Endpoint Detection and Response (EDR) solutions are crucial for modern cybersecurity, enabling quick threat detection and response through extensive telemetry. However, attackers utilize various evasion techniques to bypass these systems, exploiting vulnerabilities in EDR architecture and Windows core files. This guide provides insights into EDR monitoring, evasion methods, and defensive strategies. Affected: EDR solutions, Windows operating system
Keypoints :
- EDR solutions gather telemetry data to detect and respond to threats.
- Attackers employ evasion techniques to exploit vulnerabilities in EDRs.
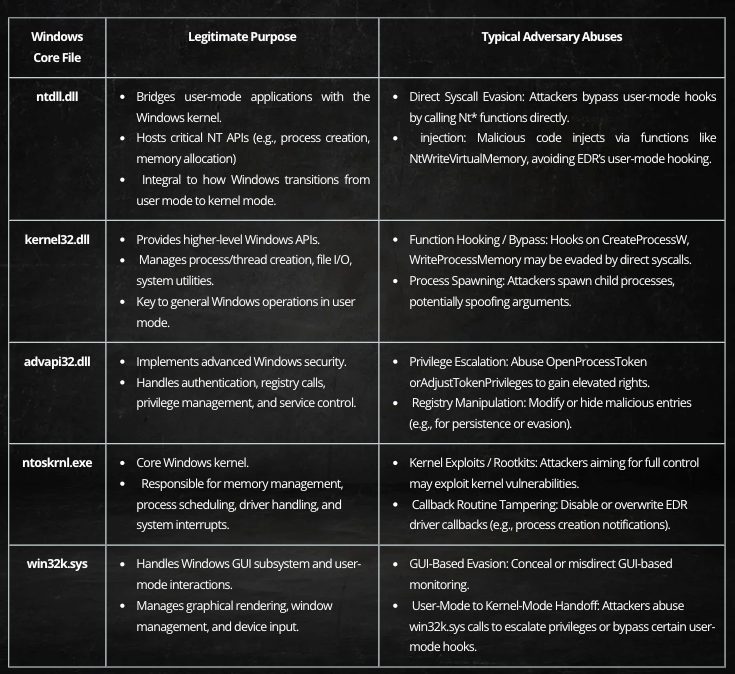
- Key Windows core files essential for EDR monitoring include ntdll.dll, kernel32.dll, advapi32.dll, ntoskrnl.exe, and win32k.sys.
- EDR architecture involves local sensors, centralized analysis, and response mechanisms.
- Practical evasion techniques include function hooking bypass, process creation manipulation, and network traffic evasion.
- Understanding evasion methods helps enhance EDR defenses and threat detection.
MITRE Techniques :
- T1055 – Process Injection: Utilizing direct syscalls to bypass user-mode hooks.
- T1562.001 – Disable or Modify Tools (AMSI/ETW): Techniques for neutralizing AMSI and ETW detection features.
- T1027 – Obfuscated Files or Information: Using encoded or encrypted scripts to avoid detection.
- T1599 – Network Boundary Bridging: Evasion tactics over well-known ports or domain fronting.
Indicator of Compromise :
- No IoC found
Full Research: https://snailsploit.medium.com/evading-endpoint-detection-and-response-edr-f18cf2da38ed?source=rss——cybersecurity-5