In early 2024, a significant uptick in destructive cyberattacks targeting critical infrastructure in Ukraine was uncovered, attributed to the Russia-linked UAC-0212 group, tied to the notorious Sandworm APT collective. CERT-UA highlighted the risks posed to around 20 Ukrainian organizations across various sectors, suggesting a trend indicating these offensives are being used as a means to refine tactics for broader attacks.
Affected: Ukraine, critical infrastructure sector, energy, water, heat supply sectors.
Affected: Ukraine, critical infrastructure sector, energy, water, heat supply sectors.
Keypoints :
- Destructive cyberattacks were discovered against ICT systems of 20 organizations in Ukraine.
- The attacks are linked to the Russian state-sponsored Sandworm APT group (UAC-0002).
- Attackers employed various tactics, including malicious PDF links and exploitation of vulnerabilities.
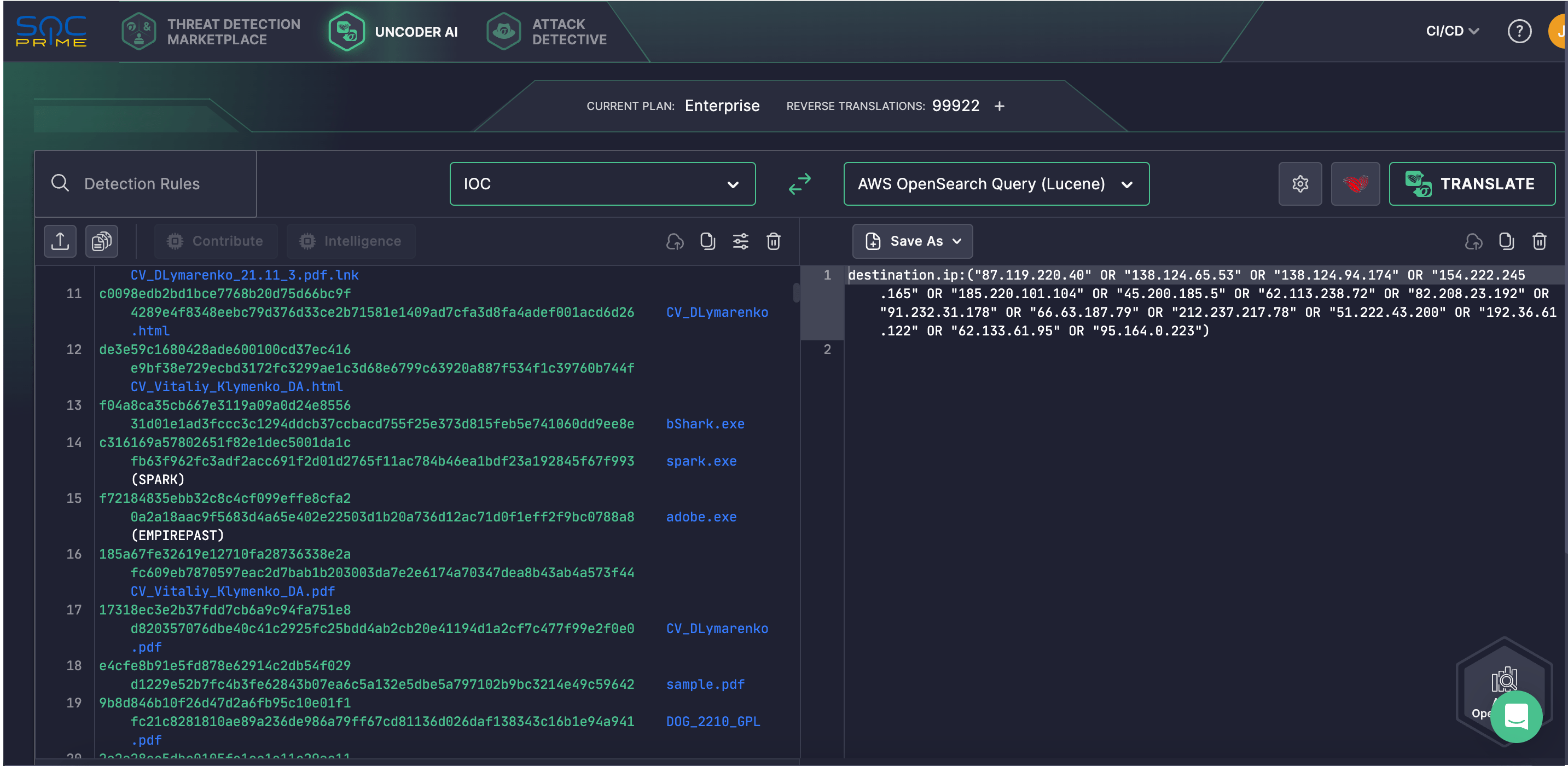
- The UAC-0212 group used tools like SECONDBEST, EMPIREPAST, SPARK malware, and CROOKBAG.
- Cybersecurity alerts have been issued by CERT-UA regarding the ongoing threat landscape.
- The group’s tactics have expanded beyond Ukraine, affecting companies in Serbia and Czechia.
MITRE Techniques :
- TA0001 – Initial Access: Exploitation of CVE-2024-38213 to download LNK files.
- TA0002 – Execution: Execution of PowerShell commands facilitated by LNK file.
- TA0003 – Persistence: Establishing persistence via the Run registry key.
- TA0009 – Collection: Document exfiltration using RSYNC.
- TA0040 – Impact: Intent to cause disruptions in critical infrastructure operations in Ukraine.
Indicator of Compromise :
- [File] pdf.lnk
- [Vulnerability] CVE-2024-38213
Full Story: https://socprime.com/blog/detecting-uac-0212-attacks-linked-to-sandworm/