
DLL (Dynamic-Link Library) sideloading is a technique used by Threat Actors to infect users using legitimate applications which load malicious DLL files that spoof legitimate ones. Recently published a blog about Qakbot malware that leverages a calculator to perform DLL Sideloading.
Similarly, we came across a Twitter post wherein researchers mentioned a document file that performs DLL Sideloading using Microsoft applications such as “Teams.exe” and “OneDrive.exe.” The dropped DLL contains the C&C URL through which the malware can deliver a Cobalt-Strike beacon.
Cobalt Strike is a penetration testing product that allows Threat Actors (TAs) to deploy an agent named ‘Beacon’ on the victim machine. The Beacon provides various functionalities to TAs, including command execution, key logging, file transfer, SOCKS proxying, privilege escalation, mimikatz, port scanning, and lateral movement.
Several TAs are actively using this tool, from ransomware operators to espionage-focused Advanced Persistent Threats (APTs).
Upon analyzing the malicious doc file, we observed that it was targeting a company located in Italy that provides services such as Credit Servicing, Fund and Asset Management, and Real Estate services. The below figure shows the malicious document file content.
Technical Analysis
When opening the malicious document, it shows a security warning stating that macros have been disabled. The malware then requests the user to enable the content. Once enabled, the malicious document runs the macro code automatically in the background using the AutoOpen() function.
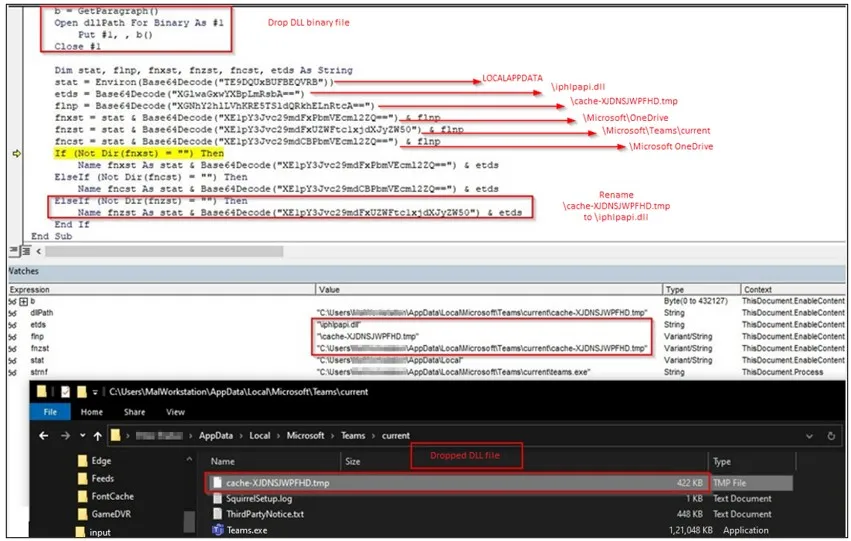
The malware then calls the function process(), which identifies the path of the OneDrive and Teams applications. The below figure shows the VBA macro code with the base64 decoded path of the OneDrive and Teams applications.

In the event that any of the application’s paths are identified by the malicious document, the malware drops a DLL file in that path with the name cache-XJDNSJWPFHD.tmp and renames it as iphlpapi.dll by calling the EnableContent() function as shown below.
Upon execution of the Teams application, the dropped malicious DLL file (“iphlpapi.dll”) is sideloaded, as shown below. sideloaded DLL malware, which creates a mutex with the name “MSTeams.Synchronization.Primitive.2.0″ to avoid running another instance on the same machine. The malware then communicates to the C&C server using the below URL: d2xiq5m2a8wmm4.cloudfront[.]net/communications.
While monitoring the malware’s traffic, Cyble has observed the C&C communication with the same URL mentioned above.
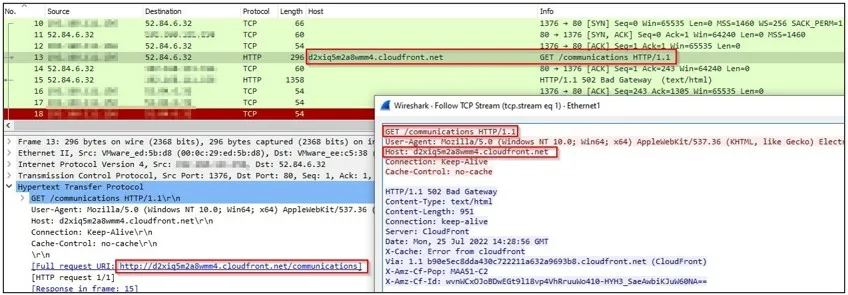
After analyzing the C&C URL: d2xiq5m2a8wmm4.cloudfront[.]net/communications, we concluded that it executes a Cobalt-Strike on the victim’s machine.
The Cobalt-Strike Beacon can be used for malicious activities such as downloading additional payloads, lateral movement, etc.
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| 697ac31e2336c340e46ae8a777f51cdb 91bd5585383685b82af8e801ce8f43586a797f49 92e7395073c6588e1d8172148525144189c3d92ed052a163b8f7fad231e7864c | MD5 SHA-1 SHA-256 | Malicious Doc |
| 6e1e6194dd00f88638d03db3f74bb48a d4a3050246d30a26671d05b90ffa17de39d5e842 ee56e43ed64e90d41ea22435baf89e97e9238d8e670fc7ed3a2971b41ce9ffaf | MD5 SHA-1 SHA-256 | Sideloaded DLL |
| d2xiq5m2a8wmm4.cloudfront.net | URL | Cobalt-Strike C&C URL |
| hxxps://laureati-prelios.azureedge[.]net/forms/Modulo_Testimone_Universitario_v3.doc | URL | Download URL |
Detection & Response:
Splunk:
source="WinEventLog:*" AND (((TargetFilename="*cache-XJDNSJWPFHD.tmp" OR TargetFilename="*iphlpapi.dll") AND (TargetFilename="*AppDataLocalMicrosoftTeamscurrent*" OR TargetFilename="*AppDataLocalMicrosoftOneDrive*")) OR ((Image="*Teams.exe") AND (CommandLine="*iphlpapi.dll*")))Qradar:
SELECT UTF8(payload) from events where (LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and (CATEGORYNAME(category) ILIKE 'File Created' or CATEGORYNAME(category) ILIKE 'Successful File Modification')) and ((("TargetFilename" ilike '%cache-XJDNSJWPFHD.tmp' or "TargetFilename" ilike '%iphlpapi.dll') and ("TargetFilename" ilike '%AppDataLocalMicrosoftTeamscurrent%' or "TargetFilename" ilike '%AppDataLocalMicrosoftOneDrive%')) or (("Image" ilike '%Teams.exe') and ("Process CommandLine" ilike '%iphlpapi.dll%')))Elastic Query:
((file.path.text:(*cache-XJDNSJWPFHD.tmp OR *iphlpapi.dll) AND file.path.text:(*AppDataLocalMicrosoftTeamscurrent* OR *AppDataLocalMicrosoftOneDrive*)) OR (process.executable.text:*Teams.exe AND process.command_line.text:*iphlpapi.dll*))CarbonBlack:
((filemod_name:(*cache-XJDNSJWPFHD.tmp OR *iphlpapi.dll) AND filemod_name:(*AppDataLocalMicrosoftTeamscurrent* OR *AppDataLocalMicrosoftOneDrive*)) OR (process_name:*Teams.exe AND process_cmdline:*iphlpapi.dll*))Fireeye:
(metaclass:`windows` ((filepath:[`*cache-XJDNSJWPFHD.tmp`,`*iphlpapi.dll`] filepath:[`AppDataLocalMicrosoftTeamscurrent`,`AppDataLocalMicrosoftOneDrive`]) OR (process:`*Teams.exe` args:`iphlpapi.dll`)))GrayLog:
((TargetFilename.keyword:(*cache-XJDNSJWPFHD.tmp *iphlpapi.dll) AND TargetFilename.keyword:(*AppDataLocalMicrosoftTeamscurrent* *AppDataLocalMicrosoftOneDrive*)) OR (Image.keyword:*Teams.exe AND CommandLine.keyword:*iphlpapi.dll*))Logpoint:
((TargetFilename IN ["*cache-XJDNSJWPFHD.tmp", "*iphlpapi.dll"] TargetFilename IN ["*AppDataLocalMicrosoftTeamscurrent*", "*AppDataLocalMicrosoftOneDrive*"]) OR (Image IN "*Teams.exe" CommandLine IN "*iphlpapi.dll*"))Microsoft Defender:
DeviceFileEvents | where (((FolderPath endswith "cache-XJDNSJWPFHD.tmp" or FolderPath endswith "iphlpapi.dll") and (FolderPath contains @"AppDataLocalMicrosoftTeamscurrent" or FolderPath contains @"AppDataLocalMicrosoftOneDrive")) or ((InitiatingProcessFolderPath endswith @"Teams.exe") and (InitiatingProcessCommandLine contains "iphlpapi.dll")))Microsoft Sentinel:
SecurityEvent | where EventID == 11 | where (((TargetFilename endswith 'cache-XJDNSJWPFHD.tmp' or TargetFilename endswith 'iphlpapi.dll') and (TargetFilename contains @'AppDataLocalMicrosoftTeamscurrent' or TargetFilename contains @'AppDataLocalMicrosoftOneDrive')) or ((Image endswith @'Teams.exe') and (CommandLine contains 'iphlpapi.dll')))RSA Netwitness:
(((TargetFilename contains 'cache-XJDNSJWPFHD.tmp', 'iphlpapi.dll') && (TargetFilename contains 'AppDataLocalMicrosoftTeamscurrent', 'AppDataLocalMicrosoftOneDrive')) || ((Image contains 'Teams.exe') && (CommandLine contains 'iphlpapi.dll')))SumoLogic:
(_sourceCategory=*windows* AND (((("cache-XJDNSJWPFHD.tmp" OR "iphlpapi.dll") AND ("AppDataLocalMicrosoftTeamscurrent" OR "AppDataLocalMicrosoftOneDrive")) OR ((Image = "*Teams.exe") AND (CommandLine = "*iphlpapi.dll*")))))Source/Credits: http/blog.cyble.com/2022/07/27/targeted-attacks-being-carried-out-via-dll-sideloading/