The WIRTE APT group has been active since 2018, primarily targeting organizations in the Middle East and Europe, including government and financial sectors. Recent activities have focused on Middle Eastern entities, utilizing custom loaders like IronWind. A comprehensive analysis revealed 56 indicators of compromise (IoCs) and additional artifacts, highlighting the group’s ongoing threat. Affected: WIRTE APT group, Palestinian Authority, Jordan, Egypt, Saudi Arabia
Keypoints :
- WIRTE APT group has been active since August 2018.
- Targets include government, diplomatic, financial, military, legal, and technology organizations.
- Recent focus on Middle Eastern entities, particularly the Palestinian Authority, Jordan, Egypt, and Saudi Arabia.
- Utilizes custom loaders like IronWind in attacks.
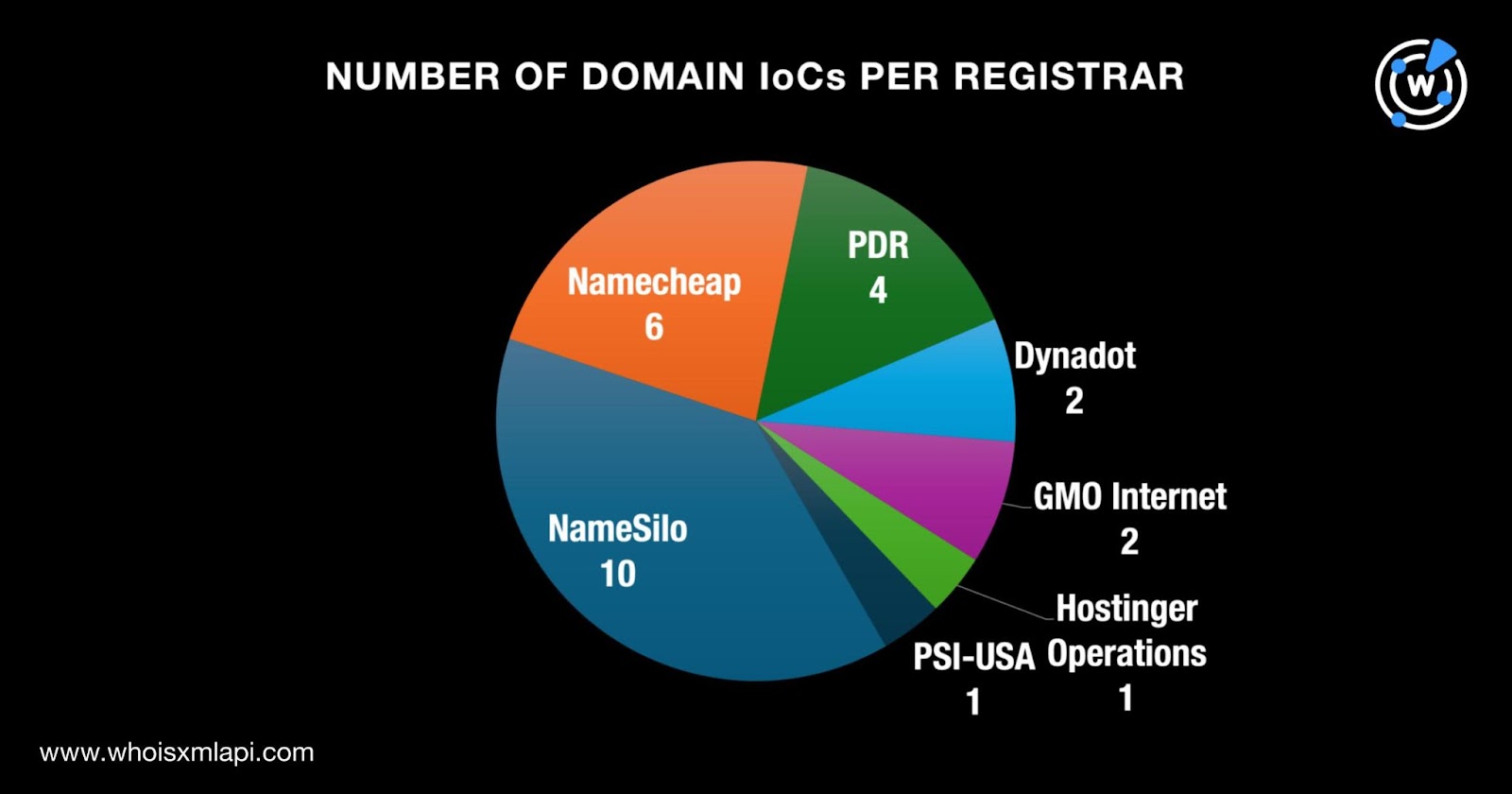
- Check Point Research identified 56 IoCs including 30 domains and 23 IP addresses.
- WhoisXML API expanded the IoC list to include 360 email-connected domains and 36 additional IP addresses.
- Domains were registered between 2022 and 2024, with the majority in the U.S.
- Historical WHOIS records revealed 88 email addresses linked to the IoCs.
- Research findings and artifacts are available for download on the website.
MITRE Techniques :
- Initial Access (T1071) – The group uses custom loaders to gain initial access to targeted systems.
- Command and Control (T1071) – Utilizes various domains and IP addresses for command and control operations.
- Data Exfiltration (T1041) – Engages in data exfiltration through compromised domains and email addresses.
Indicator of Compromise :
- [domain] ainiaiwo2025[.]com
- [domain] gagatour2025[.]com
- [domain] vegaskickoffclassic2025[.]com
- [ip address] 185[.]158[.]248[.]161
- [ip address] 213[.]252[.]244[.]234
- Check the article for all found IoCs.
Full Research: https://circleid.com/posts/tracking-down-apt-group-wirtes-dns-movements