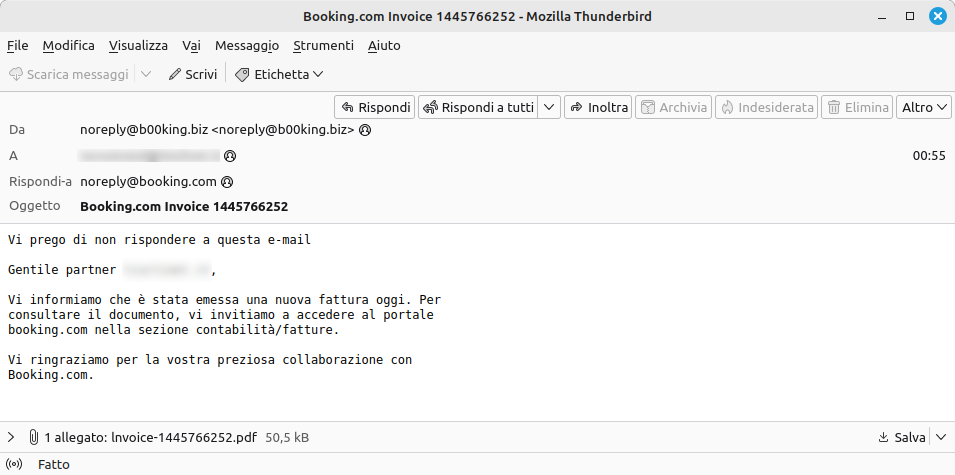
Recently, AgentTesla operators have strengthened their malspam campaigns in Italy, confirming the trend observed in recent months towards a greater use of PDF attachments. These documents contain links that, once used, initiate the download of files with malicious JavaScript code.
The email in question urgently urges the recipient to view the attached document in the communication. Upon opening the document, a fake error message appears that prompts the user to click on the Reload button. However, this action masks the real intent of initiating the download of a malicious JavaScript file.
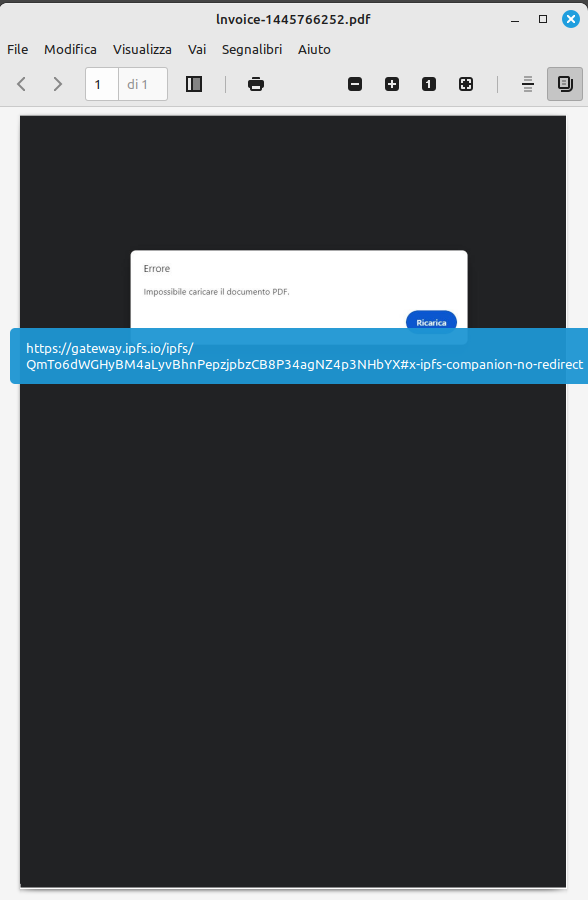
The downloaded file simulates being a PDF by using a double extension .pdf.js. Many spaces are strategically inserted between “.pdf” and “.js“, a clever trick aimed at hiding the true JS extension and concealing its intrinsic danger.
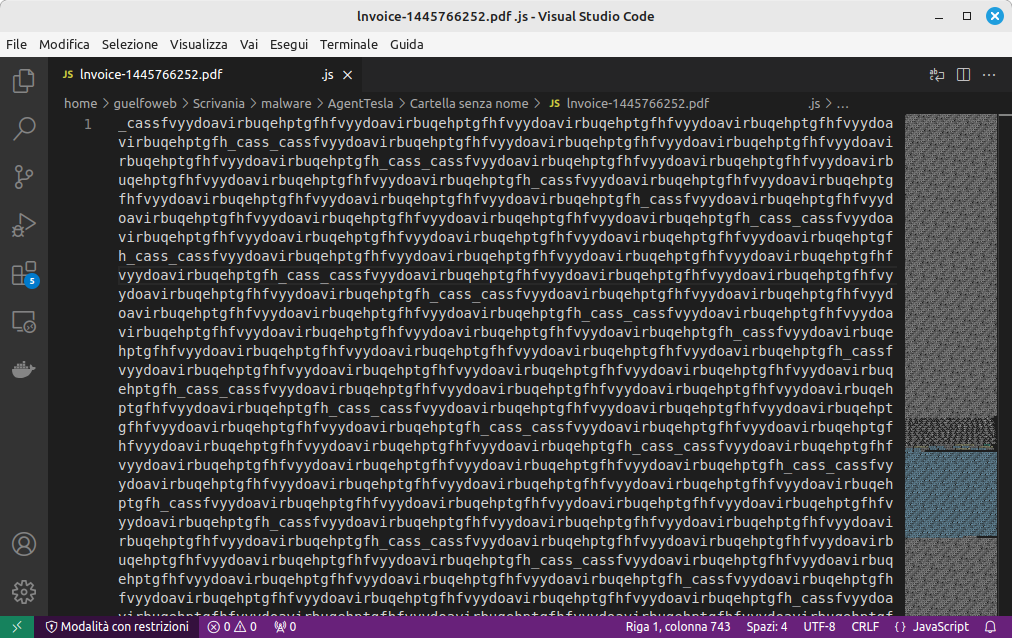
The deliberately obfuscated JavaScript code aims to download and execute a PowerShell script, taken from a Bitbucket repository. This script, in turn, contains binary values that, through simple substitutions, give life to the AgentTesla executable.
The details of the script decoding steps and the in-depth analysis of the AgentTesla sample in question are omitted, as no significant peculiarities emerge from there. However, the change in style adopted by the authors of AgentTesla in spreading the malware without using the usual compressed files containing the executable is particularly noteworthy.
The infection chain
The infection process can be effectively represented by the following graph:
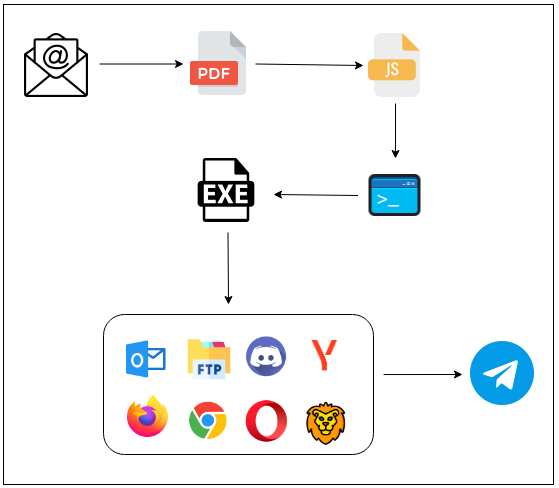
The AgentTesla executable
The binary generated by the PowerShell script is not saved to disk but is instead loaded and executed directly in memory. Only through a manual decoding operation is it possible to export the file for analysis.
The behavior remains unchanged, as confirmed by checks performed on 60 clients: browsers, email, FTP, and instant messaging.
ChromiumViewerCoowonChromeEdgeChromiumFirefoxSeaMonkeyThunderbiBlackHawkCyberfoxK-MeleonicecatPale MoonIceDragonWaterfoxPostboxFlockSafariFalkon BrowserOutlookIncrediMailEudoraFoxMailOpera MailMailbirdCoreFTPFTP NavigatorSmartFTPSWS_FTPFTPGetterDiscordTrillianPsi+MysqlWorkbenchInternet Downloader ManagerJDownloaderOpera SoftwareYanexBrowserIridiumChromiumChromePlusKometaAmigoBrave-BrowserCentBrowserChedotOrbitumSputnikDragonVivaldiCitrio360ChromeCozMedialiebaoElements BrowserEpic Privacy BrowserCocCocSleipnirSurfCoowon
Communications with C2: a Telegram Bot
In conclusion, information about the compromised machine, such as the hostname and hardware specifications, along with credentials extracted from the observed clients, is sent to a Telegram bot. This method of data transmission, already detected in numerous other AgentTesla campaigns, highlights a recurring strategy of exfiltrating information by exploiting instant messaging platforms to facilitate remote access to stolen data.
“Turnkey” access
AgentTesla plays a crucial role in the cybercrime ecosystem, serving as an initial entry point for more invasive and harmful operations. Once this malware successfully exfiltrates credentials and sensitive data from compromised systems, this information is often sold on the dark web by specialized intermediaries, better known as
Source: Original Post