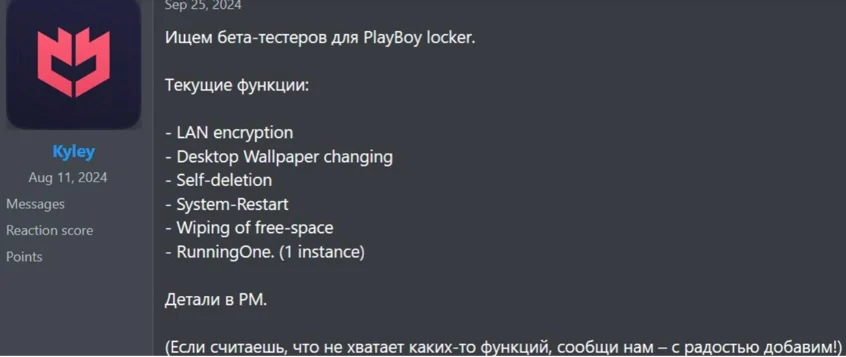
Cybereason’s Threat Analysis report discusses the emerging PlayBoy Locker Ransomware-as-a-Service (RaaS), detailing how it enables less-skilled cybercriminals to conduct ransomware attacks through a comprehensive toolkit. The platform provides affiliates with customized ransomware capabilities, regular updates, and customer support, thus representing a growing threat. Affected: Ransomware, Cybersecurity, Dark Web, Affiliates
Keypoints :
- PlayBoy Locker RaaS is designed for less-skilled attackers with a complete toolkit for launching ransomware attacks.
- Binary customization allows affiliates to tailor ransomware binaries for various systems like Windows, NAS, and ESXi.
- Operators provide regular updates and customer support, increasing the sophistication of attacks.
- The platform was launched in September 2024 and features a profit-sharing model for affiliate partners.
- Technical capabilities include advanced encryption, automated infections, and extensive process termination.
- PlayBoy Locker employs multithreading for efficient file encryption and deletion of shadow copies to hinder data recovery.
- Indicators of compromise (IOCs) include specific hashes associated with the ransomware.
- Recommendations for prevention include monitoring affiliate activities, promoting cybersecurity practices, and maintaining regular backups.
MITRE Techniques :
- Execution: T1047 – Windows Management Instrumentation
- Execution: T1106 – Native API
- Persistence: T1543.003 – Create or Modify System Process: Windows Service
- Discovery: T1083 – File and Directory Discovery
- Privilege Escalation: T1078.001 – Valid Accounts: Default Accounts
- Privilege Escalation: T1078.002 – Valid Accounts: Domain Accounts
- Discovery: T1135 – Network Share Discovery
- Discovery: T1016 – System Network Configuration Discovery
- Defense Evasion: T1406.002 – Obfuscated Files or Information: Software Packing
- Defense Evasion: T1620 – Reflective Code Loading
- Collection: T1119 – Automated Collection
- Impact: T1486 – Data Encrypted for Impact
- Impact: T1489 – Service Stop
- Impact: T1490 – Inhibit System Recovery
Indicator of Compromise :
- SHA-256 3030a048f05146b85c458bcabe97968e5efdd81b224b96c30c83b74365839e7b (PlayBoy Locker Windows Encryptor)
- SHA-256 a9e1bd8f9cbeeec64da558027f380195f7ed572f03830a890dd0494e64d98556 (PlayBoy Locker Windows Encryptor)
- SHA-256 a9e1bd8f9cbeeec64da558027f380195f7ed572f03830a890dd0494e64d98556 (PlayBoy Locker Windows Encryptor)
Full Story: https://www.cybereason.com/blog/threat-analysis-playboy-locker