi/eghhcp5hi7y22ok662mud/ipscan-3[.]9[.]1-setup[.]exe
dropbox[.]com/scl/fi/0om3wuhw9cqfip7gez6il/ipscan-3[.]9[.]1-setup[.]exe
dropbox[.]com/scl/fi/cnbw5pd6kgw8cjmod7yru/ipscan-3[.]9[.]1-setup[.]exe
C2
getstorege[.]com