Summary:
Keypoints:
MITRE Techniques
11/11/2024
A week after the previous wave of attacks, the Vidar malware has returned to menace Italian email users by exploiting, once again, compromised PEC mailboxes.
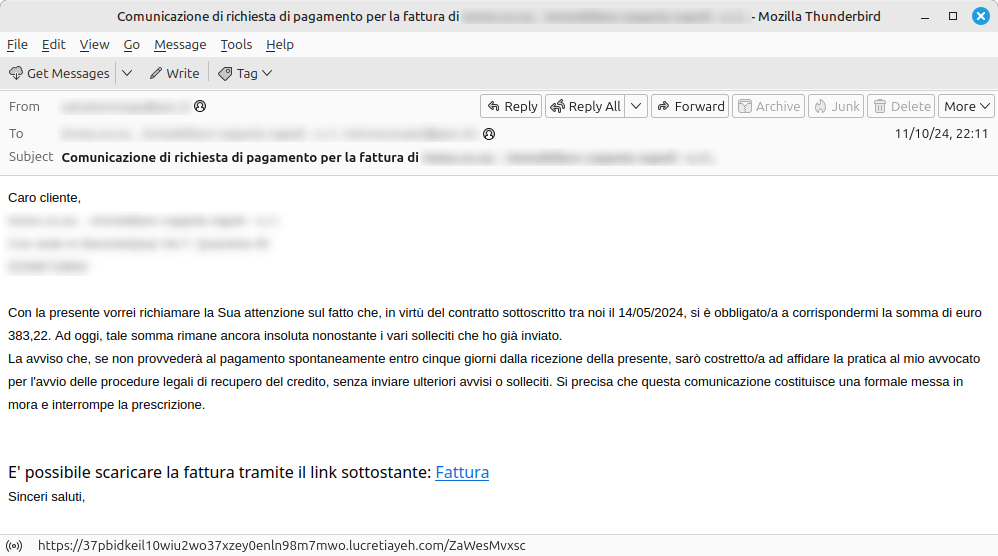
This new campaign replicates the methods already observed in the previous activity, which was notable for the use of a VBS payload instead of the more common JS files. The distribution techniques remain unchanged, with similar templates for the PEC messages and a persistent abuse of .top domains. However, the reference URLs for downloading the components have been updated, suggesting that the campaign’s authors intend to evade detection systems and prolong the effectiveness of its distribution.
Vidar, known for its ability to steal access credentials and sensitive data, once again confirms its adaptability and danger, especially considering that the technique of delivery via compromised PEC mailboxes can more easily lead recipients to trust the messages received.
Countermeasures
Countermeasures have already been implemented with the support of PEC managers. The IoCs related to the campaign have been disseminated through the IoC Feed of CERT-AGID to the PEC managers and accredited structures.
It is recommended to always pay close attention to communications received via PEC, particularly when they contain links deemed suspicious. When in doubt, it is always possible to forward suspicious emails to the email address malware@cert-agid.gov.it
Indicators of Compromise
In order to make the details of today’s campaign public, the detected IoCs are listed below:
Link: Download IoC
Source: Original Post