Summary: A critical cross-site scripting (XSS) vulnerability in pfSense v2.5.2, tracked as CVE-2024-46538, allows attackers to execute arbitrary scripts on affected systems, potentially leading to remote code execution. Discovered by security researcher physicszq, the flaw poses significant risks for users of this popular open-source firewall and router software.
Threat Actor: Malicious actors | malicious actors
Victim: pfSense users | pfSense users
Key Point :
- The vulnerability arises from inadequate input filtering in the interfaces_groups_edit.php component.
- Attackers can exploit the flaw by tricking pfSense administrators into executing crafted requests, leading to potential full compromise of the firewall.
- A proof-of-concept exploit has been published on GitHub, highlighting the severity of the vulnerability.
- Users are urged to update to the latest patched version of pfSense to mitigate risks.
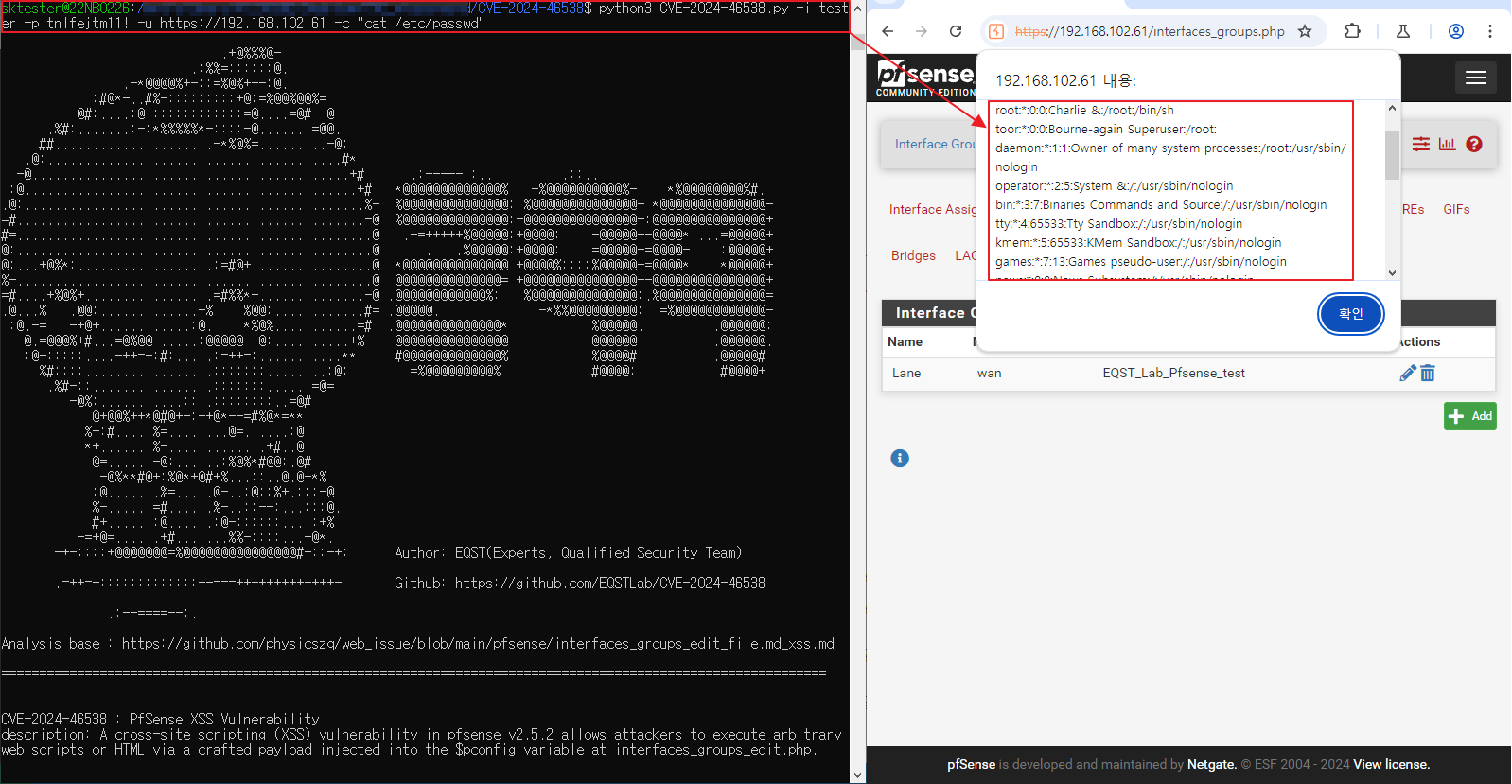
A recently discovered cross-site scripting (XSS) vulnerability in pfSense v2.5.2 has been identified, posing a significant security risk that could allow attackers to execute arbitrary web scripts or HTML on affected systems. The flaw, tracked as CVE-2024-46538, was uncovered by security researcher physicszq and affects the interfaces_groups_edit.php component of the popular open-source firewall and router software.
The vulnerability stems from inadequate input filtering of the $pconfig variable within the interfaces_groups_edit.php script. When user-supplied data is processed without proper sanitization, malicious actors can inject crafted payloads capable of executing arbitrary scripts in the context of the administrator’s browser session. This can ultimately lead to remote code execution (RCE) through subsequent malicious actions, such as manipulating the diag_command.php endpoint.
The flaw can be exploited by an attacker who tricks a pfSense administrator into executing a specially crafted request. Once the XSS payload is activated, the attacker can execute arbitrary commands with administrative privileges, potentially leading to a full compromise of the firewall.
EQSTLab has published a proof-of-concept (PoC) exploit on GitHub, demonstrating the severity of the vulnerability. The PoC illustrates how an attacker can leverage the XSS flaw to execute commands remotely.
Given the widespread use of pfSense as a firewall and router solution in both small and large-scale network environments, the impact of this vulnerability is far-reaching. If you are running pfSense version 2.5.2, update to the latest patched version as soon as possible.
For more detailed information on the vulnerability and access to the PoC, visit the GitHub repository shared by EQSTLab.