In this blog entry, we’d like to highlight our findings on Vice Society, which includes an end-to-end infection diagram that we were able to create using Trend Micro internal telemetry.
Updated on January 26, 2023 to remove references to Kape Tool and to remove Trend Micro Apex One from the list of programs that the ransomware disables.
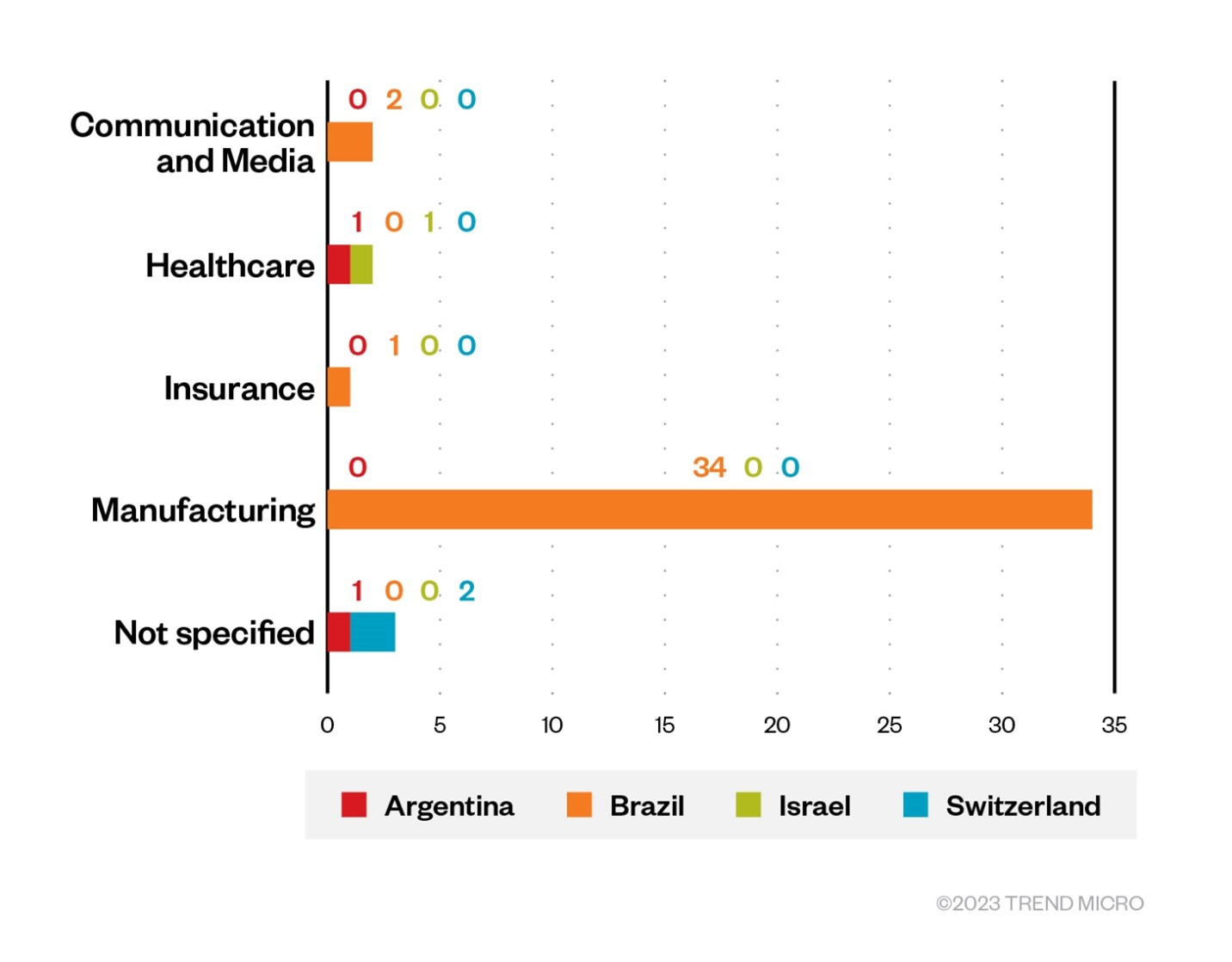
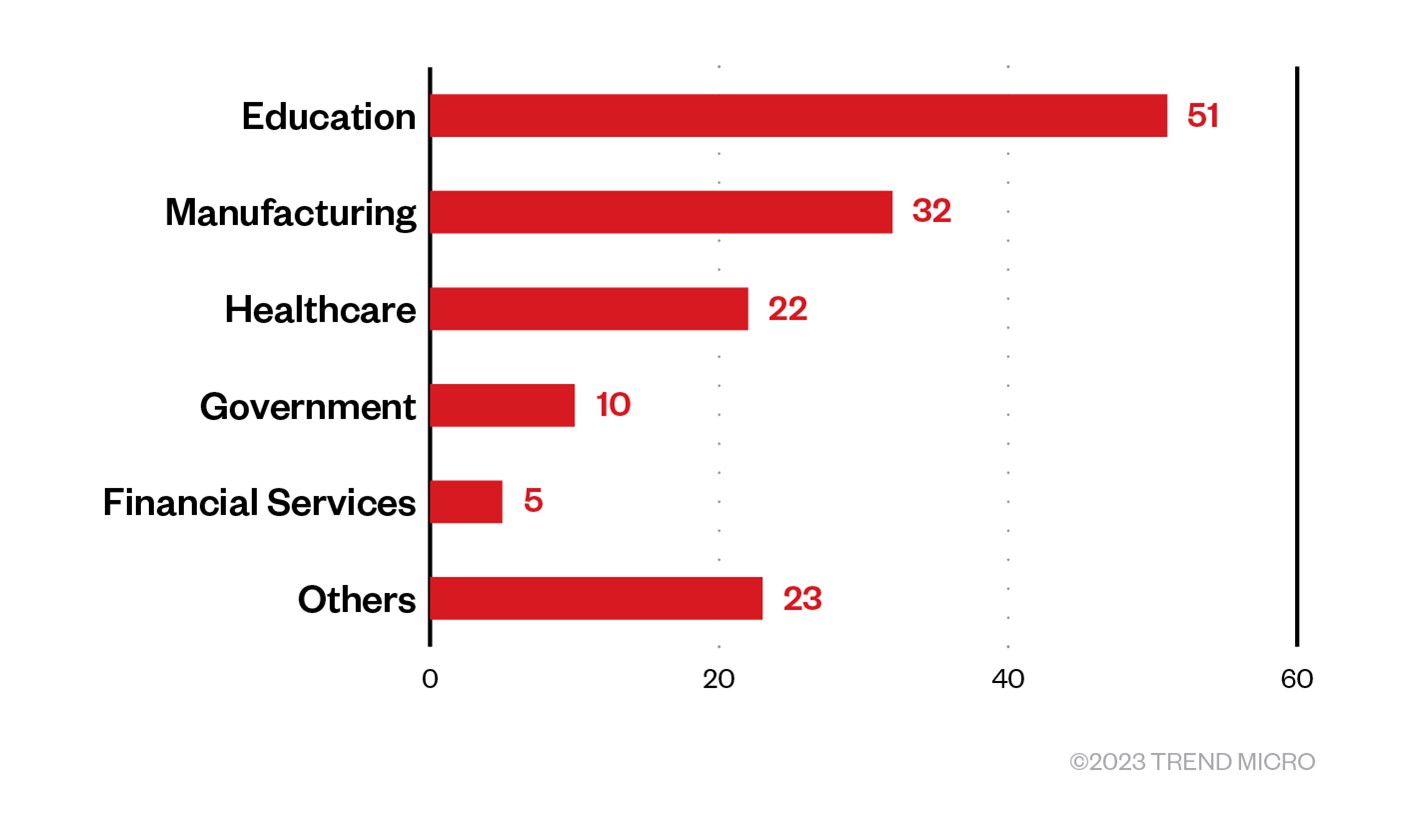
The Vice Society ransomware group made headlines in late 2022 and early 2023 during a spate of attacks against several targets, such as the one that affected the rapid transit system in San Francisco. Most reports have the threat actor focusing its efforts on the education and the healthcare industries. However, through Trend Micro’s telemetry data, we have evidence that the group is also targeting the manufacturing sector, which means that they have capability and desire to penetrate different industries — most likely accomplished via the purchasing of compromised credentials from underground channels. We have detected the presence of Vice Society in Brazil (primarily affecting the country’s manufacturing industry), Argentina, Switzerland, and Israel.
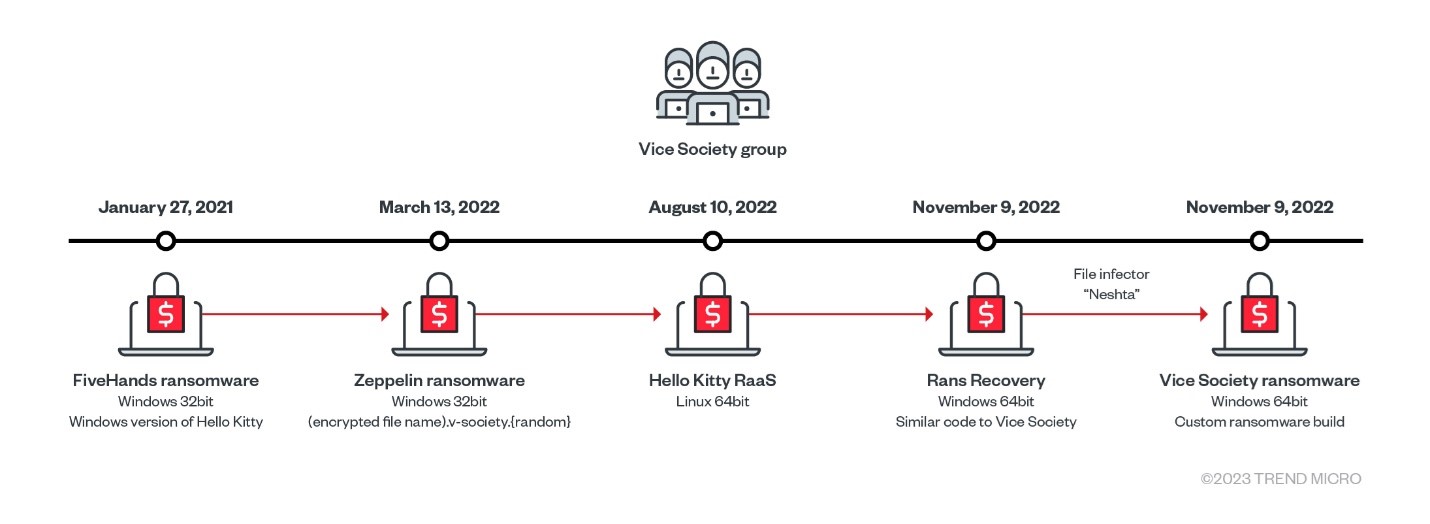
Vice Society, which was initially reported to be exploiting the PrintNightmare vulnerability in their routines, have previously deployed ransomware variants such as Hello Kitty/Five Hands and Zeppelin (the group’s email has been in their ransom notes). More recently, Vice Society has been able to develop its own custom ransomware builder and adopt more robust encryption methods. This, and any further enhancements, could mean that the group is preparing for their own ransomware-as-a-service (RaaS) operation.
In this blog entry, we’d like to highlight our findings on Vice Society, which includes an end-to-end infection diagram that we were able to create using Trend Micro internal telemetry. Our detection name for this variant of Vice Society’s ransomware is Ransom.Win64.VICESOCIETY.A .
Technical analysis and infection flow
Based on our internal telemetry, we were able to create infection diagram for a Vice Society ransomware attack (illustrated in Figure 4). The arrival vector likely involves the exploitation of a public-facing website or abuse of compromised remote desktop protocol (RDP) credentials.
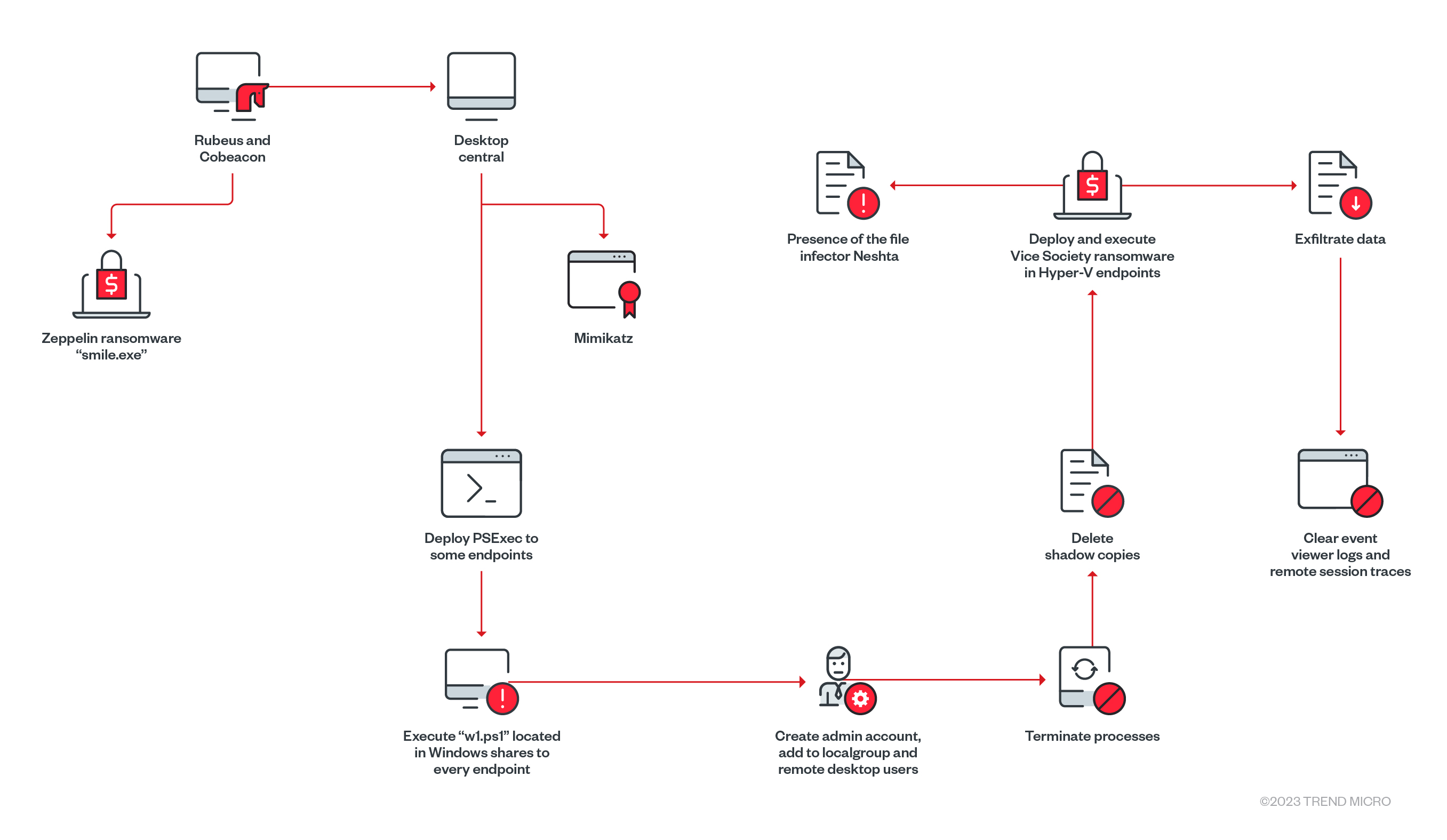
The following table shows what we were able to observe from a Vice Society attack. Note that all endpoints indicated belong to one Pointer to the GUID.
Date | Description |
October 28, 2022 | Possible entry point using Cobalt Strike and the Rubeus hacktool Cobalt Strike connects to 57thandnormal[.]com |
November 12, 2022 | Deployed Zeppelin ransomware Path: C:mntsmile.exe |
November 12, 2022 | Deployed Mimikatz Path: C:ProgramDatatoolkiit{redacted}outputC |
November 12, 2022 | Executed a PowerShell script (w1.ps1) Command: /c powershell.exe -ExecutionPolicy Bypass -file {ComputerName}s$w1.ps1 |
November 12, 2022 | Disabled antivirus (AV) programs such as Windows Defender add “HKLMSoftwarePoliciesMicrosoftWindows Defender” /v DisableAntiVirus /t REG_DWORD /d 1 /f |
November 12, 2022 | Deployed Vice Society ransomware Path: C:ProgramDatatest.exe |
November 12, 2022 | Created Administrator account on each endpoint, add to Administrators and Remote Desktop Users localgroup user Administrator {password} /add |
November 12, 2022 | Terminated processes such as AV and security software. process where “name like ‘%Agent%’” delete |
November 12, 2022 | Exfiltrated important files |
November 12, 2022 | Multiple deployments of Vice Society ransomware was dropped in the %Temp% directory on different endpoints Path: C:windowstempsvchost.exe |
November 12, 2022 | Observed file infector Neshta |
November 12, 2022 | Performed ransomware routine via $mytemp$svchost.exe “/c vssadmin.exe Delete Shadows /All /Quiet |
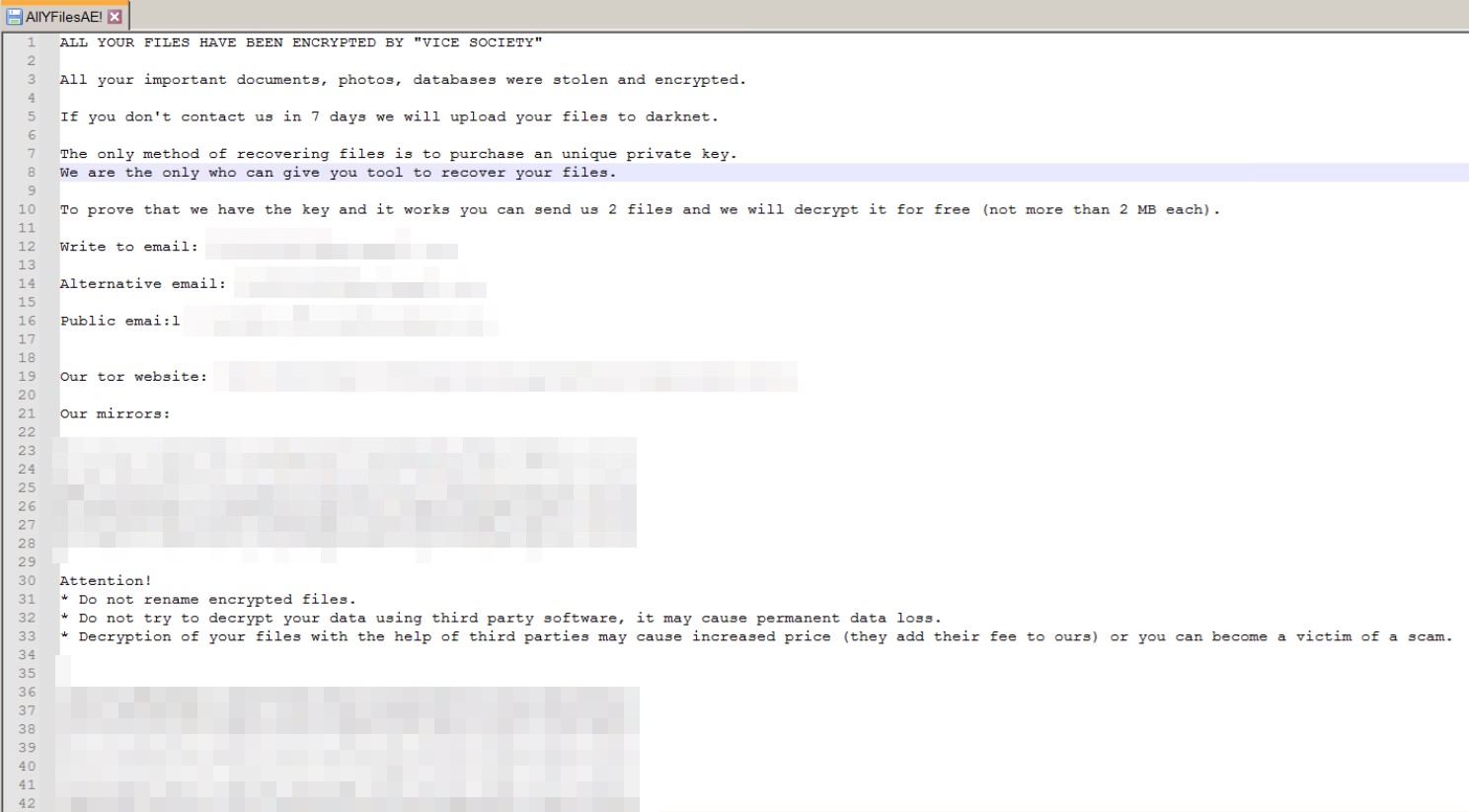
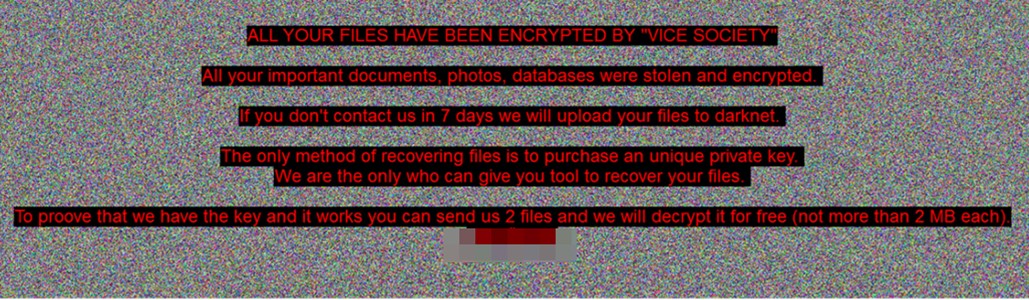
November 12, 2022 | Vice Society ransomware routine is performed (files are encrypted, ransom note with email contacts is dropped and files are appended with the extension .v1cesO0ciety) Ransom note: AllYFilesAE! |
November 12, 2022 | Event viewer logs and remote session traces such as RDP and terminal services were cleared reg delete “”HKEY_CURRENT_USERSoftwareMicrosoftTerminal Server ClientDefault”” /va /f |
November 12, 2022 | Deleted itself from the system “%System%cmd.exe” /c del {Malware File Path}{Malware File Name} -> nul -> to delete itself |
Table 1. Date and description of the routines involved in a Vice Society attack
The weaponized tool used by Vice Society is Cobalt Strike, which allows the group to remotely access and control the infected endpoint. The threat actor also used the Rubeus C# toolset for raw Kerberos interaction and abuse (although this is not a new technique, since it has been previously used by Ryuk, Conti, and BlackCat).
To laterally move within the target network, Mimikatz was used to dump passwords. We also observed the presence of the Zeppelin ransomware from another endpoint. Vice Society was known to have deployed Zeppelin before, however, perhaps due to its weaker encryption, the threat actor decided to go with custom-built ransomware.
Vice Society will then execute a PowerShell script to create an administrator account that allows for the remote access of other endpoints and to terminate several processes such as running security software before dropping the custom-built ransomware. In most of the ViceSociety detections we also observed the presence of Neshta file infector (which can be cleaned by Trend Micro), although it is not clear how this occurred.
Virtual servers, such as Microsoft Hyper-V, are also affected in this attack. We also found the attacker removing traces of RDP sessions such as wevtutil.exe, a technique that was previously used by Clop ransomware and KillDisk.

Once the administrator account is added and established, Vice Society can terminate several processes, including security-related ones, to enable the successful deployment and execution of its ransomware on the affected endpoints.
- %Agent%
- %Malware%
- %Endpoint%
- %sql%
- %Veeam%
- %Core.Service%
- %Mongo%
- %Backup%
- %QuickBooks%
- %QBDB%
- %QBData%
- %QBCF%
- %Kaspersky%
- %server%
- %sage%
- %http%
- %apache%
- %segurda%
- %center%
- %silverlight%
- %exchange%
- %manage%
- %acronis%
- %autodesk%
- %database%
- %firefox%
- %chrome%
- %barracuda%
- %arcserve%
- %sprout%
- %anydesk%
- %protect%
- %secure%
- %adobe%
- %java%
- %logmein%
- %microsoft%
- %solarwinds%
- %engine%
- %web%
- %vnc%
- %teamviewer%
- %OCSInventory%
- %monitor%
- %security%
- %def%
- %dev%
- %office%
- %Framework%
- %AlwaysOn%
- %Agent%
- %Malware%
- %Endpoint%
- %sql%
- %Veeam%
- %acronis%
- %autodesk%
- %database%
- %adobe%
- %java%
- %logmein%
- %microsoft%
- %solarwinds%
- %engine%
- %QBDB%
- %QBData%
- %QBCF%
- %Kaspersky%
- %server%
- %sage%
- %http%
- %apache%
- %web%
- %vnc%
- %AlwaysOn%
- %Framework%
- %sprout%
- %firefox%
- %chrome%
- %barracuda%
- %arcserve%
- %exchange%
- %manage%
- %Core.Service%
- %Mongo%
- %Backup%
- %QuickBooks%
- %teamviewer%
- %OCSInventory%
- %monitor%
- %security%
- %def%
- %dev%
- %office%
- %anydesk%
- %protect%
- %secure%
- %segurda%
- %center%
- %silverlight%
Conclusion and Trend Micro solutions
Vice Society seems to be constantly improving their capabilities, managing to build their own custom-built ransomware while also continuing to employ toolsets such as Cobalt Strike and malware such as Zeppelin and Hello Kitty/FiveHands to enhance their routines. Given what we know of the group’s technical knowledge and their willingness to target several different industries and regions, we can expect them to remain a significant player in the ransomware landscape and a threat that organizations must keep track of moving forward.
A multilayered approach can help organizations guard possible entry points into their system, such as endpoints, emails, web, and networks. The following security solutions can detect malicious components and suspicious behavior, which can help protect enterprises.
- Trend Micro Vision One™ provides multilayered protection and behavior detection, which helps block questionable behavior and tools early on before the ransomware can do irreversible damage to the system.
- Trend Micro Cloud One™ Workload Security protects systems against both known and unknown threats that exploit vulnerabilities. This protection is made possible through techniques such as virtual patching and machine learning.
- Trend Micro™ Deep Discovery™ Email Inspector employs custom sandboxing and advanced analysis techniques to effectively block malicious emails, including phishing emails that can serve as entry points for ransomware.
- Trend Micro Apex One™ offers next-level automated threat detection and response against advanced concerns such as fileless threats and ransomware, ensuring the protection of endpoints.
Indicators of Compromise
The indicators of compromise for this blog entry can be found here.