This article discusses a malicious URL that exploits vulnerable PHP servers to download and execute malware, specifically targeting systems to mine cryptocurrency. The investigation reveals the use of various executables and their interactions, highlighting the importance of securing PHP servers against such attacks. Affected Platform: PHP servers
Keypoints :
- The SANS DShield project collects logs from various participants.
- An interesting URL was identified that exploits PHP servers.
- The URL executes a command to download a secondary payload named dr0p.exe.
- dr0p.exe retrieves another file, pkt1.exe, from a specific IP address.
- pkt1.exe further spawns packetcrypt.exe, which is involved in cryptocurrency mining.
- The mining activity is linked to a specific PKTC wallet address.
- Vulnerabilities in PHP servers, such as CVE-2024-4577, are exploited in this attack.
- System owners are reminded to patch and audit their PHP servers regularly.
MITRE Techniques :
- T1071.001 – Application Layer Protocol: Web Protocols – The malware uses HTTP to download executables.
- T1203 – Exploitation for Client Execution – The attack exploits vulnerabilities in PHP servers.
- T1486 – Data Encrypted for Impact – The malware may encrypt data for mining purposes.
Indicator of Compromise :
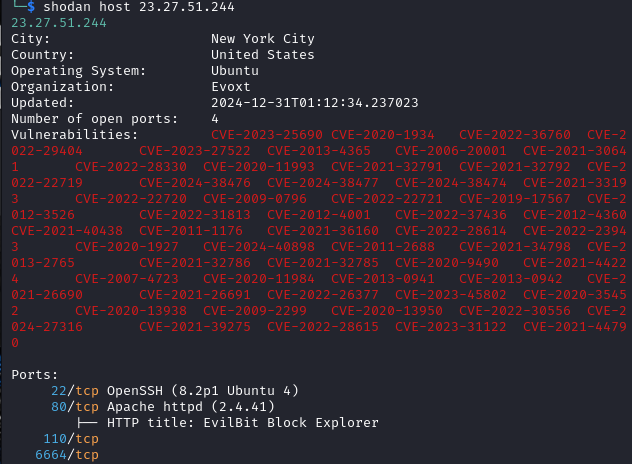
- [IP address] 23.27.51.244
- [file hash] d078d8690446e831acc794ee2df5dfabcc5299493e7198993149e3c0c33ccb36
- [file hash] e3d0c31608917c0d7184c220d2510848f6267952c38f86926b15fb53d07bd562
- [file hash] 717fe92a00ab25cae8a46265293e3d1f25b2326ecd31406e7a2821853c64d397
- [others] pkt1qxysc58g4cwwautg6dr4p7q7sd6tn2ldgukth5a
- Check the article for all found IoCs.
Full Research: https://isc.sans.edu/diary/rss/31564