Summary: A recent OSINTMATTER report reveals a sophisticated phishing campaign targeting Booking.com, involving a multi-phase approach that compromises hotel managers’ accounts and scams customers directly through the app. The attackers utilize a cleverly disguised domain and advanced techniques to harvest sensitive information, posing significant risks to both the travel industry and its customers.
Threat Actor: Unknown | unknown
Victim: Booking.com | Booking.com
Key Point :
- The phishing campaign starts by compromising hotel managers’ accounts, allowing attackers to access customer reservation systems.
- Attackers use a fake domain, “extraknet-booking.com,” to deceive users into providing sensitive information through a fraudulent portal.
- Advanced techniques like JavaScript obfuscation and dynamic cloaking are employed to evade detection and manipulate user experiences.
- The operation is linked to the Ninja Trojan malware, which enables multiple operators to control compromised systems simultaneously.
- Unusual STUN binding requests suggest potential data exfiltration or covert communication with compromised systems.
- The phishing site features an iFrame that connects to numerous other phishing sites, enhancing the attackers’ control and reach.
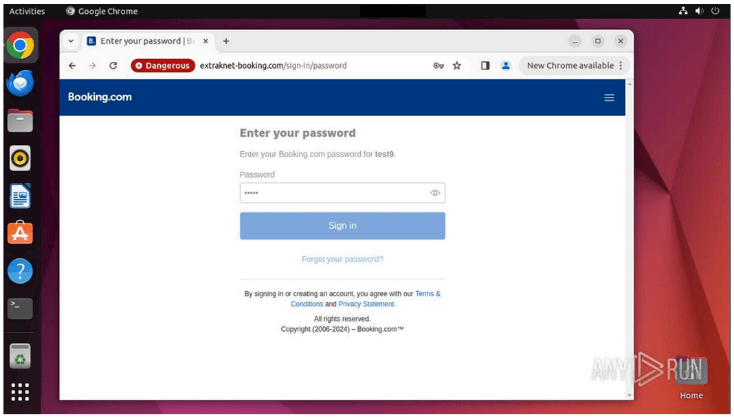
A new report from OSINTMATTER has detailed a sophisticated phishing campaign targeting Booking.com, a leading online travel reservation platform. The attack involves a multi-phase approach, starting with compromising hotel managers’ accounts and culminating in scamming hotel customers directly through the Booking.com app.
The first phase involves compromising the Booking.com accounts of hotel managers, allowing attackers to infiltrate the very systems that manage customer reservations and transactions. Once inside, the second phase kicks in—scamming hotel guests through the official Booking.com app. This dual-pronged approach has made the scam one of the most successful in the cybercriminal world, with devastating consequences for both the industry and its customers.
At the heart of this operation lies a cleverly disguised domain, “extraknet-booking.com,” which was carefully crafted to mimic the legitimate subdomain “extranet-booking.com” used by Booking.com hotel managers. By subtly altering the domain name, the attackers have managed to deceive even the most vigilant users, directing them to a fake portal that mirrors the genuine Booking.com interface.
This fraudulent portal was meticulously designed to harvest sensitive information, including login credentials, personal data, and financial details. To lure victims to this portal, attackers employed a range of tactics, from traditional spoofed emails to advanced SEO poisoning techniques, which manipulate search engine results to make malicious sites appear legitimate.
One of the standout features of this phishing site is its use of JavaScript obfuscation—a technique employed to obscure the malicious code and evade detection by security tools. The obfuscation, which involved encoding a specific string using parseInt, rendered the code difficult to analyze. This string, when decoded, revealed the word “загружено” (loaded) in Cyrillic script, hinting at possible ties to Russian-speaking regions.
Further analysis of the JavaScript files executed by “extraknet-booking.com” revealed connections to dozens of other malicious sites, all linked to the Ninja Trojan malware. This malware is notorious for enabling multiple operators to simultaneously control compromised systems, making it a potent tool in the cybercriminal’s arsenal.
Another critical element uncovered in this phishing campaign was the identification of 238 STUN (Session Traversal Utilities for NAT) binding requests to various domains associated with open WebRTC VoIP services. While STUN requests are commonly used in legitimate applications like VoIP calls, the unusual volume and non-standard port usage observed here point to potential malicious intent, such as data exfiltration or maintaining covert communication with compromised systems.
One of the contacted STUN servers, “stun.usfamily.net,” had already been flagged as compromised, further raising suspicions about the attackers’ activities. The use of STUN in this context aligns with findings from previous research, which highlighted how attackers exploit new protocols and hide malicious traffic within legitimate services.
The phishing site also employed dynamic cloaking techniques, a sophisticated method that allows the site to present different content based on the user’s profile. Depending on factors like IP address, browser settings, or other identifiable data, the site might show the malicious fake portal, the genuine Booking.com page, or even error pages to evade detection by security researchers.
This cloaking mechanism effectively shields the phishing operation from prying eyes, making it difficult for investigators to uncover the full extent of the scam. Tests conducted on different virtual machine configurations demonstrated how the site could deliver varied responses, ranging from timeouts to full access to the phishing portal, based on the conditions met.
During the investigation, a pivotal discovery was made—the phishing page contained an iFrame linked to “httxx://ls.cdn-gw-dv[.]vip/+dedge/zd/zd-service[.]html,” a central hub connecting hundreds of other phishing sites targeting Booking.com and similar platforms. This iFrame served as a powerful tool for the attackers, allowing them to centralize control, widen the reach of their scam, and gather valuable analytics on the effectiveness of their various phishing pages.
This attack underscores the increasingly sophisticated nature of phishing campaigns and the urgent need for heightened vigilance within the travel industry. Both businesses and individuals must exercise caution when interacting with emails and links, particularly those related to Booking.com or other travel platforms. It is crucial to independently verify the legitimacy of any website before entering sensitive information.
Related Posts:
Source: https://securityonline.info/travelers-targeted-booking-com-phishing-scam-unveiled