
EXECUTIVE SUMMARY
A critical vulnerability, identified as CVE-2024-3273, has been discovered in certain end-of-life (EOL) D-Link NAS devices, presenting a severe threat due to the lack of ongoing support and their high susceptibility to attacks. With a CVSS base score of 9.8, this vulnerability is extremely serious, potentially allowing unauthorized access, data theft, system modifications, or denial of service attacks. The urgency to decommission these devices is crucial to protect data integrity and security. The risk is exacerbated by the fact that threat actors on underground forums are actively discussing this vulnerability and sharing IP addresses of affected D-Link NAS devices. This concerning development highlights the immediate need for organizations to mitigate the vulnerability and retire or replace these compromised devices to safeguard their data and infrastructure.
It has also been observed that the attacks are originating from IP addresses associated with Russia and China. Historically, Chinese state-sponsored APT groups such as Camaro Dragon (aka Mustang Panda) have utilized similar firmware implants customized for routers to carry out malicious cyber-attacks. Another Chinese-backed hacking group, Volt Typhoon, is also reportedly involved in network attacks against high-value targets.
INTRODUCTION
CVE-2024-3273 is a critical vulnerability affecting certain end-of-life (EOL) D-Link NAS devices, this vulnerability can result in unauthorized access, data theft, system modifications, and denial of service attacks. These NAS devices, designed for network-attached storage, enable users and organizations to connect them to local networks for customizable and remote data access, primarily for backing up critical and sensitive information. This vulnerability has been promptly added to the Known Exploited Vulnerabilities catalogue, highlighting its active exploitation.
KEY TAKEAWAYS AND ACKNOWLEDGEMENTS
Key Takeaways:
- Hackers are actively exploiting the vulnerability, evidenced by the sharing of affected device IP addresses on underground forums, posing a significant risk to users.
- A search engine indicates approximately 90446 results for purportedly affected D-Link NAS devices.
- CVE-2024-3273, identified as a critical security vulnerability due to hard-coded credentials, was added to CISA’s Known Exploited Vulnerabilities catalogue on May 2, 2024.
- D-Link NAS devices, extensively utilized for data backup purposes, are particularly vulnerable to the CVE-2024-3273 exploit, with notable impacts observed in the United Kingdom, Russia, Germany, Italy, USA, and France.
Acknowledgements:
The CYFIRMA Research team acknowledges security researchers who responsibly disclosed this vulnerability.
VULNERABILITY AT A GLANCE
Vulnerability Type: Command injection
CVE ID: CVE-2024-3273
CVSS Severity Score: 9.8 (Critical)
Application: D-Link NAS
Impact: Allowing to perform root privileges
Severity: Critical
Affected Versions: D-Link DNS-320L, DNS-325, DNS-327L and DNS-340L up to 20240403
Patch Available: NO
DESCRIPTION
CVE-2024-3273 allows remote attackers to take control of end-of-life (EOL) network
attached storage (NAS) devices, such as the DNS-320L, DNS-325, DNS-327L, and DNS-340L. D-Link has indicated that this vulnerability affects all of its EOL NAS devices. This issue potentially exposes over 92,000 hosts. D-Link NAS devices provide network-attached storage, enabling users and organizations to connect these devices to local networks for customizable and remote data access, often used for backing up critical and sensitive data. Exploitation of this vulnerability could result in data theft or destruction, significantly impacting the security of users’ data storage solutions.
IMPACT
The vulnerability allows remote attackers to take control of affected devices due to hardcoded, password-less credentials and a command injection flaw. This can lead to data theft or destruction on D-Link NAS devices, posing significant risks for sensitive data storage. Attackers could also store malicious data or tools on compromised devices. NAS devices serve as centralized storage on a network, offering convenient and reliable data access with their own processing capabilities and operating systems.
AFFECTED VERSIONS
According to D-Link, this vulnerability impacts the EOL NAS device models DNS-320L, DNS-325, DNS-327L, and DNS-340L, and potentially all its EOL NAS devices. This vulnerability poses a significant risk to users who depend on these devices for data storage. For more information, click here
SECURITY INDICATORS
Is there already an exploit tool to attack this vulnerability?
Yes, there have been reports indicating that the CVE-2024-3273 vulnerability has been actively exploited in attacks. Hackers have attempted to execute Mirai malware on vulnerable D-Link NAS devices, targeting multiple CPU architectures in the hope of successfully compromising the devices. This highlights the severity of the vulnerability and the urgency for users to address it promptly to prevent potential exploitation and compromise of their NAS devices.
Has this vulnerability already been used in an attack?
Yes, in addition to discussing the vulnerability in underground forums, hackers are also sharing tactics, techniques, and procedures (TTPs) for exploiting the CVE-2024-3273 vulnerability in the Deep/Dark Web. They may also be exchanging or selling exploit tools and services related to this vulnerability, increasing the potential for widespread attacks on vulnerable D-Link NAS devices.
Are hackers discussing this vulnerability in the Deep/Dark Web?
Yes, hackers are actively discussing the CVE-2024-3273 vulnerability in the Deep/Dark Web, with reports of discussions and sharing of affected device IP addresses in underground forums.
What is the attack complexity level?
The attack complexity level for CVE-2024-3273 in D-Link NAS is assessed as Critical.
EXPLOIT AND ANALYSIS
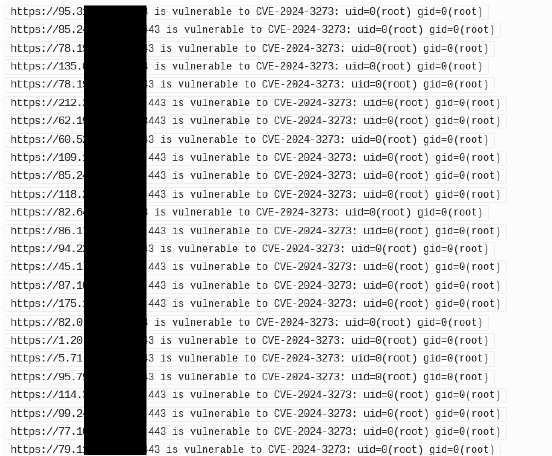
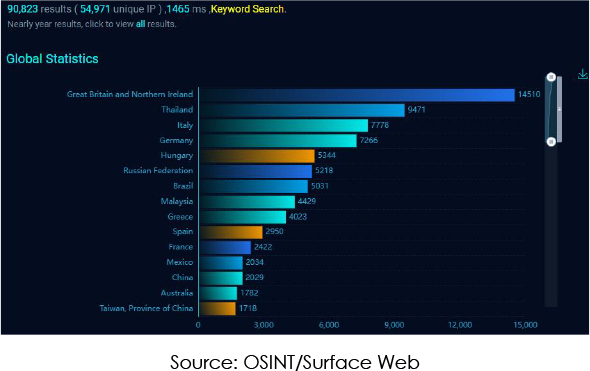
Our investigation has unveiled a critical vulnerability impacting D-Link NAS devices. Through our research, we have identified 90446 publicly accessible instances of D-Link NAS out of which 54845 unique IP that may be vulnerable to this flaw.
The CVE-2024-3273 command injection vulnerability affects end-of-life network-attached storage (NAS) devices, which are commonly used by end users. This vulnerability is exploited through Common Gateway Interface (CGI) binaries, specifically nas_sharing.cgi and orospucoc.cgi, which execute arbitrary commands on the system. The attack leverages a pre-configured system user named messagebus, which has no password. This user is typically used for system processes and should not be able to log in, but due to a logic flaw, the empty password is not correctly validated, allowing unauthorized access.
The exploit involves crafting an HTTP GET request where the payload is base64 encoded and injected into the system parameter. For example, the command echo hello is encoded as ZWNobyBoZWxsbw== and included in the URL: /cgi-bin/nas_sharing.cgi?user=messagebus&passwd=&cmd=15&system=ZWNobyBoZWxsbw==. Similar requests can be made to /cgi-bin/orospucoc.cgi and /.most/orospucoc.cgi.
Exploiting this vulnerability can lead to full system compromise, data exfiltration, and integration of the device into a botnet. Mitigation measures include updating the device firmware if available, isolating vulnerable devices from critical networks, and disabling or restricting access to vulnerable CGI binaries. This underscores the importance of proper network segmentation to protect against such vulnerabilities.
MITIGATION
D-Link US is unable to offer support for these end-of-life (EOL) or end-of-service (EOS) products. If your device was provided by a licensed carrier (service provider) and includes firmware modifications, please contact your carrier directly for support. It’s important to note that some devices on this list may have available third-party open firmware. However, D-Link does not endorse or provide support for open firmware, as its use voids any warranty and becomes the sole responsibility of the device owner.
EXTERNAL THREAT LANDSCAPE MANAGEMENT (ELTM)
Target Geography:
Organizations worldwide, especially those running affected versions susceptible to this exploit, face substantial risk. This vulnerability extends across geographical regions, affecting countries such as the United Kingdom, Russia, Germany, Italy, and France. Regardless of their location, organizations globally may encounter exploitation risks if they employ the vulnerable servers. Hence, it is crucial for organizations to promptly address this vulnerability to protect their data and infrastructure from potential cyber threats.
Target Industry:
The CVE-2024-3273 vulnerability poses a significant threat to organizations across various sectors, including banking, healthcare, software manufacturing, and more. These industries heavily rely on D-Link NAS devices for their automation requirements. Malicious actors with knowledge of this vulnerability may strategically target specific sectors, taking into account the perceived value of the data or services facilitated by these industries. Therefore, it is imperative for organizations in these sectors to enhance their external threat landscape management (ETLM) strategies. This includes implementing robust security measures, conducting regular vulnerability assessments, and ensuring timely patching and updates to safeguard critical data and infrastructure from malicious attacks.
Target Technology:
The vulnerability poses a significant threat to organizations relying on Network-Attached Storage (NAS) devices for their data storage and access needs. D-Link NAS devices use ARM or Intel processors, multiple drive bays for HDDs or SSDs, and Gigabit Ethernet for connectivity. They run a customized OS supporting file systems like NTFS and EXT4, file-sharing protocols like SMB and NFS, RAID configurations for redundancy, and user authentication for security. Therefore, it is crucial for organizations to enhance their external threat landscape management (ETLM) strategies specifically tailored to NAS devices. This includes implementing robust security measures, conducting regular vulnerability assessments, and ensuring timely patching and updates to mitigate the risk of exploitation and safeguard critical data and infrastructure from malicious attacks.
INDICATORS OF COMPROMISE (IOCS)
We’ve identified malicious IP addresses associated with attacks targeting D-Link Multiple NAS vulnerabilities:
- 195[.]1[.]144[.]109
- 80[.]94[.]92[.]60
- 45[.]142[.]182[.]70
- 195[.]1[.]144[.]107
- 45[.]128[.]232[.]229
- 183[.]81[.]169[.]139
- 89[.]190[.]156[.]248
- 5[.]10[.]250[.]35
- 193[.]35[.]18[.]142
- 103[.]245[.]236[.]120
- 39[.]106[.]15[.]3
- 81[.]71[.]150[.]157
- 183[.]249[.]224[.]224
- 121[.]229[.]47[.]93
- 183[.]129[.]150[.]114
- 117[.]66[.]222[.]122
- 14[.]225[.]53[.]162
- 54[.]254[.]93[.]204
- 114[.]132[.]210[.]77
- 114[.]132[.]210[.]77
- 59[.]26[.]247[.]22
- 114[.]67[.]183[.]11
- 14[.]225[.]218[.]2
- 139[.]59[.]241[.]87
- 47[.]120[.]10[.]39
UNDERGROUND AND DARK WEB FORUMS
There are active discussions focused on exploiting the vulnerability discovered in D-Link NAS devices. Forum members are contemplating the possibility of selling exploits related to this vulnerability. Furthermore, they are analysing the technical details and potential consequences of a proof-of-concept (PoC) associated with this exploit, indicating the serious attention this vulnerability has garnered among malicious actors in the cybercriminal community.
CONCLUSION
The active discourse surrounding the exploitation of the vulnerability in D-Link NAS devices within underground forums underscores the seriousness of the threat. The willingness of forum members to discuss selling exploits related to the vulnerability, along with the detailed analysis of associated proof-of-concepts, highlights the potential for widespread exploitation. This situation emphasizes the urgent need for users and organizations to prioritize patching and securing their D-Link NAS devices to mitigate the risk of exploitation and protect their data and infrastructure from malicious attacks.