This web content discusses a sophisticated steganographic malware campaign involving various stealer malware such as Remcos and AsyncRAT. The campaign employs multiple stages of infection beginning with a phishing email containing an exploit that leads to the downloading of malicious payloads. It emphasizes the need for robust cybersecurity practices to protect against such advanced threats. Affected: Remcos, AsyncRAT, phishing email users, cybersecurity sector
Keypoints :
- The steganographic campaign distributes multiple types of malware, including Remcos and AsyncRAT.
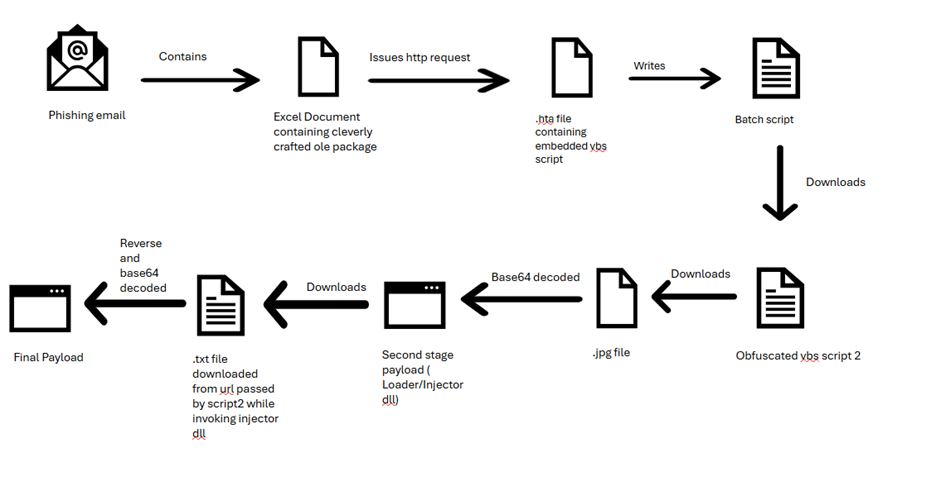
- The infection begins with a phishing email containing a malicious Excel file that exploits a vulnerability (CVE-2017-0199).
- The initial infection leads to downloading an HTA file, which contains VBS code to execute further malicious actions.
- Both Remcos and AsyncRAT are designed to steal information and maintain remote access on infected systems.
- The malware uses masquerading techniques to disguise malicious scripts as legitimate processes.
- Final payloads are injected into clean processes through process hollowing, which adds complexity to detection efforts.
- The campaign highlights the importance of vigilance and cybersecurity measures against advanced malware tactics.
MITRE Techniques :
- Initial Access (T1566) – Phishing emails are used to gain initial access.
- Execution (T1204) – User execution of the malicious Excel file triggers the infection chain.
- Persistence (T1547.001) – The malware utilizes registry run keys and startup folder to maintain persistence.
- Defense Evasion (T1055) – Process injection is utilized to evade detection.
- Defense Evasion (T1027) – The malware employs obfuscated files to hide its presence.
- Defense Evasion (T1036.004) – Masquerading techniques are applied to disguise malware as legitimate tasks or services.
- Discovery (T1614) – The malware discovers system locations for further exploitation.
- Exfiltration (T1041) – Malware exfiltrates data over command-and-control channels.
- Command and Control (T1001.0012) – Steganography is used for command and control communications.
Indicator of Compromise :
- [SHA-256] 9d66405aebff0080cc5d28a1684d501fa7e183dc8b6340475fc06845509cb466
- [SHA-256] 42813b301da721c34ca1aca29ce2e4c7d71ae580b519a3332a4ba71870b6a58e
- [SHA-256] f67c6341bfe37f5b05c00a0dda738f472fdabd6ea94ca8dc761f57f11ce12036
- [Domain] interestedthingsforkissinggirlwithloves[.]duckdns[.]org
- [C2 IP] 148[.]113[.]214[.]176
Full Story: https://www.seqrite.com/blog/steganographic-campaign-distributing-malware/