A vulnerability (CVE-2025-30066) was identified in the GitHub Action tj-actions/changed-files, affecting numerous repositories. This article discusses how Falco Actions can be integrated into CI/CD workflows to detect and respond to attacks like this one, providing enhanced visibility and security against potential threats. Affected: GitHub Actions, CI/CD environments, software repositories
Keypoints :
- A vulnerability (CVE-2025-30066) was discovered in tj-actions/changed-files on March 14, 2025.
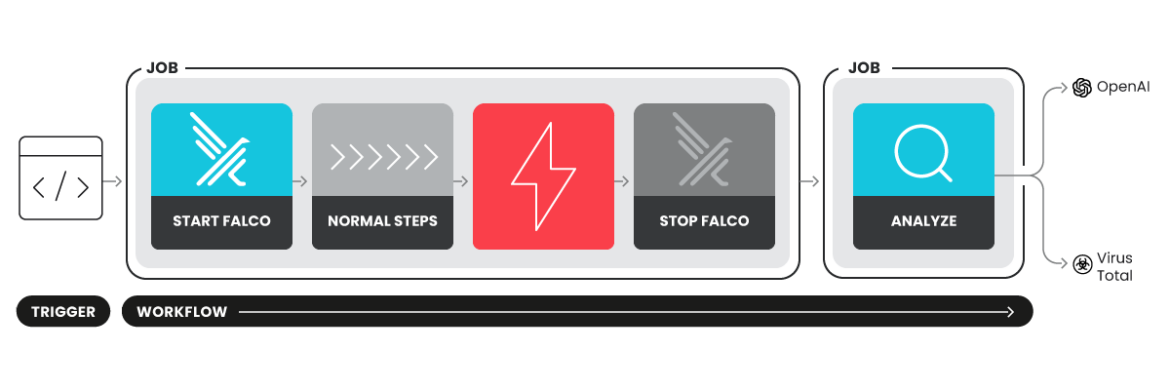
- Falco Actions is an open-source tool that monitors CI/CD workflows for threats in real time.
- The attack involved a compromised GitHub Personal Access Token, allowing unauthorized access to repositories.
- Memdump.py was used to extract sensitive information from the memory of the Runner.Worker process.
- Falco Actions can detect memory dumping activities, aiding quick identification of threats.
- Integration with GitHub workflows can be achieved through simple configuration of start and stop actions.
- Falco Actions generates detailed reports of detected threats during workflow runs.
- The analyze mode offers additional insights on runtime activities and external connections.
- Integration with services like VirusTotal and OpenAI enhances analysis and remediation.
- The vulnerability highlights the increasing risks of supply chain attacks in CI/CD environments.
MITRE Techniques :
- T1005 – Data from Local System: The attacker accessed the memory of the Runner.Worker process to retrieve sensitive information.
- T1055 – Process Memory Theft: The use of memdump.py indicates techniques involving memory dumping to extract credentials.
- T1036 – Masquerading: The attacker leveraged a compromised GitHub Personal Access Token to gain access to sensitive repositories.
Indicator of Compromise :
- [Domain] gist.githubusercontent.com
- [File] memdump.py
- [File] /proc/{pid}/mem
- [Hash] SHA256: 0b1fc4b9cb4a7d57d82aa4a65484fd46eb3dbf4d19c93cdbe4e4245e956ee3f2
- [IP Address] Not specified in the article.
Full Story: https://sysdig.com/blog/tj-actions-changed-files-with-falco-actions/
Views: 32