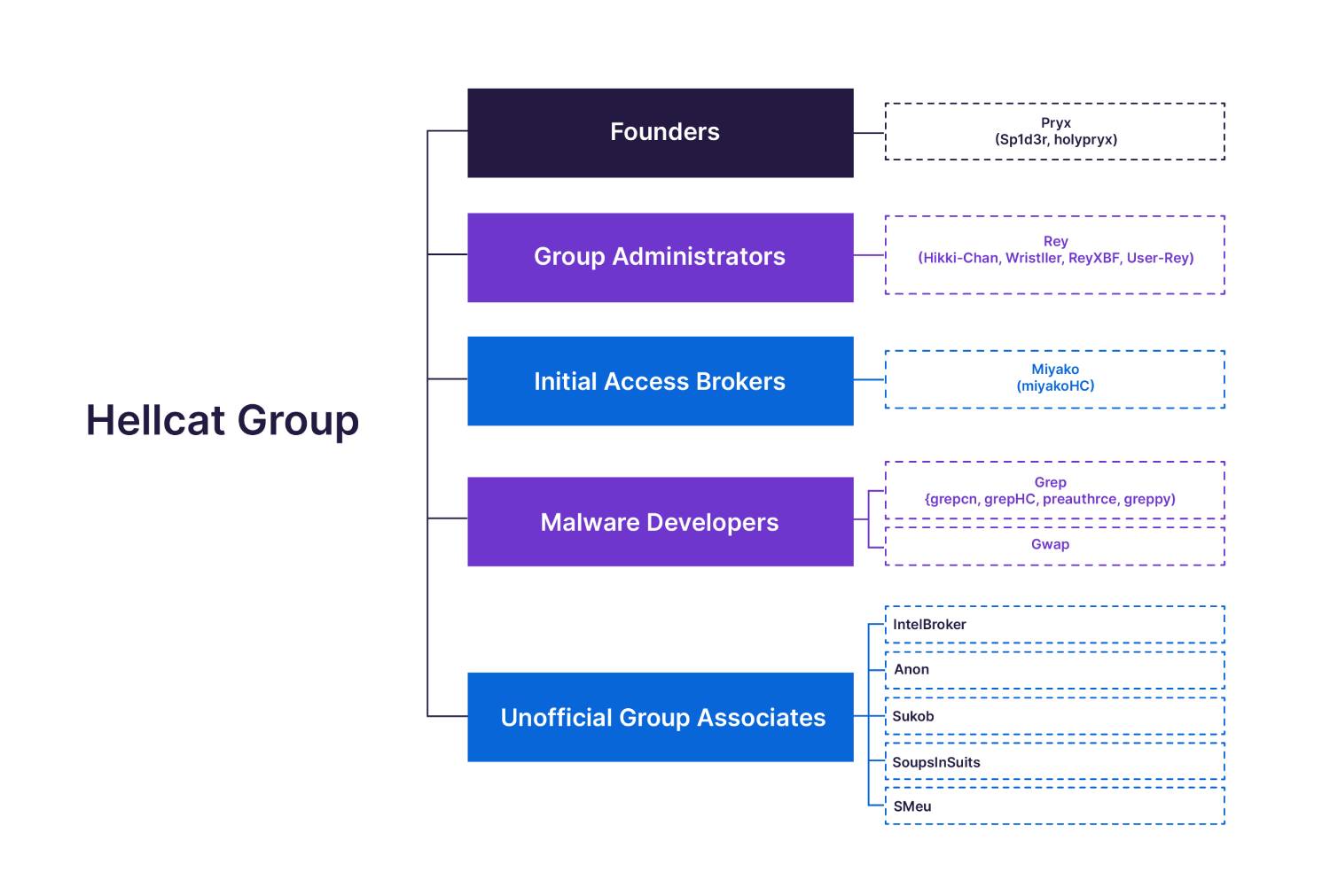
The Hellcat Ransomware Group is a newly identified Ransomware-as-a-Service (RaaS) threat group, recognized for targeting various organizations, especially in telecommunications and government sectors. Their operations reveal sophisticated tactics, including phishing, exploitation of public-facing applications, and deployment of PowerShell for maintaining persistence. The group has shown strong ties with other ransomware actors and employs unique methods for data exfiltration. Affected: telecommunications, government, information technology, healthcare, emergency services
Keypoints :
- Emergence of the Hellcat Ransomware Group identified in Q4 2024.
- Targets include telecommunications and government entities, notably Knesset and Schnieder Electric.
- Utilizes phishing and exploitation of public-facing applications for initial access.
- Employs PowerShell infection chains for persistence and command-and-control.
- Utilizes SliverC2 malware for establishing command-and-control channels.
- Involvement in exploit discussions on hacker forums related to CVE vulnerabilities.
- Evidence of collaboration with other ransomware groups, including similarities in encryptor payloads.
- Strong operational security measures highlighted, using secure communication tools and environments.
- Ransom notes exhibit characteristics similar to other ransomware groups, suggesting possible collaboration.
- Custom ransomware payloads utilized for encrypting victims’ data.
MITRE Techniques :
- T1190: Exploit Public-Facing Application – Hellcat exploits vulnerabilities in public-facing assets.
- T1566: Phishing – Initial access achieved through spearphishing emails.
- T1562.001: Impair Defenses: Disable or Modify Tools – Bypass techniques using AMSI performed by the “isma.ps1” script.
- T1620: Reflective Code Loading – Utilized by “shellcode.ps1” to load SliverC2 malware.
- T1071.001: Application Layer Protocol: Web Protocols – Used for command and control communications with SliverC2.
- T1071.002: Application Layer Protocol: File Transfer Protocols – SFTP used for data exfiltration.
Indicator of Compromise :
- [IP Address] 45.200.148[.]157
- [IP Address] 185.247.224[.]8
- [Domain] pryx[.]pw
- [Email Address] h3llr4ns[@]onionmail[.]com
- [File Name] payload.ps1
Full Story: https://www.bridewell.com/insights/blogs/detail/who-are-hellcat-ransomware-group