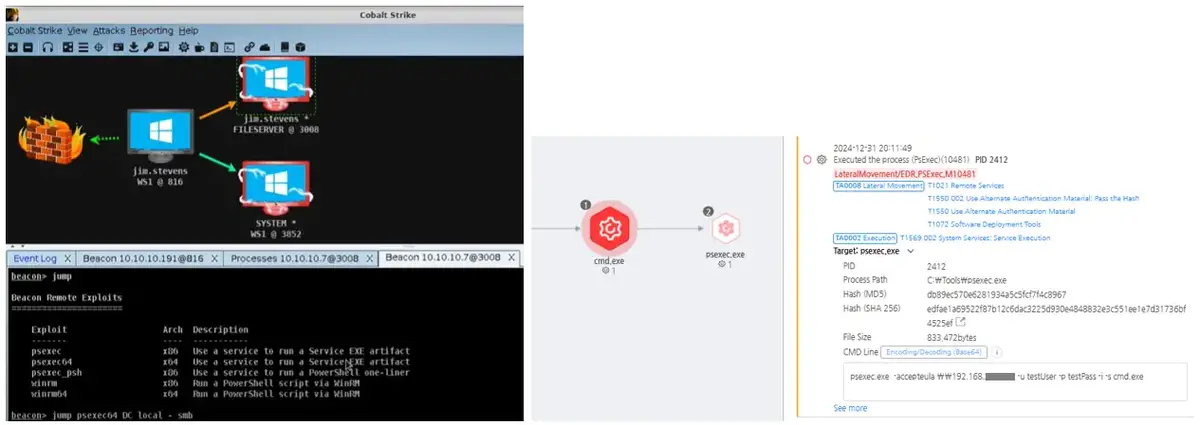
Summary: The Play ransomware, linked to the North Korean Andariel group, employs sophisticated techniques during the lateral movement phase of attacks, exploiting vulnerabilities and leveraging legitimate tools to infiltrate networks. Organizations are urged to enhance their security measures to combat these evolving threats.
Threat Actor: Andariel Group | Andariel Group
Victim: Various Organizations | Various Organizations
Key Point :
- Play ransomware encrypts files and follows a double extortion model, stealing data before encryption.
- Attackers utilize tools like BloodHound for reconnaissance and Mimikatz for credential access.
- Legitimate tools are often exploited to evade detection and maintain control over infected systems.
- Organizations are advised to prioritize patching vulnerabilities and enhancing security awareness.
Source: https://securityonline.info/unmasking-play-ransomware-tactics-techniques-and-mitigation-strategies/
Views: 0