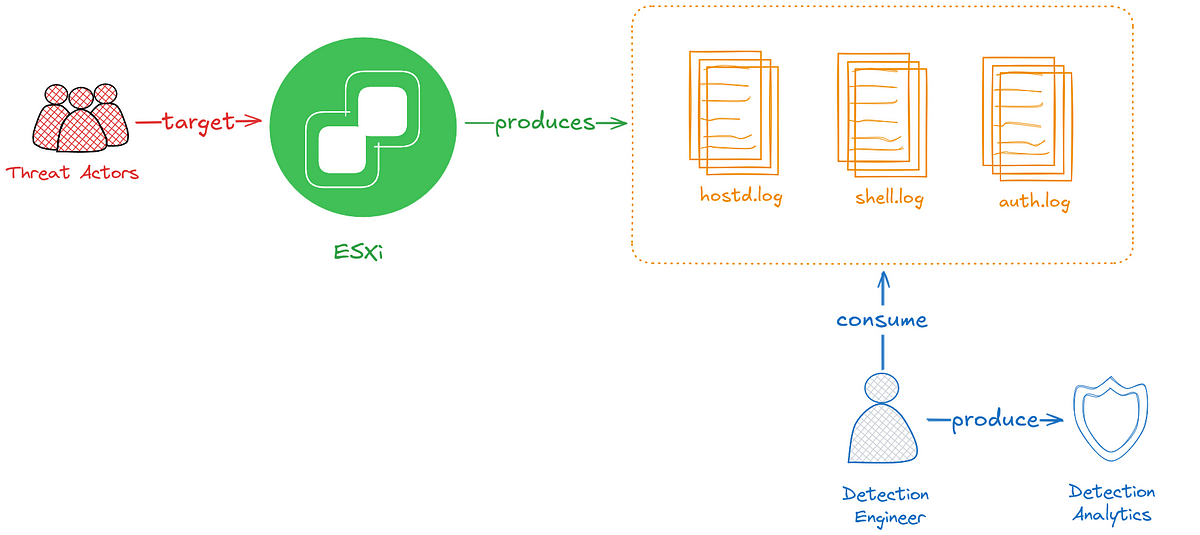
This article discusses the unique challenges faced by Detection Engineers in securing ESXi environments, which often lack adequate security controls. It highlights the importance of effective log sources, common adversary techniques, and provides a Python-based CLI tool for automating detection tasks. Affected: ESXi
Keypoints :
- ESXi environments are often considered legacy and may lack effective maintenance and security controls.
- Numerous ransomware variants target ESXi systems, indicating a growing threat landscape.
- Important log sources include /var/log/shell.log, /var/log/auth.log, and /var/log/hostd.log.
- Shell events are logged in shell.log, but commands executed via SSH may not appear there.
- ESXi systems expose an undocumented API that can perform various administrative tasks.
- Built-in utilities like esxcli and vim-cmd can be abused by threat actors.
- Detection strategies should focus on API logs in hostd.log for comprehensive coverage.
- Automated detection tools, such as the ESXi Testing Toolkit, can simplify the detection engineering process.
MITRE Techniques :
- T1021.004 – Remote Services: SSH – Adversaries may use SSH to access ESXi hosts and execute commands.
- T1562.001 – Impair Defenses: Disable or modify security controls like firewalls using esxcli or SOAP API.
- T1485 – Data Destruction: Deleting VM snapshots can hinder recovery efforts during a ransomware attack.
- T1529 – System Shutdown/Reboot: Adversaries may power off VMs to facilitate their attacks.
Indicator of Compromise :
- [url] https://ESXI_IP_ADDRESS
- [domain] vmware.com
- [tool name] esxcli
- [tool name] vim-cmd
- Check the article for all found IoCs.
Full Research: https://detect.fyi/vmware-esxi-logging-detection-opportunities-4fb56411ec21?source=rss——cybersecurity-5