Short Summary:
This article discusses a sophisticated phishing attack that impersonates a company’s human resources department. It highlights the tactics used by threat actors to deceive employees into clicking malicious links and entering their credentials on fake login pages. The article emphasizes the importance of vigilance and robust cybersecurity measures to combat such threats.
Key Points:
- Phishing attacks are becoming more sophisticated, targeting employees through impersonation.
- A recent phishing email mimics official HR communications, urging recipients to review an “Important: Revised Employee Handbook.”
- The email uses formal language and creates a sense of urgency to provoke quick action.
- Threat actors leverage psychological tactics, including fear of non-compliance, to manipulate recipients.
- Clicking on the embedded hyperlink leads to a fake login page that captures user credentials.
- The attack involves redirection to a legitimate-looking Microsoft login page after an error message is displayed.
- Indicators of compromise include specific URLs and IP addresses associated with the phishing campaign.
- Organizations must implement user awareness training and advanced email security solutions to mitigate risks.
MITRE ATT&CK TTPs – created by AI
- Phishing (T1566)
- Threat actors impersonate trusted entities to deceive users into providing sensitive information.
- Credential Dumping (T1003)
- Capturing user credentials through fake login pages.
- Redirection (T1071)
- Redirecting users to legitimate-looking login pages after capturing credentials.
By Sabi Kiss, Cofense Phishing Defense Center
Phishing attacks are becoming increasingly sophisticated, and the latest trend in attack strategies targeting employees highlights this evolution. In this blog post, we’ll dissect a recent phishing attempt that impersonates a company’s human resources department, and we’ll provide detailed insights to help you recognize and avoid falling victim to such scams.
This phishing email, which has been found in environments protected by Google, Outlook 365, and Proofpoint, is designed to look like an official communication from your company’s HR department. It arrives in your inbox with a subject line that grabs attention, urging you to review the Employee Handbook.
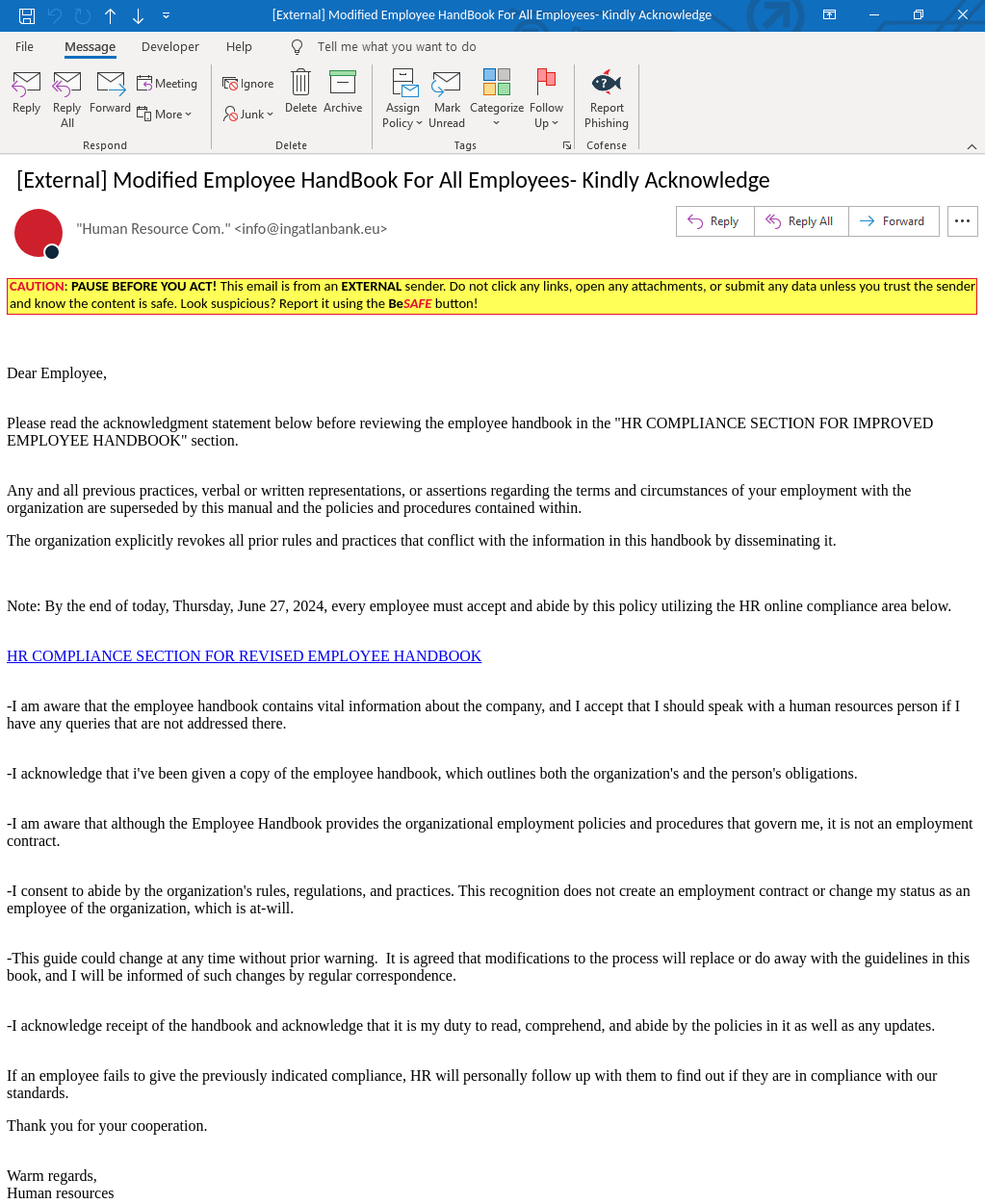
The email’s layout and language further enhance its perceived legitimacy. It opens with a formal greeting and presents a message in a structured format typical of corporate communications. The language used is professional, clear, and direct, mimicking the tone and style that employees would expect from an HR department.
The subject line, “Important: Revised Employee Handbook,” immediately grabs attention and creates a sense of urgency. This tactic is designed to provoke quick action from recipients, prompting them to open the email and engage with its contents without much hesitation.
The body of the email includes formal language and directives typical for corporate communications. It begins with a polite greeting and swiftly transitions into a directive to review a revised employee handbook. The email stresses the importance of compliance by a specific deadline, typically by the end of the day, fostering a sense of urgency and importance among recipients.
The primary goal of this phishing email is twofold: to lure recipients into clicking on the embedded hyperlink, and to trick them into entering their credentials on a fake login page. By appearing to originate from a trusted source (the employee’s HR department), the email leverages authority and urgency to persuade the recipient into taking immediate action without questioning the authenticity of the request.
The threat actor employs psychological tactics such as fear of non-compliance with company policies, and the promise of significant changes outlined in the handbook, to manipulate recipients into clicking on the malicious link. This psychological manipulation aims to override recipients’ natural scepticism and caution when handling unsolicited emails.
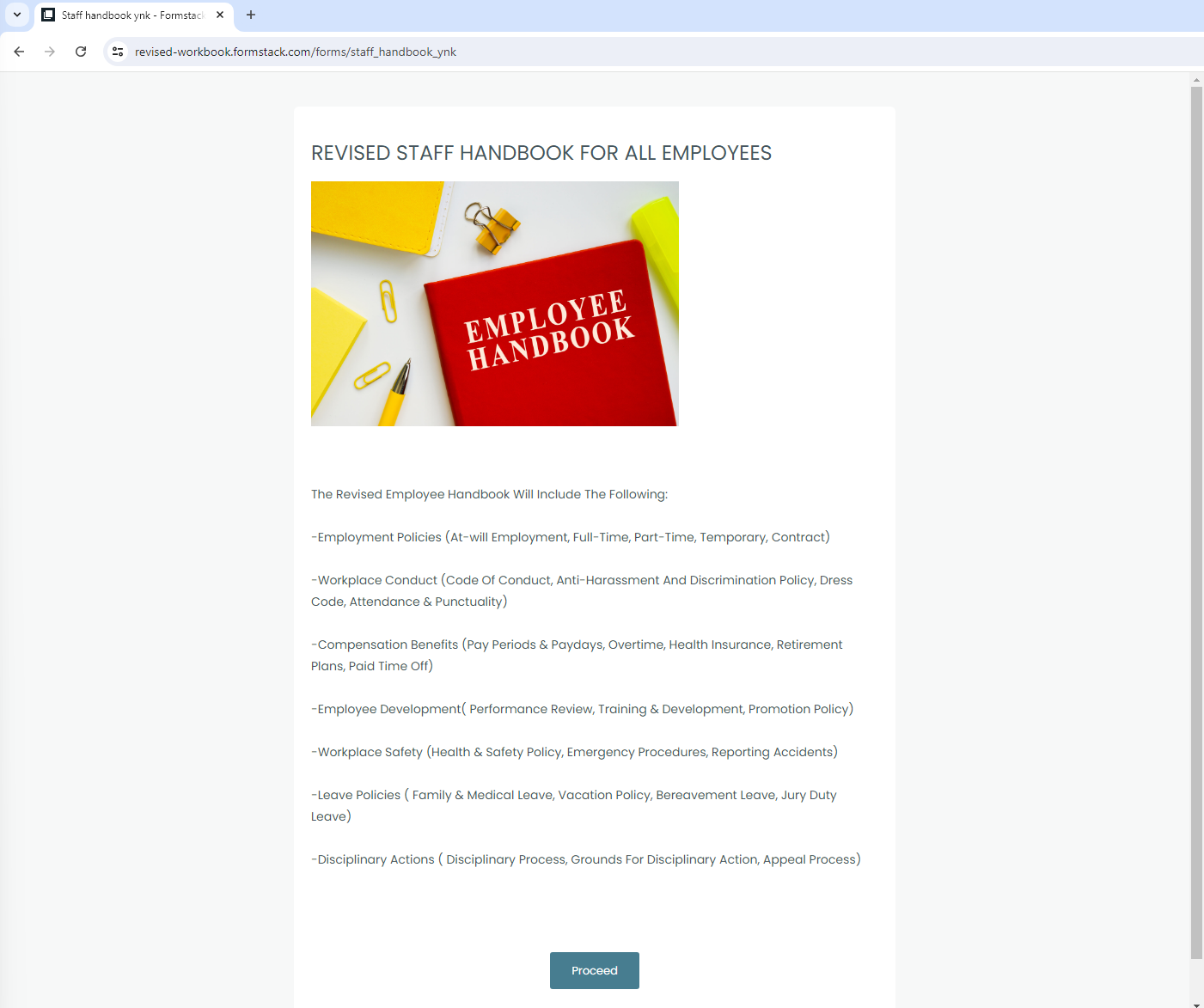
The email contains a hyperlink masked as the “HR COMPLIANCE SECTION FOR REVISED EMPLOYEE HANDBOOK.” Clicking on this link takes you to a page that mimics a legitimate document hosting site. Here, you are presented with a “PROCEED” button to continue.
Upon clicking “PROCEED” you are redirected to a page that appears to be branded by Microsoft. This is where the phishing attack becomes more sophisticated. The page asks for your Microsoft username, and it looks very convincing.
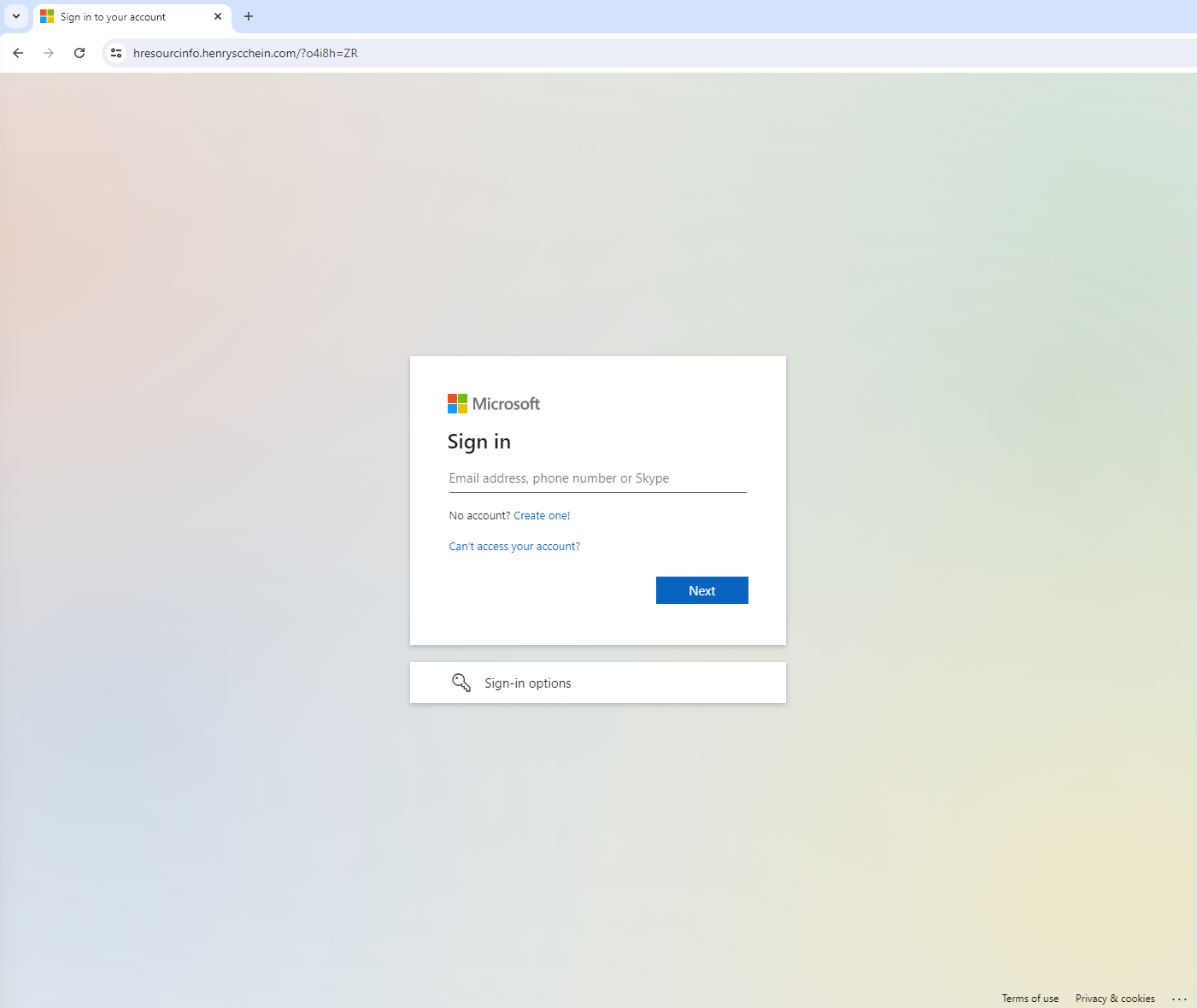
The threat actor’s strategy is to gain your trust by presenting a legitimate-looking website where you are prompted to log in with your company’s Microsoft credentials. Here is a detailed breakdown of what happens next:
- Capture of Credentials: When you enter your company email address and press next, you are redirected to what looks like your company’s Microsoft Office 365 login page.
- Error Message: After entering your username and potentially your password, you receive an error message stating, “There was an unexpected internal error. Please try again.” This message is a ruse.
- Redirection to Legitimate Login Page: You are then redirected to the actual company SSO/Okta login page, making you think there was a minor issue. In the meantime, the threat actor has captured your username and possibly your password.
|
Indicators of Compromise |
IP |
|
hXXps://hresourcinfo[.]henryscchein[.]com/?o4i8h=ZR |
104[.]236[.]9[.]231 |
|
hXXps://revised-workbook[.]formstack[.]com/forms/staff_handbook_ynk |
52[.]85[.]132[.]103 52[.]85[.]132[.]32 52[.]85[.]132[.]40 52[.]85[.]132[.]118 |
This phishing campaign exemplifies the growing sophistication of cyber threats that exploit trust and urgency within corporate environments. By mimicking legitimate HR communications and leveraging psychological manipulation, threat actors attempt to deceive employees into divulging sensitive information. Vigilance and robust cybersecurity measures, including user awareness training and advanced email security solutions, are crucial in mitigating such risks and protecting organizations from falling victim to phishing attacks. Strengthening defenses against phishing requires a multi-layered approach that combines technological solutions with empowered and vigilant employees as the first line of defense.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.
Source: https://cofense.com/blog/threat-actors-continue-to-utilize-hr-related-phishing-tactics