Key Point :
– Proofpoint identified multiple YouTube channels distributing malware by promoting cracked and pirated video games and related content.
– The video descriptions include links leading to the download of information stealers.
– The activity likely targets consumer users who do not have the benefits of enterprise-grade security on their home computers.
——————————
——————————
Key takeaways
- Proofpoint identified multiple YouTube channels distributing malware by promoting cracked and pirated video games and related content.
- The video descriptions include links leading to the download of information stealers.
- The activity likely targets consumer users who do not have the benefits of enterprise-grade security on their home computers.
Overview
Threat actors often target home users because they do not have the same resources or knowledge to defend themselves from attackers compared to enterprises. While the financial gain might not be as large as attacks perpetrated on corporations, the individual victims likely still have data like credit cards, cryptocurrency wallets, and other personal identifiable information (PII) stored on their computers which can be lucrative to criminals.
Proofpoint Emerging Threats has observed information stealer malware including Vidar, StealC, and Lumma Stealer being delivered via YouTube in the guise of pirated software and video game cracks. The videos purport to show an end user how to do things like download software or upgrade video games for free, but the link in the video descriptions leads to malware. Many of the accounts that are hosting malicious videos appear to be compromised or otherwise acquired from legitimate users, but researchers have also observed likely actor-created and controlled accounts that are active for only a few hours, created exclusively to deliver malware. Third-party researchers have previously published details on fake cracked software videos used to deliver malware.
The distribution method is particularly notable due to the type of video games the threat actors appear to promote. Many of them appear to be targeted to younger users including games popular with children, a group that is less likely to be able to identify malicious content and risky online behaviors.
During our investigation, Proofpoint Emerging Threats reported over two dozen accounts and videos distributing malware to YouTube, which removed the content.
Example account
The following is an example of a suspected compromised account (or potentially sold to a new “content creator”) used to deliver malware. Indicators of a suspected compromised or otherwise acquired account include significant gaps of time between the videos posted, content that vastly differs from previously published videos, differences in languages, and descriptions of the videos containing likely malicious links, among other indicators.
The account has around 113,000 subscribers, and the account displays a grey check mark which indicates the account owner has met verified channel requirements including verifying their identity.
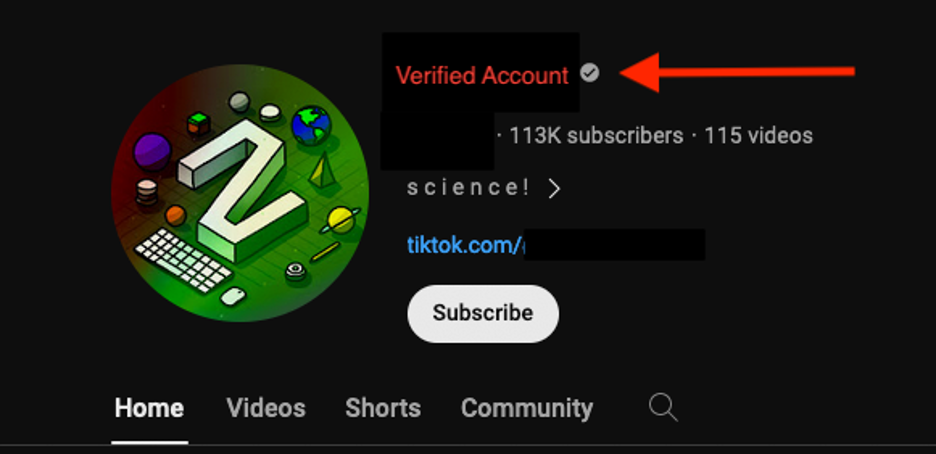
Example of a verified YouTube account with a large following, suspected to be compromised.
When Proofpoint researchers identified the account, the majority of the account’s videos had been posted one year or more previously, and all had titles written in Thai. However, when the account was identified, twelve (12) new English language videos had been posted within a 24-hour period, all related to popular video games and software cracks. All of the new video descriptions included links to malicious content. Some of the videos had over 1,000 views, possibly artificially increased by bots to make the videos seem more legitimate.
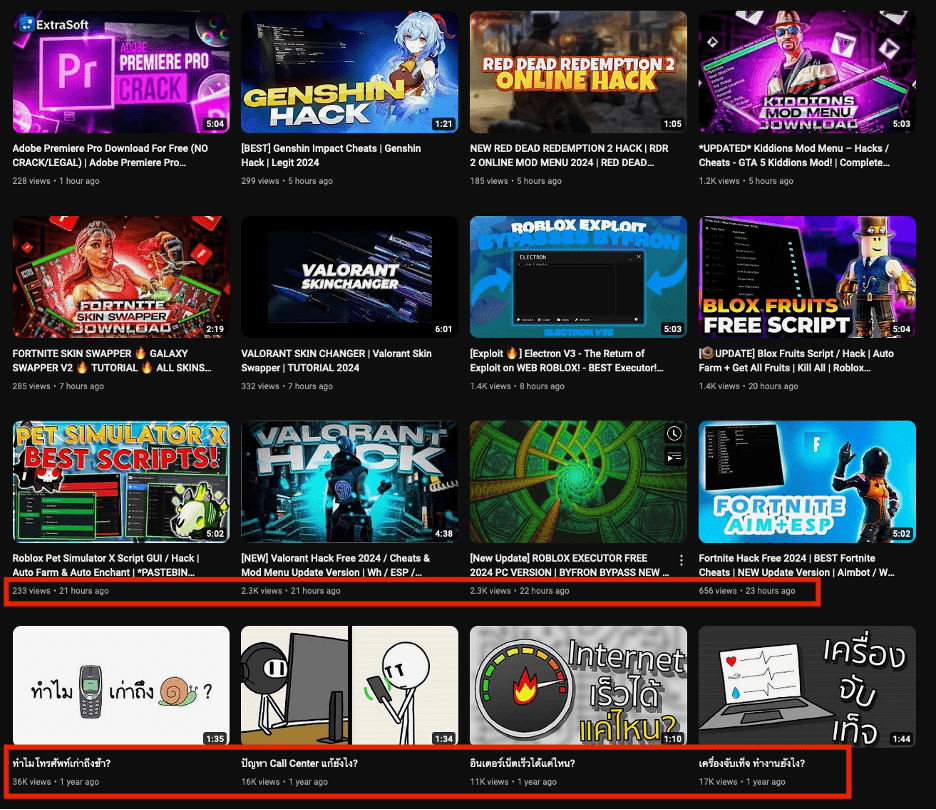
Screenshot of a suspected compromised YouTube account distributing malware comparing upload dates.
In one example, a video purported to contain a character enhancement for a popular video game with a MediaFire link in the description. The MediaFire URL led to a password-protected file (Setup_Pswrd_1234.rar) containing an executable (Setup.exe) that, if executed, downloaded and installed Vidar Stealer malware.
The video was uploaded to the suspected compromised account seven (7) hours prior to our investigation. Around the same time the video was posted, several comments purported to attest to the legitimacy of the software crack. It is likely those accounts and comments were created by the video uploader or their collaborators to lend authenticity to the malicious link.
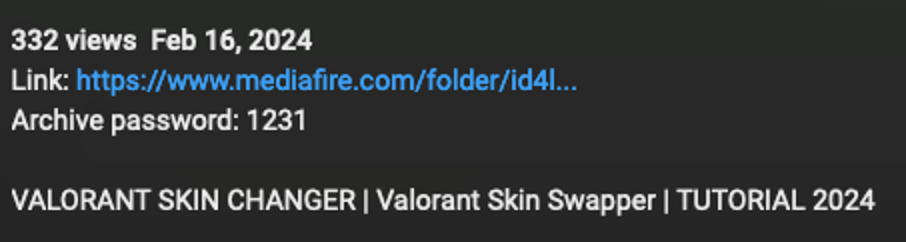
Video description containing a MediaFire URL leading to Vidar Stealer.
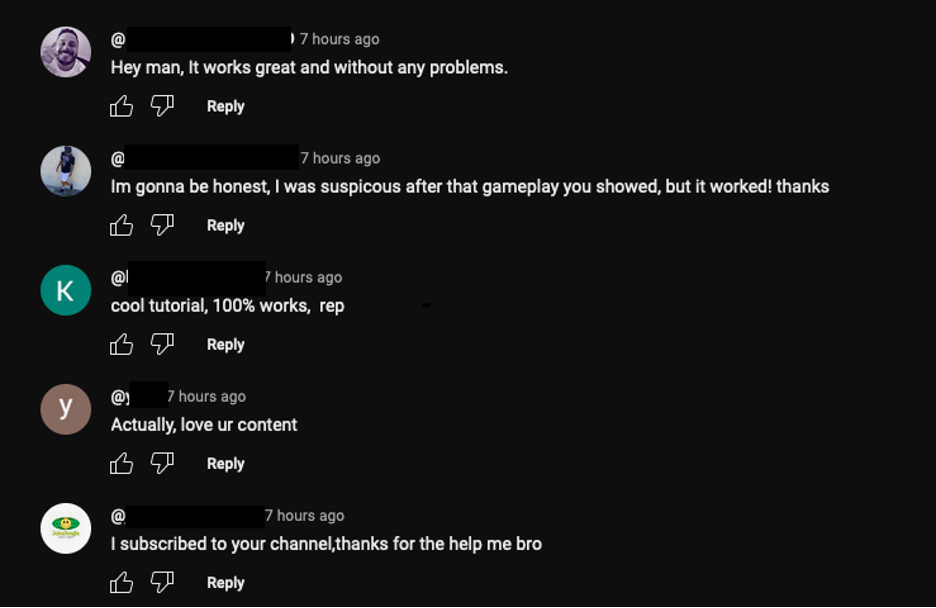
Comments on the video purporting to confirm the legitimacy of the URL.
In another example from a video uploaded to a different account, the video description was more verbose. The description contained a malicious MediaFire URL also leading to Vidar Stealer, as well as some additional tips. This is a common example that includes instructions on how to disable Windows Defender or other antivirus products. The video creator promises that the “files are completely clean” which does instill a lot of trust (sarcasm)!
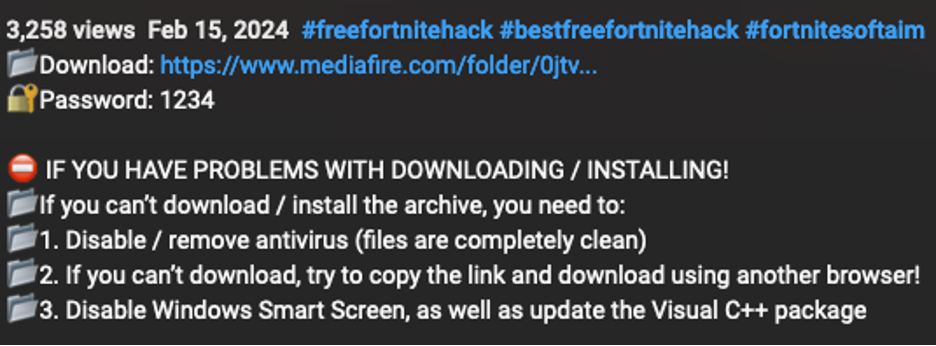
Screenshot of a video description that includes instructions to disable antivirus.
Empress impersonation
Proofpoint identified multiple videos purporting to distribute Empress video game cracks. Empress is an entity who is well known in the software piracy community. In one example, a user purported to distribute cracked “League of Legends” content on the video sharing platform. The video description contained a Telegram URL that led to a post containing instructions on how to download the content, and a MediaFire URL leading to a RAR archive containing an executable. The file was named “empress.exe” to appear to come from the popular software piracy resource and appear to be “legitimate”.
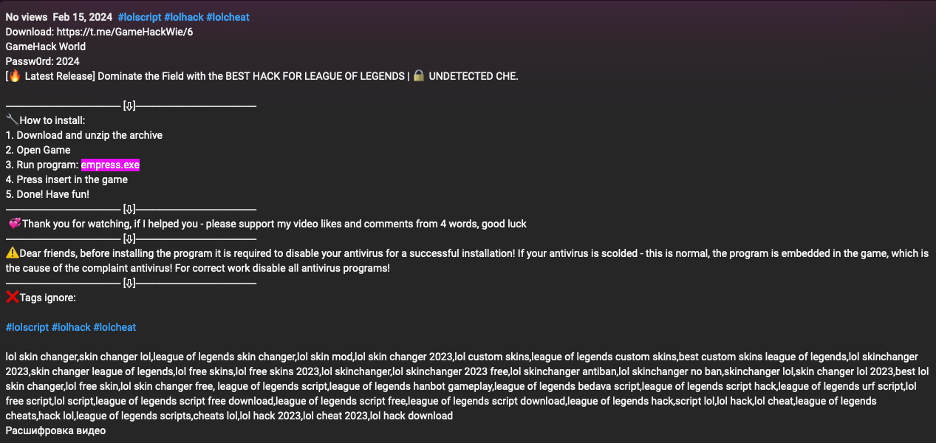
YouTube description advertising empress.exe.
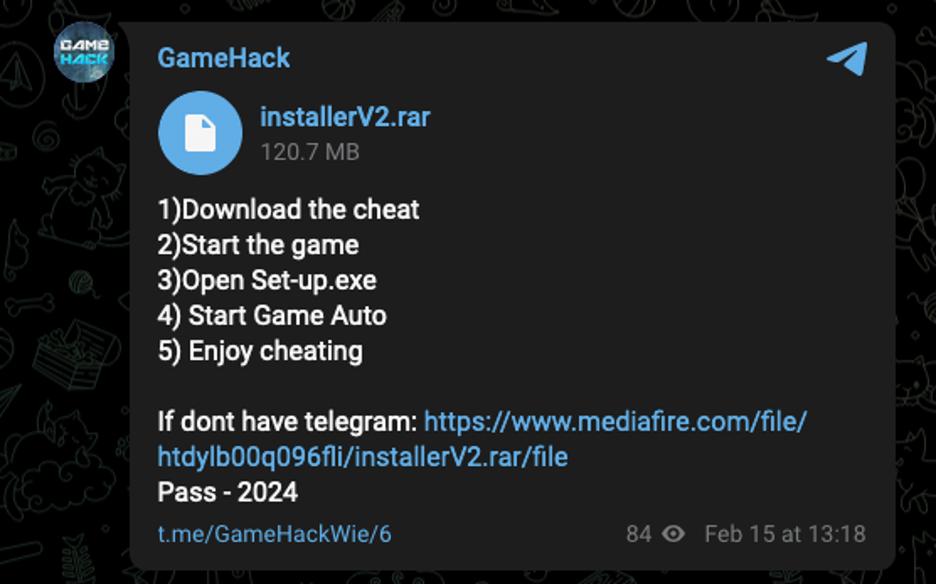
Telegram link from Empress video.
The identified videos using the “Empress” themes contained visual instructions on how to download and install the file—which was actually Vidar Stealer malware —to make it easy for the victim to follow along.
Malware details and C2 activity
In all observed cases of malware distribution via YouTube videos containing MediaFire URLs to password-protected compressed executables, the .rar file was small, but the compressed payload always expanded to around 800 MB. This can indicate there is a significant amount of padding in the executable. This is a common antivirus/sandbox evasion technique as many tools will not scan large files.
Opening the file in a hex editor confirms this assessment, as you can see a significant amount of repeating hex bytes throughout a good portion of the payload.
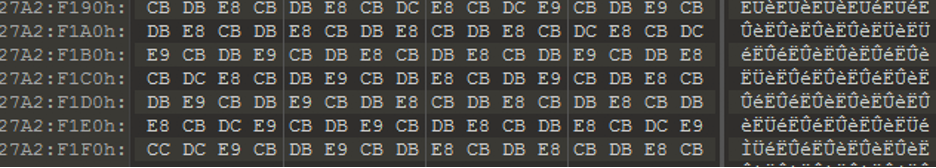
Repeating bytes identified in a hex editor.
Sandbox detonation reveals that the payload is Vidar. Vidar uses social media and community forums to receive command and control (C2) instructions including Telegram, Steam Community, and Tumblr. In all cases, the C2 account is created with a username or account description containing a set of alphanumeric characters followed by an IP address ending with a vertical pipe.
In the example of the previously identified “empress.exe” file, the Steam and Telegram C2 samples both have different C2 IP destinations but have the same leading identifier “got4a”.
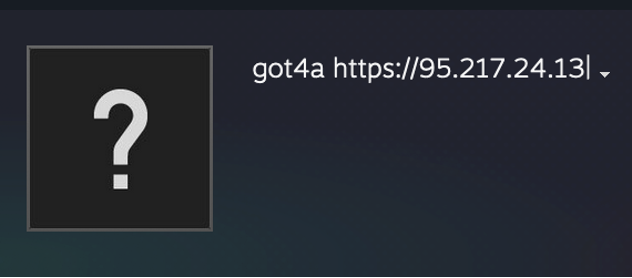
Steam C2 profile.

Telegram C2 profile.
After the C2 IP address is retrieved, we observed standard Vidar/StealC C2 activity within three seconds.
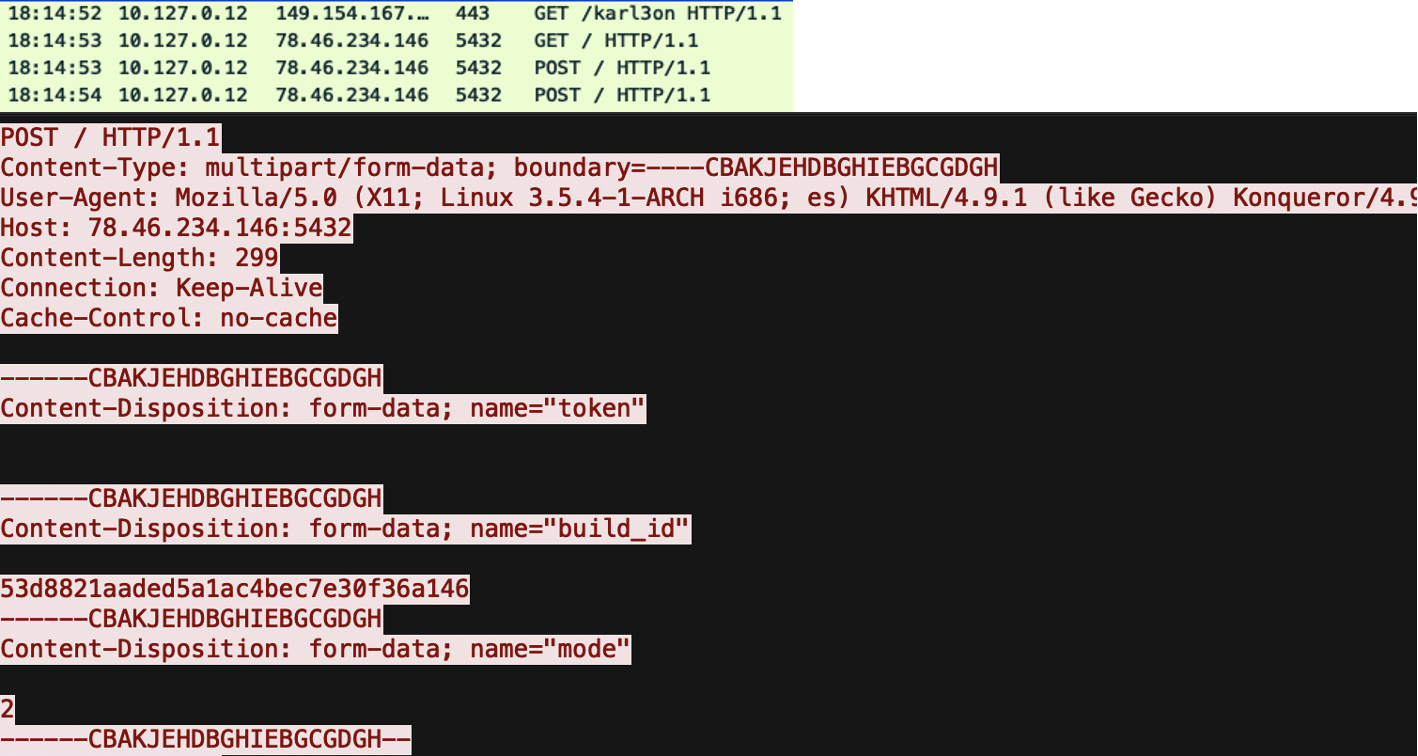
Vidar Stealer C2 check-in PCAP.
Using social platforms for C2 can enable malware to hide in network traffic, as connections to these websites may not immediately appear suspicious.
Discord server distribution
Another payload distribution method via YouTube video descriptions that differs from MediaFire URLs is Discord URLs. Proofpoint observed threat actors creating and managing a Discord server that has different malware for each game. The Discord link in the video description will direct users to a Discord channel that hosts the files available for download and includes instructions on how to download and install them.
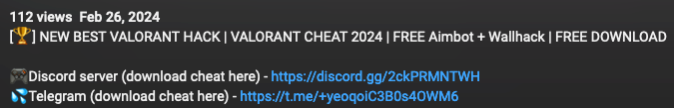
YouTube Video description containing a Discord link.
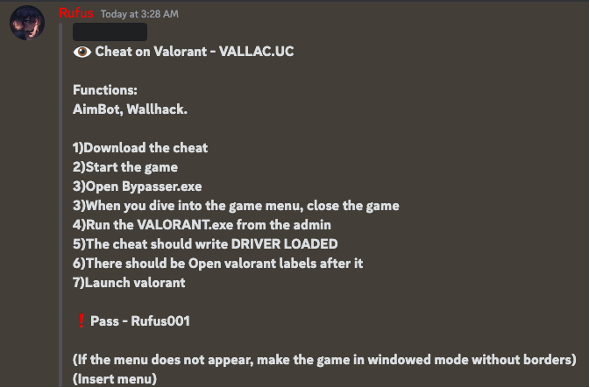
The link leads to a Discord post from the threat actor.
Another post on the Discord server instructs users to disable antivirus in order to download the game cheat.
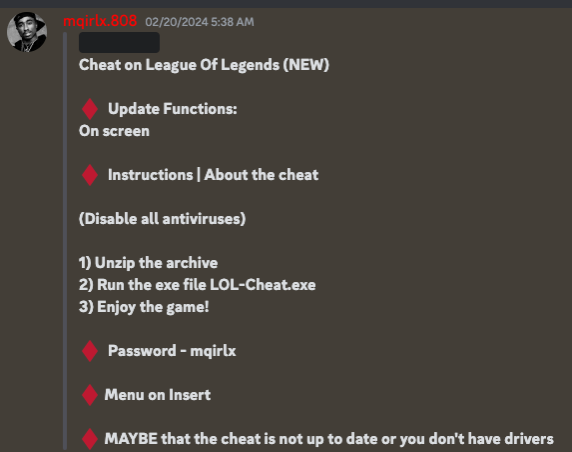
Instructions on how to download a game cheat including disabling antivirus.
There are multiple files available to download on the Discord server, and they are associated with different video games. The above post leads to “valoskin.zip” a compressed executable that leads to malware. Ultimately, the payloads on this server delivered Lumma Stealer. Here is a screenshot of some of the C2 traffic from the executables.
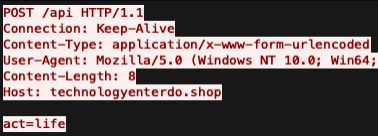
Lumma C2 traffic – detected by Emerging Threats SID 2049836.
Notably, the Discord server administrator appears to update the payloads every few weeks.
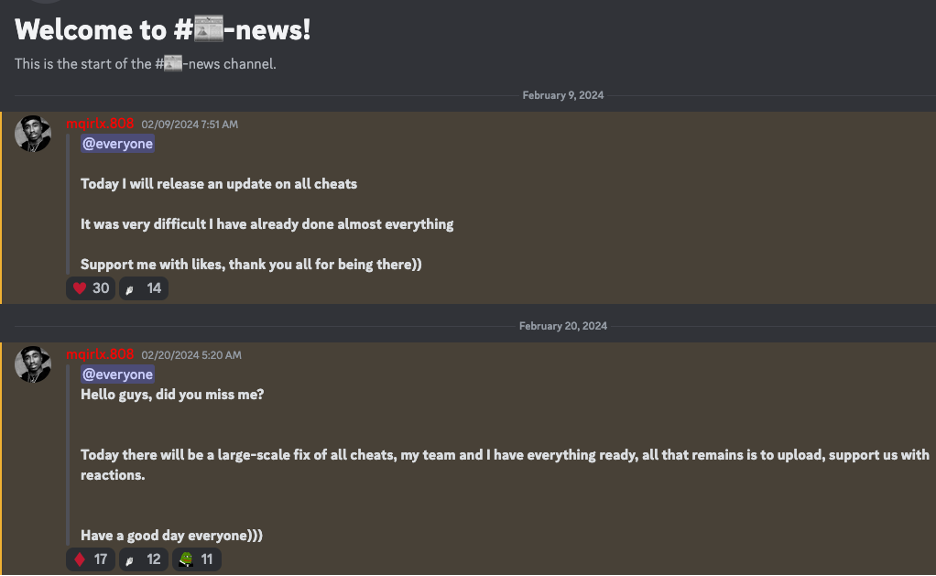
Posts from the Discord server administrator posting when new “cheats” are released.
List of “supported” games.
Conclusion
Proofpoint observed multiple distinct activity clusters distributing information stealers via YouTube, and does not attribute the activity to a tracked threat actor or group. The techniques used are similar, however, including the use of video descriptions to host URLs leading to malicious payloads and providing instructions on disabling antivirus, and using similar file sizes with bloating to attempt to bypass detections. Based on the similarities of the video content, payload delivery, and deception methods, Proofpoint assesses that the actors are consistently targeting non-enterprise users.
Proofpoint does not currently have visibility on how the identified YouTube accounts may have been compromised and YouTube has been quick to remove accounts reported by the Proofpoint Research team.
End users should be aware of the techniques used by threat actors to entice users into engaging with video game content purported to help them cheat or bypass paid functionality.
Indicators of compromise
Indicator | Description | Family | First Seen |
dd0f7e40960943820da54ef28e1ffafb | spoofer.exe | Lumma | 2024/03/04 |
2c1e42d5e1eaf851b3b1ce14f6646a94 | Ring-1.exe | Lumma | 2024/03/08 |
e1f4c125e7ec9e784198518ade924a40 | bypasser.exe | Lumma | 2024/02/26 |
679dff0691158b5367ef511a57e7a1fc | VALORANT.exe | Lumma | 2024/02/26 |
477a4bbb17eb966c637f1fbdb5219fbf | setup.exe | Vidar | 2024/02/16 |
82574182bfe062e72bb750ee1e641e08 | Setup_Pswd_1234.rar | Vidar | 2024/02/16 |
associationokeo[.]shop | C2 Domain | Lumma | 2024/02/20 |
detectordiscusser[.]shop | C2 Domain | Lumma | 2024/02/21 |
edurestunningcrackyow[.]fun | C2 Domain | Lumma | 2024/03/05 |
lighterepisodeheighte[.]fun | C2 Domain | Lumma | 2024/03/05 |
pooreveningfuseor[.]pw | C2 Domain | Lumma | 2024/02/20 |
problemregardybuiwo[.]fun | C2 Domain | Lumma | 2024/02/20 |
sideindexfollowragelrew[.]pw | C2 Domain | Lumma | 2024/01/10 |
technologyenterdo[.]shop | C2 Domain | Lumma | 2024/02/21 |
turkeyunlikelyofw[.]shop | C2 Domain | Lumma | 2024/02/20 |
hxxps://mediafire[.]com/folder/ol5512r4mova/Setup | Payload URL | Vidar | 2024/02/16 |
hxxps://t[.]me/karl3on | C2 URL | Vidar | 2024/02/16 |
hxxps://steamcommunity[.]com/profiles/76561199637071579 | C2 URL | Vidar | 2024/02/16 |
Emerging Threats signatures
Vidar
2036316, 2038523, 2038524, 2049203, 2038525, 2035873, 2043334, 2033066, 2044788, 2025431, 2035911, 2029236, 2034813, 2047626, 2047627, 2044245, 2044244, 2044246, 2044249, 2044248, 2044247, 2049087, 2036667, 2033163, 2036654, 2049253, 2047625, 2044243, 2851826, 2853039, 2853038, 2842708, 2855525, 2841407, 2841237, 2841406
Lumma
2050952, 2050957, 2050996, 2050999, 2051473, 2051480, 2051544, 2051547, 2051551, 2051555, 2051470, 2051477, 2051545, 2051548, 2051549, 2051553, 2050953, 2050958, 2050974, 2050976, 2051552, 2051556, 2050955, 2050960, 2051482, 2051483, 2049958, 2049959, 2050998, 2051001, 2050956, 2050961, 2048936
“An interesting youtube video that may be related to the article above”
Views: 0

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português