Cybereason Security Services has released a Threat Analysis report focusing on the Phorpiex botnet’s role in delivering LockBit Black Ransomware (LockBit 3.0). The report highlights unique automated execution methods used by threat actors and the minimal changes made to the Phorpiex codebase since its sale in 2021. Recommendations for protection against these threats are also provided. Affected: Phorpiex, LockBit
Keypoints :
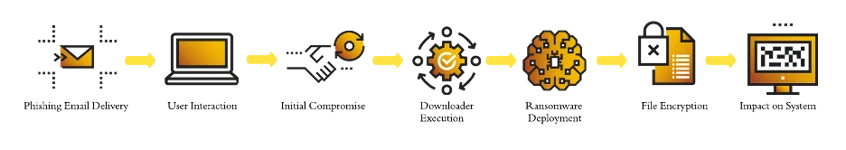
- Phorpiex botnet automates the delivery of LockBit ransomware.
- Minimal changes observed in Phorpiex’s codebase since its source code sale.
- LockBit downloader variant directly downloads ransomware without extensive network encryption.
- Phorpiex spreads through phishing emails with malicious attachments.
- LockBit is a significant threat, responsible for 30% of ransomware attacks as of 2023.
- Cybereason recommends enabling application control and anti-ransomware measures.
MITRE Techniques :
- TA0001: Initial Access – T1566.001 – Phishing: Spearphishing Attachment: Phorpiex arrives via phishing emails containing ZIP files with malware.
- TA0002: Execution – T1204.002 – User Execution: Malicious File: Users executing malicious files (.lnk, .scr) connect to C2 to download additional payloads.
- TA0003: Persistence – T1547.001 – Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder: Phorpiex variants manipulate the registry for automatic execution.
- TA0005: Defense Evasion – T1070.009 – Indicator Removal: Clear Persistence: Deletes Zone.Identifier files to remove traces of downloaded files.
- TA0005: Defense Evasion – T1562.001 – Impair Defenses: Disable or Modify Tools: Disables Windows Defender’s AntiSpyware feature.
- TA0005: Defense Evasion – T1027.002 – Obfuscated Files or Information: Uses obfuscation to evade detection.
- TA0005: Defense Evasion – T1497.001 – Virtualization/Sandbox Evasion: System Checks: Checks for virtualization to evade analysis.
- TA0011: Command and Control – T1071 – Application Layer Protocol: Communicates with C2 for downloading additional payloads.
Indicator of Compromise :
- [Domain] twizt[.]net
- [IP Address] 193.233.132[.]177
- [SHA-256] a861d931cbeb1541193c8707a7114e21daf4ad6d45099427b99a9d0982d976ae
- [SHA-256] 05ca9f97a27b675d24edf621b716159ddebff4f16f70b15b2ca68fc7203308b7
- [SHA-256] 01cd4320fa28bc47325ccbbce573ed5c5356008ab0dd1f450017e042cb631239
- Check the article for all found IoCs.
Full Research: https://www.cybereason.com/blog/threat-analysis-phorpiex-downloader