This article discusses the effective use of the CyberChef tool for deobfuscating a .vbs loader associated with Nanocore malware. It outlines various methods, including regular expressions and mathematical operations, to simplify the analysis of obfuscated code. Affected: Nanocore malware, .vbs loader
Keypoints :
- CyberChef is a versatile tool for malware analysis and deobfuscation.
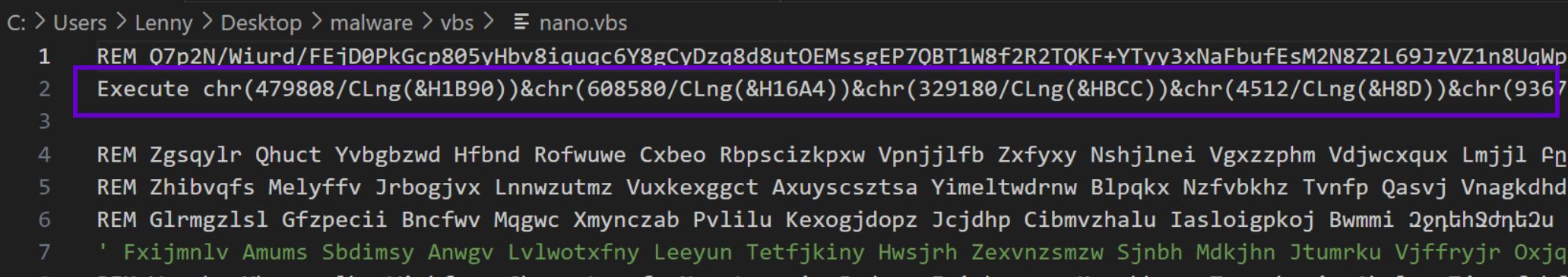
- The article focuses on a .vbs loader for Nanocore malware.
- Obfuscation techniques used include large decimal values, hexadecimal representations, and mathematical operations.
- Regular expressions are essential to isolate and manipulate obfuscated code segments.
- The deobfuscation process involves converting values and applying mathematical operations like addition and division.
- Final analysis reveals that the obfuscated code executes a PowerShell command to run a Nanocore payload.
- The original obfuscated content can be restored to access the final payload.
MITRE Techniques :
- Obfuscated Files or Information (T1027) – The malware uses obfuscation techniques to disguise its true intent and functionality by employing a vbs loader.
- Command and Control (T1071) – The obfuscated code ultimately allows execution of a PowerShell command that triggers the Nanocore payload.
Indicator of Compromise :
- [SHA256] c6092b1788722f82280d3dca79784556df6b8203f4d8f271c327582dd9dcf6e1