Estimated reading time: 5 minutes
AsukaStealer, marketed on a Russian-language cybercrime forum by the alias ‘breakcore,’ has been exposed. The perpetrator offers its services for a monthly fee of $80, targeting individuals and organizations seeking to exploit its capabilities for malicious purposes.
Written in C++, AsukaStealer features customizable configurations and an intuitive web-based interface, enhancing its usability for cybercriminals seeking to deploy and manage malware efficiently.
It is a sophisticated malware designed to infiltrate a wide range of browsers, including popular ones like Mozilla Firefox, Google Chrome, and Microsoft Edge. It has the capability to extract valuable information such as extension data, internet cookies, and saved login credentials from these browsers, posing a significant threat to user’s privacy and security. With its ability to target both Gecko and Chromium-based browsers, Asuka ensures a broad reach across various browsing platforms, making it a potent tool for cybercriminals seeking to harvest sensitive data.
In addition to browser data, Asuka is equipped to target other applications and software commonly used by individuals and businesses. It seeks information related to cryptocurrency wallets, FTP clients like FileZilla, messaging platforms like Discord and Telegram, and gaming software like Steam.
Moreover, Asuka’s capabilities extend beyond data extraction to include exfiltrating files from infected systems and taking screenshots.
Technical Details
AsukaStealer r is a C++ custom malware. While analyzing the sample, it initially uses the API hashing technique.
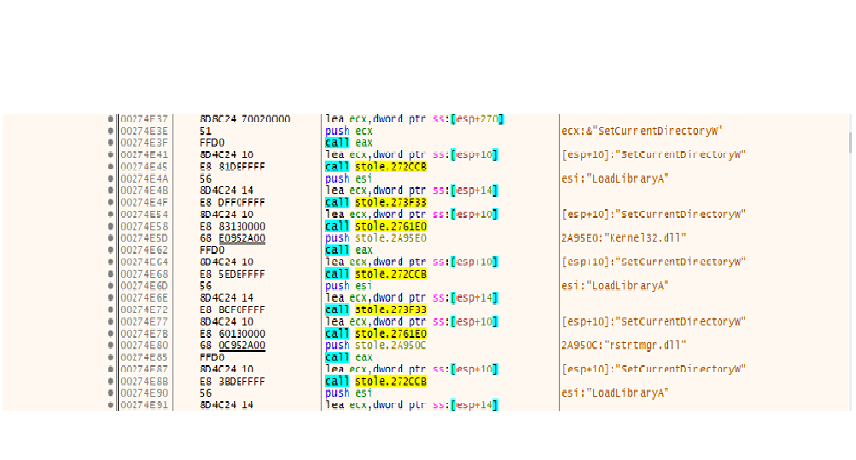
Fig 1: API resolution done by malware
Upon our analysis, we found that Asuka has some base64-encoded and hexadecimal values.
It is utilizing “1d6f6623f5e8555c446dc496567bd86e” as the key and “WRBCFgwZHQZIAVcWAwMbUQEOBVRTBA==” as the base64-encoded C2 address
After decoding the c2c address is hxxp://5.42.66.25:3000/
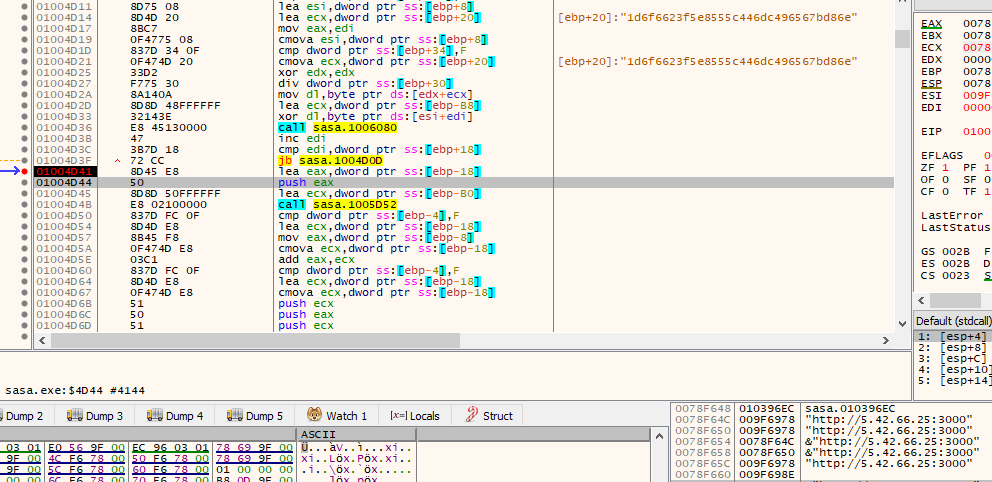
Fig 2: Decoding c2c base 64 value with key
C2C download of config file
The most interesting fact is that it downloads configuration files from the c2c server hxxp://5.42.66.25:3000/ and tries to utilize them.
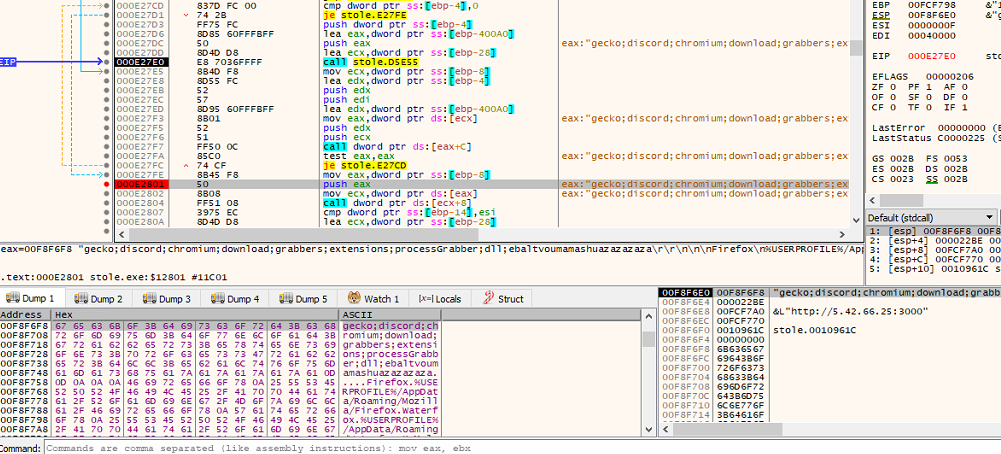
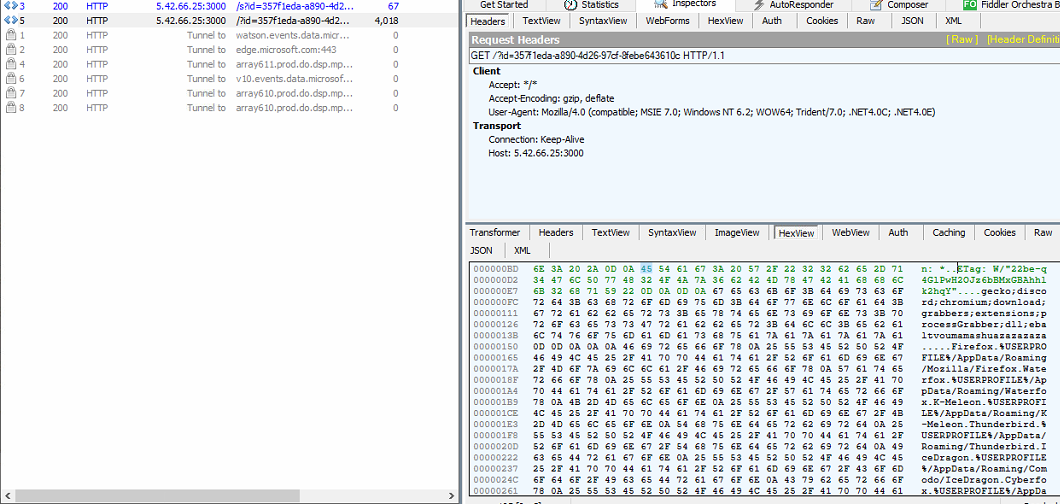
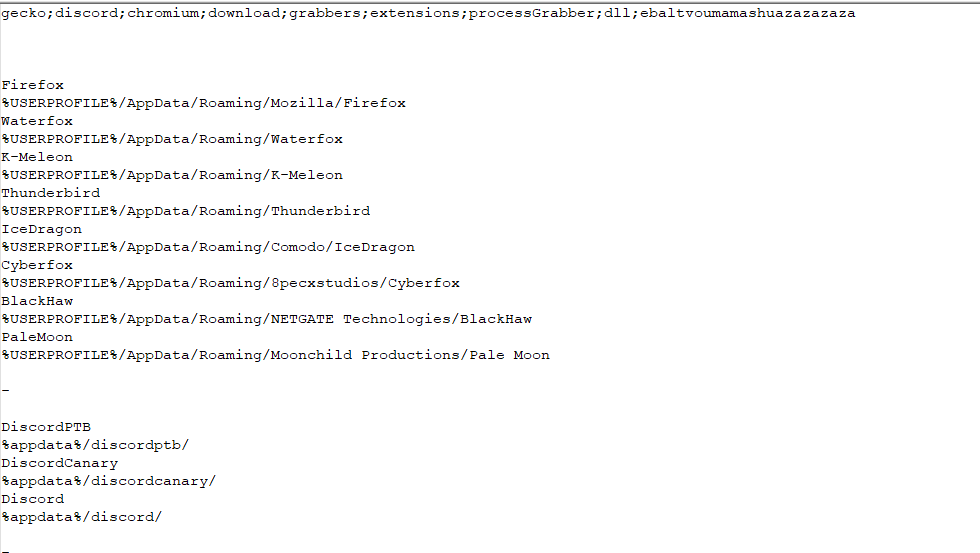
Fig 3: Configuration file
From the configuration file, we can see that it is utilizing browser and discord details.
Data Exfiltration
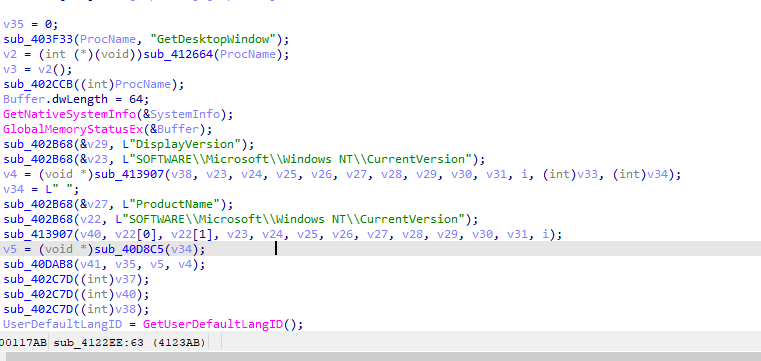
Fig 4: Desktop version and language ID check
It tries to collect desktop version and language ID and checks if they are from Armenia, Azerbaijan, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Tajikistan, Uzbekistan, Ukraine, or Russia.
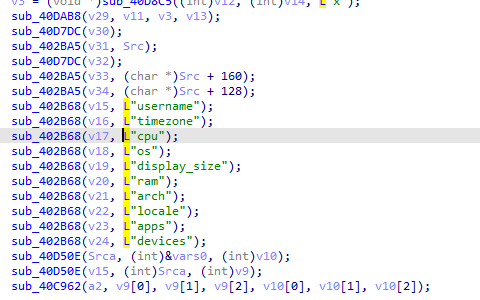
Fig 5: OS details capture
It also tries to capture CPU details, OS version, RAM, time zone, and other details.
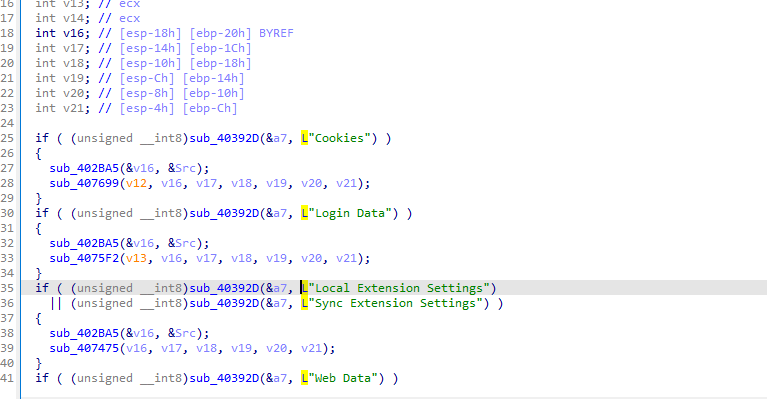
Fig 6: Browser credential details
It also tries to collect login details like cookies, passwords, and web Data of browsers.
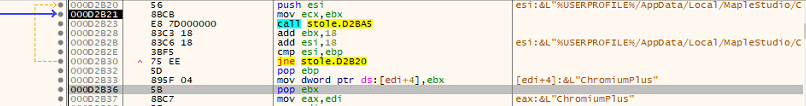
Fig 7: Chromium browser details
The above figure shows how it tries to steal data from the chromium browsers.
List of browsers it tries to steal are,
- OperaGX
- net
- Chromium
- Google86
- Opera
- ChromiumPlus
- Iridium
- 7Star
- CentBrowser
- Chedot
- Vivaldi
- Kometa
- Elements
- EpicPrivacyBrowser
- Uran
- Sleipnir5
- Citrio
- Coowon
- liebao
- QIPSurf
- Orbitum
- Amigo
- Torch
- YandexBrowser
- Comodo
- 360Browser
- Maxthon3
- K-Melon
- Sputnik
- Nichrome
- CocCoc
- Uran2
- Chromodo2
- Atom
- BraveSoftware
- Edge
- GeForceExperience
- Steam
- CryptoTabBrowser
It also tries to steal the following Crypto wallet details:
- osmwallet
- DogeLabsWallet
- Safepal
- KeplrWallet
- Zecrey
- LeapCosmosWallet
- EthosSuiWallet
- Nightly
- Z3US
- Bitski
- ABCWallet
- BitPay
- AuroxWallet
- WalletGuard
- EOFinanceWallet
- BitKeep-Wallet
- CoreWallet
- Crypto-Wallet
- VenomWallet
- BraavosWallet
- SolflareWallet
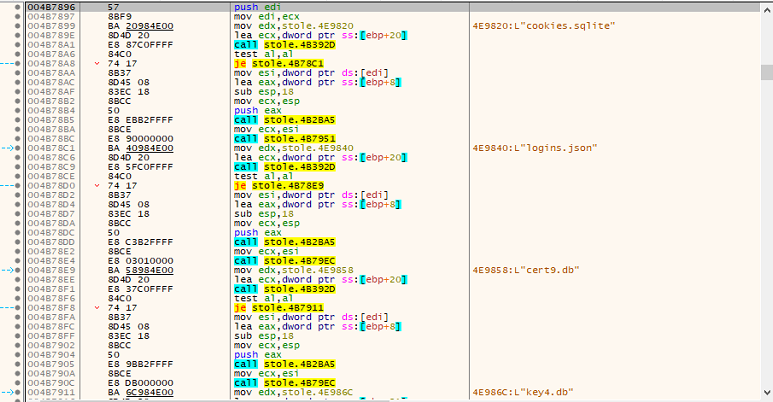
Fig 8: Storing browsing data in database file
Then malware collects and transmits crucial files for decrypting browser data, including cookies.sqlite, logins.json, cert9.db, and key4.db.
Each file is associated with a unique UUID generated using the UuidCreate function, enhancing tracking and organization of the exfiltrated data. Notably, UuidCreate is also employed for other data extracted from the host, spanning cryptocurrency wallets, the Grabber module, Steam, Telegram, and additional sources, showcasing the malware’s comprehensive data exfiltration capabilities.
Downloads Coinminer
It also downloads the Coinminer file, saves it in a temp folder with the name tempik22814838.exe, and executes it.
C2c of Coinminer: hxxp://www.marrem.ee/altushka1488228pudge.exe
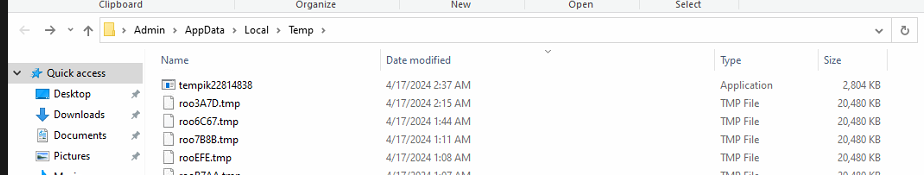
Fig 9: Coinminer downloaded and dropped in the temp folder
When we tried to check the c2c, we found the login page of AsukaStealer, where the attacker stored all the user’s details.
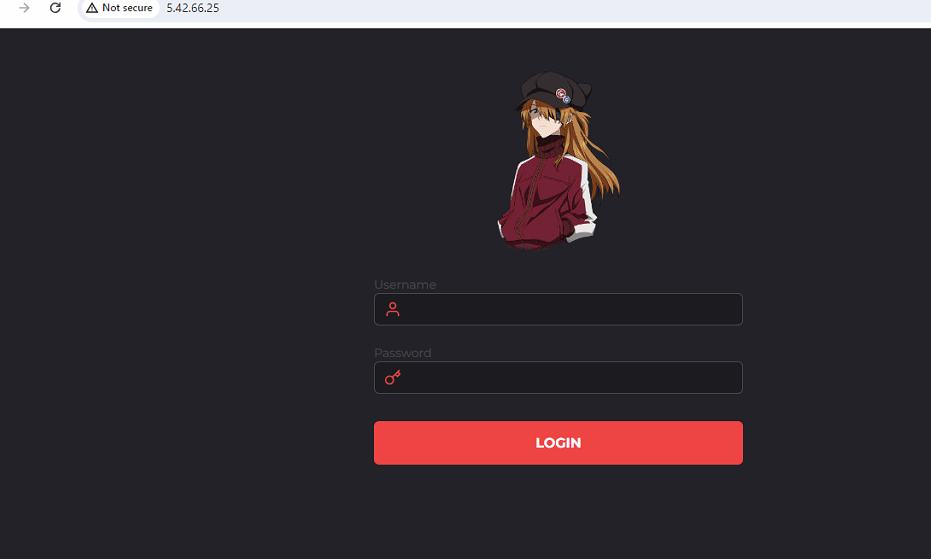
Fig 10: Login page of AsukaStealer malware
Mitre attack techniques:
| Initial Access | TA0001 |
| Execution | TA0002 |
| Defense Evasion | TA0005 |
| Credential Access | TA0006 |
| Discovery | TA0007 |
| Collection | TA0009 |
Command and Control | TA0011 |
| Steal Application Token | T1528 |
| Steal Web Session Cookie | T1539 |
| Screen Capture | T1113 |
| Exfiltration Over C2 | T1041 |
Conclusion:
With the increasing number of malware and the prevalence of Malware-as-a-Service, it is becoming easier for threat actors to consume what is readily available without spending much time. Data is the most important commodity for an individual or a business, which threat actors can steal and sell on underground forums, resulting in massive breaches. So, it becomes more crucial to keep your antivirus up to date to avoid such circumstances.
IOCs:
24bb4fc117aa57fd170e878263973a392d094c94d3a5f651fad7528d5d73b58a AsukaStealer
6b8277813999b908fc38eca68db5249fe0b76a8f652cb1a5a21d073247ed7dc4 Coinminer
Authors:
Soumen Burma
Rumana Siddiqui
Views: 0