Remember ‘.tprc’, the cyber scourge that sent shivers down spines in 2021? It seems this digital phoenix has risen from the ashes, reborn in a new, even more menacing form. December 2023 marks the unsettling return of ‘.tprc’, not just a rehash of the old, but a cunning evolution that puts both individuals and organizations on high alert. Its victims haven’t been spared: healthcare facilities and the education system had havoc, data loss and operational chaos.
It cunningly injects its malicious payload into host’s regasm.exe and takes its data as hostage, encrypting files, exploiting vulnerabilities and leaving victims helpless until the ransom is paid. But there’s light in the darkness, by understanding its anatomy – its encryption methods, communication channels, and preferred entry points – we can build defenses.
The ransomware sample in question is a .Net file and under its resource section with the name of ‘TC0412.properties’, the actual malicious payload exists as a PE file.
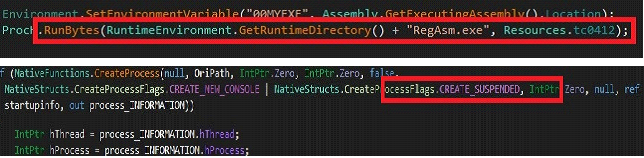
This .Net file creates the RegAsm.exe process in suspend mode to inject the ‘TC0412’ malicious PE file into the RegAsm.exe process.
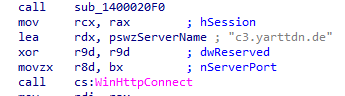
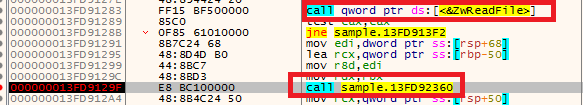
Analysing the malicious file ‘TC0412”, we found that this malicious file tries to connect to the network of the domain given in Fig 3.
If that system has no internet connection, it returns a rax value as ‘1’ which keeps ZF as ‘0’ for ‘test’ instruction , which makes the flow of code exit the process execution at ‘jne’ instruction.
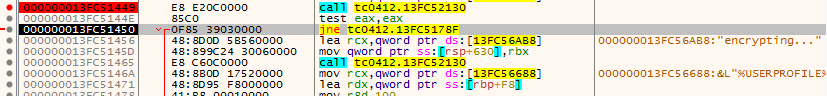
If not taking a jump, it once again gets into the same function which makes a C2C connection which we can see in Fig 4.
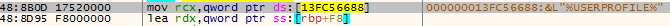
Loads the “%USERPROFILE%” string to rcx, and it is getting passed as an argument to load root directory.
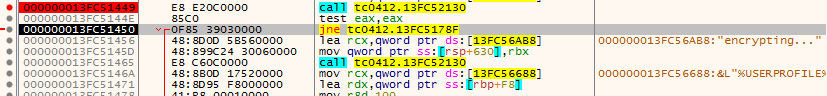
By using NtQueryDirectoryFile API, it traverses through the file system, it checks if the file extension is in the inclusion list, then pass the file path to the encryption function in fig 8 which comes after traversing one folder.
INCLUSION LIST:
“.doc”,”.docx”,”.xls”,”.xlsx”,”.ppt”,”.pptx”,”.odt”,”.ods”,”.jpg”,”.png”,”.gif”,”.pdf”,”.zip”,”.rar”,”.7z”,”.txt”,”.log”,”.mov”,”.avi”,”.mp4″,”.mp3″,”.wma”,”.wav”,”.mkv”,”.flv”,”.vob”,”.wma”,”.psd”,”.dwg”
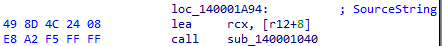
After passing through the function it reads the file to encrypt and pass the address of file as argument to main encryption which is shown in the figure below
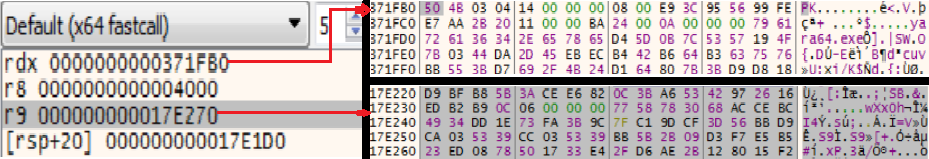
The following fig shows the address of the key stream and the file to be encrypted, being passed as arguments to the above function.
On further analysis, we can find access to AES S-block for key expansion, so we can confirm that this ransomware is using the AES algorithm, which we can find in fig.11.
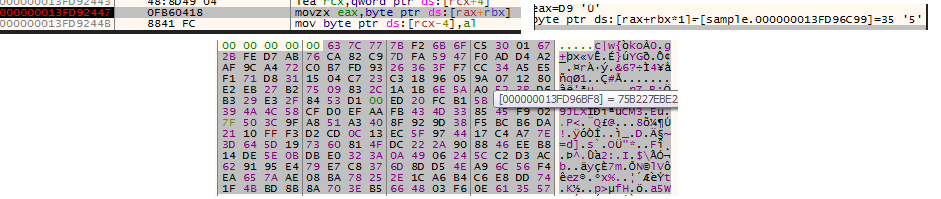
It then encrypts the 16 bytes of file data on every loop and stores that in memory address at location in fig.12 & fig.13.
After doing all the job on file the encrypted file looks like below one,
It then writes at the end of every encrypted file, a data which is size of 48 bytes which may be used as the key for decryption, which looks as in fig.15 and it changes the extension of encrypted file to .tprc as shown in fig.16.
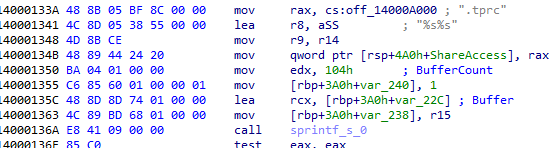
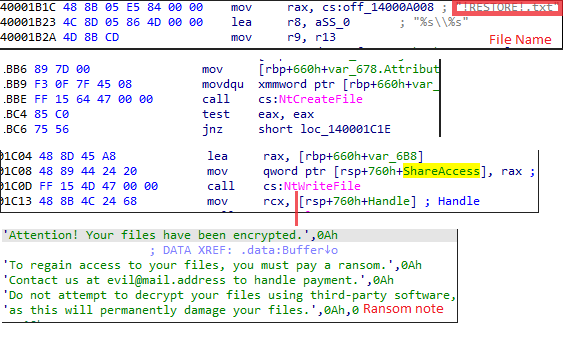
On completing data encryption and changing the extension, it drops a file with the name “!Restore.txt” in that folder with help of NtCreateFile API and it writes the ransom note into it by NtWritefile API.
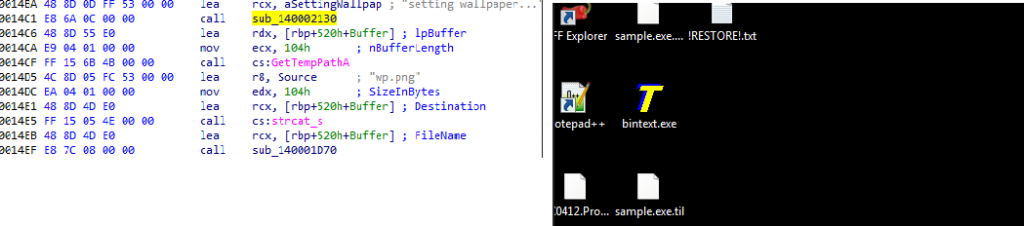
It encrypts all the data that are present in “%UserProfile%” area and after doing that it sets the wallpaper “wp.png” as shown in fig.18.
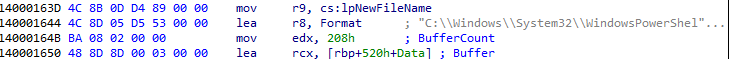
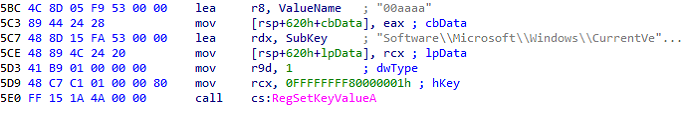
On further analysis we can see the malware gains Persistence, by setting the registry value of “SoftwareMicrosoftWindowsCurrentVersionRun” for the location of “C:ProgramData0aaaa.exe” and it also makes persistence for Script that runs by using PowerShell command “C:WindowsSystem32Windows PowerShellv1.0powershell.exe -ep bypass %s” where the location for script was “C:ProgramData0aaaa.ps1”.
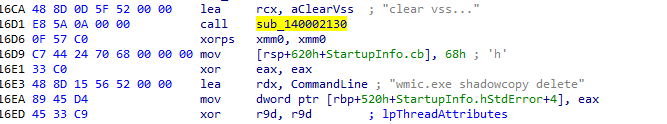
It then executes the code to make sure of deleting shadow copy using command ‘wmic.exe shadow copy delete’ that shown fig.21
With the increasing risk of ransomware attacks, it’s important to take steps to protect your data. Using a reliable security solution like K7 Total Security and keeping it updated is crucial to defend against these threats.
IoCs
| Hash | Detection Name |
| 96CE6FB0513AC8F9DBCE153F362D6C7D | Ransomware ( 005a7a3d1 ) |
Source: Original Post
“An interesting youtube video that may be related to the article above”
Views: 0