For over 10 years, security researchers have been observing and keeping tabs of APT group Earth Aughisky’s malware families and the connections, including previously documented malware that have yet to be attributed.
For security researchers and analysts monitoring advanced persistent threat (APT) groups’ attacks and tools, Earth Aughisky (also known as Taidoor) is among the more active units that consistently make security teams vigilant. Over the last decade, the group has continued to make adjustments in the tools and malware deployments on specific targets located in Taiwan and, more recently, Japan.
Our research paper, “The Rise of Earth Aughisky: Tracking the Campaigns Taidoor Started,” lists all the malware attributed to the group, the connections of these malware families and tools with other APT groups, and the latest updates in illicit activities potentially connected to real-world changes. Our research also covers recommendations and potential opportunities from the changes this APT group appears to be undergoing.
Malware families attributed
This blog post summarizes and highlights some of the malware families and tools with components that have yet to be identified, reported, or attributed to the group. For a full list of all the malware families and tools we attribute to Earth Aughisky, download our research here.
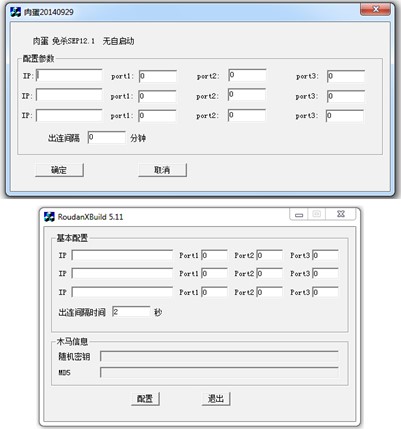
Roudan (also known as Taidoor)
While the name Taidoor has been interchangeably used to refer to the group and the malware, we analyzed that the threat actors named this malware family Roudan while looking at both the backdoor and backdoor builder. This classic Earth Aughisky malware, which was first disclosed over 10 years ago, has been observed for the different formats the group employed for callback traffic as it contains an encoded MAC address and data.
LuckDLL
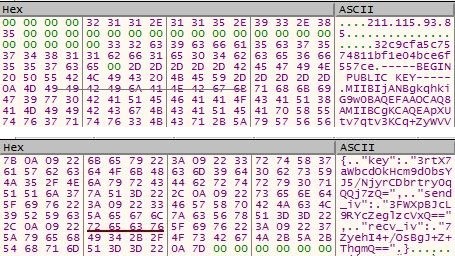
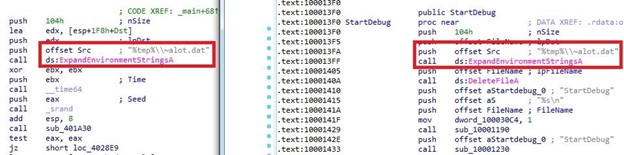
Still unreported, LuckDLL is a relatively new backdoor observed to be active after 2020. The public key is embedded inside the malware configuration and subsequently communicates with the C&C server. LuckDLL then proceeds to generate a random session key and initialization vector (IV) to encrypt the traffic.
The public key encrypts the session key and IV during initial communication, and shared with the C&C.
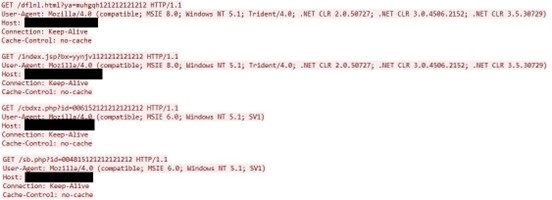
GrubbyRAT
Following our sensors’ observations, GrubbyRAT is deployed only when Earth Aughisky is interested in important targets that follow certain criteria. Still unreported, the configuration file is sometimes installed under an existing application or general system folder and uses the same file name as the component. This suggests that this RAT is installed manually and after the threat actor has gained administrative privileges and control in the infected system.
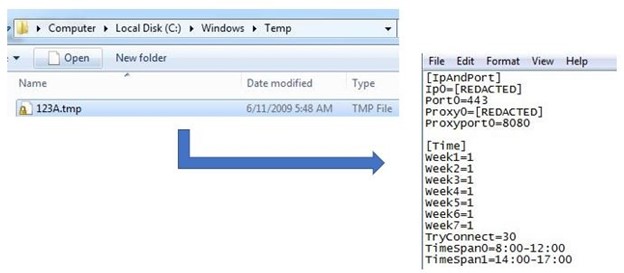
Taikite (also known as SVCMONDR)
While previously reported as SVCMONDR, this malware has yet to be attributed to Earth Aughisky. Previously identified with a 2015 report identifying a vulnerability, some samples of this dropped file observed in Taiwan had a .pdb similar to the APT group’s other malware families and tools. The C&C callback traffic is encoded in Base64 and showed a detailed feedback data structure and behavior analysis.
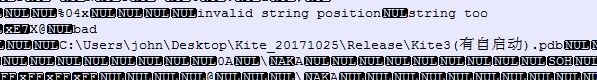
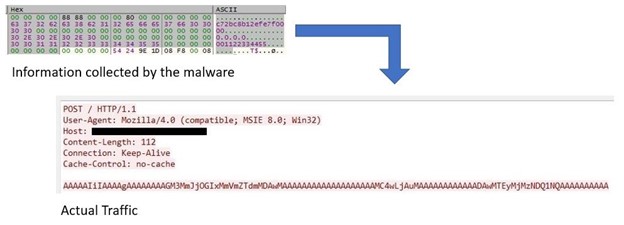
SiyBot
This backdoor has yet to be reported, likely because we observed this tool as being deployed less and only in few attack incidences. SiyBot abuses earlier versions of public services such as Gubb and 30 Boxes to perform C&C communication, wherein the necessary credential or token can be found in the malware configuration. We observed this backdoor to support only a few functions based on the commands we found.
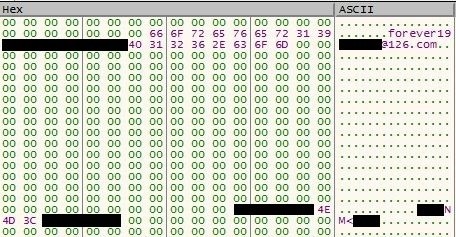
Connections
We feature some of the overlaps and connections we found with Earth Aughisky’s malware and tools.
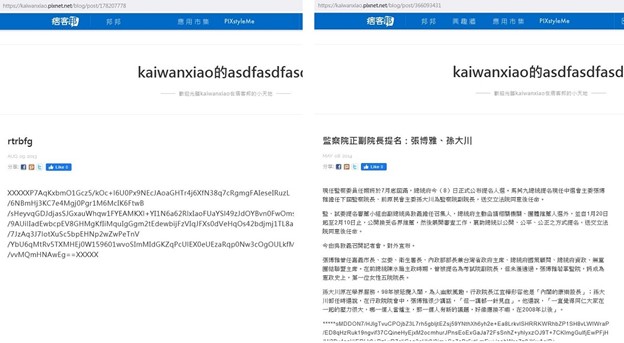
Roudan and SiyBot
We found the same website being used to host Roudan and SiyBot, as well as ASRWEC downloader (a tool we also attribute to Earth Aughisky) payload in the same repository.
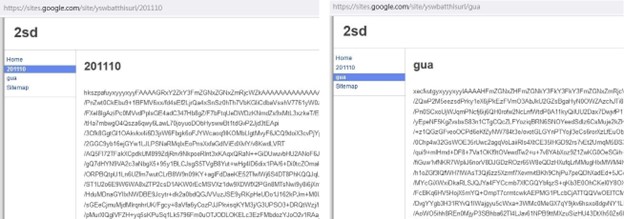
Roudan, Taleret, and Taikite
Taleret is another malware family that has been identified or suspected with Earth Aughisky for years. We found overlaps in the C&C servers being used by these malware families, as well as the same hashes, logging mechanisms, and blog hosts between Taleret and earlier versions of Roudan payload.
Insights
As Earth Aughisky is one of the few APT groups that has exercised longevity in cyberespionage, security analysts and teams have collected and continue to gather data to evaluate the group’s skills, developments, relations with other APT groups, and their activities. Samples of their malware families and tools allow security teams to gain an understanding of the level of sophistication – or lack of it – of the group’s operations, connection, and even changes possibly affecting them from the real-world complexities such as politics and geographic objectives.
To find the complete details of our malware analyses, insights, and attribution connections, download our research paper, “The Rise of Earth Aughisky: Tracking the Campaigns Taidoor Started.”
Indicators of Compromise (IOCs)
For a full list of the IOCs, find them here.
Source: https://www.trendmicro.com/en_us/research/22/j/tracking-earth-aughiskys-malware-and-changes.html
Views: 0