Short Summary:
The UTA0137 cyber espionage group, linked to Pakistani hackers, has employed a new malware called DISGOMOJI, disguised as emojis, to target Indian organizations. Volexity’s analysis revealed numerous indicators of compromise (IoCs) and additional threat artifacts related to this attack.
Key Points:
- UTA0137 is a cyber espionage group believed to be affiliated with Pakistani hackers.
- DISGOMOJI is a malware written in Golang, disguised as emojis.
- The attack primarily targets Indian organizations.
- Volexity disclosed 24 IoCs, including 19 domains and five IP addresses.
- Additional artifacts included five email-connected domains and eight malicious IP addresses.
- Most IoCs were registered between 2023 and 2024, with a majority administered by Namecheap, Inc.
- The U.S. was the top registrant country for the IoCs, followed by Iceland and Pakistan.
- Further analysis revealed connections between the IoCs and additional malicious domains and IP addresses.
MITRE ATT&CK TTPs – created by AI
- Initial Access – T1071.001
- Utilization of newly registered domains (NRDs) to facilitate initial access.
- Command and Control – T1071
- Malware communicates through DNS queries to resolve domains.
- Exfiltration – T1041
- Possible data exfiltration through the established command and control channels.
Cyber espionage is not uncommon and often occurs between rivals. And though the cyber attackers’ tactics and techniques remain the same, their tools do not. The latest UTA0137 attack, for example, has taken to using DISGOMOJI, a malware written in Golang and disguised as various emojis to infiltrate target Indian organizations. UTA0137 is a threat group believed to be affiliated with Pakistani hackers. The malware, meanwhile, also has ties to an attack instigated by Transparent Tribe, a Pakistan-nexus hacking crew.
Volexity analyzed the cyber attack and disclosed 24 indicators of compromise (IoCs) comprising 19 domains and five IP addresses on 13 June 2024. The WhoisXML API research team expanded the current list of IoCs and found other potentially connected threat artifacts, including:
- Five email-connected domains
- Eight additional IP addresses, all of which turned out to be malicious
- 320 IP-connected domains
- 31 string-connected domains
A sample of the additional artifacts obtained from our analysis is available for download from our website.
More about the DISGOMOJI IoCs
The DNS can always give more information about IoCs based on their WHOIS and DNS records. We began our DNS investigation with a bulk WHOIS lookup for the 19 domains tagged as IoCs. Our query allowed us to determine that:
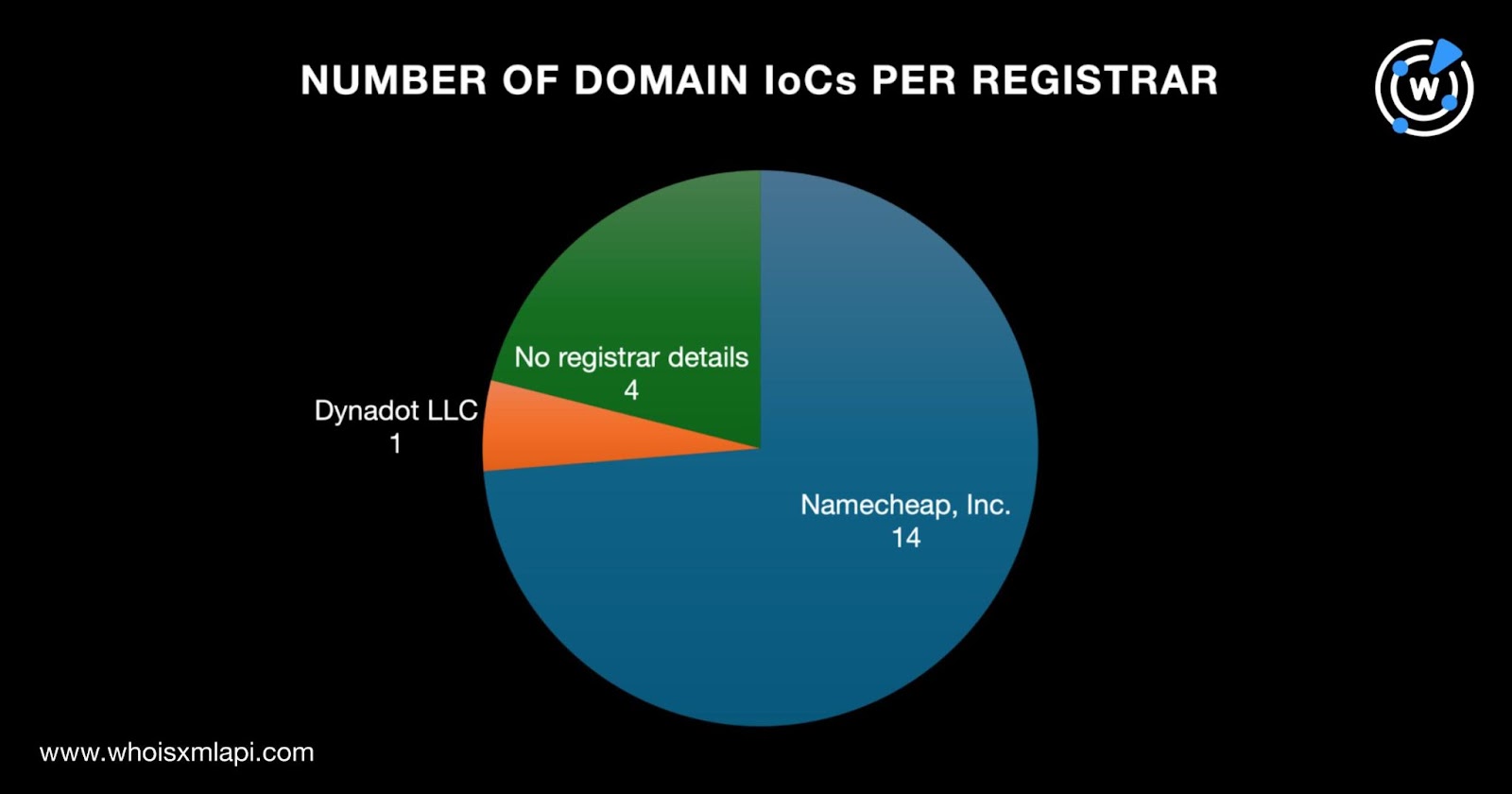
- A huge majority of the domain IoCs, 14 to be exact, were administered by Namecheap, Inc. One fell under the purview of Dynadot LLC. Four, however, did not have registrars in their current WHOIS records.
- The UTA0137 threat actors seemed to favor using newly registered domains (NRDs) for this particular attack, given that the domain IoCs were only created between 2023 and 2024. Note, though, that four of the IoCs did not have creation dates in their current WHOIS records and so might be inactive.
-
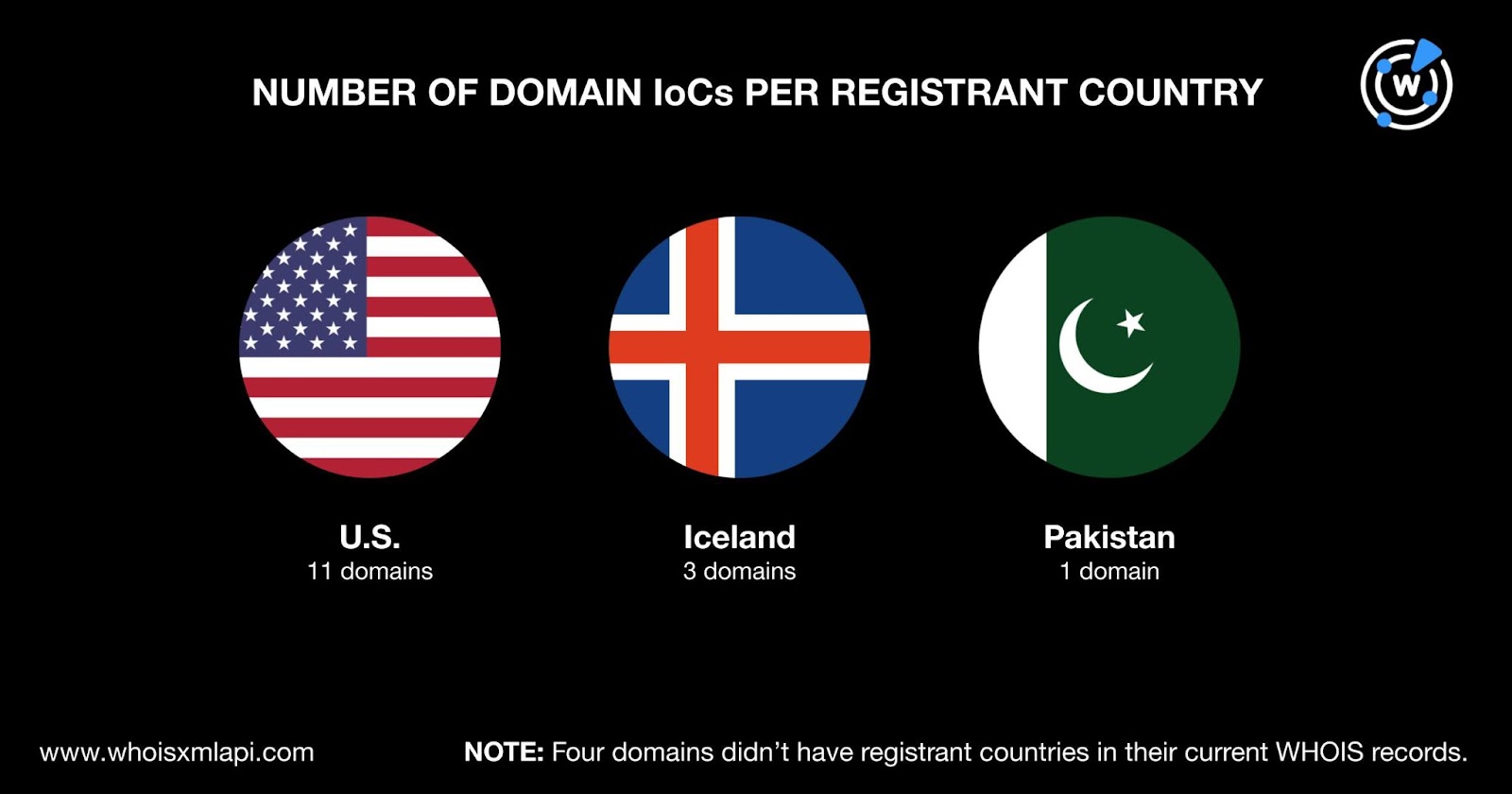
The U.S. topped the list of registrant countries, accounting for 11 of the domain IoCs. Iceland followed with three IoCs. Pakistan completed the list of registrant countries with one IoC. Note that four domain IoCs did not have registrant countries in their current WHOIS records.
Next, we performed a bulk IP geolocation lookup for the five IP addresses tagged as IoCs. We found out that:
Other DISGOMOJI DNS Facts
After obtaining more information about the IoCs, we proceeded with looking for potentially connected DISGOMOJI artifacts.
We began by searching for email-connected domains. We ran WHOIS History API queries for the 19 domains tagged as IoCs, which allowed us to gather two email addresses from their historical WHOIS records. One of them was public.
A Reverse WHOIS API query for the public email address uncovered five email-connected domains after duplicates and the IoCs were filtered out.
Next, we sought out IP-connected domains. We began by running DNS lookups for the 19 domains tagged as IoCs. We found out that they resolved to eight unique IP addresses, which all turned out to be malicious according to Threat Intelligence Lookup.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Source: Original Post
