This blog examines CACTUS, a relatively new strain of ransomware that first appeared in the threat landscape in March 2023. In November 2023, Darktrace detected CACTUS ransomware on a US customer network and was able to provide full visibility over the attack and its kill chain.
What is CACTUS Ransomware?
In May 2023, Kroll Cyber Threat Intelligence Analysts identified CACTUS as a new ransomware strain that had been actively targeting large commercial organizations since March 2023 [1]. CACTUS ransomware gets its name from the filename of the ransom note, “cAcTuS.readme.txt”. Encrypted files are appended with the extension “.cts”, followed by a number which varies between attacks, e.g. “.cts1” and “.cts2”.
As the cyber threat landscape adapts to ever-present fast-paced technological change, ransomware affiliates are employing progressively sophisticated techniques to enter networks, evade detection and achieve their nefarious goals.
How does CACTUS Ransomware work?
In the case of CACTUS, threat actors have been seen gaining initial network access by exploiting Virtual Private Network (VPN) services. Once inside the network, they may conduct internal scanning using tools like SoftPerfect Network Scanner, and PowerShell commands to enumerate endpoints, identify user accounts, and ping remote endpoints. Persistence is maintained by the deployment of various remote access methods, including legitimate remote access tools like Splashtop, AnyDesk, and SuperOps RMM in order to evade detection, along with malicious tools like Cobalt Strike and Chisel. Such tools, as well as custom scripts like TotalExec, have been used to disable security software to distribute the ransomware binary. CACTUS ransomware is unique in that it adopts a double-extortion tactic, stealing data from target networks and then encrypting it on compromised systems [2].
At the end of November 2023, cybersecurity firm Arctic Wolf reported instances of CACTUS attacks exploiting vulnerabilities on the Windows version of the business analytics platform Qlik, specifically CVE-2023-41266, CVE-2023-41265, and CVE-2023-48365, to gain initial access to target networks [3]. The vulnerability tracked as CVE-2023-41266 can be exploited to generate anonymous sessions and perform HTTP requests to unauthorized endpoints, whilst CVE-2023-41265 does not require authentication and can be leveraged to elevate privileges and execute HTTP requests on the backend server that hosts the application [2].
Darktrace’s Coverage of CACTUS Ransomware
In November 2023, Darktrace observed malicious actors leveraging the aforementioned method of exploiting Qlik to gain access to the network of a customer in the US, more than a week before the vulnerability was reported by external researchers.
Here, Qlik vulnerabilities were successfully exploited, and a malicious executable (.exe) was detonated on the network, which was followed by network scanning and failed Kerberos login attempts. The attack culminated in the encryption of numerous files with extensions such as “.cts1”, and SMB writes of the ransom note “cAcTuS.readme.txt” to multiple internal devices, all of which was promptly identified by Darktrace DETECT™.
While traditional rules and signature-based detection tools may struggle to identify the malicious use of a legitimate business platform like Qlik, Darktrace’s Self-Learning AI was able to confidently identify anomalous use of the tool in a CACTUS ransomware attack by examining the rarity of the offending device’s surrounding activity and comparing it to the learned behavior of the device and its peers.
Unfortunately for the customer in this case, Darktrace RESPOND™ was not enabled in autonomous response mode during their encounter with CACTUS ransomware meaning that attackers were able to successfully escalate their attack to the point of ransomware detonation and file encryption. Had RESPOND been configured to autonomously act on any unusual activity, Darktrace could have prevented the attack from progressing, stopping the download of any harmful files, or the encryption of legitimate ones.
Cactus Ransomware Attack Overview
Holiday periods have increasingly become one of the favoured times for malicious actors to launch their attacks, as they can take advantage of the festive downtime of organizations and their security teams, and the typically more relaxed mindset of employees during this period [4].
Following this trend, in late November 2023, Darktrace began detecting anomalous connections on the network of a customer in the US, which presented multiple indicators of compromise (IoCs) and tactics, techniques and procedures (TTPs) associated with CACTUS ransomware. The threat actors in this case set their attack in motion by exploiting the Qlik vulnerabilities on one of the customer’s critical servers.
Darktrace observed the server device making beaconing connections to the endpoint “zohoservice[.]net” (IP address: 45.61.147.176) over the course of three days. This endpoint is known to host a malicious payload, namely a .zip file containing the command line connection tool PuttyLink [5].
Darktrace’s Cyber AI Analyst was able to autonomously identify over 1,000 beaconing connections taking place on the customer’s network and group them together, in this case joining the dots in an ongoing ransomware attack. AI Analyst recognized that these repeated connections to highly suspicious locations were indicative of malicious command-and-control (C2) activity.
![Cyber AI Analyst Incident Log showing the offending device making over 1,000 connections to the suspicious hostname “zohoservice[.]net” over port 8383, within a specific period.](https://assets-global.website-files.com/626ff4d25aca2edf4325ff97/662971c1cf09890fd46729a1_Screenshot%202024-04-24%20at%201.55.10%20PM.png)
The infected device was then observed downloading the file “putty.zip” over a HTTP connection using a PowerShell user agent. Despite being labelled as a .zip file, Darktrace’s detection capabilities were able to identify this as a masqueraded PuttyLink executable file. This activity resulted in multiple Darktrace DETECT models being triggered. These models are designed to look for suspicious file downloads from endpoints not usually visited by devices on the network, and files whose types are masqueraded, as well as the anomalous use of PowerShell. This behavior resembled previously observed activity with regards to the exploitation of Qlik Sense as an intrusion technique prior to the deployment of CACTUS ransomware [5].
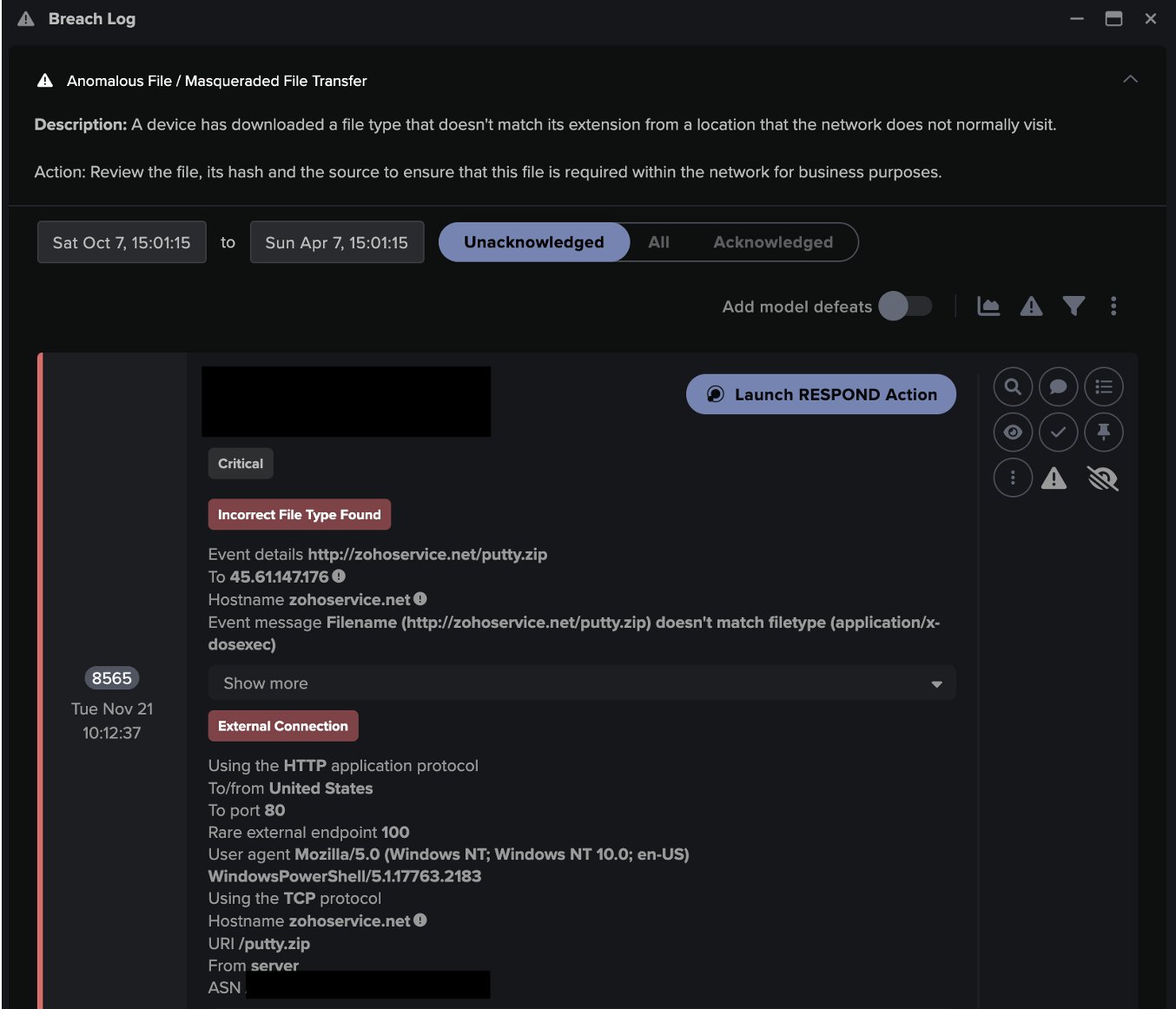
Following the download of the masqueraded file, Darktrace observed the initial infected device engaging in unusual network scanning activity over the SMB, RDP and LDAP protocols. During this activity, the credential, “service_qlik” was observed, further indicating that Qlik was exploited by threat actors attempting to evade detection. Connections to other internal devices were made as part of this scanning activity as the attackers attempted to move laterally across the network.
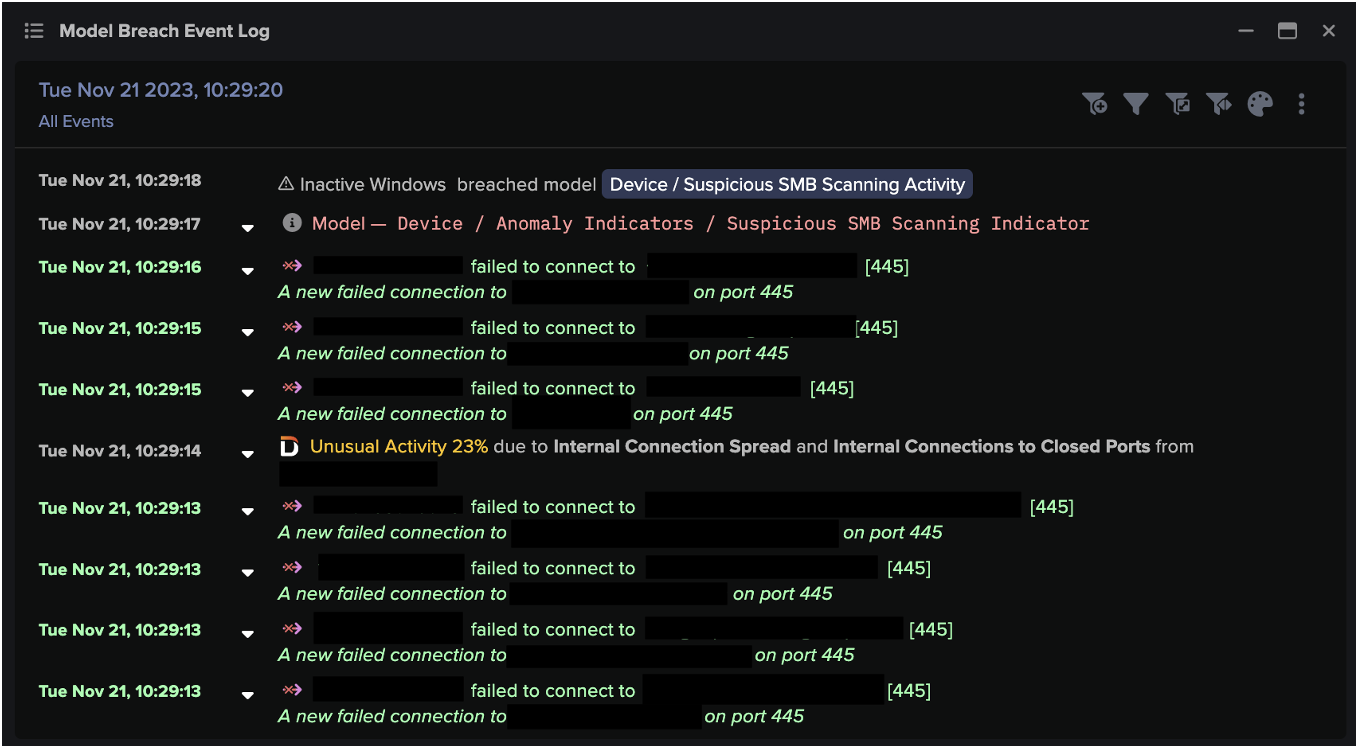
The compromised server was then seen initiating multiple sessions over the RDP protocol to another device on the customer’s network, namely an internal DNS server. External researchers had previously observed this technique in CACTUS ransomware attacks where an RDP tunnel was established via Plink [5].
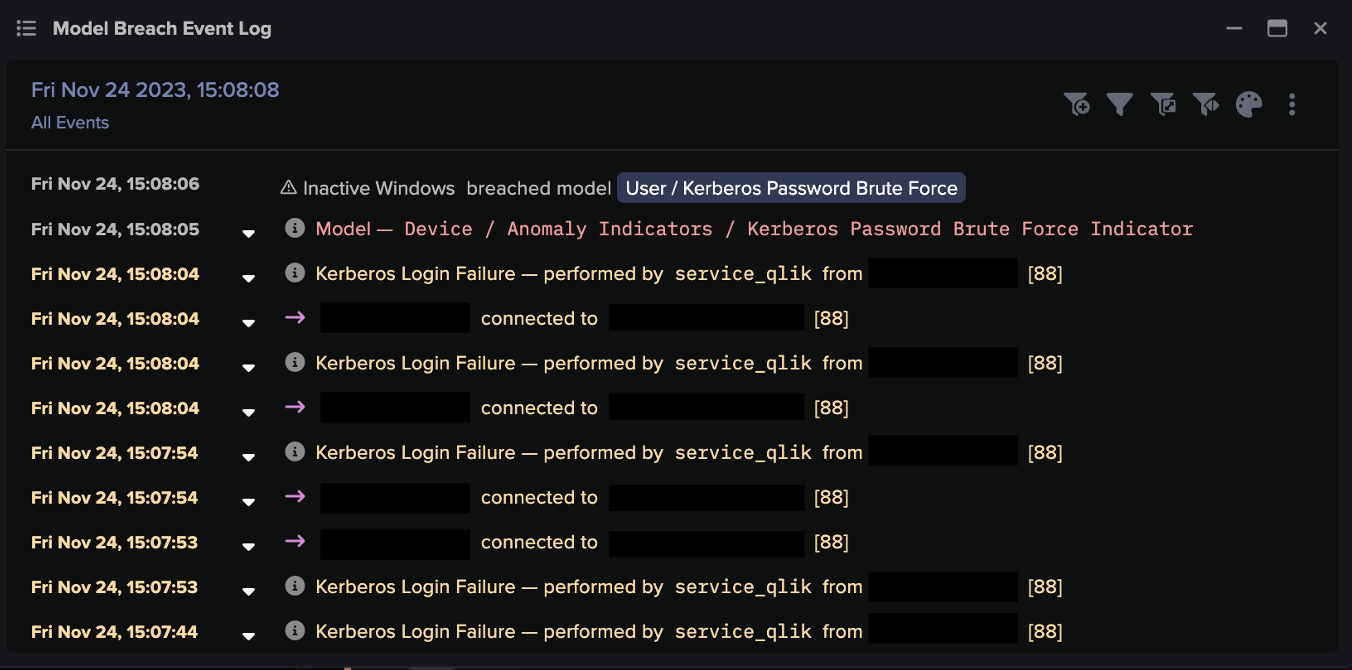
A few days later, on November 24, Darktrace identified over 20,000 failed Kerberos authentication attempts for the username “service_qlik” being made to the internal DNS server, clearly representing a brute-force login attack. There is currently a lack of open-source intelligence (OSINT) material definitively listing Kerberos login failures as part of a CACTUS ransomware attack that exploits the Qlik vulnerabilities. This highlights Darktrace’s ability to identify ongoing threats amongst unusual network activity without relying on existing threat intelligence, emphasizing its advantage over traditional security detection tools.
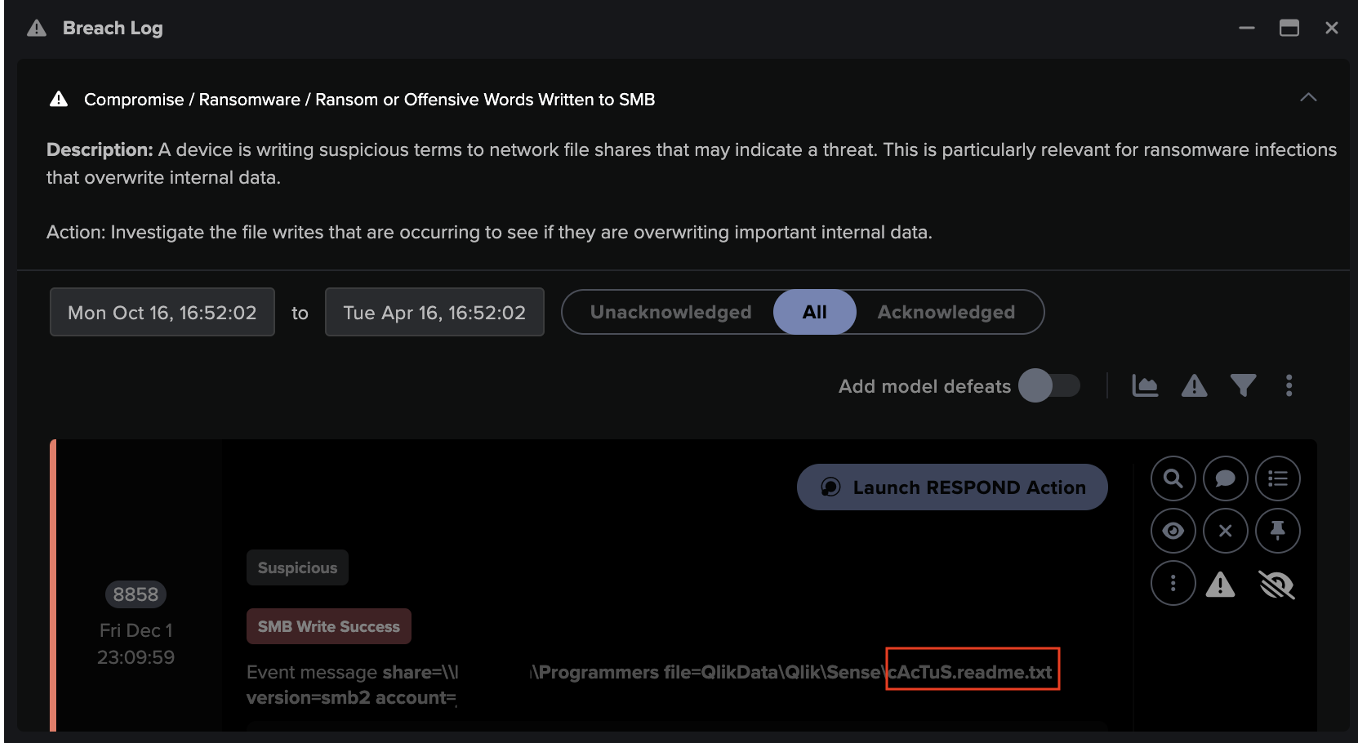
In the month following these failed Kerberos login attempts, between November 26 and December 22, Darktrace observed multiple internal devices encrypting files within the customer’s environment with the extensions “.cts1” and “.cts7”. Devices were also seen writing ransom notes with the file name “cAcTuS.readme.txt” to two additional internal devices, as well as files likely associated with Qlik, such as “QlikSense.pdf”. This activity detected by Darktrace confirmed the presence of a CACTUS ransomware infection that was spreading across the customer’s network.

Following this initial encryption activity, two affected devices were observed attempting to remove evidence of this activity by deleting the encrypted files.
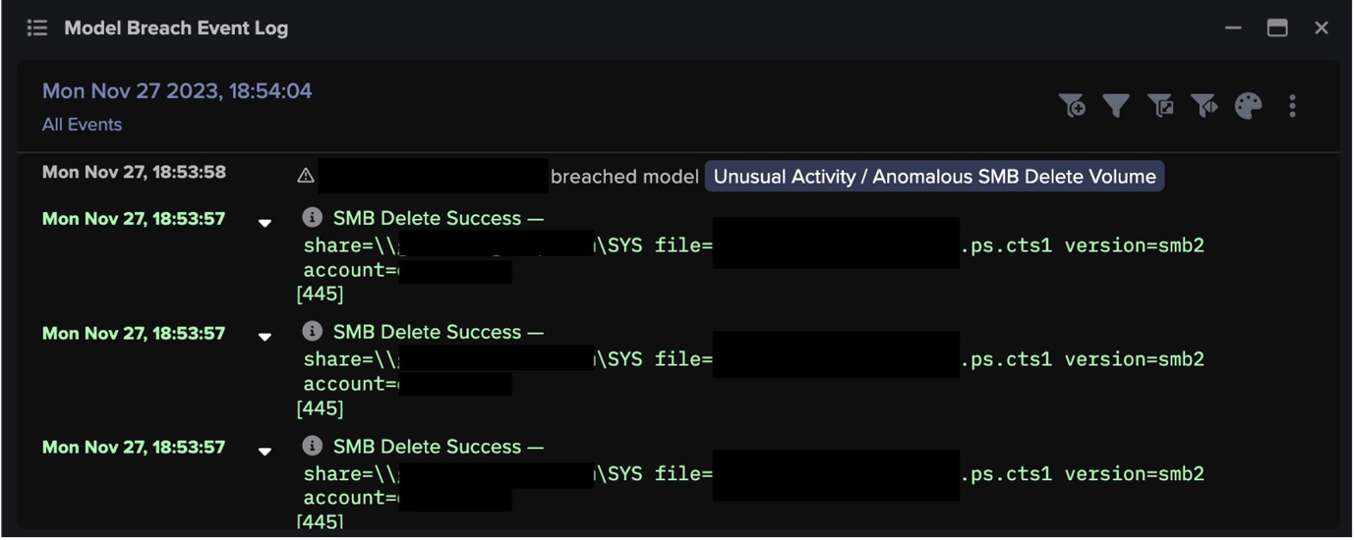
Conclusion
In the face of this CACTUS ransomware attack, Darktrace’s anomaly-based approach to threat detection enabled it to quickly identify multiple stages of the cyber kill chain occurring in the customer’s environment. These stages ranged from ‘initial access’ by exploiting Qlik vulnerabilities, which Darktrace was able to detect before the method had been reported by external researchers, to ‘actions on objectives’ by encrypting files. Darktrace’s Self-Learning AI was also able to detect a previously unreported stage of the attack: multiple Kerberos brute force login attempts.
If Darktrace’s autonomous response capability, RESPOND, had been active and enabled in autonomous response mode at the time of this attack, it would have been able to take swift mitigative action to shut down such suspicious activity as soon as it was identified by DETECT, effectively containing the ransomware attack at the earliest possible stage.
Learning a network’s ‘normal’ to identify deviations from established patterns of behaviour enables Darktrace’s identify a potential compromise, even one that uses common and often legitimately used administrative tools. This allows Darktrace to stay one step ahead of the increasingly sophisticated TTPs used by ransomware actors.
Credit to Tiana Kelly, Cyber Analyst & Analyst Team Lead, Anna Gilbertson, Cyber Analyst
Appendices
References
[3] https://explore.avertium.com/resource/new-ransomware-strains-cactus-and-3am
[4] https://www.soitron.com/cyber-attackers-abuse-holidays/
[5] https://arcticwolf.com/resources/blog/qlik-sense-exploited-in-cactus-ransomware-campaign/
Darktrace DETECT Models
Compromise / Agent Beacon (Long Period)
Anomalous Connection / PowerShell to Rare External
Device / New PowerShell User Agent
Device / Suspicious SMB Scanning Activity
Anomalous File / EXE from Rare External Location
Anomalous Connection / Unusual Internal Remote Desktop
User / Kerberos Password Brute Force
Compromise / Ransomware / Ransom or Offensive Words Written to SMB
Unusual Activity / Anomalous SMB Delete Volume
Anomalous Connection / Multiple Connections to New External TCP Port
Compromise / Slow Beaconing Activity To External Rare
Compromise / SSL Beaconing to Rare Destination
Anomalous Server Activity / Rare External from Server
Compliance / Remote Management Tool On Server
Compromise / Agent Beacon (Long Period)
Compromise / Suspicious File and C2
Device / Internet Facing Device with High Priority Alert
Device / Large Number of Model Breaches
Anomalous File / Masqueraded File Transfer
Anomalous File / Internet facing System File Download
Anomalous Server Activity / Outgoing from Server
Device / Initial Breach Chain Compromise
Compromise / Agent Beacon (Medium Period)
Compromise / Agent Beacon (Long Period)
List of IoCs
IoC – Type – Description
zohoservice[.]net: 45.61.147[.]176 – Domain name: IP Address – Hosting payload over HTTP
Mozilla/5.0 (Windows NT; Windows NT 10.0; en-US) WindowsPowerShell/5.1.17763.2183 – User agent -PowerShell user agent
.cts1 – File extension – Malicious appendage
.cts7- File extension – Malicious appendage
cAcTuS.readme.txt – Filename -Ransom note
putty.zip – Filename – Initial payload: ZIP containing PuTTY Link
MITRE ATT&CK Mapping
Tactic – Technique – SubTechnique
Web Protocols: COMMAND AND CONTROL – T1071 -T1071.001
Powershell: EXECUTION – T1059 – T1059.001
Exploitation of Remote Services: LATERAL MOVEMENT – T1210 – N/A
Vulnerability Scanning: RECONAISSANCE – T1595 – T1595.002
Network Service Scanning: DISCOVERY – T1046 – N/A
Malware: RESOURCE DEVELOPMENT – T1588 – T1588.001
Drive-by Compromise: INITIAL ACCESS – T1189 – N/A
Remote Desktop Protocol: LATERAL MOVEMENT – 1021 -T1021.001
Brute Force: CREDENTIAL ACCESS T – 1110 – N/A
Data Encrypted for Impact: IMPACT – T1486 – N/A
Data Destruction: IMPACT – T1485 – N/A
File Deletion: DEFENSE EVASION – T1070 – T1070.004
Source: Original Post