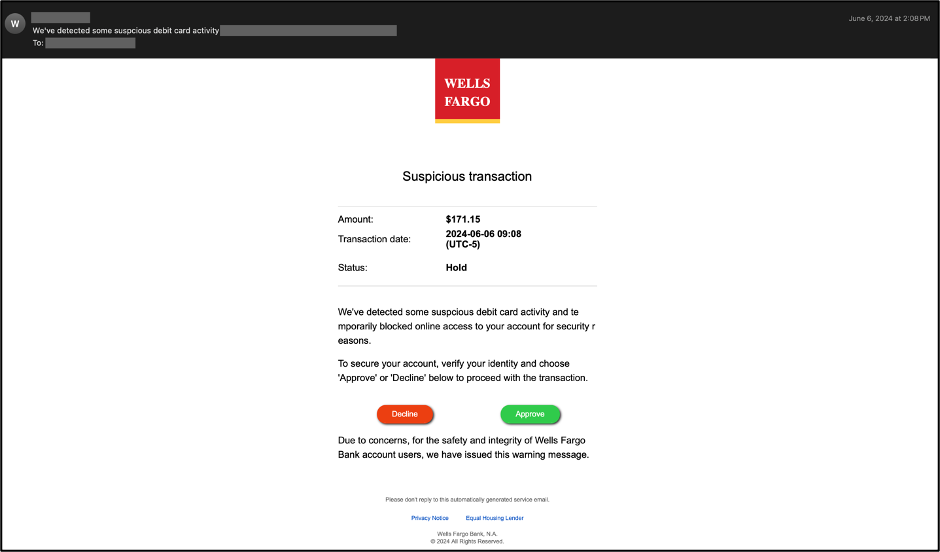
Cisco Talos has reported a notable rise in email threats utilizing hidden text salting, a technique that allows attackers to bypass detection systems by embedding invisible characters in emails. This method complicates the work of email parsers and spam filters, making it easier for phishing attempts to succeed. Affected: Email Threat Detection Systems, Phishing Detection Mechanisms
Keypoints :
- Hidden text salting is a technique used by threat actors to evade email detection systems.
- This method involves inserting invisible characters into the HTML source of emails.
- It can confuse spam filters and language detection procedures.
- Examples include phishing emails impersonating brands like Wells Fargo and Norton LifeLock.
- Mitigation strategies include advanced filtering techniques and reliance on visual features of emails.
- AI-powered email security solutions are essential for detecting and protecting against these threats.
MITRE Techniques :
- Phishing (T1566) – Threat actors use hidden text salting to craft emails that impersonate legitimate brands.
- HTML Smuggling (T1071.001) – Inserting irrelevant comments in base64-encoded HTML attachments to evade detection.
- Content Spoofing (T1071.001) – Utilizing invisible characters to confuse language detection and spam filters.
Indicator of Compromise :
- [email] phishing@example.com
- [url] www[.]wellsfargo[.]com
- [url] www[.]nortonlifelock[.]com
- [file name] malicious_email.html
- [others ioc] Zero-Width Space (ZWSP), Zero-Width Non-Joiner (ZWNJ)
- Check the article for all found IoCs.
Full Research: https://blog.talosintelligence.com/seasoning-email-threats-with-hidden-text-salting/