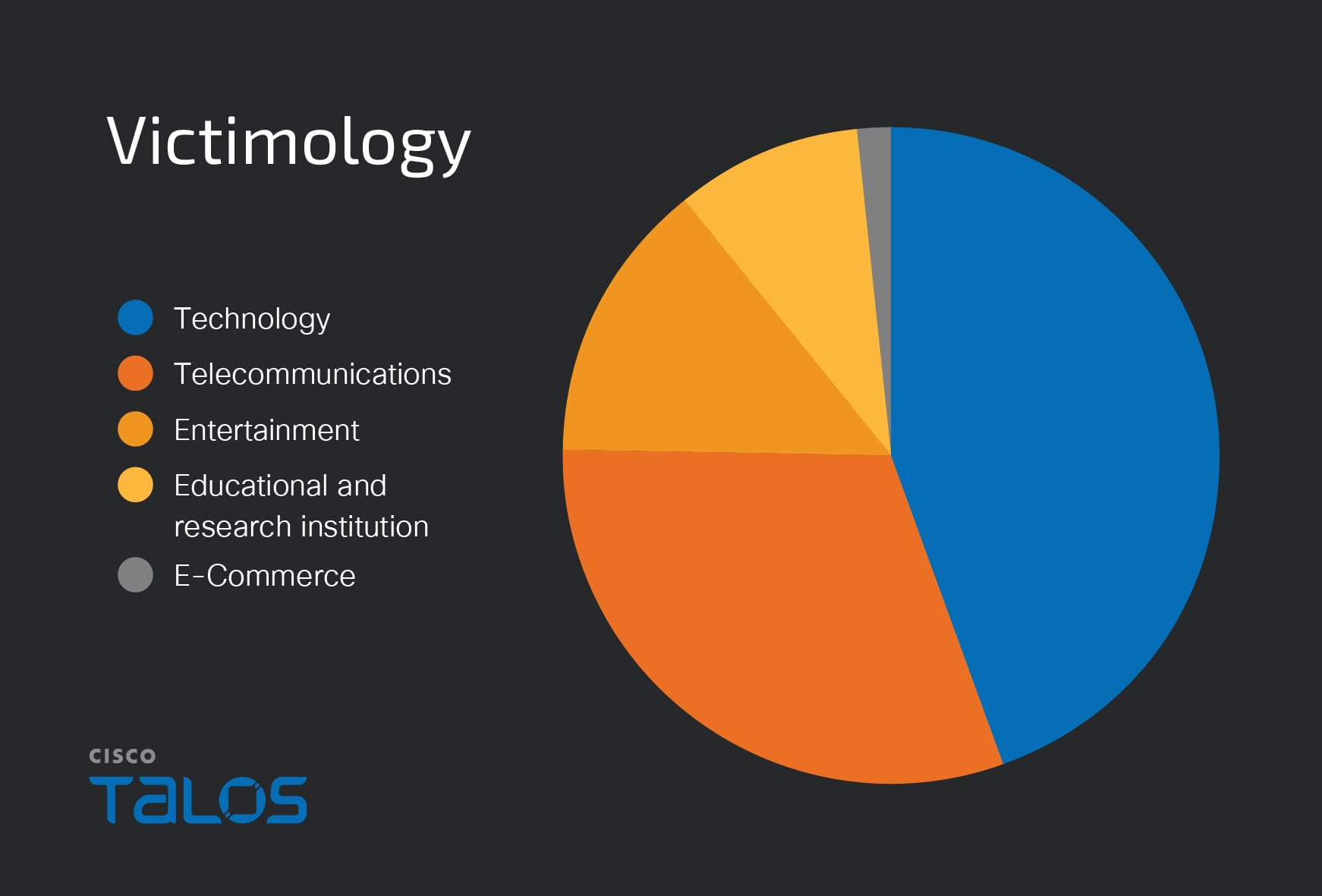
Cisco Talos discovered a malicious campaign attributed to an unknown attacker targeting organizations in Japan since January 2025, primarily exploiting the CVE-2024-4577 vulnerability to gain initial access and deploy advanced adversarial tools via Cobalt Strike. The attacker’s activities entail credential theft, system compromise, and potential lateral movement which could impact various industries. Affected: Japan, technology, telecommunications, entertainment, education, e-commerce
Keypoints :
- An unknown attacker has been conducting malicious activities since January 2025.
- Predominantly targeting organizations in Japan across various sectors.
- The attack exploits a remote code execution vulnerability (CVE-2024-4577) in PHP-CGI on Windows.
- The attacker uses the Cobalt Strike kit “TaoWu” for post-exploitation activities.
- Multiple techniques such as credential theft, privilege escalation, and lateral movement are evident in the attack.
- Exploited vulnerabilities allow for the execution of arbitrary PHP code on servers.
- Indicators of continued efforts to exploit public-facing applications noted in Talos IR report Q4 2024.
- C2 servers were identified with exposed directories containing malicious payloads.
- Attacker utilizes various tools and frameworks for post-exploitation, including Mimikatz for credential dumping.
MITRE Techniques :
- Reconnaissance (T1033): Collects system and user information using commands like whoami /all and net time.
- Exploitation for Privilege Escalation (T1068): Utilizes JuicyPotato, RottenPotato, and SweetPotato for privilege escalation.
- Modify Registry (T1112): Modifies Windows registry for persistence.
- Scheduled Task/Job (T1053): Creates scheduled tasks for maintaining access.
- Create or Modify System Process (T1543): Establishes malicious services for persistence.
- Clear Windows Event Logs (T1070.001): Attempts to erase event logs to conceal activities.
- Lateral Tool Transfer (T1570): Utilizes tools such as fscan.exe and Seatbelt.exe for network scanning and reconnaissance.
- OS Credential Dumping (T1003): Employs Mimikatz to dump credentials.
- Exfiltration Over C2 Channel (T1041): Exfiltrates stolen credentials back to C2 servers.
Indicator of Compromise :
- [IP Address] 38.14.255.23
- [IP Address] 118.31.18.77
- [MD5 Hash] e10adc3949ba59abbe56e057f20f883e
- [URL] http://38.14.255.23:8000/payload.ps1
- [Domain] gitee.com
Full Story: https://blog.talosintelligence.com/new-persistent-attacks-japan/