Summary: The content discusses a new hacking campaign called “SickSync” launched by the UAC-0020 (Vermin) hacking group, targeting the Ukrainian defense forces and using the legitimate file-syncing software SyncThing in combination with malware called SPECTR.
Threat Actor: UAC-0020 (Vermin) hacking group | UAC-0020 (Vermin)
Victim: Ukrainian defense forces | Ukrainian defense forces
Key Point :
- The UAC-0020 (Vermin) hacking group, linked to the Luhansk People’s Republic (LPR) region occupied by Russia, has launched a new hacking campaign called “SickSync” targeting the Ukrainian defense forces.
- The attack involves a phishing email carrying a password-protected RARSFX archive, which extracts a PDF, an installer, and a BAT script that executes SyncThing and SPECTR malware.

The Computer Emergency Response Team of Ukraine (CERT-UA) reports about a new campaign dubbed “SickSync,” launched by the UAC-0020 (Vermin) hacking group in attacks on the Ukrainian defense forces.
The threat group is linked to the Luhansk People’s Republic (LPR) region, which Russia has occupied almost in its entirety since October 2022. The hacker’s activities commonly align with Russia’s interests.
The attack utilizes the legitimate file-syncing software SyncThing in combination with malware called SPECTR.
Vermin’s apparent motive is to steal sensitive information from military organizations.
Attack details
The attack begins with a phishing email sent to the target, carrying a password-protected RARSFX archive named “turrel.fop.wolf.rar.”
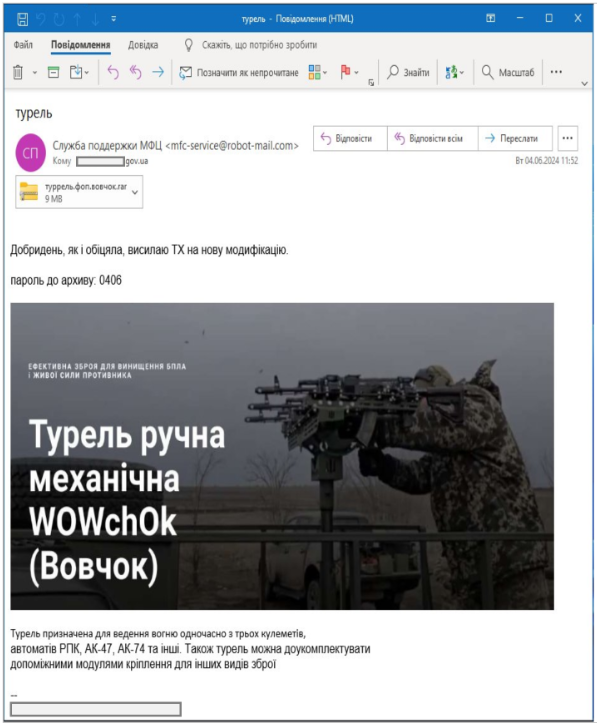
Source: CERT-UA
Upon launching the file, it extracts a PDF (“Wowchok.pdf”), an installer (“sync.exe”), and a BAT script (“run_user.bat”). The BAT executes sync.exe, which contains SyncThing and SPECTR malware, along with the required libraries.
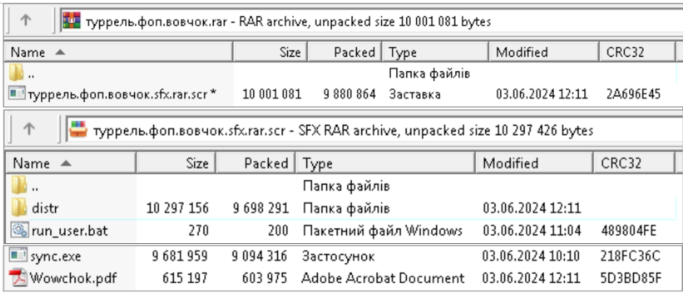
Source: CERT-UA
SyncThing establishes a peer-to-peer connection for data synchronization, which is used for stealing documents and account passwords.
The legitimate tool is modified with new directory names and scheduled tasks to evade identification, while the component that displays a window when it’s active has been removed.
SPECTR is a modular malware that has the following capabilities:
- SpecMon: Calls PluginLoader.dll to execute DLLs containing the “IPlugin” class.
- Screengrabber: Takes screenshots every 10 seconds when specific program windows are detected.
- FileGrabber: Uses robocopy.exe to copy files from user directories such as Desktop, MyPictures, Downloads, OneDrive, and DropBox.
- Usb: Copies files from removable USB media.
- Social: Steals authentication data from various messengers like Telegram, Signal, Skype, and Element.
- Browsers: Steals data from browsers including Firefox, Edge, and Chrome, focusing on authentication data, session information, and browsing history.
Data stolen by SPECTR is copied into subfolders within the ‘%APPDATA%syncServe_Sync’ directory and subsequently transferred through syncing to the threat actor’s system.
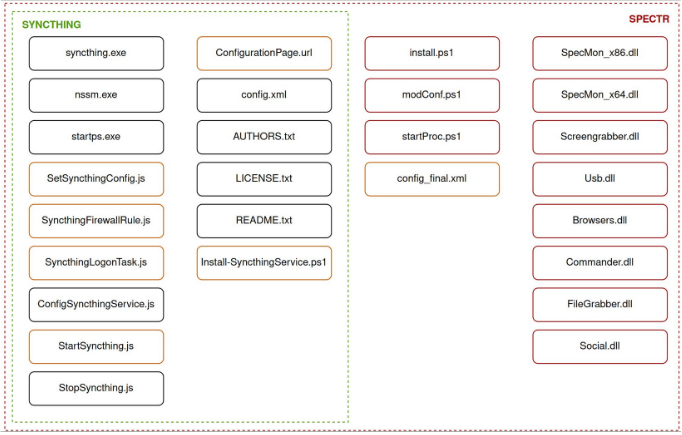
Source: CERT-UA
CERT-UA believes Vermin decided to use a legitimate tool for data exfiltration to reduce the likelihood of security systems flagging the network traffic as suspicious.
The cybersecurity agency notes that any interaction with SyncThing’s infrastructure (e.g., *.syncthing.net) should be enough to consider a system compromised and launch an investigation to detect and uproot the infection.
“An interesting youtube video that may be related to the article above”