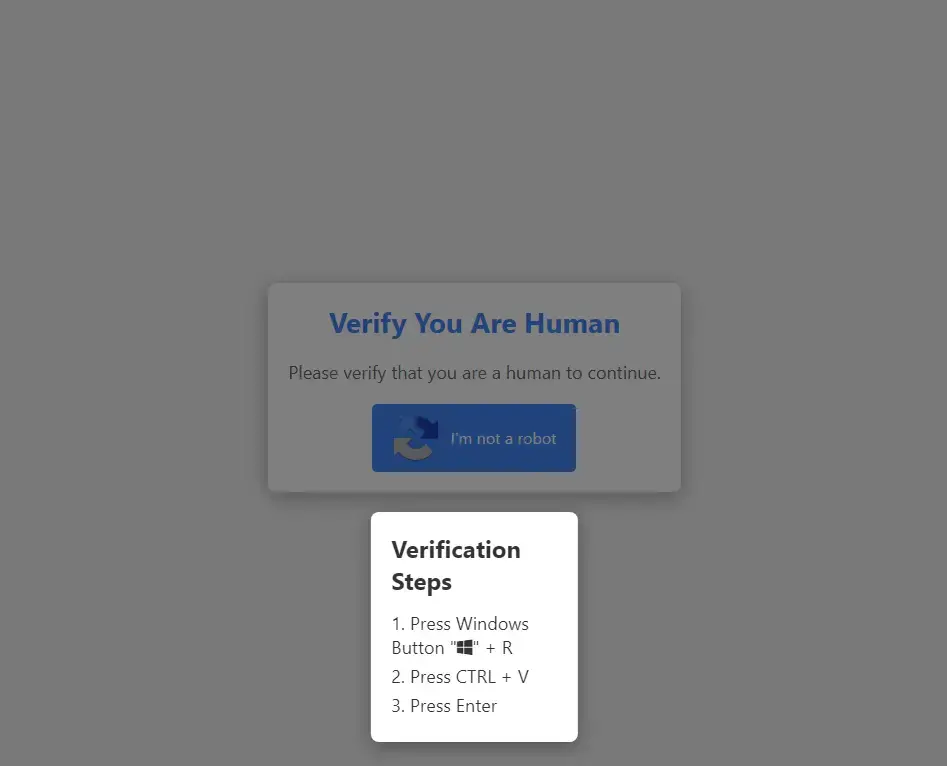
Summary: AhnLab Security Intelligence Center (ASEC) has identified a new distribution method for the LummaC2 malware that uses a fake CAPTCHA verification page to deceive users. This tactic tricks victims into executing harmful scripts by presenting a false authentication step that copies malicious commands to their clipboard. The malware targets sensitive information, including browser credentials and cryptocurrency wallets, while employing techniques to redirect cryptocurrency transfers to the attackers’ accounts.
Threat Actor: LummaC2 Group | LummaC2
Victim: Users of crack program download pages and phishing emails | users of crack program download pages and phishing emails
Keypoints :
- Malicious campaign uses a fake CAPTCHA page to trick users into executing harmful scripts.
- The initial payload is disguised as an HTA file, making detection difficult.
- LummaC2 malware targets sensitive data and redirects cryptocurrency transfers to the attackers’ wallets.
Source: https://securityonline.info/lummac2-infostealer-malware-spreads-via-crack-programs-and-phishing/